Abstract
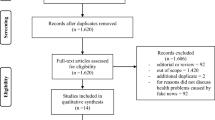
The recent surge in phishing incidents in the post-COVID era poses a serious threat towards the social and economic well-being of users. The escalation in dependency upon the internet for meeting daily chores has made them vulnerable to falling prey to the ever-evolving menace of phishing. The objective of this article is: to explore different tactics and motivational factors behind phishing, identify the communication mediums through which phishing is circulated and perform a detailed review along with a comparison of the various surveys in this domain. Another objective is to determine the open research challenges in this genre and to identify the scope of research in the future. An extensive literature survey is performed, which includes articles from eminent online research databases. Barring a few initial articles related to phishing, the articles published in Science Citation/Scopus-indexed journals and survey/review articles published in the last ten years are considered. Highly cited works are given preference. The search query returned numerous articles, which were narrowed by title screening. Further screening of articles was performed by reading the abstract and eliminating the articles related to user-oriented phishing interventions. Eventually, 25 survey articles were shortlisted to be surveyed. This article is an effort to provide a novel taxonomy of phishing to academia that would assist in identifying the sections where phishing countermeasures are inadequate.




Similar content being viewed by others
Data availability
Since this work is a survey, no datasets were created or analysed. Hence, data sharing is not applicable.
References
Williams, E.J., Hinds, J., Joinson, A.N.: Exploring susceptibility to phishing in the workplace. Int. J. Hum. Comput. Stud. 120, 1–13 (2018)
Maroofi, S., Korczyński, M., Hölzel, A., Duda, A.: Adoption of email anti-spoofing schemes: a large scale analysis. IEEE Trans. Netw. Serv. Manag. 18(3), 3184–3196 (2021)
Pandey, N., Pal, A., et al.: Impact of digital surge during COVID-19 pandemic: a viewpoint on research and practice. Int. J. Inf. Manag. 55, 102171 (2020)
Beech, F.M..: Covid-19 pushes up internet use 70% and streaming more than 12%, first figures reveal. https://www.forbes.com/sites/markbeech/2020/03/25/covid-19-pushes-up-internet-use-70-streaming-more-than-12-first-figures-reveal/?sh=1e813ced3104, (May 2020). Accessed June 2022
Akala, A.: More big employers are talking about permanent work-from-home positions. https://www.cnbc.com/2020/05/01/major-companies-talking-about-permanent-work-from-home-positions.html. Accessed June 2022
BBC News. Twitter allows staff to work from home “forever”. https://www.bbc.com/news/technology-52628119 (2020). Accessed June 2022
APWG. Phishing activity trends report-4th quarter (2022). https://apwg.org/trendsreports/. Accessed July 2023
Abroshan, H., Devos, J., Poels, G., Laermans, E.: Covid-19 and phishing: effects of human emotions, behavior, and demographics on the success of phishing attempts during the pandemic. IEEE Access 9, 121916–121929 (2021)
Lallie, H.S., Shepherd, L.A., Nurse, J.R.C., Erola, A., Epiphaniou, G., Maple, C., Bellekens, X.: Cyber security in the age of Covid-19: a timeline and analysis of cyber-crime and cyber-attacks during the pandemic. Comput. Secur. 105, 102248 (2021)
BNP Media T. Kelly: How hackers are using Covid-19 to find new phishing victims. https://www.securitymagazine.com/articles/92666-how-hackers-are-using-covid-19-to-find-new-phishing-victims. Accessed June 2022
Cision: Phishing in a pandemic: 1 in 4 Americans received a Covid-19 related phishing email. https://www.prnewswire.com/news-releases/phishing-in-a-pandemic-1-in-4-americans-received-a-covid-19-related-phishing-email-301134037.html (2021). Accessed June 2022
Security Boulevard: Phishing statistics: the 29 latest phishing stats to know in 2020. https://securityboulevard.com/2020/04/phishing-statistics-the-29-latest-phishing-stats-to-know-in-2020/. Accessed June 2022
APWG: Phishing activity trends report-1st quarter 2020. https://docs.apwg.org/reports/apwg_trends_report_q1_2020.pdf?_ga=2.30422460.2018635328.1665064249-1448730527.1654753557 &_gl=1*a4rx10*_ga*MTQ0ODczMDUyNy4xNjU0NzUzNTU3*_ga_55RF0RHXSR*MTY2NTA2NDI0OC4xNS4xLjE2NjUwNjQ1MDYuMC4wLjA. Accessed April 2022
Stu Sjouwerman: Q1 2020 coronavirus-related phishing email attacks are up 600%. https://blog.knowbe4.com/q1-2020-coronavirus-related-phishing-email-attacks-are-up-600. Accessed 15 Jan 2022
FBI: Internet crime report. https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf. Accessed 16 Feb 2022
Jakobsson, M., Myers, S.: Phishing and Countermeasures: Understanding the Increasing Problem of Electronic Identity Theft. Wiley, New York (2006)
Ollmann, G.: The phishing guide understanding & preventing phishing attacks. NGS Software Insight Security Research (2004)
Ramzan, Z.: Phishing Attacks and Countermeasures, pp. 433–448. Springer, Berlin (2010)
Khonji, M., Iraqi, Y., Jones, A.: Phishing detection: a literature survey. IEEE Commun. Surv. Tutor. 15(4), 2091–2121 (2013)
Almomani, A., Gupta, B.B., Atawneh, S., Meulenberg, A., Almomani, E.: A survey of phishing email filtering techniques. IEEE Commun. Surv. Tutor. 15(4), 2070–2090 (2013)
Mohammad, R.M., Thabtah, F., McCluskey, L.: Tutorial and critical analysis of phishing websites methods. Comput. Sci. Rev. 17, 1–24 (2015)
Tewari, A., Jain, A.K., Gupta, B.B.: Recent survey of various defense mechanisms against phishing attacks. J. Inf. Priv. Secur. 12(1), 3–13 (2016)
Varshney, G., Misra, M., Atrey, P.K.: A survey and classification of web phishing detection schemes. Secur. Commun. Netw. 9(18), 6266–6284 (2016)
Aleroud, A., Zhou, L.: Phishing environments, techniques, and countermeasures: A survey. Comput. Secur. 68, 160–196 (2017)
Gupta, B.B., Tewari, A., Jain, A.K., Agrawal, D.P.: Fighting against phishing attacks: state of the art and future challenges. Neural Comput. Appl. 28(12), 3629–3654 (2017)
Dou, Z., Khalil, I., Khreishah, A., Al-Fuqaha, A., Guizani, M.: Systematization of knowledge (SOK): a systematic review of software-based web phishing detection. IEEE Commun. Surv. Tutor. 19(4), 2797–2819 (2017)
Chiew, K.L., Yong, K.S.C., Tan, C.L.: A survey of phishing attacks: their types, vectors and technical approaches. Expert Syst. Appl. 106, 1–20 (2018)
Qabajeh, I., Thabtah, F., Chiclana, F.: A recent review of conventional vs. automated cybersecurity anti-phishing techniques. Comput. Sci. Rev. 29, 44–55 (2018)
Das, A., Baki, S., El Aassal, A., Verma, R., Dunbar, A.: Sok: a comprehensive reexamination of phishing research from the security perspective. IEEE Commun. Surv. Tutor. 22(1), 671–708 (2019)
Akinyelu, A.A.: Machine learning and nature inspired based phishing detection: a literature survey. Int. J. Artif. Intell. Tools 28(05), 1930002 (2019)
Alabdan, R.: Phishing attacks survey: types, vectors, and technical approaches. Future Internet 12(10), 168 (2020)
Gangavarapu, T., Jaidhar, C.D., Chanduka, B.: Applicability of machine learning in spam and phishing email filtering: review and approaches. Artif. Intell. Rev. 53(7), 5019–5081 (2020)
Vijayalakshmi, M., Shalinie, S.M., Yang, M.H., Meenakshi, U.R.: Web phishing detection techniques: a survey on the state-of-the-art, taxonomy and future directions. IET Netw. 9(5), 235–246 (2020)
Lee, J., Lee, Y., Lee, D., Kwon, H., Shin, D.: Classification of attack types and analysis of attack methods for profiling phishing mail attack groups. IEEE Access 9, 80866–80872 (2021)
Alkhalil, Z., Hewage, C., Nawaf, L., Khan, I.: Phishing attacks: a recent comprehensive study and a new anatomy. Front. Comput. Sci. 3, 563060 (2021)
Jain, A.K., Gupta, B.B.: A survey of phishing attack techniques, defence mechanisms and open research challenges. Enterp. Inf. Syst. 16(4), 527–565 (2022)
Al-Qahtani, A.F., Cresci, S.: The COVID-19 scamdemic: a survey of phishing attacks and their countermeasures during COVID-19. IET Inf. Secur. 16(5), 324–345 (2022)
Basit, A., Zafar, M., Liu, X., Javed, A.R., Jalil, Z., Kifayat, K.: A comprehensive survey of ai-enabled phishing attacks detection techniques. Telecommun. Syst. 76(1), 139–154 (2021)
Salloum, S., Gaber, T., Vadera, S., Sharan, K.: A systematic literature review on phishing email detection using natural language processing techniques. IEEE Access (2022)
Abdillah, R., Shukur, Z., Mohd, M., Murah, M.Z.: A systematic literature review on phishing classification techniques . IEEE Access (2022)
Rekouche, K.: Early phishing. arXiv preprint arXiv:1106.4692 (2011)
BBC News: Twitter hack: staff tricked by phone spear-phishing scam. https://www.bbc.com/news/technology-53607374. Accessed Jan 2022
Twitter: An update on our security incident. https://blog.twitter.com/en_us/topics/company/2020/an-update-on-our-security-incident (2020). Accessed Jan 2022
CNBC: How this scammer used phishing emails to steal over \$100 million from google and facebook. https://www.cnbc.com/2019/03/27/phishing-email-scam-stole-100-million-from-facebook-and-google.html (2019). Accessed Jan 2022
Reuters: Austria’s facc, hit by cyber fraud, fires CEO. https://www.reuters.com/article/us-facc-ceo-idUSKCN0YG0ZF (2016). Accessed Jan 2022
SecurityIntelligence: Ibm uncovers global phishing campaign targeting the covid-19 vaccine cold chain. https://securityintelligence.com/posts/ibm-uncovers-global-phishing-covid-19-vaccine-cold-chain/. Accessed Jan 2022
Weider, D.Yu., Nargundkar, S., Tiruthani, N.: A phishing vulnerability analysis of web based systems. In: 2008 IEEE Symposium on Computers and Communications, pp. 326–331. IEEE (2008)
Nazah, S., Huda, S., Abawajy, J., Hassan, M.M.: Evolution of dark web threat analysis and detection: a systematic approach. IEEE Access 8, 171796–171819 (2020)
Bates, R.A.: Tracking lone wolf terrorists. J. Public Prof. Sociol. 8(1), 6 (2016)
Weimann, G.: Going dark: terrorism on the dark web. Stud. Conf. Terror. 39(3), 195–206 (2016)
E-ISAC and SANS: Analysis of the cyber attack on the Ukrainian power grid. https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2016/05/20081514/E-ISAC_SANS_Ukraine_DUC_5.pdf. Accessed Jan 2022
Verizon: Dbir:data breach investigations report. https://www.verizon.com/business/resources/Tcd0/reports/dbir/2022-data-breach-investigations-report-dbir.pdf (2022). Accessed Dec 2022
SOPHOS: The state of ransomware 2022. https://assets.sophos.com/X24WTUEQ/at/4zpw59pnkpxxnhfhgj9bxgj9/sophos-state-of-ransomware-2022-wp.pdf. Accessed Oct 2022
Hull, G., John, H., Arief, B.: Ransomware deployment methods and analysis: views from a predictive model and human responses. Crime Sci. 8(1), 1–22 (2019)
Damopoulos, D., Kambourakis, G., Gritzalis, S.: From keyloggers to touchloggers: take the rough with the smooth. Comput. Secur. 32, 102–114 (2013)
Statista: Number of smartphone subscriptions worldwide from 2016 to 2021, with forecasts from 2022 to 2027. https://www.statista.com/statistics/330695/number-of-smartphone-users-worldwide/ (2022). Accessed June 2022
APWG: Phishing activity trends report-2nd quarter 2022. https://docs.apwg.org/reports/apwg_trends_report_q2_2022.pdf?_ga=2.45552807.263073049.1665252062-1448730527.1654753557 &_gl=1*14k5jc7*_ga*MTQ0ODczMDUyNy4xNjU0NzUzNTU3*_ga_55RF0RHXSR*MTY2NTI1ODU1NS4xOS4xLjE2NjUyNTg1NTkuMC4wLjA. Accessed April 2022
Diksha Goel and Ankit Kumar Jain: Mobile phishing attacks and defence mechanisms: state of art and open research challenges. Comput. Secur. 73, 519–544 (2018)
Jain, A.K., Debnath, N., Jain, A.K.: APuML: an efficient approach to detect mobile phishing webpages using machine learning. Wirel. Pers. Commun. 125(4), 3227–3248 (2022)
Shahriar, H., Klintic, T., Clincy, V., et al.: Mobile phishing attacks and mitigation techniques. J. Inf. Secur. 6(03), 206 (2015)
Felt, A.P., Wagner, D.: Phishing on mobile devices (2011)
Business2Community: SMS marketing: texting your way to success. https://www.business2community.com/digital-marketing/sms-marketing-texting-your-way-to-success-02388639. Accessed June 2022
Mishra, S., Soni, D.: Smishing detector: a security model to detect smishing through SMS content analysis and URL behavior analysis. Futur. Gener. Comput. Syst. 108, 803–815 (2020)
Jakobsson, M.: The human factor in phishing. Privacy Security of Consumer Information (2007)
Singh, H.P., Singh, S., Singh, J., Khan, S.A.: VoIP: state of art for global connectivity—a critical review. J. Netw. Comput. Appl. 37, 365–379 (2014)
Mustafa, H., Wenyuan, X., Sadeghi, A.-R., Schulz, S.: End-to-end detection of caller id spoofing attacks. IEEE Trans. Depend. Secure Comput. 15(3), 423–436 (2016)
DENSO WAVE INCORPORATED. History of QR code. https://www.qrcode.com/en/history/. Accessed Dec 2021
Lin, P.-Y., Chen, Y.-H.: High payload secret hiding technology for QR codes. EURASIP J. Image Video Process. 2017(1), 1–8 (2017)
Dabrowski, A., Krombholz, K., Ullrich, J., Weippl, E.R.: QR inception: barcode-in-barcode attacks. In: Proceedings of the 4th ACM Workshop on Security and Privacy in Smartphones & Mobile Devices, pp. 3–10 (2014)
Vidas, T., Owusu, E., Wang, S., Zeng, C., Cranor, L.F., Christin, N.: Qrishing: the susceptibility of smartphone users to QR code phishing attacks. In: International Conference on Financial Cryptography and Data Security, pp. 52–69. Springer (2013)
Focardi, R., Luccio, F.L., Wahsheh, H.A.M.: Security threats and solutions for two-dimensional barcodes: a comparative study. In: Computer and Network Security Essentials, pp. 207–219. Springer (2018)
Verizon: Dbir:data breach investigations report. https://www.verizon.com/business/resources/reports/2020-data-breach-investigations-report.pdf (2020). Accessed Dec 2021
PhishLabs: Social media attacks doubled in 2021 according to latest phishlabs report. https://www.phishlabs.com/news/social-media-attacks-doubled-in-2021-according-to-latest-phishlabs-report/ (2022). Accessed 3 Sept 2022
Jagatic, T.N., Johnson, N.A., Jakobsson, M., Menczer, F.: Social phishing. Commun. ACM 50(10), 94–100 (2007)
Cisco: Cybersecurity threat trends: phishing, crypto top the list. https://learn-umbrella.cisco.com/ebook-library/2021-cyber-security-threat-trends-phishing-crypto-top-the-list (2021). Accessed 3 Sept 2022
Avanan: 1h cyber attack report. https://www.avanan.com/hubfs/Content/Collateral/1H-Cyber-Attack-Report.pdf (2021). Accessed 3 Sept 2022
Statista: Number of internet and social media users worldwide as of July 2022. https://www.statista.com/statistics/617136/digital-population-worldwide/ (2022). Accessed 3 Sept 2022
Statista: 16% of all facebook accounts are fake or duplicates. https://www.statista.com/chart/20685/duplicate-and-false-facebook-accounts/ (2020). Accessed 20 Aug 2022
Song, Y., Yang, C., Gu, G.: Who is peeping at your passwords at starbucks? To catch an evil twin access point. In: 2010 IEEE/IFIP International Conference on Dependable Systems & Networks (DSN), pp. 323–332. IEEE (2010)
Atzori, L., Iera, A., Morabito, G.: The internet of things: a survey. Comput. Netw. 54(15), 2787–2805 (2010)
Sharma, R., Mahapatra, R. P., Sharma, N.: The internet of things and its applications in cyber security. In: A Handbook of Internet of Things in Biomedical and Cyber Physical System, pp. 87–108 (2020)
Nirmal, K., Janet, B., Kumar, R.: Analyzing and eliminating phishing threats in IoT, network and other web applications using iterative intersection. Peer-to-Peer Netw. Appl. 14, 2327–2339 (2021)
Tewari, A., Gupta, B.B.: Security, privacy and trust of different layers in internet-of-things (IoTs) framework. Future Gener. Comput. Syst. 108, 909–920 (2020)
PaloAlto Networks. 2020 unit 42 IoT threat report. https://start.paloaltonetworks.com/unit-42-iot-threat-report. Accessed July 2023
Caputo, D.D., Pfleeger, S.L., Freeman, J.D., Johnson, M.E.: Going spear phishing: exploring embedded training and awareness. IEEE Secur. Priv. 12(1), 28–38 (2013)
Parmar, B.: Protecting against spear-phishing. Comput. Fraud Secur. 2012(1), 8–11 (2012)
Wang, J., Herath, T., Chen, R., Vishwanath, A., Rao, H.R.: Research article phishing susceptibility: an investigation into the processing of a targeted spear phishing email. IEEE Trans. Prof. Commun. 55(4), 345–362 (2012)
Symantec: Istr:internet security threat report. https://docs.broadcom.com/doc/istr-24-2019-en (2019). Accessed 23 Apr 2022
Kwak, Y., Lee, S., Damiano, A., Vishwanath, A.: Why do users not report spear phishing emails? Telemat. Inf. 48, 101343 (2020)
Al-Musib, N.S., Al-Serhani, F.M., Humayun, M., Jhanjhi, N.Z.: Business email compromise (BEC) attacks. Mater. Today Proc. (2021)
FBI. Public service announcement. https://www.ic3.gov/Media/Y2022/PSA220504 (2022). Accessed 23 Apr 2022
FBI. Public service announcement. https://www.ic3.gov/Media/Y2022/PSA220216 (2022). Accessed 23 Apr 2022
Le Page, S., Jourdan, G.-V.: Victim or attacker? A multi-dataset domain classification of phishing attacks. In: 2019 17th International Conference on Privacy, Security and Trust (PST), pp. 1–10. IEEE (2019)
Corona, I., Biggio, B., Contini, M., Piras, L., Corda, R., Mereu, M., Mureddu, G., Ariu, D., Roli, F.: Deltaphish: detecting phishing webpages in compromised websites. In: European Symposium on Research in Computer Security, pp. 370–388. Springer (2017)
Moore, T., Clayton, R.: Examining the impact of website take-down on phishing. In: Proceedings of the anti-phishing working groups 2nd annual eCrime researchers summit, pp. 1–13 (2007)
PhishLabs. Most phishing attacks use compromised domains and free hosting. https://www.phishlabs.com/blog/most-phishing-attacks-use-compromised-domains-and-free-hosting/ (2021). Accessed 14 Feb 2022
Pope, M.B., Warkentin, M., Mutchler, L.A., Luo, X.R.: The domain name system-past, present, and future. Commun. Assoc. Inf. Syst. 30(1), 21 (2012)
Kim, H., Huh, J.H.: Detecting DNS-poisoning-based phishing attacks from their network performance characteristics. Electron. Lett. 47(11), 656–658 (2011)
Perdisci, R., Antonakakis, M., Luo, X., Lee, W.: WSEC DNS: protecting recursive DNS resolvers from poisoning attacks. In: 2009 IEEE/IFIP International Conference on Dependable Systems & Networks, pp. 3–12. IEEE (2009)
Schiller, C.A., Binkley, J., Harley, D., Evron, G., Bradley, T., Willems, C., Cross, M.: Botnets overview. In: Botnets, pp. 29–75. Syngress (2007)
Vural, I., Venter, H.: Detecting mobile spam botnets using artificial immune systems. In: IFIP International Conference on Digital Forensics, pp. 183–192. Springer (2011)
Negash, N., Che, X.: An overview of modern botnets. Inf. Secur. J. Glob. Perspect. 24(4–6), 127–132 (2015)
Milletary, J., CERT Coordination Center.: Technical trends in phishing attacks. Retrieved December 1(2007):3 (2005)
Gupta, S., Gupta, B.B.: Cross-site scripting (XSS) attacks and defense mechanisms: classification and state-of-the-art. Int. J. Syst. Assur. Eng. Manag. 8(1), 512–530 (2017)
Ruderman, J.: The same origin policy. http://www.mozilla.org/projects/security/components/same-origin.html (2001)
Patchstack. State of wordpress security in 2021. https://patchstack.com/wp-content/uploads/2022/03/Patchstack-%E2%80%93-State-Of-WordPress-Security-In-2021.pdf (2022). Accessed 15 May 2022
Nagar, N., Suman, U.: Prevention, detection, and recovery of CSRF attack in online banking system. In: Online banking security measures and data protection, pp. 172–188. IGI Global (2017)
Zhang, J., Hu, H., Huo, S.: A browser-based cross site request forgery detection model. J. Phys. Conf. Ser. 1738, 012073 (2021)
Gelernter, N., Herzberg, A.: Tell me about yourself: the malicious captcha attack. In: Proceedings of the 25th International Conference on World Wide Web, pp. 999–1008 (2016)
Yalçın, N., Köse, U.: What is search engine optimization: Seo? Procedia Soc. Behav. Sci. 9, 487–493 (2010)
Chaudhry, J.A., Chaudhry, S.A., Rittenhouse, R.G.: Phishing attacks and defenses. Int. J. Secur. Appl. 10(1), 247–256 (2016)
Nagunwa, T.: Behind identity theft and fraud in cyberspace: the current landscape of phishing vectors. Int. J. Cyber-Secur. Digit. Forensics IJCSDF 3(1), 72–83 (2014)
van der Toorn, O., Müller, M., Dickinson, S., Hesselman, C., Sperotto, A., van Rijswijk-Deij, R.: Addressing the challenges of modern DNS a comprehensive tutorial. Comput. Sci. Rev. 45, 100469 (2022)
Wang, Y.-M., Beck, D., Wang, J., Verbowski, C., Daniels, B.: Strider typo-patrol: discovery and analysis of systematic typo-squatting. SRUTI 6(31–36), 2–2 (2006)
Spaulding, J., Nyang, D., Mohaisen, A.: Understanding the effectiveness of typosquatting techniques. In: Proceedings of the fifth ACM/IEEE Workshop on Hot Topics in Web Systems and Technologies, pp. 1–8 (2017)
Moore, T., Edelman, B.: Measuring the perpetrators and funders of typosquatting. In: International Conference on Financial Cryptography and Data Security, pp. 175–191. Springer (2010)
Dinaburg, A.: Bitsquatting: Dns hijacking without exploitation (2011)
Nikiforakis, N., Balduzzi, M., Desmet, L., Piessens, F., Joosen, W.: Soundsquatting: uncovering the use of homophones in domain squatting. In: International Conference on Information Security, pp. 291–308. Springer (2014)
Holgers, T., Watson, D.E., Gribble, S.D.: Cutting through the confusion: a measurement study of homograph attacks. In: USENIX Annual Technical Conference, General Track, pp. 261–266 (2006)
Kintis, P., Miramirkhani, N., Lever, C., Chen, Y., Romero-Gómez, R., Pitropakis, N., Nikiforakis, N., Antonakakis, M.: Hiding in plain sight: a longitudinal study of combosquatting abuse. In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, pp. 569–586 (2017)
Zeng, Y., Zang, T., Zhang, Y., Chen, X., Wang, Y.: A comprehensive measurement study of domain-squatting abuse. In: ICC 2019-2019 IEEE International Conference on Communications (ICC), pp. 1–6. IEEE (2019)
Nikiforakis, N., Van Acker, S., Meert, W., Desmet, L., Piessens, F., Joosen, W.: Bitsquatting: exploiting bit-flips for fun, or profit? In: Proceedings of the 22nd international conference on World Wide Web, pp. 989–998 (2013)
Rader, M., Rahman, S.: Exploring historical and emerging phishing techniques and mitigating the associated security risks. arXiv preprint arXiv:1512.00082 (2015)
Skolka, P., Staicu, C.-A., Pradel, M.: Anything to hide? Studying minified and obfuscated code in the web. In: The World Wide Web Conference, pp. 1735–1746 (2019)
APWG. Phishing activity trends report-4th quarter 2020. https://docs.apwg.org/reports/apwg_trends_report_q4_2020.pdf?_ga=2.52213802.263073049.1665252062-1448730527.1654753557 &_gl=1*1imdh26*_ga*MTQ0ODczMDUyNy4xNjU0NzUzNTU3*_ga_55RF0RHXSR*MTY2NTI1MjA2MS4xOC4wLjE2NjUyNTIzNTMuMC4wLjA (2021). Accessed April 2022
Sarker, S., Jueckstock, J., Kapravelos, A.: Hiding in plain site: detecting javascript obfuscation through concealed browser api usage. In: Proceedings of the ACM Internet Measurement Conference, pp. 648–661 (2020)
Romano, A., Lehmann, D., Pradel, M., Wang, W.: Wobfuscator: Obfuscating javascript malware via opportunistic translation to webassembly. In: Proceedings of the 2022 IEEE Symposium on Security and Privacy (S &P 2022), pp. 1101–1116 (2022)
Bagchi, K., Udo, G.: An analysis of the growth of computer and internet security breaches. Commun. Assoc. Inf. Syst. 12(1), 46 (2003)
Loughran, D.T., Salih, M.K., Subburaj, V.H.: All about SQL injection attacks. J. Colloq. Inf. Syst. Secur. Educ. 6, 24–24 (2018)
Patil, D.R., Patil, J.B.: Survey on malicious web pages detection techniques. Int. J. u-and e-Serv. Sci. Technol. 8(5), 195–206 (2015)
Conti, M., Dragoni, N., Lesyk, V.: A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 18(3), 2027–2051 (2016)
Sahani, R., Randhawa, S.: Clickjacking: Beware of clicking. Wirel. Pers. Commun. 121(4), 2845–2855 (2021)
Shahriar, H., Devendran, V.K.: Classification of clickjacking attacks and detection techniques. Inf. Secur. J. A Glob. Perspect. 23(4–6), 137–147 (2014)
Sinha, R., Uppal, D., Singh, D., Rathi, R.: Clickjacking: existing defenses and some novel approaches. In: 2014 International Conference on Signal Propagation and Computer Technology (ICSPCT 2014), pp 396–401. IEEE (2014)
Akhawe, D., He, W., Li, Z., Moazzezi, R., Song, D.: Clickjacking revisited: a perceptual view of \(\{\)UI\(\}\) security. In: 8th USENIX workshop on offensive technologies (WOOT 14) (2014)
Stone, P.: Next generation clickjacking. BlackHat Europe (2010)
Huang, L.-S., Moshchuk, A., Wang, H.J., Schecter, S., Jackson, C.: Clickjacking: attacks and defenses. In: 21st USENIX Security Symposium (USENIX Security 12), pp. 413–428 (2012)
Gupta, B.B., Yadav, K., Razzak, I., Psannis, K., Castiglione, A., Chang, X.: A novel approach for phishing URLs detection using lexical based machine learning in a real-time environment. Comput. Commun. 175, 47–57 (2021)
Jain, A.K., Gupta, B.B.: A machine learning based approach for phishing detection using hyperlinks information. J. Amb. Intell. Hum. Comput. 10(5), 2015–2028 (2019)
Ramana, A.V., Rao, K.L., Rao, R.S.: Stop-phish: an intelligent phishing detection method using feature selection ensemble. Soc. Netw. Anal. Min. 11(1), 1–9 (2021)
Rao, R.S., Pais, A.R., Anand, P.: A heuristic technique to detect phishing websites using TWSVM classifier. Neural Comput. Appl. 33(11), 5733–5752 (2021)
Rao, R.S., Pais, A.R.: Jail-phish: an improved search engine based phishing detection system. Comput. Secur. 83, 246–267 (2019)
Suri, R.K., Tomar, D.S., Sahu, D.R.: An approach to perceive tabnabbing attack. Int. J. Sci. Technol. Res. 1(6), 90–94 (2012)
Raskin, A.: Tabnabbing: a new type of phishing attack. línea. http://www.azarask.in/blog/post/a-new-type-of-phishing-attack/. [Último acceso: 10 12 2013] (2010)
Kolsek, M.: Session fixation vulnerability in web-based applications. ACROS Security. http://www.acrossecurity.com/papers/sessionfixation.pdf (2002)
Kaspersky. Phishing-kit market: what’s inside “off-the-shelf” phishing packages. https://securelist.com/phishing-kit-market-whats-inside-off-the-shelf-phishing-packages/106149/ (2022). Accessed 25 Aug 2022
Kaspersky. How scammers are creating thousands of fake pages using phishing kits. https://usa.kaspersky.com/about/press-releases/2022_quick-cheap-and-dangerous-how-scammers-are-creating-thousands-of-fake-pages-using-phishing-kits (2022). Accessed 25 Aug 2022
Bahnsen, A.C., Torroledo, I., Camacho, L.D., Villegas, S.: Deepphish: simulating malicious AI. In: 2018 APWG Symposium on Electronic Crime Research (eCrime), pp. 1–8 (2018)
Group-IB. https://www.group-ib.com/media-center/press-releases/phishing-kits-2022/ (2023). Accessed Sep 2023
CNBC. https://www.cnbc.com/2023/01/07/phishing-attacks-are-increasing-and-getting-more-sophisticated.html (2023). Accessed July 2023
Dupuis, M., Geiger, T., Slayton, M., Dewing, F.: The use and non-use of cybersecurity tools among consumers: do they want help? In: Proceedings of the 20th Annual SIG Conference on Information Technology Education, pp. 81–86 (2019)
SECTRIO. https://sectrio.com/iot-security-reports/2023-ot-iot-threat-landscape-report/ (2023). Accessed July 2023
Proofpoint. https://www.proofpoint.com/sites/default/files/threat-reports/pfpt-us-tr-state-of-the-phish-2023.pdf (2023). Accessed Sep 2023
Check Point. https://www.avanan.com/hubfs/2022-Defender-Report/WP_Avanan_Keeping_Your_Emails_Secure_Who_Does_It_Best.pdf (2022). Accessed Sep 2023
Abnormal Society. https://cdn2.assets-servd.host/gifted-zorilla/production/files/Read-Alert-Data-Shows-28-of-BEC-Attacks-Opened-by-Employees.pdf?dm=1675457683 (2023). Accessed Sep 2023
AKAMAI. https://www.akamai.com/blog/security/over-25-percent-of-malicious-javascript-is-being-obfuscated (2021). Accessed July 2023
AKAMAI. https://www.akamai.com/blog/security/web-application-and-api-protection-from-sql-injection-to-magecart (2020). Accessed July 2023
COMPARITECH. https://www.comparitech.com/blog/information-security/botnet-statistics/ (2022). Accessed July 2023
ZedNET. https://www.zdnet.com/article/clickjacking-scripts-found-on-613-popular-sites-academics-say// (2019). Accessed July 2023
F5 Labs. https://www.f5.com/content/dam/f5-labs-v2/article/articles/threats/22--2020-oct-dec/20201110_2020_phishing_report/F5Labs-2020-Phishing-and-Fraud-Report.pdf (2020). Accessed July 2023
CheckPoint. https://blog.checkpoint.com/security/social-networks-most-likely-to-be-imitated-by-criminal-groups-with-linkedin-now-accounting-for-half-of-all-phishing-attempts-worldwide/ (2022). Accessed July 2023
Rao, R.S., Pais, A.R.: An enhanced blacklist method to detect phishing websites. In: International Conference on Information Systems Security, pp. 323–333. Springer (2017)
Bell, S., Komisarczuk, P.: An analysis of phishing blacklists: Google safe browsing, openphish, and phishtank. In: Proceedings of the Australasian Computer Science Week Multiconference, pp. 1–11 (2020)
Prakash, P., Kumar, M., Kompella, R R., Gupta, M.: Phishnet: predictive blacklisting to detect phishing attacks. In: 2010 Proceedings IEEE INFOCOM, pp. 1–5. IEEE (2010)
Han, W., Cao, Y., Bertino, E., Yong, J.: Using automated individual white-list to protect web digital identities. Expert Syst. Appl. 39(15), 11861–11869 (2012)
Jain, A.K., Gupta, B.B.: A novel approach to protect against phishing attacks at client side using auto-updated white-list. EURASIP J. Inf. Secur. 2016(1), 1–11 (2016)
Azeez, N.A., Misra, S., Margaret, I.A., Fernandez-Sanz, L., et al.: Adopting automated whitelist approach for detecting phishing attacks. Comput. Secur. 108, 102328 (2021)
Sheng, S., Wardman, B., Warner, G., Hong, J., Zhang, C.: An empirical analysis of phishing blacklists. Lorrie Cranor (2009)
Sahingoz, O.K., Buber, E., Demir, O., Diri, B.: Machine learning based phishing detection from URLs. Expert Syst. Appl. 117, 345–357 (2019)
Jain, A.K., Gupta, B.B.: Phish-safe: URL features-based phishing detection system using machine learning. In: Cyber Security, pp. 467–474. Springer (2018)
Ali, M.S., Jain, A.K.: Efficient feature selection approach for detection of phishing URL of Covid-19 era. In: International Conference on Cyber Security, Privacy and Networking, pp. 45–56. Springer (2021)
Jain, A.K., Parashar, S., Katare, P., Sharma, I.: Phishskape: a content based approach to escape phishing attacks. Procedia Comput. Sci. 171, 1102–1109 (2020)
Rao, R.S., Umarekar, A., Pais, A.R.: Application of word embedding and machine learning in detecting phishing websites. Telecommun. Syst. 1–13 (2022)
Varshney, G., Misra, M., Atrey, P.K.: A phish detector using lightweight search features. Comput. Secur. 62, 213–228 (2016)
Jain, A.K., Gupta, B.B.: Two-level authentication approach to protect from phishing attacks in real time. J. Amb. Intell. Hum. Comput. 9(6), 1783–1796 (2018)
Gupta, B.B., Jain, A.K.: Phishing attack detection using a search engine and heuristics-based technique. J. Inf. Technol. Res. JITR 13(2), 94–109 (2020)
Jain, A.K., Gupta, B.B.: Towards detection of phishing websites on client-side using machine learning based approach. Telecommun. Syst. 68(4), 687–700 (2018)
Rao, R.S., Pais, A.R.: Detection of phishing websites using an efficient feature-based machine learning framework. Neural Comput. Appl. 31(8), 3851–3873 (2019)
Jain, A.K., Gupta, B.B., Kaur, K., Bhutani, P., Alhalabi, W., Almomani, A.: A content and URL analysis-based efficient approach to detect smishing SMS in intelligent systems. Int. J. Intell. Syst. 37(12), 11117–11141 (2022)
Mao, J., Tian, W., Li, P., Wei, T., Liang, Z.: Phishing-alarm: robust and efficient phishing detection via page component similarity. IEEE Access 5, 17020–17030 (2017)
Chen, J.-L., Ma, Y.-W., Huang, K.-L.: Intelligent visual similarity-based phishing websites detection. Symmetry 12(10), 1681 (2020)
Routhu Srinivasa Rao and Alwyn Roshan Pais: Two level filtering mechanism to detect phishing sites using lightweight visual similarity approach. J. Ambient. Intell. Humaniz. Comput. 11(9), 3853–3872 (2020)
Ahmet Selman Bozkir and Murat Aydos: Logosense: a companion hog based logo detection scheme for phishing web page and e-mail brand recognition. Comput. Secur. 95, 101855 (2020)
Phishtank. https://phishtank.org/. Accessed July 2023
Ahrefs. https://ahrefs.com/. Accessed July 2023
Similarweb. https://www.similarweb.com/. Accessed July 2023
Majestic million. https://majestic.com/reports/majestic-million. Accessed July 2023
https://github.com/ebubekirbbr/pdd/tree/master/input. Accessed July 2023
https://www.unb.ca/cic/datasets/url-2016.html. Accessed July 2023
Vrbančič, G.: Phishing websites dataset. Mendeley Data (2020)
Jpcert/cc. https://github.com/JPCERTCC/phishurl-list/. Accessed July 2023
Lee, L.-H., Lee, K.-C., Chen, H.-H., Tseng, Y.-H.: Poster: Proactive blacklist update for anti-phishing. In: Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, pp. 1448–1450 (2014)
Barraclough, P.A., Fehringer, G., Woodward, J.: Intelligent cyber-phishing detection for online. Comput. Secur. 104, 102123 (2021)
Karim, A., Shahroz, M., Mustofa, K., Belhaouari, S.B., Joga, S.R.K.: Phishing detection system through hybrid machine learning based on URL. IEEE Access 11, 36805–36822 (2023)
Funding
No funding was received for conducting this study and the authors have no financial or proprietary interests in any material discussed in this article.
Author information
Authors and Affiliations
Contributions
RG wrote the whole manuscript. MC and NT provided valuable inputs and reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Goenka, R., Chawla, M. & Tiwari, N. A comprehensive survey of phishing: mediums, intended targets, attack and defence techniques and a novel taxonomy. Int. J. Inf. Secur. 23, 819–848 (2024). https://doi.org/10.1007/s10207-023-00768-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-023-00768-x