Abstract
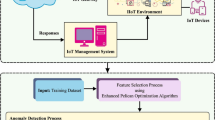
Industrial Internet of Things (IIoT) acts as essential part of the revolutionary transition of conventional industries towards Industry 4.0. By the integration of instruments, sensors, and other industry devices to the Internet, the IIoT enables data analysis, acquisition, and automated control, thereby enhancing the production and performance of the IIoT systems. Owing to the complex IIoT infrastructure, dynamic, large scale, and heterogeneous data, anomaly detection becomes an effective way of ensuring the effective performance of the IIoT. Anomaly detection techniques have been commonly employed for accomplishing security in the IIoT environment. The recent advances of deep learning (DL) models find a way to design effective anomaly detection techniques. With this motivation, this study develops a novel metaheuristic feature selection with DL enabled anomaly detection technique in the IIoT environment, named MFSDL-ADIIoT model. The proposed MFSDL-ADIIoT approach aims to effectively identify and classify the presence of anomalies in the IIoT environment. To accomplish this, the MFSDL-ADIIoT model derives a new deer hunting optimization algorithm based feature selection technique to derive useful subset of features. In addition, cascaded recurrent neural network (CRNN) system is applied for the identification and classification of anomalies. Finally, sparrow search algorithm is utilized to optimally tune the parameters involved in the CRNN model. In order to determine the enhanced detection outcomes of the MFSDL-ADIIoT model, a wide range of simulations was carried out. The extensive comparison study reported the better outcomes of the MFSDL-ADIIoT model over the other recent approaches.















Similar content being viewed by others
Availability of data and materials
Data will be made available on reasonable request.
Code availability
Available on reasonable request.
References
Genge, B., Haller, P., Enăchescu, C.: Anomaly detection in aging industrial internet of things. IEEE Access 7, 74217–74230 (2019)
Tanuska, P., Spendla, L., Kebisek, M., Duris, R., Stremy, M.: Smart anomaly detection and prediction for assembly process maintenance in compliance with industry 4.0. Sensors 21(7), 2376 (2021)
Huong, T.T., Bac, T.P., Long, D.M., Luong, T.D., Dan, N.M., Thang, B.D., Tran, K.P.: Detecting cyberattacks using anomaly detection in industrial control systems: a federated learning approach. Comput. Ind. 132, 103509 (2021)
Bulla, C., Birje, M.N.: Anomaly detection in industrial IoT applications using deep learning approach. In: Fernandes, S.L., Sharma, T.K. (eds.) Artificial Intelligence in Industrial Applications, pp. 127–147. Springer, Cham (2022)
Mothukuri, V., Khare, P., Parizi, R.M., Pouriyeh, S., Dehghantanha, A., Srivastava, G.: Federated learning-based anomaly detection for IoT security attacks. IEEE Internet Things J. 9(4), 2545–2554 (2021)
Zhan, P., Wang, S., Wang, J., Qu, L., Wang, K., Hu, Y., Li, X.: Temporal anomaly detection on IIoT-enabled manufacturing. J. Intell. Manuf. 32(6), 1669–1678 (2021)
Han, G., Tu, J., Liu, L., Martínez-García, M., Peng, Y.: Anomaly detection based on multidimensional data processing for protecting vital devices in 6G-enabled massive IIoT. IEEE Internet Things J. 8(7), 5219–5229 (2021)
Sharghivand, N., Derakhshan, F.: Classification and intelligent mining of anomalies in Industrial IoT. In: Karimipour, H., Derakhshan, F. (eds.) AI-Enabled Threat Detection and Security Analysis for Industrial IoT (pp. 163–180). Springer, Cham (2021)
Fu, L., Zhang, W., Tan, X., Zhu, H.: An algorithm for detection of traffic attribute exceptions based on cluster algorithm in industrial internet of things. IEEE Access 9, 53370–53378 (2021)
Wang, Z., Tian, J., Fang, H., Chen, L., Qin, J.: LightLog: a lightweight temporal convolutional network for log anomaly detection on the edge. Comput. Netw. 203, 108616 (2022)
Peng, Y., Tan, A., Wu, J., Bi, Y.: Hierarchical edge computing: a novel multi-source multi-dimensional data anomaly detection scheme for industrial Internet of Things. IEEE Access 7, 111257–111270 (2019)
Kong, F., Li, J., Jiang, B., Wang, H., Song, H.: Integrated generative model for industrial anomaly detection via bi-directional LSTM and attention mechanism. IEEE Trans. Ind. Inform. (2021). https://doi.org/10.1109/TII.2021.3078192
Wu, D., Jiang, Z., Xie, X., Wei, X., Yu, W., Li, R.: LSTM learning with Bayesian and Gaussian processing for anomaly detection in industrial IoT. IEEE Trans. Ind. Inform. 16(8), 5244–5253 (2019)
Wang, X., Garg, S., Lin, H., Hu, J., Kaddoum, G., Piran, M.J., Hossain, M.S.: Towards accurate anomaly detection in industrial internet-of-things using hierarchical federated learning. IEEE Internet Things J. 9(10), 7110–7119 (2021)
Wu, Y., Dai, H.N., Tang, H.: Graph neural networks for anomaly detection in industrial internet of things. IEEE Internet Things J. 9(12), 9214–9231 (2021)
Zhou, X., Hu, Y., Liang, W., Ma, J., Jin, Q.: Variational LSTM enhanced anomaly detection for industrial big data. IEEE Trans. Ind. Inform. 17(5), 3469–3477 (2020)
De Vita, F., Bruneo, D., Das, S.K.: A novel data collection framework for telemetry and anomaly detection in industrial iot systems. In: 2020 IEEE/ACM Fifth International Conference on Internet-of-Things Design and Implementation (IoTDI, pp. 245–251. IEEE (2020)
Ikram, S.T., Priya, V., Anbarasu, B., Cheng, X., Ghalib, M.R., Shankar, A.: Prediction of IIoT traffic using a modified whale optimization approach integrated with random forest classifier. J. Supercomput. 78(8), 10725–10756 (2022)
Yan, X., Xu, Y., Xing, X., Cui, B., Guo, Z., Guo, T.: Trustworthy network anomaly detection based on an adaptive learning rate and momentum in IIoT. IEEE Trans. Ind. Inform. 16(9), 6182–6192 (2020)
Savic, M., Lukic, M., Danilovic, D., Bodroski, Z., Bajović, D., Mezei, I., Vukobratovic, D., Skrbic, S., Jakovetić, D.: Deep learning anomaly detection for cellular IoT with applications in smart logistics. IEEE Access 9, 59406–59419 (2021)
Jose, A., Jeba, S.V.A., Jose, B.J.: A novel missing data imputation algorithm for deep learning-based anomaly detection system in IIoT networks. In: Smart Computing and Self-Adaptive Systems, pp. 27–46. CRC Press (2021)
Makkar, A., Kim, T.W., Singh, A.K., Kang, J., Park, J.H.: SecureIIoT environment: federated learning empowered approach for securing IIoT from data breach. IEEE Trans. Ind. Inform. 18(9), 6406–6414 (2022)
Shi, F., Yan, L., Zhao, X., Xian-Ke, R.: Machine learning-based time-series data analysis in edge-cloud-assisted oil industrial IoT system. Mob. Inf. Syst. 2022, 1–11 (2022)
Balakrishna, S.: Multi objective-based incremental clustering by fast search technique for dynamically creating and updating clusters in large data. Cluster Comput. 25, 1441–1457 (2022). https://doi.org/10.1007/s10586-022-03549-8
Balakrishna, S.: D-ACSM: a technique for dynamically assigning and adjusting cluster patterns for IoT data analysis. J. Supercomput. (2022). https://doi.org/10.1007/s11227-022-04427-1
Brammya, G., Praveena, S., Ninu Preetha, N.S., Ramya, R., Rajakumar, B.R., Binu, D.: Deer hunting optimization algorithm: a new nature-inspired meta-heuristic paradigm. Comput. J. (2019). https://doi.org/10.1093/comjnl/bxy133
Shankar, K., Perumal, E., Díaz, V.G., Tiwari, P., Gupta, D., Saudagar, A.K.J., Muhammad, K.: An optimal cascaded recurrent neural network for intelligent COVID-19 detection using Chest X-ray images. Appl. Soft Comput. 113, 107878 (2021)
Xue, J., Shen, B.: A novel swarm intelligence optimization approach: sparrow search algorithm. Syst. Sci. Control Eng. 8(1), 22–34 (2020)
Kasongo, S.M., Sun, Y.: Performance analysis of intrusion detection systems using a feature selection method on the UNSW-NB15 dataset. J. Big Data 7(1), 1–20 (2020)
Kotecha, K., Verma, R., Rao, P.V., Prasad, P., Mishra, V.K., Badal, T., Jain, D., Garg, D., Sharma, S.: Enhanced network intrusion detection system. Sensors 21, 7835 (2021). https://doi.org/10.3390/s21237835
Moldovan, D., Anghel, I., Cioara, T., Salomie, I.: Particle swarm optimization based deep learning ensemble for manufacturing processes. In: 2020 IEEE 16th International Conference on Intelligent Computer Communication and Processing (ICCP), pp. 563–570. IEEE (2020)
Funding
No funding.
Author information
Authors and Affiliations
Contributions
The authors confirm contribution to the paper as follows: NC study conception and design, data collection, analysis and interpretation of results, and manuscript preparation. Dr. MUK reviewed the results and approved the final version of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chander, N., Upendra Kumar, M. Metaheuristic feature selection with deep learning enabled cascaded recurrent neural network for anomaly detection in Industrial Internet of Things environment. Cluster Comput 26, 1801–1819 (2023). https://doi.org/10.1007/s10586-022-03719-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-022-03719-8