Abstract
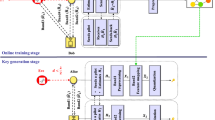
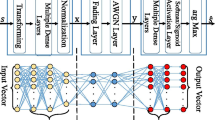
As a novel approach to enhance information security, physical-layer key generation is based on the channel reciprocity and spatial decorrelation of the wireless channels between two legitimate sides. Due to the half-duplex mode of communication systems, the channel responses detected by the two sides are not exactly reciprocal. Also, the eavesdropper may be extremely close to the legitimate side, and information leakage could arise due to the spatial correlation in this case. To solve this problem, this paper proposes an efficient physical-layer key generation scheme based on the combination of an autoencoder and Domain-Adversarial Training of Neural Networks (DANN), i.e., Domain-Adversarial Training of Autoencoder (DAAE). DAAE extracts the reciprocal channel features of the legitimate sides while maximizing the feature difference on the eavesdropper. Simulation experiments are conducted to verify the effectiveness of DAAE, and the experimental results show that based on DAAE, the correlation of extracted features between the eavesdropper and its adjacent node is weakened without significant influence on the legitimate sides. Meanwhile, after quantization, the primary key shows a good consistency rate and randomness. The proposed method has a good potential for industrial applications.














Similar content being viewed by others
Data Availability
The datasets generated during the current study are available through the following links: https://drive.google.com/file/d/1_G5DpOiL-82mGxY1idWbNYgq2sLRgLn9/view?usp=sharing.
References
Wu Y, Khisti A, Xiao C, Caire G, Wong KK, Gao X (2018) A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE J Sel Areas Commun 36:679–695
Ottaviani C, Woolley MJ, Erementchouk M, Federici JF, Mazumder P, Pirandola S, Weedbrook C (2020) Terahertz quantum cryptography. IEEE J Sel Areas Commun 38:483–495
Maurer UM (1993) Secret key agreement by public discussion from common information. IEEE Trans Inf Theory 39:733–742
Hamamreh JM, Furqan HM, Arslan H (2019) Classifications and applications of physical layer security techniques for confidentiality: a comprehensive survey. IEEE Communications Surveys Tutorials 21:1773–1828
Zhang J, Duong TQ, Marshall A, Woods R (2016) Key generation from wireless channels: a review. IEEE Access 4:614–626
Sudarsono A, Yuliana M, Kristalina P (2018) A Reciprocity Approach for Shared Secret Key Generation Extracted from Received Signal Strength in The Wireless Networks. In: 2018 International Electronics Symposium on Engineering Technology and Applications (IES-ETA), pp 170–175. https://doi.org/10.1109/ELECSYM.2018.8615568
Peng Y, Wang P, Xiang W, Li Y (2017) Secret key generation based on estimated channel state information for TDD-OFDM systems over fading channels. IEEE Trans Wirel Commun 16:5176–5186
Li G, Hu A, Zou Y, Peng L, Valkama M (2015) A novel transform for secret key generation in time-varying TDD Channel under hardware fingerprint deviation. In: 2015 IEEE 82nd vehicular technology conference (VTC2015-fall), pp 1–5. https://doi.org/10.1109/VTCFall.2015.7390807
Goel A, Vishwakarma VP (2016) Efficient feature extraction using DCT for gender classification. In: 2016 IEEE international conference on recent trends in electronics, information communication technology (RTEICT), pp 1925–1928. https://doi.org/10.1109/RTEICT.2016.7808171
Li G, Hu A, Zhang J, Peng L, Sun C, Cao D (2018) High-agreement uncorrelated secret key generation based on principal component analysis preprocessing. IEEE Trans Commun 66:3022–3034
Li J, Zhang Q, Xin X, Tao Y, Tian Q, Tian F, Chen D, Shen Y, Cao G, Gao Z, Qian J (Year) Deep learning-based massive MIMO CSI feedback. In: 2019 18th International Conference on Optical Communications and Networks (ICOCN), pp 1–3. https://doi.org/10.1109/ICOCN.2019.8934725
He H, Jin S, Wen CK, Gao F, Li GY, Xu Z (2019) Model-driven deep learning for physical layer communications. IEEE Wirel Commun 26:77–83
Wang T, Wen C, Jin S, Li GY (2019) Deep learning-based CSI feedback approach for time-varying massive MIMO channels. IEEE Wireless Commun Lett 8:416–419
Wen C, Shih W, Jin S (2018) Deep learning for massive MIMO CSI feedback. IEEE Wireless Commun Lett 7:748–751
Liu Z, Zhang L, Ding Z (2019) Exploiting bi-Directional Channel reciprocity in deep learning for low rate massive MIMO CSI feedback. IEEE Wireless Commun Lett 8:889–892
Weinand A, Sattiraju R, Karrenbauer M, Schotten HD (2019) Supervised learning for physical layer based message authentication in URLLC scenarios. In: 2019 IEEE 90th vehicular technology conference (VTC2019-fall), pp 1–7. https://doi.org/10.1109/VTCFall.2019.8891424
Zhang X, Li G, Zhang J, Hu A, Hou Z, Xiao B (2022) Deep-learning-based physical-layer secret key generation for FDD systems. IEEE Internet Things J 9:6081–6094
Han J, Zeng X, Xue X, Ma J (2020) Physical layer secret key generation based on autoencoder for weakly correlated channels. In: 2020 IEEE/CIC international conference on Communications in China (ICCC), pp 1220–1225. https://doi.org/10.1109/ICCC49849.2020.9238931
He X, Dai H, Huang Y, Wang D, Shen W, Ning P (2014) The security of link signature: a view from channel models. In: 2014 IEEE conference on communications and network security, pp 103–108. https://doi.org/10.1109/CNS.2014.6997473
Caruana R (1997) Multitask learning. Mach Learn 28:41–75
Yaroslav G, Victor L (2015) Unsupervised domain adaptation by backpropagation. In: 32nd international conference on machine learning (ICML), pp 1180–1189
Rangari JD, Karmore SP (2014) Comparative analysis and development of new approach for random testing. In: 2014 international conference on circuits. Systems, Communication and Information Technology Applications (CSCITA), pp 332–335
Chen C, Jensen MA (2011) Secret key establishment using temporally and spatially correlated Wireless Channel coefficients. IEEE Trans Mob Comput 10:205–215
Premnath SN, Jana S, Croft J, Gowda PL, Clark M, Kasera SK, Patwari N, Krishnamurthy SV (2013) Secret key extraction from wireless signal strength in real environments. IEEE Trans Mob Comput 12:917–930
Maaten L, Group BJCS (2013) Barnes-hut-SNE. In: 2013 international conference on learning representations, pp 1–11
Acknowledgments
This work was supported by the Shanghai Sailing Program (Grant No. 19YF1451500), the Program of Shanghai Science and the Technology Innovation Action Plan (Grant No. 19DZ1201100) and the National-level Student Innovation and Entrepreneurship Training Program.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhou, J., Zeng, X. Physical-layer secret key generation based on domain-adversarial training of autoencoder for spatial correlated channels. Appl Intell 53, 5304–5319 (2023). https://doi.org/10.1007/s10489-022-03777-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-022-03777-w