Abstract
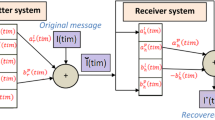
The use of CMOS technology to generate neural session keys is presented in this research for incorporation with the Internet of Things (IoT) to improve security. Emerging technology advancements in the IoT era have enabled better tactics to exacerbate energy efficiency and security difficulties. Current safety solutions do not effectively address the security of IoT. Regarding IoT integration, a tiny logic area ASIC design of a re-keying enabled Triple Layer Vector-Valued Neural Network (TLVVNN) is presented utilizing CMOS designs with measurements of 65 and 130 nanometers. There hasn’t been much study into optimizing the value of neural weights for faster neural synchronization. Harris’ Hawks is used in this instance to optimize the neural network’s weight vector for faster coordination. Once this process is completed, the synchronized weight becomes the session key. This method offers several advantages, namely (1) production of the session key by mutual neural synchronization over the public channel is one of the advantages of this technology. (2) It facilitates Hawks-based neural weight vector optimization for faster neural synchronization across public channels. (3) As per behavioral modeling, the synchronization duration might be reduced from 1.25 ms to less than 0.7 ms for a 20% weight imbalance in the re-keying phase. (4) Geometric, brute force, and majority attacks are all prohibited. Experiments to validate the suggested method’s functionality are carried out, and the results show that the proposed approach outperforms current similar techniques in terms of efficiency.























Similar content being viewed by others
References
Perrig A (1999) Efficient collaborative key management protocols for secure autonomous group communication. In: International workshop on cryptographic techniques and electronic commerce. University of Hong Kong Press, pp 192–202
Boyd C, Mathuria A (2013) Protocols for authentication and key establishment Springer books
Dolecki M, Kozera R (2015) The impact of the TPM weights distribution on network synchronization time. In: Computerinformation systems and industrial management. Springer international publishing, vol 9339. pp 451–460
Dong T, Huang T (2020) Neural cryptography based on complex-valued neural network. IEEE Trans Neural Netw Learn Syst 31(11):4999–5004
Gu X, Zhao Y, Yang J (2012) Reducing rekeying time using an integrated group key agreement scheme. J Commun Netw 14(4):418–428
Heidari AA, Mirjalili S, Faris H, Aljarah I, Mafarja M, Huiling C (2019) Harris hawks optimization: Algorithm and applications. Futur Gener Comput Syst 97:849–872
Ingemarsson I, Tang D, Wong C (1982) A conference key distribution system. IEEE Trans:714–720
Jarecki S, Kim J, Tsudik G (2011) Flexible robust group key agreement. IEEE Trans Parallel DistribSyst 22(5):879–886
Jeong Sooyong, Park Cheolhee, Hong Dowon, Seo Changho, Jho Namsu (2021) Neural cryptography based on generalized tree parity machine for real-life systems. Secur Commun Netw, 2021
Joux A (2000) A one round protocol for tripartite Diffie -Hellman” algorithmic number theory. 4th International Symposium ANTS-IV 1838:385–393
Karakaya B, Gülten A, Frasca M (2019) A true random bit generator based on a Memristive chaotic circuit analysis, design and FPGA implementation. Chaos Solit Fractals 119:143–149
Kelsey J, Schneier B, Wagner D, Hall C (1998) Cryptanalytic attacks on pseudorandom number generators. Fast Software Encryption:168–188
Kim Y, Tsudik G (2000) Simple and fault tolerant key agreement for dynamic collaborative groups. 7th ACM Conf Comput Com Sec ACM Press:235–244
Konstantinou E (2013) An efficient constant round id-based group key agreement protocol for Ad hoc networks”. In: and others, editor, Proc of NSS 2013, vol 7873. of LNCS, pp 563– 574
Kumar A (2019) An enhanced quantum key distribution protocol for security authentication. J Discret Math Sci Cryptogr 22:499–507
Liu L, Miao S, Hu H, Deng Y (2016) Pseudo-random bit generator based on non-stationary logistic maps. IET Inf Secur 10:87–94
Liu P, Zeng Z, Wang J (2019) Global synchronization of coupled fractional-order recurrent neural networks. EEE Trans Neural Netw Learn Syst 30(8):2358–2368
Mühlbach S, Wallner S (2008) Secure communication in microcomputer bus systems for embedded devices. J Syst Archit 54(11):1065–1076
NIST (2020) NIST Statistical Test
Patidar V, Sud KK, Pareek NK (2009) A pseudo random bit generator based on chaotic logistic map and its statistical testing. Informatica 33:441–452
Sarkar A. (2021) Deep learning guided double hidden layer neural synchronization through mutual learning. Neural Process Lett 53:1355–1384
Sarkar A, Khan MZ, Noorwali A (2021) CMOS technology-based energy efficient artificial neural session key synchronization for securing IoT. Comput Electr Eng 95:107369
Shacham LN, Klein E, Mislovaty R, Kanter I, Kinzel W (2004) Cooperating attackers in neural cryptography. Physical Review E, vol 69(6)
Steiner M, Tsudik G, Waidner M (1996) Diffie-hellman key distribution extended to group communication. 3rd ACM ACM Conf Comput Commun Secur ACM press:31–37
Steiner M, Tsudik G, Waidner M (2000) Key agreement in dynamic peer groups. IEEE Trans Parallel Distrib Syst 11(8):769–780
Teodoro AAM, Gomes OSM, Saadi M et al (2021) An FPGA-based performance evaluation of artificial neural network architecture algorithm for IoT. Wirel Pers Commun
Volkmer M, Wallner S (2005) Tree parity machine rekeying architectures. IEEE Trans Comput 54(4):421–427
Wu Q, Mu Y, Susilo W, Qin B, Domingo-Ferrer J (2009) Asymmetric group key agreement”. In: Iand others, editor, Proc of Eurocrypt ’09, vol 5479. of LNCS, pp 153–70
Zhang L, Wu Q, Qin B, Domingo-Ferrer J (2011) Provably secure one-round identity-based authenticated asymmetric group key agreement protocol”. Inf Sci 181(19):4318–29
Acknowledgements
The author expressed deep gratitude for the moral and congenial atmosphere support provided by the Ramakrishna Mission Vidyamandira, Belur Math, India through the DBT STAR college scheme.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
No conflict of Interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sarkar, A. A symmetric neural cryptographic key generation scheme for Iot security. Appl Intell 53, 9344–9367 (2023). https://doi.org/10.1007/s10489-022-03904-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-022-03904-7