Abstract
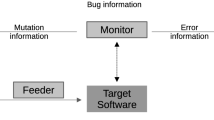
The paper considers the technology of fuzz testing, which is testing software systems by feeding critical or unexpected input data to them. An overview of the current problem state is made and the main systems of fuzz testing are presented. An approach to the fuzz testing technology with the use of algebraic methods, in particular, symbolic modeling, is considered. The lightweight algorithm, which is designed to reduce test generation time, is considered. The algorithm is implemented in the environment of an insertion modeling system and tested in older system versions developed in Linux.
Similar content being viewed by others
References
American Fuzzy Lop. URL: https://lcamtuf.blogspot.com/2014/10/bash-bug-how-we-finally-cracked.html.
Synopsis. URL: https://www.synopsys.com/software-integrity/security-testing/fuzz-testing.html.
Syzkaller. URL: https://github.com/google/syzkaller/blob/master/docs/research.md.
SAGE. URL: https://queue.acm.org/detail.cfm?id=2094081.
Csmith. URL: https://srg.doc.ic.ac.uk/files/papers/compilerbugs-oopsla-19.pdf.
O. O. Letychevskyi, Ya. V. Hryniuk, and V. M. Yakovlev, “Algebraic approach to vulnerability formalization in the binary code,” Control Systems and Computers, No. 6, 5–20 (2019)
A. Letichevsky, “Algebra of behavior transformations and its applications,” in: V. B. Kudryavtsev, I. G. Rosenberg, and M. Goldstein (eds.), Structural Theory of Automata, Semigroups, and Universal Algebra; NATO Science Series II: Mathematics, Physics and Chemistry, Vol. 207, Springer, Dordrecht (2005), pp. 241–272.
O. Letychevskyi, V. Peschanenko, V. Radchenko, Y. Hryniuk, and V. Yakovlev, “Algebraic patterns of vulnerabilities in binary code,” in: Proc. of 2019 10th Intern. Conf. on Dependable Systems, Services and Technologies (DESSERT’2019) (Leeds, UK, June 5–7, 2019), IEEE (2019), pp. 70–73.
S. V. Potiyenko, “Methods of forward and backward symbolic modeling of systems specified by basic protocols,” Problems in Programming, No. 4, 39–45 (2008).
A. A. Letichevsky, A. B. Godlevsky, A. A. Letychevsky Jr, S. V. Potiyenko, and V. S. Peschanenko, “Properties of a predicate transformer of the VRS system,” Cybern. Syst. Analysis, Vol. 46, No. 4, 521–532 (2010). https://doi.org/10.1007/s10559-010-9229-7.
A. Letichevsky, O. Letychevskyi, and V. Peschanenko, “Insertion modeling and its applications,” Computer Science J. of Moldova, Vol. 24, Iss. 3, 357–370 (2016).
Author information
Authors and Affiliations
Corresponding author
Additional information
Translated from Kibernetyka ta Systemnyi Analiz, No. 1, January–February, 2022, pp. 181–189.
Rights and permissions
About this article
Cite this article
Letychevskyi, O.O., Peschanenko, V.S. & Hryniuk, Y.V. Fuzz Testing Technique and its Use in Cybersecurity Tasks. Cybern Syst Anal 58, 157–163 (2022). https://doi.org/10.1007/s10559-022-00445-2
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10559-022-00445-2