Abstract
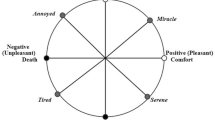
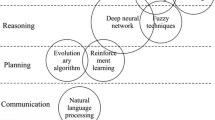
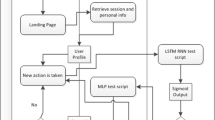
Prediction is a method of detecting a person's behavior toward online buying by evaluating publically available evaluations on the web. Understanding expressive human communication involves a simultaneous examination of speech and gestures since human behavior is communicated through a combination of verbal and nonverbal channels. Machine learning algorithms are utilized in this work to extract evaluations from the net and categorize these into five classes, namely, highly favorable, favorable, neutrality, bad, and strongly negative, for the prediction of human behavior. A person's behavior is analyzed, and the experimental comparison is made to machine learning methodologies. Numerous classifiers are employed on manuscript transcripts in this work to determine the accuracy, exactness, recollection, and f1-score, which are also represented in terms of muddle matrices. In this research studies a new technique is proposed using Ludwig classifier and it has been discovered that deep learning employing the Ludwig classifier achieves near-perfect accuracy about 99.9%. The outcomes are presented to demonstrate the preceding point.









Similar content being viewed by others
References
Alazab M, Venkatraman S, Watters P, Alazab M et al (2011) Zero-day malware detection based on supervised learning algorithms of API call signatures. In: Proceedings of the 9-th Australasian Data Mining Confere (AusDM'11), vol 121. Australian Computer Society Inc., Ballarat, Australia, pp 171–182. https://doi.org/10.5555/2483628.2483648. ISBN: 9781921770029
Alkali Y, Routray I, Whig P (2022) Study of various methods for reliable, efficient and Secured IoT using Artificial Intelligence 1(2):1–7. Available at SSRN 4020364
Anand M, Velu A, Whig P (2022) Prediction of loan behaviour with machine learning models for secure banking. J Comput Sci Eng (JCSE) 3(1):1–13
Arun Velu PW (2021) Impact of Covid Vaccination on the Globe using data analytics. Int J Sustain Dev Comput Sci 3(2):1–13
Asopa P, Purohit P, Nadikattu RR, Whig P (2021) Reducing carbon footprint for sustainable development of smart cities using IoT. In: 2021 Third International Conference on intelligent communication technologies and virtual mobile networks (ICICV), vol 5, pp 361–367
Av-test institute, Germany (2019) https://www.av-test.org/en/statistics/malware/ 2(5): 1–10. Accessed 20 Oct 2019
Bhargav R, Whig P (2021) More insight on data analysis of titanic data set. Int J Sustain Dev Comput Sci 3(4):1–10
Bhatia V, Whig P (2013a) Modeling and simulation of electrical load control system using RF technology. Int J Multidiscipl Sci Eng 4(2):44–47
Bhatia V, Whig P (2013b) A secured dual tune multi frequency-based smart elevator control system. Int J Res Eng Adv Technol 4(1):2319–1163
Chopra G, Whig P (2022a) Energy efficient scheduling for internet of vehicles. Int J Sustain Dev Comput Sci 4(1):1–10
Chopra G, Whig P (2022b) A clustering approach based on support vectors. Int J Mach Learn Sustain Dev 4(1):21–30
Fischer EA (2014) Cybersecurity issues and challenges: in brief. Congr Res Serv 5:1–10
George N, Muiz K, Whig P, Velu A (2021) Framework of perceptive artificial intelligence using natural language processing (PAIN) 1–10. Artif Comput Intell/Publ Online
Gupta BB, Tewari A, Jain AK, Agrawal DP (2017) Fighting against phishing attacks: state of the art and future challenges. Neural Comput Appl 28(12):3629–3654
IBM Security Report (2019) https://www.ibm.com/security/data-breach 2(3):1–10. Accessed 20 Oct 2019
Jiwani N, Gupta K, Whig P (2021) Novel healthcare framework for cardiac arrest with the application of AI using ANN. In: 2021 5th International Conference on information systems and computer networks (ISCON), vol 2, no 5, pp 1–5
Juniper Research (2019) https://www.juniperresearch.com/ 1(2):1–15. Accessed 20 Oct 2019
Li S, Da Xu L, Zhao S (2015) The internet of things: a survey. Inform System Front 17(2):243–259
Mamza ES (2021) Use of AIOT in health system. Int J Sustain Dev Comput Sci 3(4):21–30
McIntosh T, Jang-Jaccard J, Watters P, Susnjak T (2019) The inadequacy of entropy-based ransomware detection. In: International Conference on neural information processing. Springer, New York, pp 181–189
Nadikattu RR, Bhandari R, Whig P (2021) Improved pattern of adaptive rood-pattern search algorithm for motion estimation in video compression. In: Singh J, Kumar S, Choudhury U (eds) Innovations in cyber physical systems, Lecture Notes in Electrical Engineering, vol 788. Springer, Singapore, pp 441–448. https://doi.org/10.1007/978-981-16-4149-7_39
Rainie L, Anderson J, Connolly J (2014) Cyber attacks likely to increase. Digital Life 2025 5(2):1–25
Ruchin CM, Whig P (2015) Design and simulation of dynamic UART using scan path technique (USPT). Int J Electric Electron Comput Sci Eng 10(2):1–14
Sharma A, Kumar A, Whig P (2015) On the performance of CDTA based novel analog inverse low pass filter using 0.35 µm CMOS parameter. Int J Sci Technol Manag 4(1):594–601
Shaw A (2009) Data breach: from notification to prevention using PCI DSS. Colum Soc Probs 43:517–524
Sinha R, Prashar S, Whig P (2015) Effect of output error on fuzzy interface for VDRC of second-order systems. Int J Comput Appl 125(13):11–16
Sun N, Zhang J, Rimba P, Gao S, Zhang LY, Xiang Y (2018) Data-driven cybersecurity incident prediction: a survey. IEEE Commun Surv Tutor 21(2):1744–1772
Velu A, Whig P (2021) Protect personal privacy and wasting time using Nlp: a comparative approach using Ai. Vivekananda J Res 10:42–52
Velu A, Whig P (2022) Studying the impact of the COVID vaccination on the world using data analytics. Vivekananda J Res 10(1):147–160
Whig P (2019a) Machine learning based techniques for communication and signal processing problem. Int J Mach Learn Sustain Dev 1(3):1–10
Whig P (2019b) Prediction of smart building indoor temperature using IoT and machine learning. Int J Mach Learn Sustain Dev 1(4):1–10
Whig P, Ahmad SN (2012) Performance analysis of various readout circuits for monitoring quality of water using analog integrated circuits. Int J Intell Syst Appl (IJISA) 4(11):91–98
Whig P, Ahmad SN (2013a) A novel pseudo PMOS integrated CC-ISFET device for water quality monitoring. J Integr Circ Syst Publ 8(2):1–6
Whig P, Ahmad SN (2013b) A Novel Pseudo NMOS Integrated ISFET device for water quality monitoring. Active Passive Compon 1(1):258
Whig P, Ahmad SN (2016a) Simulation and performance analysis of low power quasi floating gate PCS model. Int J Intell Eng Syst 9(2):8–13
Whig P, Ahmad SN (2016b) Ultraviolet photo catalytic oxidation (UVPCO) sensor for air and surface sanitizers using CS amplifier. Glob J Res Eng 16(6):1–13
Whig P, Ahmad SN (2014a) Simulation of linear dynamic macro model of photo catalytic sensor in SPICE. Compel Int J Comput Math Electric Electron Eng 33(1/2):611–629
Whig P, Ahmad SN (2014b) Development of economical ASIC for PCS for water quality monitoring. J Circ Syst Comput 23(6):1–13
Whig P, Rupani A (2020) Novel economical social distancing smart device for COVID19. Int J Electric Eng Technol 2(1):1–10
Whig P, Nadikattu RR, Velu A (2022) COVID-19 pandemic analysis using application of AI. In: Healthcare monitoring and data analysis using IoT: technologies and applications, vol 10, no 1, pp 1–15
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Author A has received research grants from Company A. Author B has received a speaker honorarium from Company X and owns stock in Company Y. Author C is a member of committee Z. OR if no conflict exists: Author A declares that he/she has no conflict of interest. Author B declares that he/she has no conflict of interest. There is no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jupalle, H., Kouser, S., Bhatia, A.B. et al. Automation of human behaviors and its prediction using machine learning. Microsyst Technol 28, 1879–1887 (2022). https://doi.org/10.1007/s00542-022-05326-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00542-022-05326-4