Abstract
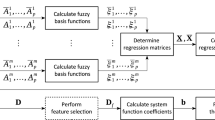
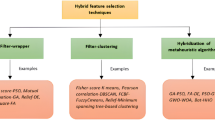
Fuzzy system is one of the most used systems in the decision-making and classification method as it is easy to understand because the way this system works is closer to how humans think. It is a system that uses human experts to hold the membership values to make decisions. However, it is hard to determine the fuzzy parameter manually in a complex problem, and the process of generating the parameter is called fuzzy modelling. Therefore, an optimization method is needed to solve this issue, and one of the best methods to be applied is Butterfly Optimization Algorithm. In this paper, BOA was improvised by combining this algorithm with Harmony Search (HS) in order to achieve optimal results in fuzzy modelling. The advantages of both algorithms are used to balance the exploration and exploitation in the searching process. Two datasets from UCI machine learning were used: Website Phishing Dataset and Phishing Websites Dataset. As a result, the average accuracy for WPD and PWD was 98.69% and 98.80%, respectively. In conclusion, the proposed method shows promising and effective results compared to other methods.







Similar content being viewed by others
Data availability
BOA java code used to support this study is available in ResearchGate with identifier https://doi.org/10.13140/RG.2.2.29675.6992. Datasets from the University of California, Irvine (UCI) can be freely accessed on their official website linked http://archive.ics.uci.edu/ml/.
References
Kettani H, Wainwright P (2019) On the Top threats to cyber systems on the top threats to cyber systems. In: 2019 IEEE 2nd international conference on information and computer technologies. https://doi.org/10.1109/INFOCT.2019.8711324
Amir Latif RM, Umer M, Tariq T, Farhan M, Rizwan O, Ali G (2019) A smart methodology for analysing secure E-banking and E-commerce websites. In: Proceedings of 2019 16th international bhurban conference on applied sciences and technology, IBCAST 2019, February 2020. pp 589–596. https://doi.org/10.1109/IBCAST.2019.8667255
Orunsolu AA, Sodiya AS, Akinwale AT (2020) A predictive model for phishing detection. J King Saud Univ Comput Inf Sci xxxx. https://doi.org/10.1016/j.jksuci.2019.12.005
Niu W, Zhang X, Yang G, Ma Z, Zhuo Z (2018) Phishing emails detection using CS-SVM. In: Proceedings - 15th IEEE international symposium on parallel and distributed processing with applications and 16th IEEE international conference on ubiquitous computing and communications, ISPA/IUCC 2017, pp 1054–1059. https://doi.org/10.1109/ISPA/IUCC.2017.00160
Barraclough P, Sexton G (2015) Phishing Website detection fuzzy system modelling. In: Science and information conference 2015, July 28–30 (2015). pp 1384–1386
Gorzałczany MB, Rudziński F (2016) A multi-objective genetic optimization for fast, fuzzy rule-based credit classification with balanced accuracy and interpretability. Appl Soft Comput 40:206–220. https://doi.org/10.1016/j.asoc.2015.11.037
Babu R (2001) Fuzzy systems, modeling, and identification. Electr Eng. https://doi.org/10.1002/0471224340.ch5
Yadollahi MM, Shoeleh F, Serkani E, Madani A, Gharaee H (2019) An adaptive machine learning based approach for phishing detection using hybrid features
Jupin JA, Sutikno T, Ismail MA, Mohamad MS, Kasim S (2019) Review of the machine learning methods in the classification of phishing attack. Bull Electr Eng Inf 8(4):1545–1555. https://doi.org/10.11591/eei.v8i4.1344
Nivedha MS, Gokulan S, Karthik C, Gopinath R, Gowshik R (2017) Improving phishing URL detection using fuzzy association mining. pp 21–31. https://doi.org/10.9790/1813-0604012131
Zabihimayvan M, Doran D (2019) Fuzzy rough set feature selection to enhance phishing attack detection. In: IEEE international conference on fuzzy systems, 2019-June. pp 5–10. https://doi.org/10.1109/FUZZ-IEEE.2019.8858884
Fehringer G, Barraclough PA (2017) Intelligent security for phishing online using adaptive neuro fuzzy systems. Int J Adv Comput Sci Appl 8(6):1–10. https://doi.org/10.14569/IJACSA.2017.080601
Tuo S, Yong L, Deng F, Li Y, Lin Y, Lu Q (2017) HSTLBO: a hybrid algorithm based on Harmony Search and Teaching-Learning- Based Optimization for complex high dimensional optimization problems. PLoS ONE 12(4):1–23. https://doi.org/10.1371/journal.pone.0175114
Sharma S, Saha AK (2019) m-MBOA: a novel butterfly optimization algorithm enhanced with mutualism scheme. Soft Comput. https://doi.org/10.1007/s00500-019-04234-6
Fan Y, Shao J, Sun G, Shao X (2020) A self-adaption butterfly optimization algorithm for numerical optimization problems. IEEE Access. https://doi.org/10.1109/ACCESS.2020.2993148
Arora S, Singh S (2019) Butterfly optimization algorithm: a novel approach for global optimization. Soft Comput 23(3):715–734. https://doi.org/10.1007/s00500-018-3102-4
Priyadharshini P, Prakashraj K, Padmapriya S (2019) Improved butterfly optimization algorithm using local search operator for capacitated vehicle routing problem. Int Res J Eng Technol (IRJET) 6(4):983–988
Li G, Shuang F, Zhao P, Le C (2019) An improved butterfly optimization algorithm for engineering design problems using the cross-entropy method. Symmetry 11(8):1049. https://doi.org/10.3390/sym11081049
Geem ZW, Kim JH, Loganathan GV (2001) A new heuristic optimization algorithm: harmony search. Simulation 76(2):60–68. https://doi.org/10.1177/003754970107600201
Yang XS (2009) Harmony search as a metaheuristic algorithm. Stud Comput Intell 191:1–14. https://doi.org/10.1007/978-3-642-00185-7_1
Pezhman Ramezani MA (2013) Harmony search algorithm: strengths and weaknesses. J Comput Eng Inf Technol 02(01):1–7. https://doi.org/10.4172/2324-9307.1000102
Abdelhamid N (2014) phishing detection based associative classification data mining. Expert Syst Appl (ESWA) 41(2014):5948–5959
Arora S, Singh S (2017) An effective hybrid butterfly optimization algorithm with artificial bee colony for numerical optimization. Int J Interact Multimed Artif Intell 4(4):14. https://doi.org/10.9781/ijimai.2017.442
Guo L, Wang GG, Wang H, Wang D (2013) An effective hybrid firefly algorithm with harmony search for global numerical optimization. Sci World J. https://doi.org/10.1155/2013/125625
Zubair Hasan KM, Hasan MZ, Zahan N (2019) Automated prediction of phishing websites using deep convolutional neural network. In: 5th international conference on computer, communication, chemical, materials and electronic engineering, IC4ME2 2019. pp 11–12. https://doi.org/10.1109/IC4ME247184.2019.9036647
Nordin NS, Ismail M, Omar N (2020) Fuzzy modelling using butterfly optimization algorithm for phishing detection. Int J Adv Trends Comput Sci Eng 9(1):355–360
Vrbančič G, Fister I, Podgorelec V (2018) Swarm intelligence approaches for parameter setting of deep learning neural network. In: Proceedings of the 8th international conference on web intelligence, mining and semantics - WIMS ’18. pp 1–8 https://doi.org/10.1145/3227609.3227655
Roopak S, Vijayaraghavan AP, Thomas T (2019) On effectiveness of source code and SSL based features for phishing website detection. In: 1st International conference on advanced technologies in intelligent control, environment, computing and communication engineering, ICATIECE 2019. pp 172–175 https://doi.org/10.1109/ICATIECE45860.2019.9063824
García S, Molina D, Lozano M, Herrera F, Garcia S, Lozano M, Herrera F (2009) A study on the use of non-parametric test for analyzing the evolutionary algorithms’ behaviour: a case study on the CEC’2005 special session on real parameter optimization. J Heuristics 15:617–644
Funding
This study was supported by Fundamental Research Grant (FRGS) with FRGS/1/2022/ICT02/UMP/02/2 (RDU220134) from the Ministry of Higher Education Malaysia, and by Fundamental Research Grant (RDU) with vot No. RDU220304 from Universiti Malaysia Pahang.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Nordin, N.S., Ismail, M.A. A hybridization of butterfly optimization algorithm and harmony search for fuzzy modelling in phishing attack detection. Neural Comput & Applic 35, 5501–5512 (2023). https://doi.org/10.1007/s00521-022-07957-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-022-07957-0