Abstract
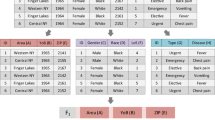
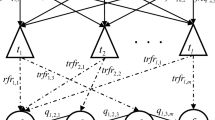
Database fragmentation has been used as a protection mechanism of database’s privacy by allocating attributes with sensitive associations into separate data fragments. A typical relational database consists of multiple relations. Thus, fragmentation process is applied to each relation separately in a sequential manner. In other words, the existing database fragmentation approaches regard each relation fragmentation problem as an independent task. When solving a sequence of fragmentation problems, redundant computational resources are consumed when extracting the same fragmentation information and limit the performance of those algorithms. In this paper, a multitasking database fragmentation problem for privacy preservation requirements is formally defined. A multitasking distributed differential evolution algorithm is introduced, including a multitasking distributed framework enriched by two new operators. The introduced framework can help exchange generic and effective allocation information among different database fragmentation problems. A similarity-based alignment operator is proposed to adjust the fragment orders in different database fragmentation solutions. A perturbation-based mutation operator with adaptive mutation strategy selection is designed to sufficiently exchange evolutionary information in the solutions. Experimental results show that the proposed algorithm can outperform other competitors in terms of solution accuracy, convergence speed, and scalability.











Similar content being viewed by others
References
Aggarwal, G., Bawa, M., Ganesan, P., Garcia-Molina, H., Kenthapadi, K., Motwani, R., Srivastava, U., Thomas, D., Xu, Y.: Two can keep a secret: a distributed architecture for secure database services. In: 2005 CIDR Conference (2005)
Attasena, V., Darmont, J., Harbi, N.: Secret sharing for cloud data security: a survey. VLDB J. 26(5), 657–681 (2017). https://doi.org/10.1007/s00778-017-0470-9
Ciriani, V., Di Vimercati, S.D.C., Foresti, S., Jajodia, S., Paraboschi, S., Samarati, P.: Fragmentation and encryption to enforce privacy in data storage. In: European Symposium on Research in Computer Security, pp. 171–186. Springer (2007)
Ciriani, V., Vimercati, S.D.C.D., Foresti, S., Jajodia, S., Paraboschi, S., Samarati, P.: Combining fragmentation and encryption to protect privacy in data storage. ACM Trans. Inf. Syst. Secur. 13(3), 1–33 (2010)
De Capitani di Vimercati, S., Foresti, S., Jajodia, S., Livraga, G., Paraboschi, S., Samarati, P.: Loose associations to increase utility in data publishing. J. Comput. Secur. 23(1), 59–88 (2015)
Feng, L., Huang, Y., Zhou, L., Zhong, J., Gupta, A., Tang, K., Tan, K.C.: Explicit evolutionary multitasking for combinatorial optimization: a case study on capacitated vehicle routing problem. IEEE Trans. Cybern. (2020). https://doi.org/10.1109/tcyb.2019.2962865
Gao, J., Yu, J.X., Jin, R., Zhou, J., Wang, T., Yang, D.: Outsourcing shortest distance computing with privacy protection. VLDB J. 22(4), 543–559 (2013). https://doi.org/10.1007/s00778-012-0304-8
Gao, Z., Pan, Z., Zuo, C., Gao, J., Xu, Z.: An optimized deep network representation of multimutation differential evolution and its application in seismic inversion. IEEE Trans. Geosci. Remote Sens. 57(7), 4720–4734 (2019). https://doi.org/10.1109/tgrs.2019.2892567
Garey, M.R., Johnson, D.S.: Computers and Intractability: A Guide to the Theory of NP-Completeness. W. H. Freeman and Company, New York (1979)
Ge, Y.F., Yu, W.J., Lin, Y., Gong, Y.J., Zhan, Z.H., Chen, W.N., Zhang, J.: Distributed differential evolution based on adaptive mergence and split for large-scale optimization. IEEE Trans. Cybern. 48(7), 2166–2180 (2018). https://doi.org/10.1109/tcyb.2017.2728725
Ge, Y.F., Yu, W.J., Zhan, Z.H., Zhang, J.: Competition-based distributed differential evolution. In: 2018 IEEE Congress on Evolutionary Computation. IEEE (2018). https://doi.org/10.1109/cec.2018.8477758
Ge, Y.F., Cao, J., Wang, H., Zhang, Y., Chen, Z.: Distributed differential evolution for anonymity-driven vertical fragmentation in outsourced data storage. In: 2020 International Conference on Web Information Systems Engineering, pp. 213–226 (2020)
Ge, Y.F., Yu, W.J., Cao, J., Wang, H., Zhan, Z.H., Zhang, Y., Zhang, J.: Distributed memetic algorithm for outsourced database fragmentation. IEEE Trans. Cybern. (2020). https://doi.org/10.1109/tcyb.2020.3027962
Gupta, A., Ong, Y.S., Feng, L.: Multifactorial evolution: toward evolutionary multitasking. IEEE Trans. Evol. Comput. 20(3), 343–357 (2016). https://doi.org/10.1109/tevc.2015.2458037
Hore, B., Mehrotra, S., Canim, M., Kantarcioglu, M.: Secure multidimensional range queries over outsourced data. VLDB J. 21(3), 333–358 (2011). https://doi.org/10.1007/s00778-011-0245-7
Köhler, J., Jünemann, K., Hartenstein, H.: Confidential database-as-a-service approaches: taxonomy and survey. J. Cloud Comput. 4(1), 1–14 (2015)
Li, J., Yao, W., Zhang, Y., Qian, H., Han, J.: Flexible and fine-grained attribute-based data storage in cloud computing. IEEE Trans. Serv. Comput. 10(5), 785–796 (2017). https://doi.org/10.1109/tsc.2016.2520932
Liaw, R.T., Ting, C.K.: Evolutionary many-tasking based on biocoenosis through symbiosis: a framework and benchmark problems. In: 2017 IEEE Congress on Evolutionary Computation, pp. 2266–2273. IEEE (2017). https://doi.org/10.1109/cec.2017.7969579
Liaw, R.T., Ting, C.K.: Evolutionary manytasking optimization based on symbiosis in biocoenosis. In: Proceedings of the AAAI Conference on Artificial Intelligence, vol. 33, pp. 4295–4303 (2019). https://doi.org/10.1609/aaai.v33i01.33014295
Price, K., Storn, R.M., Lampinen, J.A.: Differential Evolution: A Practical Approach to Global Optimization. Springer, Berlin (2006)
Price, K.V.: Differential evolution. In: Handbook of Optimization, pp. 187–214 (2013)
Rani, K., Sagar, R.K.: Enhanced data storage security in cloud environment using encryption, compression and splitting technique. In: 2017 International Conference on Telecommunication and Networks. IEEE (2017) https://doi.org/10.1109/tel-net.2017.8343557
UbaidurRahman, N.H., Balamurugan, C., Mariappan, R.: A novel DNA computing based encryption and decryption algorithm. Proc. Comput. Sci. 46, 463–475 (2015)
Wang, Y., Yan, Z., Feng, W., Liu, S.: Privacy protection in mobile crowd sensing: a survey. World Wide Web 23(1), 421–452 (2019). https://doi.org/10.1007/s11280-019-00745-2
Xu, X., Xiong, L., Liu, J.: Database fragmentation with confidentiality constraints: a graph search approach. In: 2015 ACM Conference on Data and Application Security and Privacy, pp. 263–270 (2015)
Yu, J., Wang, G., Mu, Y., Gao, W.: An efficient generic framework for three-factor authentication with provably secure instantiation. IEEE Trans. Inf. Forensics Secur. 9(12), 2302–2313 (2014)
Yu, Y., Au, M.H., Ateniese, G., Huang, X., Susilo, W., Dai, Y., Min, G.: Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans. Inf. Forensics Secur. 12(4), 767–778 (2017)
Zheng, L.M., Zhang, S.X., Zheng, S.Y., Pan, Y.M.: Differential evolution algorithm with two-step subpopulation strategy and its application in microwave circuit designs. IEEE Trans. Ind. Inform. 12(3), 911–923 (2016). https://doi.org/10.1109/tii.2016.2535347
Zhou, X.G., Peng, C.X., Liu, J., Zhang, Y., Zhang, G.J.: Underestimation-assisted global-local cooperative differential evolution and the application to protein structure prediction. IEEE Trans. Evol. Comput. 24(3), 536–550 (2019). https://doi.org/10.1109/tevc.2019.2938531
Author information
Authors and Affiliations
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ge, YF., Orlowska, M., Cao, J. et al. MDDE: multitasking distributed differential evolution for privacy-preserving database fragmentation. The VLDB Journal 31, 957–975 (2022). https://doi.org/10.1007/s00778-021-00718-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00778-021-00718-w