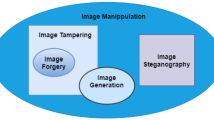
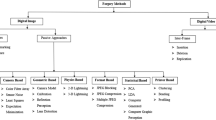
Abstract
With the advent of Internet, images and videos are the most vulnerable media that can be exploited by criminals to manipulate for hiding the evidence of the crime. This is now easier with the advent of powerful and easily available manipulation tools over the Internet and thus poses a huge threat to the authenticity of images and videos. There is no guarantee that the evidences in the form of images and videos are from an authentic source and also without manipulation and hence cannot be considered as strong evidence in the court of law. Also, it is difficult to detect such forgeries with the conventional forgery detection tools. Although many researchers have proposed advance forensic tools, to detect forgeries done using various manipulation tools, there has always been a race between researchers to develop more efficient forgery detection tools and the forgers to come up with more powerful manipulation techniques. Thus, it is a challenging task for researchers to develop h a generic tool to detect different types of forgeries efficiently. This paper provides the detailed, comprehensive and systematic survey of current trends in the field of image and video forensics, the applications of image/video forensics and the existing datasets. With an in-depth literature review and comparative study, the survey also provides the future directions for researchers, pointing out the challenges in the field of image and video forensics, which are the focus of attention in the future, thus providing ideas for researchers to conduct future research.





















Similar content being viewed by others
References
Farid, H.: Digital doctoring: how to tell the real from the fake. Significance 3(4), 162–166 (2006)
Zhu, B.B., Swanson, M.D., Tewfik, A.H.: When seeing isn’t believing. IEEE Signal Process. Mag. 21(2), 40–49 (2004)
“Photo tampering throughout history,” (2012). http://www.fourandsix.com/photo-tampering-history/
Redi, J.A., Taktak, W., Dugelay, J.-L.: Digital image forensics: a booklet for beginners. Multimed. Tools ppl. 51(1), 133–162 (2010)
Parveen, A., Tayal, A.: An algorithm to detect the forged part in an image. In: Proceedings of 2nd International Conference on Communication and Signal Processing, 1486–1490 (2016)
Yan, C., Li, Z., Zhang, Y., Liu, Y., Ji, X., Zhang, Y.: Depth Image denoising using nuclear norm and learning graph model. ACM Trans. Multimed. Comput. Commun. Appl. 16(4), 1–17 (2021)
Zheng, H., Yong, H., Zhang, L. Deep convolutional dictionary learning for image de-noising. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), 2021, 630–641 (2021)
Shi, Q., Tang, X., Yang, T., Liu, R., Zhang, L.: Hyperspectral image de-noising using a 3-D attention denoising network. IEEE Trans. Geosci. Remote Sens., pp. 1–16 (2021)
Yan, C., Hao, Y., Li, L., Yin, J., Liu, A., Mao, Z., Gao, X.: Task-adaptive attention for image captioning. IEEE Trans. Circ. Syst. Video Technol., 1–1 (2021)
Quan, Y., Chen, Y., Shao, Y., Teng, H., Xu, Y., Ji, H.: Image de-noising using complex-valued Deep CNN. Pattern Recognit. 111, 107639 (2020)
Lan, R., Zou, H., Pang, C., Zhong, Y., Liu, Z., Luoet, X.: Image denoising via deep residual convolutional neural networks. SIViP 15, 1–8 (2021)
Cheng, S., Wang, Y., Huang, H., Liu, D., Fan, H., Liu, S.: NBNet: Noise basis learning for image de-noising with subspace projection. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), pp. 4896–4906 (2021)
Jaseela, S., Nishadha, S.G.: Survey on copy move image forgery detection techniques. Int. J. Comput. Sci. Trends Technol. (IJCST) 4(1), 87–91 (2016)
Fadl, S.M., Semary, N.O.A., Hadhoud, M.M.: Copy–rotate–move forgery detection based on spatial domain. In: Proceedings of 9th International Conference on Computer Engineering and Systems, pp. 136–141 (2014)
Ren, X.: An optimal image thresholding using genetic algorithm. Int. Forum Comput. Sci.-Technol. Appl. 1, 169–172 (2009)
Hussain, M., Muhammad, G., Saleh, S.Q., Mirza, A.M., Bebis, G.: Copy–move image Forgery detection using multi-resolution weber descriptors. In: Proceedings of 8th International Conference on Signal Image Technology and Internet Based Systems, pp. 1570–1577 (2013)
Agarwal, V., Mane, V.: Reflective SIFT for improving the detection of copy–move image forgery. In: Proceedings of 2nd International Conference on Research in Computational Intelligence and Communication Networks, pp. 84–88 (2016)
Amerini, I., Ballan, L., Caldelli, R., Bimbo, A.D., Serra, G.: A SIFT-Based forensic method for copy–move attack detection and transformation recovery. IEEE Trans. Inf. Forensics Secur. 6(3), 1099–1110 (2011)
He, Z., Lu, W., Sun, W., Huang, J.: Digital image splicing detection based on markov features in DCT and DWT domain. Pattern Recogn. 45(12), 4292–4299 (2012)
Shahroudnejad, A., Rahmati, M.: Copy–move forgery detection in digital images using affine-SIFT. In: Proceedings of 2nd International Conference of Signal Processing and Intelligent Systems, pp. 1–5 (2016)
Lin, S.D., Wu, T.: An integrated technique for splicing and copy–move forgery image detection. In: Proceedings of 4th International Conference on Image and Signal Processing, 2:1086–1091 (2011)
Ting, Z., Rang-ding, W.: Copy–move forgery detection based on SVD in digital image. In: Proceedings of 2nd International Conference on Image and Signal Processing, 1–5 (2009)
Koppanati, R.K., Kumar, K.: P-MEC: polynomial congruence-based multimedia encryption technique over cloud. IEEE Consum. Electron. Mag. 10(5), 41–46 (2021)
Yan, C., Gong, B., Wei, Y., Gao, Y.: Deep multi-view enhancement hashing for image retrieval. IEEE Trans. Pattern Anal. Mach. Intell. 43, 1 (2020)
Chaudhuri, U., Banerjee, B., Bhattacharya, A.: Siamese graph convolutional network for content based remote sensing image retrieval. Comput. Vis. Image Underst. 184, 22–30 (2019)
Tolias, G., Sicre, R., Jegou, H.: Particular object retrieval with ´ integral max-pooling of CNN activations. In: ICLR, pp. 1–12 (2015)
Xu, J., Wang, C., Qi, C., Shi, C., Xiao, B.: Unsupervised part-based weighting aggregation of deep convolutional features for image retrieval. In: AAAI, 2018, 32(1), pp. 7436–7443 (2018)
Liu, H., Wang, R., Shan, S., Chen, X.: Deep supervised hashing for fast image retrieval. In: CVPR, 2016, pp. 2064–2072 (2016)
Yan, K., Wang, Y., Liang, D., Huang, T., Tian, Y.: CNN vs. SIFT for image retrieval: alternative or complementary? In: ACM MM, 2016, 407–411 (2016)
Liu, L., Ouyang, W., Wang, X., Fieguth, P., Chen, J., Liu, X., Pietikainen, M.: Deep learning for generic object detection: a survey. Int. J. Comput. Vis. 128(2), 261–318 (2020)
Sridevi, M., Mala, C., Sandeep, S.: Copy–move image forgery detection in a parallel environment. In: Proceedings of CS & IT Computer Science Conference Proceedings (CSCP), pp. 19–29 (2012)
Kang, L., Cheng, X.P.: Copy–move forgery detection in digital image. In: Proceedings of 3rd International Congress on Image and Signal Processing (CISP), vol. 5, pp. 2419–2421 (2010)
Li, H., Luo, W., Qiu, X., Huang, J.: Image forgery localization via integrating tampering possibility maps. IEEE Trans. Inf. Forensics Secur. 12, 1–13 (2017)
Al-Sanjary, O.I., Sulong, G.: Detection of video forgery: A review of literature. J. Theoret. Appl. Inf. Technol. 74(2), 217–218 (2015)
Ng, T., Chang, S.: A data set of authentic and spliced image blocks (2004)
Hsu, Y., Chang, S.: Detecting image splicing using geometry invariants and camera characteristics consistency. In: 2006 IEEE International Conference on Multimedia and Expo, 549–552 (2006)
Jegou, H., Douze, M., Schmid, C.: Hamming Embedding and Weak geometry consistency for large scale image search. In: Proceedings of the 10th European conference on Computer vision, October, 2008 (2008)
Gloe, T., Bohme, R.: The dresden image database for benchmarking digital image forensics. J. Digital Forensic Pract. 3(2–4), 150–159 (2010)
Amerini, I., Ballan, L., Caldelli, R., Del Bimbo, A., Serra, G.: A SIFT-based forensic method for copy-move attack detection and transformation recovery. IEEE Trans. Inf. Forensics Secur. 6(3), 1099–1110 (2011)
Bas, P., Filler, T., Pevny, T.: (2011). May Break our steganographic system: the ins and outs of organizing BOSS. In: International Workshop on Information Hiding, pp. 59–70 (2011)
Bianchi, T., Piva, A.: Image forgery localization via block-grained analysis of JPEG artifacts. IEEE Trans. Inf. Forensics Secur. 7(3), 1003–1017 (2012)
Christlein, V., Riess, C., Jordan, J., Riess, C., Angelopoulou, E.: An evaluation of popular copy-move forgery detection approaches. IEEE Trans. Inf. Forensics Secur. 7(6), 1841–1854 (2012)
Tralic, D., Zupancic, I., Grgic, S., Grgic, M.: CoMoFoD—New database for copy–move forgery detection. In: International Symposium Electronics in Marine, pp. 49–54 (2013)
Dong, J., Wang, W., Tan, T.: CASIA image tampering detection evaluation database. In: 2013 IEEE China Summit and International Conference on Signal and Information Processing (2013)
Amerini, I., Ballan, L., Caldelli, R., Del-Bimbo, A., Del-Tongo, L., Serra, G.: Copy-move forgery detection and localization by means of robust clustering with J-Linkage. Signal Process. Image Commun. 28(6), 659–669 (2013)
Cozzolino, D., Poggi, G., Verdoliva, L.: Copy-move forgery detection based on PatchMatch. In: 2014 IEEE International Conference on Image Processing (ICIP), pp. 5312–5316 (2014)
Ardizzone, E., Bruno, A., Mazzola, G.: Copy-move forgery detection by matching triangles of keypoints. IEEE Trans. Inf. Forensics Secur. 10, 2084–2094 (2015)
Dang-Nguyen, D.T., Pasquini, C., Conotter, V., Boato, G.: RAISE- A raw images dataset for digital image forensics. In: Proc. 6th ACM Multimed. Syst. Conf. MMSys 2015, pp. 219–224 (2015)
Wattanachote, K., Shih, T.K., Chang, W.-L., Chang, H.-H.: Tamper detection of JPEG image due to seam modifications. IEEE Trans. Inf. Forensics Secur. 10(12), 2477–2491 (2015)
Silva, E., Carvalho, T., Ferreira, A.: A. Rocha, going deeper into copy- move forgery detection: Exploring image telltales via multi-scale analysis and voting processes. J. Vis. Commun. Image Represent. 29, 16–32 (2015)
Zampoglou, M., Papadopoulos, S., Kompatsiaris, Y.: Detecting image splicing in the wild (WEB). In: 2015 IEEE International Conference on Multimedia & Expo Workshops (ICMEW), pp. 1–6 (2015)
Wen, B., Zhu, Y., Subramanian, R., Ng, T.T., Shen, X., Winkler, S.: COVERAGE—a novel database for copy-move forgery detection. In: Proc. - Int. Conf. Image Process. ICIP.2016-August, 161–165 (2016)
National Inst. of Standards and Technology (2016). The 2016 Nimble challenge evaluation dataset, https://www.nist.gov/itl/iad/mig/nimble-challenge, (2016)
Korus, P., Huang, J.J.: Multi-scale analysis strategies in PRNU-based tampering localization. IEEE Trans. Inf. Forensics Secur. 12(4), 809–824 (2017)
Guan, H., Kozak, M., Robertson, E., Lee, Y., Yates, A., Delgado, A., Zhou, D., Kheyrkhah, T., Smith, J., Fiscus, J.: MFC Datasets: Large-Scale Benchmark Datasets for Media Forensic Challenge Evaluation, IEEE Winter Conference on Applications of Computer Vision (WACV 2019), Waikola, HI, [online], https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=927035. (2019)
Novozámský, A., Mahdian, B., Saic, S.: IMD2020: a large-scale annotated dataset tailored for detecting manipulated images. In: 2020 IEEE Winter Applications of Computer Vision Workshops (WACVW), pp. 71–80 (2020)
Qadir, G., Yahahya, S., Ho, A.: Surrey University Library for Forensic Analysis (SULFA). In: Proceedings of the IETIPR 2012, 3–4 July, London (2012)
Bestagini, P., Milani, S., Tagliasacchi, M., Tubaro, S.: Local tampering detection in video sequences. In: 2013 IEEE 15Th International Workshop on Multimedia Signal Processing (MMSP). IEEE, pp. 488–493 (2013)
Al-Sanjary, O.I., Ahmed, A.A., Sulong, G.: Development of a video tampering dataset for forensic investigation. Forensic Sci. Int. 266, 565–572 (2016)
Chen, S., Tan, S., Li, B., Huang, J.: Automatic detection of object-based forgery in advanced video. IEEE Trans. Circ. Syst. Video Tech. 26(11), 2138–2151 (2016)
D’Avino, D., Cozzolino, D., Poggi, G., Verdoliva, L.: Autoencoder with recurrent neural networks for video forgery detection. Electron. Image 2017(7), 92–99 (2017)
Ulutas, G., Ustubioglu, B., Ulutas, M., Nabiyev, V.V.: Frame duplication detection based on bow model. Multimed. Syst. 24(5), 549–567 (2018)
D’Amiano, L., Cozzolino, D., Poggi, G., Verdoliva, L.: A patch match-based dense-field algorithm for video copy-move detection and localization. IEEE Trans. Circ. Syst. Video Technol. 29, 669–682 (2018)
Panchal, H.D., Shah, H.B.: Video tampering dataset development in temporal domain for video forgery authentication. Multimed. Tools Appl. 79, 24553–24577 (2020)
Ferreira, W.D., Ferreira, C.B., Junior, G.D., Soares, F.: A review of digital image forensics. Comput. Electr. Eng. 85, 106685 (2020)
Birajdar, G.K., Mankar, V.H.: Digital image forgery detection using passive techniques: a survey. Digit. Investig. 10(3), 226–245 (2013)
Farid, H.: A survey of image forgery detection techniques. IEEE Signal Process. Mag. 26, 16–25 (2009)
Qazi, T., Hayat, K., Khan, S.U., Madani, S.A., Khan, I.A., Kołodziej, J., Li, H., Lin, W., Yow, K.C., Xu, C.-Z.: Survey on blind image forgery detection. Image Process IET 7, 660–670 (2013)
Ansari, M.D., Ghrera, S.P., Tyagi, V.: Pixel-based image forgery detection: a review. IETE J. Educ. 55, 40–46 (2014)
Lanh, T.V.L.T., Van-Chong, K.-S., Chong, K.-S., Emmanuel, S., Kankanhalli, M.S.: A survey on digital camera image forensic methods. In: 2007 IEEE International Conference on Multimedia and Expo, pp. 16–19 (2007)
Mahdian, B., Saic, S.: A bibliography on blind methods for identifying image forgery. Signal Process. Image Commun. 25, 389–399 (2010)
Warif, N.B.A., Wahab, A.W.A., Idris, M.Y.I.: Copy-move forgery detection: survey, challenges and future directions. J. Netw. Comput. Appl. 75, 259–278 (2016)
Christlein, V., Riess, C.C., Jordan, J., Riess, C.C., Angelopoulou, E.: An evaluation of popular copy-move forgery detection approaches. IEEE Trans. Inf. Forensics Secur. 7, 1841–1854 (2012)
Friedman, G.L.: Trustworthy digital camera: restoring credibility to the photographic image. IEEE Trans. Consum. Electron. 39(4), 905–910 (1993)
Blythe, P., Fridrich, J.: Secure digital camera. In: Proceedings of the Digital Forensic Research Workshop (DFRWS ’04), pp. 17–19 (2004)
Rivest, R.L., Shamir, A., Adleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2), 120–126 (1978)
Menezes, A.J., VanstoneOorschot, S.S.A.P.C.V.: Handbook of Applied Cryptography, 1st edn. CRC Press, Boca Raton (1996)
Cox, I.J., Miller, M.L., Bloom, J.A.: Digital Watermarking. Morgan Kaufmann Publishers, Berlin (2002). ISBN 978-1-55860-714-9
Barni, M., Bartolini, F.: Watermarking systems engineering: enabling digital assets security and other applications. In: Signal Processing and Communications. Marcel Dekker (2004)
Cox, I.J., Miller, M.L., Bloom, J., Fridrich, J., Kalker, T.: Digital Watermarking and Steganography, 2nd edn. Morgan Kaufmann, San Francisco (2008)
Carneiro-Tavares, J.R., Madeiro-Bernardino-Junior, F.: Word-hunt: a LSB steganography method with low expected number of modifications per pixel. IEEE Lat. Am. Trans. 14(2), 1058–1064 (2016)
Laskar, S.A., Hemachandran, K.: Steganography based on random pixel selection for efficient data hiding. Int. J. Comput. Eng. Technol. (IJCET) 4, 31–44 (2013)
Bhattacharyya, S.: Study and analysis of quality of service in different image-based steganography using Pixel Mapping Method (PMM). Int. J. Appl. Inf. Syst. (IJAIS) 2(7), 42–57 (2012)
Qazanfari, K., Safabakhsh, R.: A new steganography method which preserves histogram: generalization of LSB++. Inf. Sci. (NY) 277, 90–101 (2014)
Shobana, M., Manikandan, R.: Efficient method for hiding data by pixel intensity. Int. J. Eng. Technol. (IJET) 5(1), 74–80 (2013)
Ni, J., Hu, X., Shi, Y.Q.: Efficient JPEG steganography using domain transformation of embedding entropy. IEEE Signal Process. Lett. 25(6), 773–777 (2018)
Ghoshal, N., Mandal, J.K.: A steganographic scheme for color image authentication (SSCIA), In: Proceedings of the international conference on recent trends in information technology, ICRTIT 2011, pp. 826–31 (2011)
Ibaida, A., Khalil, I.: Wavelet-Based ECG steganography for protecting patient confidential information in point-of-Care systems. IEEE Trans. Biomed. Eng. 60(12), 3322–3330 (2013)
Al-dmour, H., Al-ani, A.: A steganography embedding method based on edge identification and XOR coding. Expert Syst. Appl. 46, 293–306 (2016)
Jero, S.E., Ramu, P.: Curvelets-based ECG steganography for data security. Electron. Lett. 52(4), 283–285 (2016)
Tayan, O., Kabir, M.N., Alginahi, Y.M.: A hybrid digital-signature and zero-watermarking approach for authentication and protection of sensitive electronic documents. Sci. World J. 8, 1–15 (2014)
Subramanya, S.R., Yi, B.K.: Digital Signatures. IEEE Potentials 25(2), 5–8 (2006)
Lee, W.B., Chen, T.H.: A public verifiable copy protection technique for still images. J. Syst. Softw. 62(3), 195–204 (2002)
Damara-Ardy, R., Indriani, O.R., Sari, C.A., Setiadi, D.R.I.M., Rachmawanto, E.H.: Digital image signature using triple protection cryptosystem (RSA, Vigenere, and MD5). In: 2017 International Conference on Smart Cities, Automation & Intelligent Computing Systems (ICON-SONICS), pp. 87–92 (2017)
Meena, K.B., Tyagi, V.: A Deep Learning based Method for Image Splicing Detection. J. Phys. Conf. Ser. 1714, 012038 (2021)
Pramanik, S., Bandyopadhyay, S.K., Ghosh, R.: Signature image hiding in color image using steganography and cryptography based on digital signature, concepts. In: 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), pp. 665–669 (2020)
Moin, S.S., Islam, S.: Benford’s law for detecting contrast enhancement. In: 2017 Fourth International Conference on Image Information Processing (ICIIP), pp. 1–4 (2017)
Friedman, G.L.: The trustworthy digital camera: restoring credibility to the photographic image. IEEE Trans. Consum. Electron. 39(4), 905–910 (1993)
Rey, C., Dugelay, J.-L.: A survey of watermarking algorithms for image authentication. EURASIP J. Adv. Signal Proc. 6, 613–621 (2002)
Langelaar, G.C., Setyawan, I., Lagendijk, R.L.: Watermarking digital image and video data. A state-of-the-art overview. IEEE Signal Proc. Mag. 17(5), 20–46 (2000)
Tafti, A.P., Malakooti, M.V., Ashourian, M., Janosepah, S.: Digital image forgery detection through data embedding in spatial domain and cellular automata. In: 7th International Conference on Digital Content, Multimedia Technology and its Applications (IDCTA), pp. 11–15 (2011)
Bamatraf, A., Ibrahim, R., Najib, M., Salleh, M.: A new digital watermarking algorithm using combination of least significant bit (LSB) and inverse bit. J. Comput. 3(4), 2151–9617 (2011)
Sharma, P.K., Rajni: Analysis of image watermarking using least significant bit algorithm. Int. J. Inf. Sci. Tech. (IJIST) 2(4), 666–673 (2012)
Bhattacharya, S.: Additive watermarking in optimized digital image. In: IEEE Beacon, IEEE (Delhi Section), 79(1) (2012)
Bose, A., Maity, S.P.: Spread spectrum watermark detection on degraded compressed sensing. IEEE Sens. Lett. 1(5), 1–4 (2017)
Urvoy, M., Goudia, D., Autrusseau, F.: Perceptual DFT watermarking with improved detection and robustness to geometrical distortions. IEEE Trans. Inf. Forensics Secur. 9(7), 1108–1119 (2014)
Chaturvedi, N., Basha, S.J.: Comparison of Digital Image watermarking Methods DWT & DWT- DCT on the Basis of PSNR, International Journal of Innovative Research in Science, Engineering and Technology IJIRSET www.ijirset.com, 1 (2):147 (2012)
Ernawan, F., Kabir, M.N.: A robust image watermarking technique with an optimal DCT-psychovisual threshold. IEEE Access 6, 20464–20480 (2018)
Makbol, N.M., Khoo, B.E., Rassem, T.H.: Block-based discrete wavelet transform-singular value decomposition image watermarking scheme using human visual system characteristics. IET Image Proc. 10(1), 34–52 (2016)
Mansouri, A., Aznaveh, A.M., Azar, F.T.: SVD-based digital image watermarking using complex wavelet transform. Sadhana 34(3), 393–406 (2009)
Bapat, K.S., Totla, R.V.: Comparative analysis of watermarking in digital images using DCT & DWT. Int. J. Sci. Res. Publ. (IJSRP) 3(2), 1 (2013)
Mathai, N.J., Kundur, D., Sheikholeslami, A.: Hardware implementation perspectives of digital video watermarking algorithms. IEEE Trans. Signal Process. 51(4), 925–938 (2003)
Kougianos, E., Mohanty, S.P., Mahapatra, R.N.: Hardware assisted watermarking for multimedia. Comput. Electr. Eng. 35(2), 339–358 (2009)
Zhang, X., Wang, S.: Fragile watermarking with error free restoration capability. IEEE Trans. Multimed. 10(8), 1490–1499 (2008)
Chang, J., Chen, B., Tsai, C.: LBP-based fragile watermarking scheme for image tamper detection and recovery. In: International Symposium on Next Generation Electronics (Kaohsiung, 2013), pp. 173–176 (2013)
Doyoddorj, M., Rhee, K.H.: Multidisciplinary research and practice for information systems. In: IFIP WG 8.4, 8.9/TC 5 International Cross-Domain Conference and Workshop on Availability, Reliability, and Security, CD-ARES 2012, Prague, Czech Republic, August 20–24, 2012. Proceedings (ed. by (2012)
Quirchmayer, G., Basl, J., You, I., Xu, L., Weippl, E.: Multidisciplinary Research and Practice for Informations Systems. Springer Publishing (2012)
Tong, X., Liu, Y., Zhang, M., Chen, Y.: A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Process. Image Commun. 28(2), 301–308 (2013)
Huo, Y., He, H., Chen, F.: Alterable-capacity fragile watermarking scheme with restoration capability. Opt. Commun. 285(7), 1759–1766 (2012)
Wang, W., Men, A., Yang, B.: A feature-based semi-fragile watermarking scheme in DWT domain. In: 2010 2nd IEEE International Conference on Network Infrastructure and Digital Content, pp. 768–772 (2010)
Yu, M., Wang, J., Jiang, G., Peng, Z., Shao, F., Luo, T.: New fragile watermarking method for stereo image authentication with localization and recovery. AEU Int. J. Electron. Commun. 69(1), 361–370 (2015)
Lin, S.D., Kuo, Y.C., Huang, Y.H. An image watermarking scheme with tamper detection and recovery. In: First International Conference on Innovative Computing, Information and Control-Volume I (ICICIC’06), vol. 3, pp. 74–77 (2006)
Zhang, H., Wang, C., Zhou, X.: Fragile watermarking for image authentication using the characteristic of SVD. Algorithms 10(1), 27 (2017)
Li, C., Wang, Y., Ma, B., Zhang, Z.: A novel self-recovery fragile watermarking scheme based on dual-redundant-ring structure. Comput. Electr. Eng. 37(6), 927–940 (2011)
Bravo-Solorio, S., Nandi, A.K.: Secure fragile watermarking method for image authentication with improved tampering localization and self-recovery capabilities. Sign. Proces 91(4), 728–739 (2011)
Eswaraiah, R., Reddy, E.S.: ROI-based fragile medical image watermarking technique for tamper detection and recovery using variance. In: Seventh International Conference on Contemporary Computing (IC3), pp. 553–558 (2014)
He, H., Chen, F., Tai, H., Member, S., Kalker, T., Zhang, J.: Performance analysis of a block-neighborhood-based self-recovery fragile watermarking scheme. IEEE Trans. Inf. Forensics Secur 7(1), 185–196 (2012)
Qin, C., Ji, P., Zhang, X., Dong, J., Wang, J.: Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Signal Process. 138, 280–293 (2017)
Zhu, X.S., Sun, Y., Meng, Q.H., Sun, B., Wang, P., Yang, T.: Optimal watermark embedding combining spread spectrum and quantization. EURASIP J. Adv. Signal Process. 1, 74 (2016)
Molina-Garcia, J., Garcia-Salgado, B., Ponomaryov, V., Reyes-Reyes, R., Sadovnychiy, S., Cruz-Ramos, C.: An effective fragile watermarking scheme for color image tampering detection and self-recovery. Signal Process. Image Commun. 81, 115725 (2020)
Cao, X., Fu, Z., Sun, X.: (2016). A privacy-preserving outsourcing data storage scheme with fragile digital watermarking-based data auditing. J. Electr. Comput. Eng., pp. 1–7 (2016)
Abbas, N.H., Ahmad, S.M.S., Ramli, A.R.B., Parveen, S.: A multi-purpose watermarking scheme based on hybrid of lifting wavelet transform and Arnold transform. In: International Conference on Multidisciplinary in IT and Communication Science and Applications (2016)
Chen, F., He, H., Tai, H.M., Wang, H.: Chaos-based self-embedding fragile watermarking with flexible watermark payload. Multimed. Tool Appl. 72(1), 41–56 (2014)
Chamlawi, R., Usman, I., Khan, A.: Dual watermarking method for secure image authentication and recovery. In: IEEE 13th International Multitopic Conference (Islamabad, 2009), pp. 1–4 (2009)
Yu, X., Wang, C., Zhou, X.: Review on semi-fragile watermarking algorithms for content authentication of digital images. Future Internet 9(4), 56 (2017)
Wang, W., Men, A., Yang, B.: A feature-based semi-fragile watermarking scheme in DWT domain. In: 2nd IEEE International Conference on Network Infrastructure and Digital Content (Beijing, 2010), 768–772 (2010)
Qi, X., Xin, X.: A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J. Vis. Commun. Image Represent 30, 312–327 (2015)
Huo Y., He H, Chen F (2013). Semi-fragile watermarking scheme with discriminating general tampering from collage attack, Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (Kaohsiung, 2013), 1–6.
Li Y, Du L (2014). Semi-fragile watermarking for image tamper localization and self-recovery, Proceedings 2014 IEEE International Conference on Security, Pattern Analysis, and Cybernetics (SPAC) (Wuhan, 2014), 328–333.
Ekici, O., Sankur, B., Coşkun, B., Naci, U., Akcay, M.: Comparative evaluation of semifragile watermarking algorithms. J. Electron. Imaging 13(1), 209 (2004)
Jamal, S.S., Khan, M.U., Shah, T.: Awatermarking technique with chaotic fractional S-box transformation. Wirel. Pers. Commun. 90(4), 2033–2049 (2016)
Wang, S., Zheng, D., Zhao, J., Tam, W.J., Speranza, F.: Adaptive watermarking and tree structure-based image quality estimation. IEEE Trans. Multimed. 6(2), 331–324 (2014)
Shieh, J.M., Lou, D.C., Chang, M.C.: A semi-blind digital watermarking scheme based on singular value decomposition. Comput. Stand. Interfaces 28(4), 428–440 (2006)
Hsia, S.C., Jou, I.C., Hwang, S.M.: A gray level watermarking algorithm using double layer hidden. ICE Trans. Fund. Electron. ommun. Comput. Sci. 85(2), 436–471 (2002)
Rao, R.S.P, Kumar P.R.: Digital Signature based Image Watermarking using Ga and Pso. Int. J. Eng. Res. Technol. (IJERT), 6 (6), (2017)
Singh, H.V., Singh, A.K., Yadav, S., Mohan, A.: DCT based secure data hiding for intellectual property right protection. CSI Trans. ICT 2(3), 163–168 (2014)
Chen, T., Lu, H.: Robust spatial LSB watermarking of color images against JPEG compression. In: IEEE Fifth International Conference on Advanced Computational Intelligence (ICACI) (Nanjing, 2012), 872–875 (2012)
Wang, N., Kim, C.: Tamper detection and self-recovery algorithm of color image based on robust embedding of dual visual watermarks using DWT-SVD. In: 9th International Symposium on Communications and Information Technology (Icheon, 2009), 157–162 (2009)
Abdulazeez, A.M., Zeebaree, D.Q., Hajy, D.M., Zebari, D.A.: Robust watermarking scheme based LWT and SVD using artificial bee colony optimization. Indones. J. Electric. Eng. Comput. Sci. 21(2), 1218 (2021)
Makbol, N.M., Khoo, B.E., Rassem, T.H.: Security analyses of false positive problem for the SVD-based hybrid digital image watermarking techniques in the wavelet transform domain. Multimed. Tools Appl. 77, 1–35 (2018)
Ambadekar, S.P., Jain, J., Khanapuri, J.: Digital image watermarking through encryption and DWT for copyright protection. In: Recent trends in signal and image processing. Singapore: Springer, 187–195 (2019)
Pan-Pan, N., Xiang-Yang, W., Yu-Nan, L., Hong-Ying, Y.: A robust color image watermarking using local invariant significant bitplane histogram. Multimed. Tools Appl. 76(3), 3403–3433 (2017)
Vaidya, S.P., Mouli, P.C.: Adaptive digital watermarking for copyright protection of digital images in wavelet domain. Proc. Comput. Sci. 58, 233–240 (2015)
Wu, H.T., Huang, J.: Reversible image watermarking on prediction errors by efficient histogram modification. Signal Process. 92(12), 3000–3009 (2012)
Peng, F., Li, X., Yang, B.: Adaptive reversible data hiding scheme based on integer transform. Signal Process. 92(1), 54–62 (2012)
Ahmed, B., Gulliver, T.A., alZahir, S.: Image splicing detection using mask-RCNN. SIViP 14, 1035–1042 (2020)
Park, T.H., Han, J.G., Moon, Y.H., Eom, I.K.: Image splicing detection based on inter-scale 2D joint characteristic function moments in wavelet domain. EURASIP J. Image Video Process 30, 1–10 (2016)
Rao, Y., Ni, J.: A deep learning approach to detection of splicing and copy-move forgeries in images. In: 8th IEEE International Workshop Information Forensics Security WIFS (2016)
Shen, X., Shi, Z., Chen, H.: Splicing image forgery detection using textural features based on the grey level co-occurrence matrices. IET Image Process. 11, 44–53 (2017)
Bahrami, K., Member, S., Kot, A.C., Li, L., Li, H., Member, S.: Blurred image splicing localization by exposing blur type inconsistency. IEEE Trans. Inf. Forensics Secur 6013, 1–10 (2015)
Kanwal, N., Girdhar, A., Kaur, L., Bhullar, J.S.: Digital image splicing detection technique using optimal threshold based local ternary pattern. Multimed. Tools Appl. 79, 12829–12846 (2020)
Jaiswal, A.K., Srivastava, R.: A technique for image splicing detection using hybrid feature set. Multimed. Tools Appl. 79(17), 11837–11860 (2020)
El-Latif, E.I., Taha, A., Zayed, H.: A passive approach for detecting image splicing using deep learning and Haar Wavelet Transform. Int. J. Comput. Netw. Inf. Secur. 11, 28–35 (2019)
Jaiprakash, S.P., Desai, M.B., Prakash, C.S., Mistry, V.H., Radadiya, K.L.: Low dimensional DCT and DWT feature based model for detection of image splicing and copy-move forgery. Multimed. Tools Appl. 79, 29977–30005 (2020)
Niyishaka, P., Bhagvati, C.: Image splicing detection technique based on Illumination-Reflectance model and LBP. Multimed. Tools Appl. 80, 2161–2175 (2021)
Prabhu-Kavin, B., Ganapathy, S., Suthanthiramani, P., Kannan, A. A modified digital signature algorithm to improve the biomedical image integrity in cloud environment. In: Advances in Computational Techniques for Biomedical Image Analysis, 253–271 (2020)
Sharma, V., Jha, S., Bharti, R.K.: Image forgery and it’s detection technique: a review. Int. Res. J. Eng. Technol. (IRJET) 3(3), 756–762 (2016)
Yang, B., Sun, X., Guo, H., Xia, Z., Chen, X.: A copy-move forgery detection method based on CMFD-SIFT. Multimed. Tools Appl. 77, 837–855 (2017)
Meena, K.B., Tyagi, V.: A copy-move image forgery detection technique based on tetrolet transform. J. Inf. Secur. Appl. 52, 2481 (2020)
Zhu, Y., Shen, X., Chen, H.: Copy-move forgery detection based on scaled ORB. Multimed. Tools Appl. 75, 3221–3233 (2016)
Huang, D., Huang, C., Hu, W.: Robustness of copy-move forgery detection under high JPEG compression artifacts. Multimed. Tools Appl. 76(1), 1509–1530 (2017)
Islam, A., Long, C., Basharat, A., Hoogs, A.: DOA-GAN: Dual-order attentive generative adversarial network for image copy-move forgery detection and localization. In: 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), pp. 4675–4684 (2020)
Zhu, Y., Chen, C., Yan, G., Guo, Y., Dong, Y.: AR-Net: adaptive attention and residual refinement network for copy-move forgery detection. IEEE Trans. Ind. Inf. 16, 1–1 (2020)
Zandi, M., Mahmoudi-Aznaveh, A., Talebpour, A.: Iterative copy-move forgery detection based on a new interest point detector. IEEE Trans. Inf. Forensics Secur. 11, 2499–2512 (2016)
Bi, X., Pun, C.M., Yuan, X.C.: Multi-level dense descriptor and hierarchical feature matching for copy-move forgery detection. Inf. Sci. (Ny) 345, 226–242 (2016)
Silva, E., Carvalho, T., Ferreira, A., Rocha, A.: Going deeper into copy-move forgery detection: exploring image telltales via multi-scale analysis and voting processes. J. Vis. Commun. Image Represent. 29, 16–32 (2015)
Bi, X.L., Pun, C.M., Yuan, X.C.: Multi-scale feature extraction and adaptive matching for copy-move forgery detection. Multimed. Tools. Appl. 77, 1–23 (2016)
Wenchang, S.H.I., Fei, Z., Bo, Q.I.N., Bin, L.: Improving image copy-move forgery detection with particle swarm optimization techniques. China Commun. 13, 139–149 (2016)
Pun, C., Member, S., Yuan, X., Bi, X.: Oversegmentation and feature point matching. IEEE Trans. Inf. Forensics Secur. 10, 1705–1716 (2015)
Wang, X.Y., Li, S., Liu, Y.N., Niu, Y., Yang, H.Y., Zhou, Z.: A new keypoint-based copy-move forgery detection for small smooth regions. Multimed. Tools Appl. 76(22), 23353–23382 (2016)
Li, J., Li, X., Yang, B., Sun, X.: Segmentation-based image copy-move forgery detection scheme. IEEE Trans. Inf. Forensics Secur. 10(3), 507–518 (2015)
Zheng, J., Liu, Y., Ren, J., Zhu, T., Yan, Y., Yang, H.: Fusion of block and keypoints based approaches for effective copy-move image forgery detection. Multidimens. Syst. Signal Process. 27, 989–1005 (2016)
Park, J.Y., Kang, T.A., Moon, Y.H., Eom, I.K.: Copy-move forgery detection using scale invariant feature and reduced local binary pattern histogram. Symmetry 12, 492 (2020)
Niyishaka, P., Bhagvati, C.: Copy-move forgery detection using image blobs and BRISK feature. Multimed. Tools Appl. 79, 26045–26059 (2020)
Tinnathi, S.G.: An efficient copy move forgery detection using adaptive watershed segmentation with AGSO and hybrid feature extraction. J. Vis. Commun. Image Represent. 74, 1966 (2021)
Nguyen, H.C., Katzenbeisser, S.: Robust resampling detection in digital images. In: International Conference on Communications and Multimedia Security, pp. 3–15 (2012)
Flenner, A., Peterson, L., Bunk, J., Mohammed, T.M., Nataraj, L., Manjunath, B.S.: Resampling forgery detection using deep learning and A-contrario analysis. Electron. Imaging 7, 2121–2127 (2018)
Vazquez-Padin, D., Perez-Gonzalez, F., Comesana-Alfaro, P.: A random matrix approach to the forensic analysis of upscaled images. IEEE Trans. Inf. Forensics Secur. 12(9), 2115–2130 (2017)
Qiao, T., Zhu, A., Retraint, F.: Exposing image resampling forgery by using linear parametric model. Multimed. Tools Appl. 77, 1501–1523 (2018)
Bayar B, Stamm M.C.: On the robustness of constrained convolutional neural networks to JPEG post-compression for image resampling detection. In: IEEE International Conference on Acoustics Speech Signal Process, pp. 2152–2156 (2017)
Lamba, M., Mitra, K.: Multi-patch aggregation models for resampling detection. In: ICASSP 2020—2020 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp. 2967–2971 (2010)
Peng, A., Wu, Y., Kang, X.: Revealing traces of image resampling and resampling antiforensics. Adv. Multimed., pp. 1–13 (2017)
Bharathiraja, S., Rajesh Kanna, B.: Anti-forensics contrast enhancement detection (AFCED) technique in images based on laplace derivative histogram. Mob. Netw. Appl. 24, 1174–1180 (2019)
Lin, X., Li, C., Hu, Y.: Exposing image forgery through the detection of contrast enhancement. In: International Conference on Image Process, pp. 4467–4471 (2013)
Zhu, N., Deng, C., Gao, X.: Image sharpening detection based on multiresolution overshoot artifact analysis. Multimed. Tools Appl. 76, 16563–16580 (2017)
Stamm, M., Ray, K.J.: Blind forensics of contrast enhancement in digital images. In: Proceedings of International Conference on Image Process ICIP, 3112–3115 (2008)
Cao, G., Zhao, Y., Ni, R., Kot, A.C.: Unsharp masking sharpening detection via overshoot artifacts analysis. IEEE Signal Process. Lett. 18(10), 603–606 (2011)
Cao G, Zhao Y, Ni R (2009). Detection of image sharpening based on histogram aberration and ringing artifacts, 2009 IEEE International Conference on Multimedia and Expo.,1026–1029
Ding, F., Zhu, G., Yang, J., Xie, J., Shi, Y.-Q.: Edge perpendicular binary coding for USM sharpening detection. IEEE Signal Process. Lett. 22(3), 327–331 (2015)
Wang, Q., Zhang, R.: Double JPEG compression forensics based on a convolutional neural network. EURASIP J. Inf. Secur. 1, 23 (2016)
Madhusudhan, K.N., Sakthivel, P.: Combining digital signature with local binary pattern-least significant bit steganography techniques for securing medical images. J. Med. Imaging Health Inf. 10(6), 1288-1293 (6) (2020)
Shan, W., Yi, Y., Huang, R., Xie, Y.: Robust contrast enhancement forensics based on convolutional neural networks. Signal Process. Image Commun. 71, 138–146 (2018)
Zhang, C., Du, D., Ke, L., Qi, H., Lyu, S.: Global contrast enhancement detection via deep multi-path network. In: 2018 24th International Conference on Pattern Recognition (ICPR), pp. 2815–2820 (2018)
Barni, M., Bondi, L., Bonettini, N., Bestagini, P., Costanzo, A., Maggini, M., Tondi, B., Tubaro, S.: Aligned and non-aligned double JPEG detection using convolutional neural networks. J. Vis. Commun. Image Represent. 49, 153–163 (2017)
Zhang, Y., Thing, V.L.L.: A semi-feature learning approach for tampered region localization across multi-format images. Multimed. Tools Appl. 77, 25027–25052 (2018)
Zeng, X., Feng, G., Zhang, X.: Detection of double JPEG compression using modified DenseNet model. Multimed. Tools Appl. 78, 8183–8196 (2018)
Peng, P., Sun, T., Jiang, X., Xu, K., Li, B., Shi, Y.: Detection of double JPEG compression with the same quantization matrix based on convolutional neural networks. In: 2018 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA ASC., pp. 717–721 (2018)
Ahn, W., Nam, S.-H., Son, M., Lee, H.K., Choi, S.: End-to-end double JPEG detection with a 3D convolutional network in the DCT domain. Electron. Lett. 56, 82–85 (2020)
Amerini, I., Uricchio, T., Ballan, L., Caldelli, R. Localization of JPEG double compression through multi-domain convolutional neural networks. In: 2017 IEEE Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), 1865-1871 (2017)
Verma, V., Singh, D., Khanna, N.: Block-level double JPEG compression detection for image forgery localization. In: arXiv: Image and Video Processing (2020)
Lukas, J., Fridrich, J., Goljan, M.: Digital camera identification from sensor pattern noise. IEEE Trans. Inf. Forensics Secur. 2(1), 205–214 (2006)
Bayram, S., Sencar, H.T., Memon, N., Avcibas, I.: Source camera identification based on CFA interpolation. In: IEEE International Conference on Image Processing (ICIP) 2005 (2005)
Kharrazi, M., Sencar, H.T., Memon, N.: Blind source camera identification. In: IEEE International Conference on Image Processing (ICIP) 2004 (2004)
Taspinar, S., Mohanty, M., Memon, N.: PRNU-based camera attribution from multiple seam-carved images. IEEE Trans. Inf. Forensics Secur. 12(12), 3065–3080 (2017)
Xu, B., Wang, X., Zhou, X., Xi, J., Wang, S.: Source camera identification from image texture features. Neurocomputing 207, 131–140 (2016)
Hsu, Y.-F., Chang, S.-F.: Camera response functions for image forensics: an automatic algorithm for splicing detection. IEEE Trans. Inf. Forensics Secur. 5(4), 816–825 (2010)
Zheng L, Sun T, Shi Y. Q (2014). Inter-frame video forgery detection based on block-wise brightness variance descriptor. In: International workshop on digital watermarking, Springer, 18–30.
Liu, H., Li, S., Bian, S.: Detecting frame deletion in h. 264 video. In: International Conference on Information Security Practice and Experience, Springer, pp. 262–270 (2014)
Yao, H., Ni, R., Zhao, Y.: An approach to detect video frame deletion under anti-forensics. J. Real-Time Image Proc. 16(3), 751–764 (2019)
Shanableh, T.: Detection of frame deletion for digital video forensics. Digit. Invest. 10(4), 350–360 (2013)
Long, C., Smith, E., Basharat, A., Hoogs, A.: A c3d-based convolutional neural network for frame dropping detection in a single video shot. In: 2017 IEEE Conference on computer vision and pattern recognition workshops (CVPRW) IEEE, 1898–1906 (2017)
Bayar, B., Stamm, M. C.: A deep learning approach to universal image manipulation detection using a new convolutional layer. In: Proceedings of the 4th ACM Workshop on Information Hiding and Multimedia Security, pp. 5–10 (2016)
Cozzolino, D., Verdoliva, L.: Single-image splicing localization through autoencoder-based anomaly detection. In: 2016 IEEE International Workshop on Information Forensics and Security (WIFS), 1–6 (2016)
Fadl, S.M., Han, Q., Li, Q.: Authentication of surveillance videos: detecting frame duplication based on residual frame. J Forensic Sci. 63(4), 1099–1109 (2018)
Pandey, R.C., Singh, S.K., Shukla, K.: Passive copy-move forgery detection in videos. In: 2014 International Conference on Computer and Communication Technology (ICCCT). IEEE, pp. 301–306 (2014)
Hu, Y., Li, C.T., Wang, Y., Liu, B.B.: An improved fingerprinting algorithm for detection of video frame duplication forgery. Int. J. Digit. Crime Forensics (IJDCF) 4(3), 20–32 (2012)
Lin, G.S., Chang, J.F.: Detection of frame duplication forgery in videos based on spatial and temporal analysis. Int. J. Pattern Recognit. Artif. Intell. 26(07), 1250017 (2012)
Liao, S.Y., Huang, T.Q.: Video copy-move forgery detection and localization based on Tamura texture features. In: 2013 6th International Congress on Image and Signal Processing (CISP), vol. 2, pp. 864–868 (2013)
Li, F., Huang, T.: Video copy-move forgery detection and localization based on structural similarity. In: Proceedings of the 3rd International Conference on Multimedia Technology (ICMT 2013 Springer, 63–76 (2014)
Chao, J., Jiang, X., Sun, T.: A novel video inter-frame forgery model detection scheme based on optical flow consistency. In: International Workshop on Digital Watermarking. Springer, 267–281 (2012)
Kang, X., Liu, J., Liu, H., Wang, Z.J.: Forensics and counter anti-forensics of video inter-frame forgery. Multimed. Tools Appl. 75(21), 13833–13853 (2016)
Stamm, M.C., Lin, W.S., Liu, K.J.R.: Temporal forensics and anti-forensics for motion compensated video. IEEE Trans. Inf. Forensics Sec. 7(4), 1315–1329 (2012)
Wang, Q., Li, Z., Zhang, Z., Ma, Q.: Video inter-frame forgery identification based on consistency of correlation coefficients of gray values. J Comput. Commun. 2(04), 51 (2014)
Aghamaleki, J.A., Behrad, A.: Malicious inter-frame video tampering detection in mpeg videos using time and spatial domain analysis of quantization effects. Multimed. Tools Appl 76(20), 20691–20717 (2017)
Aghamaleki, J.A., Behrad, A.: Inter-frame video forgery detection and localization using intrinsic effects of double compression on quantization errors of video coding. Signal Process. Image Commun. 47, 289–302 (2016)
Wang, W., Farid, H.: Exposing digital forgeries in video by detecting double quantization, In: Proceedings of the 11th ACM Workshop on Multimedia and Security, 39–48 (2009)
Wang W, Jiang X, Wang S, Wan M, Sun T (2013). Identifying video forgery process using optical flow, In: International workshop on digital watermarking. Springer, 244–257.
Ravi, H., Subramanyam, A.V., Gupta, G., Kumar, B.A.: Compression noise based video forgery detection. In: 2014 IEEE International Conference on Image Processing (ICIP). IEEE, pp. 5352–5356 (2014)
Wang, W., Farid, H.: Exposing digital forgeries in video by detecting duplication. In: Proceedings of the 9th Workshop on Multimedia & Security, pp 35–42 (2007)
Singh, R.D., Aggarwal, N.: Detection and localization of copy-paste forgeries in digital videos. Forensic Sci. Int. 281, 75–91 (2017)
Chetty, G., Biswas, M., Singh, R.: Digital video tamper detection based on Multimodal fusion of residue features. In: 2010 Fourth international Conference on Network and System Security. IEEE, pp. 606–613 (2010)
Yao, Y., Shi, Y., Weng, S., Guan, B.: Deep learning for detection of object-based forgery in advanced video. Symmetry 10(1), 3 (2017)
Saddique, M., Asghar, K., Bajwa, U.I., Hussain, M., Habib, Z.: Spatial video forgery detection and localization using texture analysis of consecutive frames. Adv. Elect Comput. Eng. 19(3), 97–108 (2019)
Chen, R., Dong, Q., Ren, H., Fu, J.: Video forgery detection based on non-subsampled contourlet transform and gradient information. Inf. Technol. J. 11(10), 1456–1462 (2012)
Aloraini, M., Sharifzadeh, M., Agarwal, C., Schonfeld, S.: Statistical sequential analysis for object- based video forgery detection. Elect. Image 5, 543–551 (2019)
Aloraini, M., Sharifzadeh, M., Schonfeld, D.: Sequential and patch analyses for object removal video forgery detection and localization. IEEE Trans. Circ. Syst. Vid. Technol. 31, 917–930 (2020)
Kobayashi, M., Okabe, T., Sato, Y.: Detecting forgery from static-scene video based on inconsistency in noise level functions. IEEE Trans. Inf. Forensics Sec. 5(4), 883–892 (2010)
Wang, W., Farid, H.: Exposing digital forgeries in interlaced and deinterlaced video. IEEE Trans. Inf. Forensics Sec. 2(3), 438–449 (2007)
Labartino, D., Bianchi, T., De Rosa, A., Fontani, M., Va´zquez-Pad´ın, D., Piva, A., Barni, M.: Localization of forgeries in mpeg-2 video through GOP size and DQ analysis. In: 2013 IEEE 15th International Workshop on Multimedia Signal Processing (MMSP). IEEE, vol. 2, pp. 494–499 (2013)
Subramanyam, A.V., Emmanuel, S.: Video forgery detection using hog features and compression properties. In: 2012 IEEE 14th International Workshop on Multimedia Signal Processing (MMSP). IEEE, pp. 89–94 (2012)
Hsu, C.C., Hung, T.Y., Lin, C.W., Hsu, C.T.: Video forgery detection using correlation of noise residue. In: 2008 IEEE 10th Workshop on Multimedia Signal Processing. IEEE, 170–174 (2008)
Kancherla, K., Mukkamala, S.: Novel blind video forgery detection using markov models on motion residue. In: Asian Conference on Intelligent Information and Database Systems. Springer, 308–315 (2012)
Fayyaz, M.A., Anjum, A., Ziauddin, S., Khan, A., Sarfaraz, A.: An improved surveillance video forgery detection technique using sensor pattern noise and correlation of noise residues. Multimed. Tools Appl. 79(9), 5767–5788 (2020)
Singh, R.D., Aggarwal, N.: Detection of upscale-crop and splicing for digital video authentication. Digit. Invest. 21, 31–52 (2017)
Chen, J., Kang, X., Liu, Y., Wang, Z.J.: Median filtering forensics based on convolutional neural networks. IEEE Signal Process. Lett. 22(11), 1849–1853 (2015)
Hyun, D.K., Lee, M.J., Ryu, S.J., Lee, H.Y., Lee, H.K.: Forgery detection for surveillance video. In: The era of interactive media. Springer, pp. 25–36 (2013)
Zhang, Y., Goh, J., Win, L.L., Thing, V.L.: Image region forgery detection: A deep learning approach. In: SG-CRC, pp. 1–11 (2016)
Rao, Y., Ni, J.: A deep learning approach to detection of splicing and copy-move forgeries in images. In: 2016 IEEE International Workshop on Information Forensics and Security (WIFS), pp. 1–6 (2016)
Bondi, L., Lameri, S., Güera, D., Bestagini, P., Delp, E.J., Tubaro, S.: Tampering detection and localization through clustering of camera-based cnn features. In: 2017 IEEE Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), pp. 1855–1864 (2017)
Amerini, I., Uricchio, T., Ballan, L., Caldelli, R.: Localization of jpeg double compression through multi-domain convolutional neural networks. In: 2017 IEEE Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), pp. 1865–1871 (2017)
Salloum, R., Ren, Y., Jay, K.C.-C.: Image splicing localization using a multi-task fully convolutional network (MFCN). J. Vis. Commun. Image Represent. 51, 201–209 (2018)
Wu, Y., Abd-Almageed, W., Natarajan, P.: Busternet: detecting copy-move image forgery with source/target localization. In: Proceedings of the European Conference on Computer Vision (ECCV), 168–184 (2018)
Bi, X., Wei, Y., Xiao, B., Li, W.: Rru-net: The ringed residual u-net for image splicing forgery detection. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, (2019)
Wang, X., Wang, H., Niu, S., Zhang, J.: Detection and localization of image forgeries using improved mask regional convolutional neural network. Math. Biosci. Eng. 16, 4581–4593 (2019)
Kumar, K., Shrimankar, D.D., Singh, N.: Event bagging: A novel event summarization approach in multiview surveillance videos. In: 2017 International Conference on Innovations in Electronics, Signal Processing and Communication (IESC), pp. 106–111 (2017)
Gunawardena, P., Sudarshana, H., Amila, O., Nawaratne, R., Alahakoon, D., Perera, A.S., Chitraranjan, C.: Interest-oriented video summarization with keyframe extraction. In: 2019 19th International Conference on Advances in ICT for Emerging Regions, 250:1–8 (2019)
Xia, G., Chen, B., Sun, H., Liu, Q.: Nonconvex low-rank kernel sparse subspace learning for keyframe extraction and motion segmentation. IEEE Trans. Neural Netw. Learn. Syst. 32, 1–15 (2020)
Kumar, K., Shrimankar, D.D.: Deep event learning boost-up approach: Delta. Multimed. Tools Appl. 77, 26635–26655 (2018)
Kumar, K., Shrimankar, D.D.: F-des: Fast and deep event summarization. IEEE Trans. Multimed. 20(2), 323–334 (2018)
Kumar, K., Shrimankar, D.D., Singh, N.: Eratosthenes sieve based key-frame extraction technique for event summarization in videos. Multimed. Tools Appl. 77, 7383–7404 (2018)
Sharma, S., Kumar, K. GUESS: Genetic uses in video encryption with secret sharing. Adv. Intell. Syst. Comput., 51–62 (2018)
Sharma, S., Shivhare, S.N., Singh, N., Kumar, K. Computationally efficient ANN model for small-scale problems. Mach. Intell. Signal Anal., 423–435 (2018)
Kumar, K.: Text query based summarized event searching interface system using deep learning over cloud. Multimed. Tools Appl. 80(7), 11079–11094 (2021)
Manupriya, P., Sinha, S., Kumar, K. V⊕SEE: Video secret sharing encryption technique. In: 2017 Conference on Information and Communication Technology (CICT) (2017)
Koppanati, R.K., Kumar, K., Qamar, S.: E-MOC: an efficient secret Sharing Model for Multimedia on Cloud. In: Tripathi, M., Upadhyaya, S. (eds.) Conference Proceedings of ICDLAIR2019, p. 175 (2021)
Gadicha, A.B., Gupta, V.B., Gadicha, V.B., Kumar, K., Ghonge M.M.: Multimode approach of data encryption in images through QUANTUM STEGANOGRAPHY. In: Multidisciplinary Approach to Modern Digital Steganography, pp. 99–124 (2021)
Xiao, J., Zhao, R., Lam, K.-M.: Bayesian sparse hierarchical model for image de-noising. Signal Process. Image Commun. 96, 116299 (2021)
Author information
Authors and Affiliations
Contributions
SYED TUFAEL NABI: Writing—original draft, Data Collection, Relevant Articles Collection. Munish Kumar and Paramjeet Singh: Review Protocol, Testing, Writing—review & editing. Naveen Aggarwal and Krishan Kumar: Writing—review & editing.
Corresponding author
Ethics declarations
Conflict of Interest
All the authors declare that they have no conflict of interest in this work.
Additional information
Communicated by Y. Zhang.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Nabi, S.T., Kumar, M., Singh, P. et al. A comprehensive survey of image and video forgery techniques: variants, challenges, and future directions. Multimedia Systems 28, 939–992 (2022). https://doi.org/10.1007/s00530-021-00873-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00530-021-00873-8