Abstract
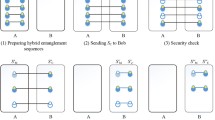
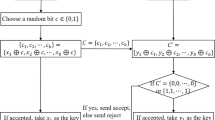
The information leakage problem in the efficient bidirectional quantum secure direct communication protocol with single photons in both polarization and spatial-mode degrees of freedom is pointed out. Next, a way to revise this protocol to a truly secure one is given. We hope people pay more attention to the information leakage problem in order to design truly secure quantum communication protocols.
Similar content being viewed by others
References
Xie, S., Wang, Y.: Construction of tree network with limited delivery latency in homogeneous wireless sensor networks. Wirel. Pers. Commun. 78(1), 231–246 (2014)
Fu, Z., Ren, K., Shu, J., Sun, X., Huang, F.: Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans. Parallel Distrib. Syst. (2015). doi:10.1109/TPDS.2015.2506573
Fu, Z., Sun, X., Liu, Q., Zhou, L., Shu, J.: Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans. Commun. E98B(1), 190–200 (2015)
Ma, T., Zhou, J., Tang, M., Tian, Y., Al-Dhelaan, A., Al-Rodhaan, M., Lee, S.: Social network and tag sources based augmenting collaborative recommender system. IEICE Trans. Inf. Syst. E98D(4), 902–910 (2015)
Ren, Y., Shen, J., Wang, J., Han, J., Lee, S.: Mutual verifiable provable data auditing in public cloud storage. J. Internet Technol. 16(2), 317–323 (2015)
Xia, Z., Wang, X., Sun, X., Wang, Q.: A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 27(2), 340–352 (2016)
Gisin, N., Ribordy, G.G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–195 (2002)
Gao, F., Qin, S.-J., Guo, F.-Z., Wen, Q.-Y.: Cryptanalysis of the arbitrated quantum signature protocols. Phys. Rev. A 84(2), 022344 (2011)
Lo, H.K., Ko, T.M.: Some attacks on quantum-based cryptographic protocols. Quantum. Inf. Comput. 5(1), 41–48 (2005)
Liu, Z.-H., Chen, H.-W., Wang, D., Li, W. -Q.: Cryptanalysis and improvement of three-particle deterministic secure and high bit-rate direct quantum communication protocol. Quantum. Inf. Process. 13(6), 1345–1351 (2014)
Zhang, Y.S., Li, C.F., Guo, G.C.: Comment on “Quantum key distribution without alternative measurements” [Phys. Rev. A 61, 052312 (2000)]. Phys. Rev. A 6303(3), 036301 (2001)
Gao, F., Qin, S.-J., Wen, Q.-Y.: A simple participant attack on the Bradler-Dusek protocol. Quantum. Inf. Comput. 7(4), 329–334 (2007)
Gao, F., Wen, Q.-Y., Zhu, F.-C.: Teleportation attack on the QSDC protocol with a random basis and order. Chin. Phys. B 17(9), 3189–3193 (2008)
Qin, S.-J., Gao, F., Wen, Q.-Y., Zhu, F.-C.: Improving the security of multiparty quantum secret sharing against an attack with a fake signal. Phys. Lett. A 357(2), 101–103 (2006)
Hao, L., Li, J., Long, G.: Eavesdropping in a quantum secret sharing protocol based on Grover algorithm and its solution. Sci. China: Phys. Mech. Astron. 53(3), 491–495 (2010)
Gao, F., Qin, S.-J., Guo, F.-Z., Wen, Q.-Y.: Dense-Coding Attack on Three-Party quantum key distribution protocols. IEEE J. Quantum Electron. 47(5), 630–635 (2011)
Cai, Q.Y.: The “ping-pong” protocol can be attacked without eavesdropping. Phys. Rev. Lett. 91(10), 109801 (2003)
Gao, F., Wen, Q.Y., Zhu, F.C.: Comment on: “Quantum exam” [Phys. Lett. A 350 (2006) 174]. Phys. Lett. A 360(6), 748–750 (2007)
Gao, F., Qin, S.-J., Wen, Q.-Y., Zhu, F.-C.: Cryptanalysis of multiparty controlled quantum secure direct communication using Greenberger-Horne-Zeilinger state. Opt. Commun. 283(1), 192–195 (2010)
Qin, S.J., Gao, F., Guo, F.Z., Wen, Q.Y.: Comment on “Two-way protocols for quantum cryptography with a nonmaximally entangled qubit pair”. Phys. Rev. A 82(3), 036301 (2010)
Liu, Z.H., Chen, H.W., Liu, W.J., Xu, J., Li, Z.Q.: Analyzing and revising a two-way protocol for quantum cryptography with a nonmaximally entangled qubit pair. Int. J. Quantum. Inf. 9(5), 1329–1339 (2011)
Gao, F., Guo, F.Z., Wen, Q.Y., Zhu, F.C.: Revisiting the security of quantum dialogue and bidirectional quantum secure direct communication. Sci. China Ser. G-Phys. Mech. Astron. 51(5), 559–566 (2008)
Liu, Z.H., Chen, H.W.: Comment on “Cryptanalysis and Improvement of a Quantum Network System of QSS-QDC Using chi-Type Entangled States” [Chin. Phys. Lett. 29 (2012) 110305]. Chin. Phys. Lett. 30(7), 079903 (2013)
Liu, Z.H., Chen, H.W.: Comment on “Improvement of Controlled Bidirectional Quantum Direct Communication Using a GHZ State” [Chin. Phys. Lett. 30 (2013) 040305]. Chin. Phys. Lett. 30(7), 079901 (2013)
Liu, Z.H., Chen, H.W., Liu, W.J., Xu, J.: Comment on “A Quantum Network System of QSS-QDC Using chi-Type Entangled States” [Chin. Phys. Lett. 29 (2012) 050303]. Chin. Phys. Lett. 30(3), 039901 (2013)
Gao, G.: Information leakage in quantum dialogue by using the two-qutrit entangled states. Mod. Phys. Lett. B 28(12), 1450094 (2014)
Ye, T.Y.: Analysis on security loophole of Two-Step efficient quantum dialogue with Three-Particle entangled w state. Int. J. Theor. Phys. 54(6), 1775–1778 (2015)
Tan, Y.G., Cai, Q.Y.: Classical correlation in quantum dialogue. Int. J. Quantum. Inf. 6(2), 325–329 (2008)
Wang, L.L., Ma, W.P., Shen, D.S., Wang, M.L.: Efficient bidirectional quantum secure direct communication with single photons in both polarization and Spatial-Mode degrees of freedom. Int. J. Theor. Phys. 54(10), 3443–3453 (2015)
Acknowledgments
This work is supported by National Natural Science Foundation of China (Grant Nos. 61502101 and 61170321), Natural Science Foundation of Jiangsu Province, China (Grant No. BK20140651), and Funded by PAPD and CICAEET.
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Liu, ZH., Chen, HW. & Liu, WJ. Information Leakage Problem in Efficient Bidirectional Quantum Secure Direct Communication with Single Photons in Both Polarization and Spatial-Mode Degrees of Freedom. Int J Theor Phys 55, 4681–4686 (2016). https://doi.org/10.1007/s10773-016-3089-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-016-3089-5