Abstract
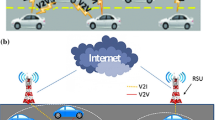
Vehicular ad hoc network (VANET) has increased its popularity in the modern era of communication and promises to provide ubiquitous connectivity, ultra-reliable, and low-latency transmissions. In day-to-day scenario, accidents or vehicular congestion may lead to a major problem and form a Traffic Congested Zone (TCZ). To overcome this situation relay-assisted vehicular communication is used to transmit the emergency and alert information in TCZ. Selecting the relay vehicle in the dynamic vehicular environment with high node density results in difficulties as network stability and also securing the vehicle’s communication remains one of the prevailing concerns in VANET applications. The proposed scheme jointly focuses on both optimal relay vehicle (RVOBU) selection and ensuring the security of RVOBU in TCZ. Initially, the location of the traffic-congested zone (TCZ), emergency/alert information, and security parameters of each vehicle are identified and stored in temporary supporting database (TS-DB) entries that are attached to each RSU. The optimal RVOBU is then selected by using the cluster-based grasshopper optimization algorithm (GOA) and securing the RVOBU using a modified AKA algorithm. Finally, an optimal and secured RVOBU is selected by verification with original and TS-DB entries. The results are compared with other optimization techniques and security is analyzed with existing work. The proposed strategy significantly forms a minimum number of a cluster with optimal RVOBU and deliberates the objective value with secured RVOBU in each iteration. As the result, the proposed scheme outperforms the existing scheme in terms of cluster lifetime, load balancing factor, verification delay, packet delivery ratio (PDR), communication overhead, and computation time.
















Similar content being viewed by others
References
Pan S, Yan H, He J, He Z (2021) Vulnerability and resilience of transportation systems: A recent literature review. Phys A: Stat Mech Its Appl 581(June). https://doi.org/10.1016/j.physa.2021.126235
National Highway Traffic Safety Administration (NHTSA) (2013) U.S. Department of Transportation. Releases Policy on Automated Vehicle Development
Fisher Development of DSRC/WAVE Standards (2007) IEEE 802.11-07/2045r0, June 2007
Center for Sustainable Systems, University of Michigan (2020) Autonomous Vehicles Fact Sheet. February, 29–30. http://css.umich.edu/sites/default/files/AutonomousVehicles_CSS16-18_e2020.pdf
Muthumeenakshi R, Anu A, Monisha, Murugan K (2018) DAKAA: Double Authentication and Key Agreement Algorithm for securing Vehicular Ad hoc Networks. Tenth International Conference on Advanced Computing (ICoAC), Chennai, India, 2018, pp 99–104. https://doi.org/10.1109/ICoAC44903.2018.8939088
Balaji CG, Anu Monisha A, Murugan K (2020) A novel hybrid UE selection scheme for efficient data offloading using D2D communication. Comput J 63(10):1513–1523. https://doi.org/10.1093/comjnl/bxaa041
He Y, Zhai D, Wang D, Tang X, Zhang R (2020) A relay selection protocol for UAV-assisted VANETs. Appl Sci (Switzerland) 10(23):1–16. https://doi.org/10.3390/app10238762
McHergui A, Moulahi T, Nasri S (2019) Relay selection based on deep learning for broadcasting in VANET. 2019 15th International Wireless Communications and Mobile Computing Conference, IWCMC 2019, 865–870. https://doi.org/10.1109/IWCMC.2019.8766487
Al-Kharasani NM, Zukarnain ZA, Subramaniam SK, Hanapi ZM (2020) An adaptive relay selection scheme for enhancing network stability in VANETs. IEEE Access 8:128757–128765. https://doi.org/10.1109/ACCESS.2020.2974105
Ali, Shah SAA (2019) VANET Clustering Using Whale Optimization Algorithm. 2019 International Symposium on Recent Advances in Electrical Engineering (RAEE), Islamabad, Pakistan, pp 1–5. https://doi.org/10.1109/RAEE.2019.8886982
Mirjalili SZ, Mirjalili S, Saremi S, Faris H, Aljarah I (2018) Grasshopper optimization algorithm for multi-objective optimization problems. Appl Intell 48(4):805–820. https://doi.org/10.1007/s10489-017-1019-8
Jahani MTG, Nazarian P, Safari A, Haghifam M (2019) Multiobjective grasshopper optimization algorithm based reconfiguration of distribution networks. J Oper Autom Power Eng 7(2):148–156
Bukar L, Tan CW, Yiew LK, Tan RAyopandW-S (2020) A rule-based energy management scheme for long-term optimal capacity planning of grid-independent micro grid optimized by a multi-objective grasshopper optimization algorithm. Energy Convers Manage 221, Art. no. 113161
Falehi D (2020) Optimal robust disturbance observer-based sliding mode controller using a multi-objective grasshopper optimization algorithm to enhance power system stability. J Ambient Intell Hum Comput 11:5045–5063
Meraihi Y, Gabis AB, Mirjalili S, Ramdane-Cherif A (2021) Grasshopper optimization algorithm: Theory, variants, and applications. IEEE Access 9:50001–50024. https://doi.org/10.1109/ACCESS.2021.3067597
Nguyen TT, Lee JH, Nguyen MT, Kim YH (2019) Machine learning-based relay selection for secure transmission in multi-hop DF relay networks. Electron (Switzerland) 8(9):1–14. https://doi.org/10.3390/electronics8090949
He D, Zeadally S, Xu B, Huang X (2015) An efficient identity-based conditional privacy-preserving authentication scheme for vehicular Ad Hoc networks. IEEE Trans Inf Forensic Secur 10(12):2681–2691
Wazid M, Das AK, Kumar N, Odelu V, Goutham Reddy A, Park K, Park Y (2017) Design of lightweight authentication and key agreement protocol for vehicular Ad Hoc networks. IEEE Access 5:14966–14980. https://doi.org/10.1109/ACCESS.2017.2723265
Wazid M, Das AK, Odelu V, Kumar N, Conti M, Jo M (2018) Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J 5(1):269–282. https://doi.org/10.1109/JIOT.2017.2780232
Wazid M, Das AK, Kumar N, Vasilakos AV, Rodrigues JJPC (2019) Design and analysis of secure lightweight remote user authentication and key agreement scheme on the internet of drones deployment. IEEE Internet Things J 6(2):3572–3584. https://doi.org/10.1109/JIOT.2018.2888821
Wazid M, Das AK, Bhat K, Vasilakos AV (2020) LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J Netw Comput Appl 150:102496. https://doi.org/10.1016/j.jnca.2019.102496
Liu Z, Guo C, Wang B (2020) A physically secure, lightweight three-factor, and anonymous user authentication protocol for IoT. IEEE Access 8:195914–195928. https://doi.org/10.1109/ACCESS.2020.3034219
Huang L, Lu L, Hua W (2020) A survey on next-cell prediction in cellular networks: Schemes and applications. IEEE Access 8:201468–201485. https://doi.org/10.1109/ACCESS.2020.3036070
Aliev H, Kim HW (2020) Matrix-based dynamic authentication with conditional privacy-preservation for vehicular network security. IEEE Access 8:200883–200896. https://doi.org/10.1109/ACCESS.2020.3035845
Aadil F, Ahsan W, Rehman ZU, Shah PA, Rho S, Mehmood I (2018) Clustering algorithm for the internet of vehicles (IoV) based on dragonfly optimizer (CAVDO). J Supercomput 74(9):4542–4567. https://doi.org/10.1007/s11227-018-2305-x
Dolev, Yao A (1983) On the security of public-key protocols. IEEE Trans Inf Theory 29(2):198–208
Ahmad M, Ikram AA, Wahid I, Ullah F, Ahmad A, Alam Khan F (2020) Optimized clustering in vehicular ad hoc networks based on honey bee and genetic algorithm for the internet of things. Peer-to-Peer Netw Applic 13(2):532–547. https://doi.org/10.1007/s12083-019-00724-4
Jamshidi V, Nekoukar V, Refan MH (2021) Real-time UAV path planning by parallel grey wolf optimization with aligning coefficient on the CAN bus. Cluster Comput 24(3):2495–2509. https://doi.org/10.1007/s10586-021-03276-6
Meraihi Y, Gabis AB, Ramdane-Cherif A, Acheli D (2021) A comprehensive survey of the Crow Search Algorithm and its applications. Artif Intell Rev 54(4). Springer Netherlands. https://doi.org/10.1007/s10462-020-09911-9.
Tirkolaee EB, Goli A, Faridnia A, Soltani M, Weber GW (2020) Multi-objective optimization for the reliable pollution-routing problem with cross-dock selection using Pareto-based algorithms. J Clean Prod 276:122927. https://doi.org/10.1016/j.jclepro.2020.122927
Tirkolaee EB, Goli A, Hematian M, Sangaiah AK, Han T (2019) Multi-objective multi-mode resource-constrained project scheduling problem using Pareto-based algorithms. Computing 101(6):547–570. https://doi.org/10.1007/s00607-018-00693-1
Tirkolaee EB, Mardani A, Dashtian Z, Soltani M, Weber GW (2020) A novel hybrid method using fuzzy decision making and multi-objective programming for sustainable-reliable supplier selection in two-echelon supply chain design. J Clean Prod 250:119517. https://doi.org/10.1016/j.jclepro.2019.119517
Alshudukhi JS, Mohammed BA, Al-Mekhlafi ZG (2020) An efficient conditional privacy-preserving authentication scheme for the prevention of side-channel attacks in vehicular Ad Hoc networks. IEEE Access 8. https://doi.org/10.1109/ACCESS.2020.3045940
Emmerich MTM, Deutz AH (2018) A tutorial on multiobjective optimization: fundamentals and evolutionary methods. Nat Comput 17(3):585–609. https://doi.org/10.1007/s11047-018-9685-y
Zhang G, Zuo H (2013) Pareto optimal solution analysis of convex multi-objective programming problem. J Networks 8(2):437–444. https://doi.org/10.4304/jnw.8.2.437-444
Ahsan W, Khan MF, Aadil F, Maqsood M, Ashraf S, Nam Y, Rho S (2020) Optimized node clustering in VANETs by using meta-heuristic algorithms. Electron (Switzerland) 9(3):1–14. https://doi.org/10.3390/electronics9030394
Acknowledgements
The authors would like to thank the anonymous reviewers whose comments have led to improvements in the paper, especially in encouraging the authors to analyze the complexity of the proposed scheme.
Funding
The authors are grateful to Anna Centenary Research Fellowship (CFR/ACRF/2018/AR1/47) provided by the Centre for Research, Anna University, Chennai – 600 025 for the support to carry out this research project.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors certify that they have NO affiliations with or involvement in any organization or entity with any financial or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Monisha, A.A., Reshmi, T.R. & Murugan, K. Secure relay selection scheme for Traffic Congested Zone in VANET using grasshopper optimization and modified authentication key agreement algorithms. Appl Intell 53, 5497–5518 (2023). https://doi.org/10.1007/s10489-022-03572-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-022-03572-7