Abstract
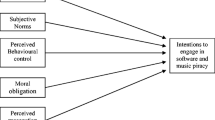
Softlifting, or the illegal duplication of copyrighted software by individuals for personal use, is a serious and costly problem for software developers and distributors. Understanding the factors that determine attitude toward softlifting is important in order to ascertain what motivates individuals to engage in the behavior. We examine a number of factors, including personal moral obligation (PMO), perceived usefulness, and awareness of the laws and regulations governing software acquisition and use, along with facets of personal self-identity that may play a role in the development of attitudes and therefore intentions regarding this behavior. These factors are examined across multiple settings expected to be pertinent to our survey respondents: home, work and school. Personal moral obligation and perceived usefulness are significant predictors of attitude across all settings. Past behavior is a significant predictor of intention across all settings, and a significant predictor of attitude in the home setting. We find evidence that awareness of the law causes a less favorable evaluation of softlifting in the school setting only, but has little effect in the home and work settings. As in previous studies, attitude is a significant predictor of intent. We do not find indications that one’s personal self-identity influences one’s attitude towards the behavior and the intention to perform it, except in the case of legal identity, where marginally significant effects are found in the work environment.
Similar content being viewed by others
References
Ajzen, I.: 1985, ‚From Intentions to Actions: A Theory of Planned Behavior’, in J. Kuhl and J. Beckmann (eds.), Action Control – From Cognition to Behavior (Springer-Verlag, Berlin) pp. 11–39
Ajzen I. 1991, The Theory of Planned Behavior Organizational Behavior and Human Decision Processes, 50, 179–211
Ajzen I., M. Fishbein: 1980, Understanding Attitudes and Predicting Social Behavior, (Prentice-Hall, Englewood Cliffs, NJ)
Athey T., R. Zmud: 1987, Computers and Information Systems, (Scott, Foresman and Company, Glenview, IL)
Banerjee, D., T. Cronan, and T. W. Jones: 1998. ‚Modeling IT Ethics: A Study in Situational Ethics’, MIS Quarterly, March, 22(1), 31–60
Beck L., I. Ajzen: 1991, Predicting Dishonest Actions Using the Theory of Planned Behavior. Journal of Research in Personality, Vol. 25, pp. 285–301
Bommer M., C. Gratto, J. Gravander, M. Tuttle: 1987, A Behavioral Model of Ethical and Unethical Decision Making. Journal of Business Ethics, Vol. 6, pp. 265–280
Business Software Alliance (2004) First Annual BSA and IDC Piracy Study; http://www.bsa.or.jp/file/PiracyStudy_E.pdf
Chang M. K.: 1998, Predicting Unethical behavior: A Comparison of the Theory of Reasoned Action and the Theory of Planned Behavior. Journal of Business Ethics, Vol. 17, pp. 1825–1834
Cheng H. K., R. R. Sims, H. Teegen: 1997, To Purchase or Pirate Software: An Empirical Study. Journal of Management Information Systems, Vol. 13, pp. 49–60
Chin, W. W.: 1998. ‚The Partial Least Squares Approach for Structural Equation Modeling’, in G. A. Marcoulides (ed.), Modern Methods for Business Research (Lawrence Erlbaum Associates, Mahwah, NJ)
Christensen, A. L. and M.M. Eining: 1991, ‚Factors Influencing Software Piracy: Implications for Accountants’, Journal of Information Systems 5(1), 67–80
Conner, K. R. and R. P. Rumelt: 1991, ‚Software Piracy: An Analysis of Protection Strategies’, Management Science, Feb., 37(2), 125–139
Davis, F. (1989). ‚Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology’, MIS Quarterly 13(3), 319–339
Davis, F. O.: 1993, ‚User Acceptance of Information Technology: System Charasteristics, User Perceptions and Behavioral Impacts’, International Journal of Man-Machine Studies 38, 475–487
Davis F., R. Bagozzi, P. Warshaw: 1989, User Acceptance of Computer Technology: A Comparison of Two Theoretical Models. Management Science, Vol. 35, pp. 982–1003
Digital Divide Network Staff: 2004, Digital Divide Basics Fact Sheet, http://www.digitaldividenetwork.org/content/stories/index.cfm?key=168
Eining, M. M. and A. L. Christensen: 1991, ‚A Psycho-Social Model of Software Piracy: The Development and Test of a Model’, in R. Dejoie, G. Fowler, and D. Paradice (eds.), Ethical Issues in Information Systems (Boyd Fraser, Boston), pp. 182–187
Elm D., M. Nichols: 1993, An Investigation of the Moral Reasoning of Managers. Journal of Business Ethics 12, pp. 817–833
Fishbein M., I. Ajzen: 1975, Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research, (Addison-Wesley, Reading, MA)
Fredricks A. J., D. L. Dossett: 1983, Attitude-Behavior Relations: A Comparison of the Fishbein-Ajzen and the Bentler-Speckart Models Journal of Personality and Social Psychology, Vol. 45, 501–512
Givon M., V. Mahajan, E. Muller: 1995, Software Piracy: Estimation of Lost Sales and the Impact on Software Diffusion Journal of Marketing, Vol. 59(1), pp. 29–37
Glass R., W. Wood: 1996, Situational Determinants of Software Piracy: An Equity Theory Perspective Journal of Business Ethics, Vol. 15, 1189–1198
Gorsuch R. L., J. Ortberg: 1983, Moral Obligation and Attitudes: Their Relation to Behavioral Intentions. Journal of Personality and Social Psychology, Vol. 44, pp. 1025–1028
Grasmick H. G., W. J. Scott: 1982, Tax Evasion and Mechanisms of Social Control: A Comparison with Grand and Petty Theft Journal of Economic Psychology, Vol. 2, pp. 213–230
Harrington, S.: 1989, ‚Why People Copy Software and Create Computer Viruses: Individual Characteristics or Situational Factors’, Information Resource Management Journal 2(3), 28–37
Harrison D. A, P. P. Jr. Mykytyn, C. K. Riemenschneider: 1997, Executive Decisions About Adoption of Information Technology in Small Business: Theory and Empirical Tests, Information Systems Research 8, pp. 171–194
Hessing, D., H. Elfers and R. Weigel: 1988, ‚Exploring the Limits of Self-reports and Reasoned Action: An Investigation of the Psychology of Tax Evasion Behavior’, Journal of Personality and Social Psychology, March, 54, 405–413
Jones T.: 1991, Ethical Decision Making by Individuals in Organizations: An Issues-Contingent Model. Academy of Management Review, Vol. 16, 366–395
Koen, C. and J. Im: 1997, ‚Software Piracy and Its Legal Implications’, Information and Management, January 31(5), 265–272
Logsdon, J., J. Thompson and R. Reid: 1994 ‚Software Piracy: Is It Related to Level of Moral Judgment?’, Journal of Business Ethics, November 13(11), 849–857
Nunnally, J. C. and I. H. Bernstein: 1994. Psychometric theory, 3rd ed. (McGraw-Hill, New York)
Oz E.: 1990, The Attitudes of Managers-To-Be Toward Software Piracy. OR/MS Today, Vol. 17(4), pp. 24–26
Peace, A. and D. Galletta: 1996, ‚Developing a Predictive Model of Software Piracy Behavior’, in Proceedings of the Seventeenth International Conference on Information Systems, Cleveland, OH, pp. 209–222
Robinson, R. and B. J. Reithel: 1994, ‚The Software Piracy Dilemma in Public Administration: A Survey of University Software Policy Enforcement’, Public Administration Quarterly, Winter 17(4), 485–498
Sambamurthy, V. and W. Chin: 1994, ‚The Effects of Group Attitudes toward Alternative GDSS Designs on the Decision-Making Performance of Computer-Supported Groups’, Decision Sciences, 25(2), 215–241
Sheppard B. H., J. Hartwick, P. R. Warshaw: 1988, The Theory of Reasoned Action: A Meta-Analysis of Past Research with Recommendations for Modifications and Future Research, Journal of Consumer Research, Vol. 15, pp. 325–343
Shim, J., and G. Taylor: 1991. ‚A Comparative Study of Unauthorized Software Copying: Information Systems Faculty Members’ vs. Practicing Managers’ Perceptions’, in R. Dejoie, G. Fowler, and D. Paradice (eds.), Ethical Issues in Information Systems (Boyd Fraser, Boston)
Simpson P., D. Banerjee, C. Simpson: 1994, Softlifting: A Model of Motivating Factors, Journal of Business Ethics, Vol. 13, pp. 431–438
Sims, R., Cheng, H., and Teegen, H.: 1996, ‚Toward a Profile of Student Software Piraters’, Journal of Business Ethics, August 15(8), 839–849
Snyder M.: 1974, Self-Monitoring of Expressive Behavior. Journal of Personality and Social Psychology, Vol. 30,pp. 526–537
Software Publishers Association: 1997, ‚New Consumer Survey Shows Almost 40% of American Homes Now Have Personal Computers’, http://www.spa.org/research/releases/consur97.htm, March 31
Solomon, S. and J. O’Brien: 1990, ‚The Effect of Demographic Factors on Attitudes Toward Software Piracy’, Journal of Computer Information Systems 30(3), 40–46
Swinyard, W., H. Rinne and A. Kau: 1990, ‚The Morality of Software Piracy: A Cross-Cultural Analysis’, Journal of Business Ethics August 9(8), 655–664
Taylor, G. and J. Shim: 1993, ‚A Comprehensive Examination of Attitudes toward Software Piracy among Business Professors and Executives’, Human Relations April, 46(4), 419–433
Taylor, S. and P. Todd: 1995, ‚Understanding Information Technology Usage: A Test of Competing Models’, Information Systems Research, June 6(2), 144–176
Taylor, S. and P. Todd: 1996, ‚Everything Old is New Again: Exploring the Role of Personal Norms in the Theory of Planned Behavior’, Working Paper
Thompson, R., C. Higgins and J. Howell: 1991, ‚Personal Computing: Toward a Conceptual Model of Utilization’, MIS Quarterly, March 15, 125–143
Thompson R., C. Higgins, J. Howell: 1994, Influence of Experience on Personal Computer Utilization: Testing a Conceptual Model Journal of Management Information Systems, Vol. 11(1), pp. 167–187
Thong, J. and C. Yap: 1998, ‚Testing an Ethical Decision-Making Theory: The Case of Softlifting’, Journal of Management Information Systems, Summer 15(1) 213–237
Triandis, H.: 1979, ‚Values, Attitudes, and Interpersonal Behavior’, in Nebraska Symposium on Motivation (University of Nebraska Press, Lincoln, NE)
Weber J.: 1991, Adapting Kohlberg to Enhance the Assessment of Managers’ Moral Reasoning. Business Ethics Quarterly, Vol. 1, pp. 293–318
Acknowledgments
We gratefully acknowledge the input of Barbara Marcolin, Wynne Chin and Peter Todd.
Author information
Authors and Affiliations
Corresponding author
Additional information
Dr. Tim Goles is an assistant Professor in the Information Systems Department of the University of Texas-San Antonio. He has numerous publications, most of which pertain to information systems.
Dr. Bandula Jayatilaka is an Assistant Professor in the School of Mangement in Binghamton University-SUNY. Most of his publications pertain to information systems.
Dr. Beena George is an Assistant Professor at the Cameron School of Business, University of St. Thomas, Houston, Most of her pblications pertain to information systems.
Dr. Linda Parsons is an Assistant Professor in the Accounting Department at George Mason University. Most of her publications pertain to accounting information systems and nonprofit organizations.
Dr. David S. Taylor is an Assitant Professor at Sam Houston State University. Most of his publications pertain to information systems.
Rebecca Brune has a strong accounting background; her work is predominantly in the information systems field.
Appendix A
Appendix A
The following definition of softlifting was provided to survey participants in the introduction of the survey:
The phrase “copying software” is intended to encompass these behaviors:
-
You purchase software and give copies to your friends, coworkers or other students.
-
Your friend, coworker or other student provides you a copy of software.
-
Your friend, coworker or other student allows you to copy software.
-
You copy software at home or at work or at school and install it on another machine.
“Copying software” does not include
-
the making of a single backup copy, or
-
the acquisition of shareware or freeware requiring no licensing or payment.
Measurement Items – 7-point Likert scales:
Past behavior
PB1 I have copied software in the past (very frequently to very infrequently).
PB2 I only use software that I purchase or is authorized for my use (strongly agree to strong disagree).
Perceived Usefulness (strongly agree to strongly disagree)
PU1 Copying software would be useful.
PU2 Copying software allows me to have more enjoyment out of my personal computer.
PU3 Copying software would allow me to get more value from my personal computer.
PU4 It is easier to obtain software for use by copying it than by purchasing it.
PU5 Overall, the advantages of copying software will outweigh the disadvantages.
PU6 Copying software would allow me to improve my performance.
Awareness of the Law (strongly certain to strongly uncertain)
AW1 Copying software is illegal.
AW2 Anyone copying software for personal use (that is, not reselling it for a profit) can be sued.
AW3 Anyone copying software for use (that is, not reselling it for a profit) can be jailed.
AW4 Anyone copying software for use (that is, not reselling it for a profit) can be fined.
Personal moral obligation (strongly agree to strongly disagree)
MO1 It is my obligation as a personal computer user not to copy software.
MO2 I would not feel guilty if I used copied software.
MO3 I would feel guilty if I copied software.
Risk-taking personal identity (strongly agree to strongly disagree)
RT1 I see myself as a risk taker.
RT2 I prefer to avoid taking unnecessary chances.
Legal personal identity (strongly agree to strongly disagree)
LG1I see myself as someone who is law-abiding.
Technical personal identity (strongly agree to strongly disagree)
TE1 I see myself as someone who needs to have the latest version of software.
TE2 I see myself as someone who needs to be on the leading edge of technology.
TE3 With respect to computer software, for me having more is always better.
Attitude (strongly agree to strongly disagree)
AT1 Using copied software is a bad idea.
AT2 I dislike the idea of using copied software.
AT3 Using copied software is a wise idea.
Behavioral Intention (strongly agree to strongly disagree)
IN1 I do not intend to copy software in the future.
IN2 I do not plan to copy software within the next year.
IN3 If the need or opportunity arises within the next year, I plan to copy software.
Rights and permissions
About this article
Cite this article
Goles, T., Jayatilaka, B., George, B. et al. Softlifting: Exploring Determinants of Attitude. J Bus Ethics 77, 481–499 (2008). https://doi.org/10.1007/s10551-007-9361-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10551-007-9361-0