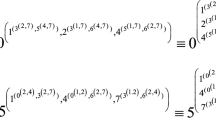Abstract
Virtualization technology allows service providers to operate data centers in a cost-effective and scalable manner. The data center network (substrate network) and the applications executed in the data center (virtual networks) are often modeled as graphs. The nodes of the graphs represent (physical or virtual) servers and switches, and the edges represent communication links. Nodes and links are annotated with the provided and required resources (e.g., memory and bandwidth). The NP-hard virtual network embedding (VNE) problem deals with the embedding of a set of virtual networks to the substrate network such that (i) all (resource) constraints of the substrate network are fulfilled, and (ii) an objective is optimized (e.g., minimizing the communication costs). The existing two-step highly customizable model-driven virtual network embedding (MdVNE) approach combines model transformation (MT) and integer linear programming (ILP) techniques to solve the VNE problem based on a declarative specification. MdVNE generates element mapping candidates from an MT specification and identifies an optimal and correct embeddings using an ILP solver. In the past, developers created the MT and ILP specifications manually and needed to ensure carefully that both are compatible and respect the problem description. In this article, we present a novel construction methodology for synthesizing the MT and ILP specification from a given declarative model-based VNE problem description. This problem description consists of a metamodel for substrate and virtual networks, additional OCL constraints, and an objective function that assigns costs to a given model. This methodology ensures that the derived embeddings are correct w.r.t. the metamodel and the OCL constraints, and optimal w.r.t. the optimization goal. The novel model-based VNE specification is applicable to different network domains, environments, and constraints. Thus, the construction methodology allows to automate most of the steps to realize a correct and optimal VNE algorithm compared to a hand-crafted VNE implementation. Furthermore, the simulative evaluation confirms that using MT techniques reduces the time for solving the VNE problem considerably in comparison with a purely ILP-based approach.






















Similar content being viewed by others
References
Abdeen, H., Varró, D., Sahraoui, H.A., Nagy, A.S., Debreceni, C., Hegedüs, Á., Horváth, Á.: Multi-objective optimization in rule-based design space exploration. In: Crnkovic, I., Chechik, M., Grünbacher, P. (eds.) International Conference on Automated Software Engineering (ASE). ACM, pp. 289–300 (2014)
Abrial, J.R., Hallerstede, S.: Refinement, decomposition, and instantiation of discrete models: application to Event-B. Fundam. Inform. 77(1–2), 1–28 (2007)
Al-Fares, M., Loukissas, A., Vahdat, A.: A scalable, commodity data center network architecture. In: ACM SIGCOMM Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, pp. 63–74 (2008)
Alanen, M., Porres, I., Centre, T., Science, C.: A relation between context-free grammars and meta object facility metamodels. Technical report (2003)
Amaldi, E., Coniglio, S., Koster, A.M.C.A., Tieves, M.: On the computational complexity of the virtual network embedding problem. Electron. Notes Discrete Math. 52, 213–220 (2016)
Anjorin, A., Leblebici, E., Kluge, R., Schürr, A., Stevens, P.: A systematic approach and guidelines to developing a triple graph grammar. In: International Workshop on Bidirectional Transformations, CEUR vol. 1396, pp. 81–95 (2015)
Arendt, T., Biermann, E., Jurack, S., Krause, C., Taentzer, G.: Henshin: advanced concepts and tools for in-place EMF model transformations. In: International Conference on Model Driven Engineering Languages and Systems (MODELS), vol. 6394. Springer, pp. 121–135 (2010)
Ballani, H., Costa, P., Karagiannis, T., Rowstron, A.I.T.: Towards predictable datacenter networks. In: Conference on Applications, pp. 242–253 (2011)
Bari, M.F., Boutaba, R., Esteves, R.P., Granville, L.Z., Podlesny, M., Rabbani, M.G., Zhang, Q., Zhani, M.F.: Data center network virtualization: a survey. Commun. Surv. Tutor. 15(2), 909–928 (2013)
Bhardwaj, S., Jain, L., Jain, S.: Cloud computing: a study of infrastructure as a service (IaaS). Int. J. Eng. Inf. Technol. 2(1), 60–63 (2010)
Bill, R., Fleck, M., Troya, J., Mayerhofer, T., Wimmer, M.: A local and global tour on momot. Softw. Syst. Model. 18(2), 1017–1046 (2019)
Böhm, M., Leimeister, S., Riedl, C., Krcmar, H.: Cloud computing–outsourcing 2.0 or a new business model for it provisioning? In: Application Management. Springer, pp. 31–56 (2011)
Cplex, I.I.: 12.2 user’s manual. Book 12.2 User’s Manual, Series 12.2 User’s Manual (2010)
Deckwerth, F., Varró, G.: Attribute handling for generating preconditions from graph constraints. In: International Conference on Graph Transformation (ICGT), pp. 81–96 (2014)
Denil, J., Jukss, M., Verbrugge, C., Vangheluwe, H.: Search-based model optimization using model transformations. In: System Analysis and Modeling: Models and Reusabilit (SAM), pp. 80–95 (2014)
Dijkstra, E.W.: A Discipline of Programming, vol. 1. Prentice Hall, Upper Saddle River (1976)
Fischer, A., Botero, J.F., Beck, M.T., de Meer, H., Hesselbach, X.: Virtual network embedding: a survey. Commun. Surv. Tutor. 15(4), 1888–1906 (2013)
Fowler, M.: UML Distilled: A Brief Guide to the Standard Object Modeling Language. Addison-Wesley Professional, Boston (2004)
Group, O.M.: Object constraint language 2.0. OMG (2003)
Guo, C., Lu, G., Wang, H.J., Yang, S., Kong, C., Sun, P., Wu, W., Zhang, Y.: Secondnet: a data center network virtualization architecture with bandwidth guarantees. In: Conference on emerging Networking EXperiments and Technologies (CoNEXT), pp. 15:1–15:12 (2010)
Gurobi Optimization, I.: Gurobi optimizer reference manual. https://www.gurobi.com/ (2016). Accessed 17 Jan 2018
Habel, A., Pennemann, K.: Correctness of high-level transformation systems relative to nested conditions. Math. Struct. Comput. Sci. 19(2), 245–296 (2009)
Hadjiconstantinou, E.: Transformation of propositional calculus statements into integer and mixed integer programs: an approach towards automatic reformulation. Brunel University, Technical report (1990)
Heckel, R., Wagner, A.: Ensuring consistency of conditional graph grammars—a constructive approach. ENTCS 2, 118–126 (1995)
Jackson, D.: Alloy: a lightweight object modelling notation. ACM Trans. Softw. Eng. Methodol. 11(2), 256–290 (2002)
Kehrer, T., Taentzer, G., Rindt, M., Kelter, U.: Automatically deriving the specification of model editing operations from meta-models. In: International Conference on Model Transformation (ICMT), pp. 173–188 (2016)
Kessentini, M., Sahraoui, H., Boukadoum, M.: Model transformation as an optimization problem. In: International Conference on Model Driven Engineering Languages and Systems (MODELS). Springer, Berlin, pp. 159–173 (2008)
Kluge, R., Stein, M., Varró, G., Schürr, A., Hollick, M., Mühlhäuser, M.: A systematic approach to constructing incremental topology control algorithms using graph transformation. JVLC 38, 47–83 (2017)
Krieger, M.P., Brucker, A.D.: Extending OCL operation contracts with objective functions. ECEASST 4. https://journal.ub.tu-berlin.de/eceasst/article/view/662, (2011)
Leblebici, E., Anjorin, A., Schürr, A.: Developing eMoflon with eMoflon. ICMT 8568, 138–145 (2014)
Leblebici, E., Anjorin, A., Schürr, A.: Inter-model consistency checking using triple graph grammars and linear optimization techniques. In: Fundamental Approaches to Software Engineering (FASE), pp. 191–207 (2017)
Lopes, F.A., Lima, L., Santos, M., Fidalgo, R., Fernandes, S.: High-level modeling and application validation for SDN. In: Network Operations and Management Symposium, pp. 197–205 (2016)
Meng, X., Pappas, V., Zhang, L.: Improving the scalability of data center networks with traffic-aware virtual machine placement. In: IEEE International Conference on Computer Communications (INFOCOM), pp. 1154–1162 (2010)
Myers, G.J., Sandler, C., Badgett, T.: The Art of Software Testing. Wiley, Hoboken (2011)
Nassar, N., Kosiol, J., Arendt, T., Taentzer, G.: OCL2AC: automatic translation of OCL constraints to graph constraints and application conditions for transformation rules. In: International Conference on Graph Transformation (ICGT), pp. 171–177 (2018)
Nassar, N., Kosiol, J., Arendt, T., Taentzer, G.: Constructing optimized validity-preserving application conditions for graph transformation rules. In: International Conference on Graph Transformation (ICGT), pp. 177–194 (2019)
Pohlmann, U., Hüwe, M.: Model-driven allocation engineering (t). In: International Conference on Automated Software Engineering (ASE), pp. 374–384 (2015)
Pohlmann, U., Hüwe, M.: Model-driven allocation engineering: specifying and solving constraints based on the example of automotive systems. Autom. Softw. Eng. 26(2), 315–378 (2019)
Rabbani, M.G., Esteves, R.P., Podlesny, M., Simon, G., Granville, L.Z., Boutaba, R.: On tackling virtual data center embedding problem. In: IFIP/IEEE International Symposium on Integrated Network Management, pp. 177–184 (2013)
Radke, H.: Weakest liberal preconditions relative to HR* graph conditions. In: International Workshop on Graph Computation Models (GCM), pp. 165–178 (2010)
Radke, H., Arendt, T., Becker, J.S., Habel, A., Taentzer, G.: Translating essential OCL invariants to nested graph constraints for generating instances of meta-models. Sci. Comput. Program. 152, 38–62 (2018)
Rensink, A., Schmidt, A., Varró, D.: Model checking graph transformations: a comparison of two approaches. In: International Conference on Graph Transformation (ICGT), vol. 3256. Springer, pp. 226–241 (2004)
Sahhaf, S., Tavernier, W., Rost, M., Schmid, S., Colle, D., Pickavet, M., Demeester, P.: Network service chaining with optimized network function embedding supporting service decompositions. Comput. Netw. 93, 492–505 (2015)
Schnabel, T., Weckesser, M., Kluge, R., Lochau, M., Schürr, A.: Cardygan: tool support for cardinality-based feature models. In: International Workshop on Variability Modelling of Software-Intensive Systems. ACM, pp. 33–40 (2016)
Schürr, A.: Specification of graph translators with triple graph grammars. In: Graph–Theoretic Concepts in Computer Science, pp. 151–163 (1994)
Shen, S., van Beek, V., Iosup, A.: Statistical characterization of business-critical workloads hosted in cloud datacenters. In: International Symposium on Cluster, Cloud and Grid Computing (CCGrid), pp. 465–474 (2015)
Strüber, D.: Generating efficient mutation operators for search-based model-driven engineering. In: International Conference on Model Transformation (ICMT), pp. 121–137 (2017)
Tomaszek, S., Leblebici, E., Wang, L., Schürr, A.: Virtual network embedding: reducing the search space by model transformation techniques. In: International Conference on Model Transformation (ICMT), pp. 59–75 (2018)
Tomaszek, S., Leblebici, E., Wang, L., Schürr, A.: Model-driven development of virtual network embedding algorithms with model transformation and linear optimization techniques. Modellierung 2018, 39–54 (2018)
Varró, D., Bergmann, G., Hegedüs, Á., Horváth, Á., Ráth, I., Ujhelyi, Z.: Road to a reactive and incremental model transformation platform: three generations of the VIATRA framework. Softw. Syst. Model. 15(3), 609–629 (2016)
Varró, G., Varró, D., Schürr, A.: Incremental graph pattern matching: Data structures and initial experiments. ECEASST 4. https://doi.org/10.14279/tuj.eceasst.4.12 (2006)
Weckesser, M.: Automatisierte analyse integrierter software-produktlinien-spezifikationen. Ph.D. thesis, Darmstadt University of Technology, Germany (2019)
Weckesser, M., Lochau, M., Ries, M., Schürr, A.: Towards complete consistency checks of clafer models. In: International Workshop on Feature-Oriented Software Development (SIGPLAN), pp. 11–20 (2017)
Wohlin, C., Runeson, P., Höst, M., Ohlsson, M.C., Regnell, B.: Experimentation in Software Engineering. Springer, Berlin (2012)
Yang, Y., Chang, X., Liu, J., Li, L.: Towards robust green virtual cloud data center provisioning. IEEE Trans. Cloud Comput. 5(2), 168–181 (2017)
Yang, Z., Guo, Y.: An exact virtual network embedding algorithm based on integer linear programming for virtual network request with location constraint. China Commun. 13(8), 177–183 (2016)
Yu, M., Yi, Y., Rexford, J., Chiang, M.: Rethinking virtual network embedding: substrate support for path splitting and migration. SIGCOMM Comput. Commun. Rev. 38(2), 17–29 (2008)
Zave, P.: Understanding SIP through Model-Checking. In: Principles, Systems and Applications of IP Telecommunications. Services and Security for Next Generation Networks, vol. 5310. Springer, pp. 256–279 (2008)
Zave, P.: Using lightweight modeling to understand chord. SIGCOMM Comput. Commun. Rev. 42(2), 49–57 (2012)
Zeng, D., Guo, S., Huang, H., Yu, S., Leung, V.C.: Optimal VM placement in data centers with architectural and resource constraints. Int. J. Autonom. Adapt. Commun. Syst. 8(4), 392–406 (2015)
Zschaler, S., Mandow, L.: Towards model-based optimisation: using domain knowledge explicitly. In: Software Technologies: Applications and Foundations (STAF), Collocated Workshops, pp. 317–329 (2016)
Acknowledgements
This work was funded by the German Research Foundation (DFG) as part of project A1 within the Collaborative Research Center (CRC) 1053 – MAKI.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Davide Di Ruscio.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
In the appendix we present the restrictions that are not necessary for understanding the work. In Appendix A.1, we present all further restrictions from Sect. 2.1.2. Afterward, we present in Appendix A.2 the constraints and graph constraints from Sect. 3.2.3 (Figs. 21, 22).
1.1 VNE problem description
In this section, we present all node and link constraints relating to Sects. 2.1.2 and 2.2.3





Further ILP node constraints


Further ILP link constraints

1.2 Construction of MT specification
In this section, we present the additional relaxed and graph constraints related to Sect. 3.2.3.




Rights and permissions
About this article
Cite this article
Tomaszek, S., Speith, R. & Schürr, A. Virtual network embedding: ensuring correctness and optimality by construction using model transformation and integer linear programming techniques. Softw Syst Model 20, 1299–1332 (2021). https://doi.org/10.1007/s10270-020-00852-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10270-020-00852-z