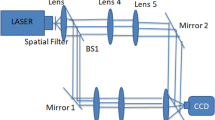
Abstract
In practical optical security systems we must consider various circumstances for reading and decrypting encrypted holograms. Binarization of the hologram is best suited for such applications because of the ease of handling encrypted data. However, the decrypted image is greatly degraded by binarization. Therefore, optimization of a binary hologram is essential in using such a technique. In this paper, we propose a fast optimization method of a binary encrypted hologram to obtain a good reconstruction based on the error correction algorithm. In the proposed method, multiple pixels of the binary hologram are simultaneously flipped for the optimization according to the priority for the correction. The time for the optimization is only 3% of that of the simulated annealing method.
Similar content being viewed by others
References
B. Javidi J. L. Horner (1994) Opt. Eng. 33 1752 Occurrence Handle10.1117/12.170736 Occurrence Handle1994OptEn..33.1752J
P. Refregier B. Javidi (1995) Opt. Lett. 90 767 Occurrence Handle1995OptL...20..767R Occurrence Handle10.1364/OL.20.000767
B. Javidi (1997) Phys. Today 50 27
Y. Kobayashi H. Toyoda (1999) Opt. Eng. 38 1250 Occurrence Handle10.1117/1.602269
H.-G. Yang E.-S. Kim (1996) Opt. Eng. 35 2473 Occurrence Handle10.1117/1.600851 Occurrence Handle1996OptEn..35.2473Y
S. Kirkpatrick C. D. Gelatt SuffixJr. M. P. Vecchi (1983) Science 220 671 Occurrence Handle10.1126/science.220.4598.671 Occurrence Handle1983Sci...220..671K Occurrence Handle702485
J. Ohtsubo K. Nakajima (1991) Opt. Commun. 86 265 Occurrence Handle10.1016/0030-4018(91)90003-V Occurrence Handle1991OptCo..86..265O
R. K. Battig C. C. Guest S. R. Schaefer D. J. Toms (1992) Appl. Opt. 31 1059 Occurrence Handle1992ApOpt..31.1059B Occurrence Handle10.1364/AO.31.001059
M. A. Seldowitz J. P. Allenbach D. W. Sweeney (1987) Appl. Opt. 26 2788 Occurrence Handle1987ApOpt..26.2788S
M. Yamazaki J. Ohtsubo (2001) Opt. Eng. 40 132 Occurrence Handle10.1117/1.1334947 Occurrence Handle2001OptEn..40..132Y
C. S. Weaver J. W. Goodman (1966) Appl. Opt. 5 1248 Occurrence Handle1966ApOpt...5.1248W
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Nakayama, K., Ohtsubo, J. Fast Optimization of Binary Encrypted Hologram Based on Error Correction Method in Optical Security Systems. OPT REV 14, 290–296 (2007). https://doi.org/10.1007/s10043-007-0290-z
Received:
Accepted:
Issue Date:
DOI: https://doi.org/10.1007/s10043-007-0290-z