Abstract
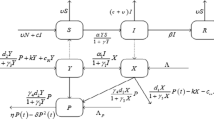
In the present study, a novel application of backpropagated neurocomputing heuristics (BNCH) is presented for epidemic virus model that portrays the Stuxnet virus propagation in regimes of supervisory control and data acquisition (SCADA) networks using multi-layer structure of neural networks (NNs) optimized with competency of efficient backpropagation with Levenberg–Marquardt (LM) method. Stuxnet virus spread through removable storage media that used to transfer of data and virus to device connected to SCADA networks with ability to exploit the whole system. The reference dataset of mathematical model of Stuxnet virus dynamics is generated by the competency of Adams method and used arbitrary for training, testing and validation of BNCH through NNs learning with LM scheme. Comparative study of BNCH with reference results shows the matching of 4–7 decimal places of accuracy and the further validated through mean squared error-based figure of merit, histograms, and regression measures.
















Similar content being viewed by others
References
Cohen FB, Cohen DF (1994) A short course on computer viruses. John Wiley & Sons Inc, Hoboken
Cohen F (1987) Computer viruses: theory and experiments. Comput Secur 6(1):22–35
Spafford EH (1990) Computer viruses - a form of artificial life? In: Computer science technical reports. Purdue University
Arqub OA, El-Ajou A (2013) Solution of the fractional epidemic model by homotopy analysis method. J King Saud Univ Sci 25(1):73–81
Kephart JO, White SR (1993) Measuring and modeling computer virus prevalence. In: Proceedings 1993 IEEE computer society symposium on research in security and privacy, IEEE, pp 2–15
Zou CC, Gong W, Towsley D (2002) Code red worm propagation modeling and analysis. In: Proceedings of the 9th ACM conference on computer and communications security, pp 138–147
Zou CC, Gong W, Towsley D, Gao L (2005) The monitoring and early detection of internet worms. IEEE ACM Trans Netw 13(5):961–974
Pont MTS, Castillo AC, Mora HM, Szymanski J (2018) Modelling the malware propagation in mobile computer devices. Comput Secur 79:80–93
Amador J (2016) The SEIQS stochastic epidemic model with external source of infection. Appl Math Model 40(19–20):8352–8365
Yang LX, Yang X, Wu Y (2017) The impact of patch forwarding on the prevalence of computer virus: a theoretical assessment approach. Appl Math Model 43:110–125
Dong T, Wang A, Liao X (2016) Impact of discontinuous antivirus strategy in a computer virus model with the point to group. Appl Math Model 40(4):3400–3409
Raza A, Arif MS, Rafiq M, Bibi M, Naveed M, Iqbal MU, Butt Z, Naseem HA, Abbasi JN (2019) Numerical treatment for stochastic computer virus model. Comput Model Eng Sci 120(2):445–465
Yu Y, Hu J, Zeng Y (2019) On computer virus spreading using node-based model with time-delayed intervention strategies. Sci China Inf Sci 62(5):59201
Gan C, Feng Q, Zhu Q, Zhang Z, Zhang Y, Xiang Y (2020) Analysis of computer virus propagation behaviors over complex networks: a case study of Oregon routing network. Nonlinear Dyn 100:1725–1740
Upadhyay RK, Singh P (2020) Modeling and control of computer virus attack on a targeted network. Phys A Stat Mech Appl 538:122617
Dang QA, Hoang MT (2020) Positivity and global stability preserving NSFD schemes for a mixing propagation model of computer viruses. J Comput Appl Math 374:112753
Zhang Z, Kundu S, Wei R (2019) A delayed epidemic model for propagation of malicious codes in wireless sensor network. Mathematics 7(5):396
Zhang C, Peng J, Xiao J (2019) An advanced persistent distributed denial-of-service attacked dynamical model on networks. Disc Dyn Nat Soc 2019:2051489. https://doi.org/10.1155/2019/2051489
Özdemir N, Uçar S, Eroğlu BBİ (2019) Dynamical analysis of fractional order model for computer virus propagation with kill signals. Int J Nonlinear Sci Numer Simul 21:239–247
Zhang Z, Kumari S, Upadhyay RK (2019) A delayed e-epidemic SLBS model for computer virus. Adv Differ Equ 2019(1):1–24
Masood Z, Majeed K, Samar R, Raja MAZ (2018) Design of epidemic computer virus model with effect of quarantine in the presence of immunity. Fundam Inform 161(3):249–273
Weinberger S (2011) Is this the start of cyberwarfare? Last year’s Stuxnet virus attack represented a new kind of threat to critical infrastructure. Nature 474(7350):142–146
Richardson J (2011) Stuxnet as cyberwarfare: applying the law of war to the virtual battlefield. J Marshall J Comput Inf L 29:1
Lachow I (2011) The Stuxnet enigma: implications for the future of cybersecurity. Georgetown J Int Aff 118–126. https://www.jstor.org/stable/43133820
Masood Z, Samar R, Raja MAZ (2019) Design of a mathematical model for the Stuxnet virus in a network of critical control infrastructure. Comput Secur 87:101565
Cserhati A (2011) The Stuxnet virus and the Iranian Atom Programme. Fiz Szle 61(5):150–155
Kerr PK, Rollins J, Theohary CA (2010) The stuxnet computer worm: Harbinger of an emerging warfare capability. Congressional Research Service, Washington, pp 7–5700
Denning DE (2012) Stuxnet: What has changed? Future Internet 4(3):672–687
Chen TM, Abu-Nimeh S (2011) Lessons from Stuxnet. Computer 44(4):91–93
Knapp ED, Langill JT (2014) Industrial network security: securing critical infrastructure networks for smart grid, SCADA, and other industrial control systems. Syngress, Rockland
Dubey VP, Kumar R, Kumar D (2020) A hybrid analytical scheme for the numerical computation of time fractional computer virus propagation model and its stability analysis. Chaos Solitons Fractals 133:109626
Arif MS, Raza A, Shatanawi W, Rafiq M, Bibi M (2019) A stochastic numerical analysis for computer virus model with vertical transmission over the internet. CMC Comput Mater Contin 61(3):1025–1043
Cheung KF, Bell MG (2019) Attacker–defender model against quantal response adversaries for cyber security in logistics management: an introductory study. Eur J Oper Res 291:471–481
Masood Z, Samar R, Raja MAZ (2020) Design of fractional order epidemic model for future generation tiny hardware implants. Future Gener Comput Syst 106:43–54
Shah Z, Raja MAZ, Chu YM, Khan WA, Waqas M, Shoaib M, Abbass SZ (2020) Design of neural network based intelligent computing for neumerical treatment of unsteady 3D flow of Eyring-Powell magneto-nanofluidic model. J Mater Res Technol 9(6):14372–14387
Jadoon I, Ahmed A, ur Rehman A, Shoaib M, Raja MAZ (2020) Integrated meta-heuristics finite difference method for the dynamics of nonlinear unipolar electrohydrodynamic pump flow model. Appl Soft Comput 97:106791
Jadoon I, Raja MAZ, Junaid M, Ahmed A, ur Rehman A, Shoaib M (2021) Design of evolutionary optimized finite difference based numerical computing for dust density model of nonlinear Van-der Pol Mathieu’s oscillatory systems. Math Comput Simul 181:444–470
Bukhari AH, Sulaiman M, Raja MAZ, Islam S, Shoaib M, Kumam P (2020) Design of a hybrid NAR-RBFs neural network for nonlinear dusty plasma system. Alexandria Eng J 59(5):3325–3345
Sabir Z, Baleanu D, Shoaib M, Raja MAZ (2021) Design of stochastic numerical solver for the solution of singular three-point second-order boundary value problems. Neural Comput Appl 33(7):2427–2443
Raja MAZ, Mehmood A, Niazi SA, Shah SM (2018) Computational intelligence methodology for the analysis of RC circuit modelled with nonlinear differential order system. Neural Comput Appl 30(6):1905–1924
Mehmood A, Zameer A, Aslam MS, Raja MAZ (2020) Design of nature-inspired heuristic paradigm for systems in nonlinear electrical circuits. Neural Comput Appl 32(11):7121–7137
Ahmad I, Ahmad F, Raja MAZ, Ilyas H, Anwar N, Azad Z (2018) Intelligent computing to solve fifth-order boundary value problem arising in induction motor models. Neural Comput Appl 29(7):449–466
Raja MAZ, Niazi SA, Butt SA (2017) An intelligent computing technique to analyze the vibrational dynamics of rotating electrical machine. Neurocomputing 219:280–299
Raja MAZ, Manzar MA, Shah SM, Chen Y (2020) Integrated intelligence of fractional neural networks and sequential quadratic programming for Bagley-Torvik systems arising in fluid mechanics. J Comput Nonlinear Dyn 15(5):051003
Lodhi S, Manzar MA, Raja MAZ (2019) Fractional neural network models for nonlinear Riccati systems. Neural Comput Appl 31(1):359–378
Ahmad I, Raja MAZ, Bilal M, Ashraf F (2017) Neural network methods to solve the Lane–Emden type equations arising in thermodynamic studies of the spherical gas cloud model. Neural Comput Appl 28(1):929–944
Raja MAZ, Shah FH, Tariq M, Ahmad I (2018) Design of artificial neural network models optimized with sequential quadratic programming to study the dynamics of nonlinear Troesch’s problem arising in plasma physics. Neural Comput Appl 29(6):83–109
Raja MAZ, Manzar MA, Shah FH, Shah FH (2018) Intelligent computing for Mathieu’s systems for parameter excitation, vertically driven pendulum and dusty plasma models. Appl Soft Comput 62:359–372
Sabir Z, Wahab HA, Umar M, Sakar MG, Raja MAZ (2020) Novel design of Morlet wavelet neural network for solving second order Lane–Emden equation. Math Comput Simul 172:1–14
Faisal F, Shoaib M, Raja MAZ (2020) A new heuristic computational solver for nonlinear singular Thomas–Fermi system using evolutionary optimized cubic splines. Eur Phys J Plus 135(1):1–29
Umar M, Raja MAZ, Sabir Z, Alwabli AS, Shoaib M (2020) A stochastic computational intelligent solver for numerical treatment of mosquito dispersal model in a heterogeneous environment. Eur Phys J Plus 135(7):1–23
Ahmad I, Raja MAZ, Ramos H, Bilal M, Shoaib M (2021) Integrated neuro-evolution-based computing solver for dynamics of nonlinear corneal shape model numerically. Neural Comput Appl 33(11):5753–5769
Raja MAZ, Mehmood A, Rehman A, Khan A, Zameer A (2018) Bio-inspired computational heuristics for Sisko fluid flow and heat transfer models. Appl Soft Comput 71:622–648
Mehmood A, Zameer A, Ling SH, Raja MAZ (2018) Design of neuro-computing paradigms for nonlinear nanofluidic systems of MHD Jeffery–Hamel flow. J Taiwan Inst Chem Eng 91:57–85
Raja MAZ, Mehmood A, Khan AA, Zameer A (2020) Integrated intelligent computing for heat transfer and thermal radiation-based two-phase MHD nanofluid flow model. Neural Comput Appl 32(7):2845–2877
Zameer A, Arshad J, Khan A, Raja MAZ (2017) Intelligent and robust prediction of short term wind power using genetic programming based ensemble of neural networks. Energy Convers Manag 134:361–372
Jamal R, Men B, Khan NH, Raja MAZ (2019) Hybrid bio-inspired computational heuristic paradigm for integrated load dispatch problems involving stochastic wind. Energies 12(13):2568
Ara A, Khan NA, Razzaq OA, Hameed T, Raja MAZ (2018) Wavelets optimization method for evaluation of fractional partial differential equations: an application to financial modelling. Adv Differ Equ 2018(1):1–13
Bukhari AH, Raja MAZ, Sulaiman M, Islam S, Shoaib M, Kumam P (2020) Fractional neuro-sequential ARFIMA-LSTM for financial market forecasting. IEEE Access 8:71326–71338
Dixit P, Silakari S (2021) Deep learning algorithms for cybersecurity applications: a technological and status review. Comput Sci Rev 39:100317
Kravchik M, Shabtai A (2018) Detecting cyber attacks in industrial control systems using convolutional neural networks. In: Proceedings of the 2018 workshop on cyber-physical systems security and privacy, pp 72–83
Muna AH, Moustafa N, Sitnikova E (2018) Identification of malicious activities in industrial internet of things based on deep learning models. J Inf Secur Appl 41:1–11
Sabir Z, Raja MAZ, Guirao JL, Shoaib M (2020) Integrated intelligent computing with neuro-swarming solver for multi-singular fourth-order nonlinear Emden-Fowler equation. Comput Appl Math 39(4):1–18
Sabir Z, Raja MAZ, Shoaib M, Aguilar JG (2020) FMNEICS: fractional Meyer neuro-evolution-based intelligent computing solver for doubly singular multi-fractional order Lane-Emden system. Comput Appl Math 39(4):1–18
Anitescu C, Atroshchenko E, Alajlan N, Rabczuk T (2019) Artificial neural network methods for the solution of second order boundary value problems. Comput Mater Contin 59(1):345–359
Erkaymaz O (2020) Resilient back-propagation approach in small-world feed-forward neural network topology based on Newman-Watts algorithm. Neural Comput Appl 32(20):16279–16289
Alfarraj O (2020) Internet of things with bio-inspired co-evolutionary deep-convolution neural-network approach for detecting road cracks in smart transportation. Neural Comput Appl. https://doi.org/10.1007/s00521-020-05401-9
Zhang Y, Wang Y, Luo G (2020) A new optimization algorithm for non-stationary time series prediction based on recurrent neural networks. Futur Gener Comput Syst 102:738–745
Kaur S, Singh M (2019) Hybrid intrusion detection and signature generation using deep recurrent neural networks. Neural Comput Appl 32:7859–7877
Munoz-Martinez F, Abellan JL, Acacio ME (2019) InsideNet: a for characterizing convolutional neural networks. Futur Gener Comput Syst 100:298–315
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All the authors of the manuscript declared that there are no potential conflict of interest.
Research involving human participants and/or animals
All the authors of the manuscript declared that there is no research involving human participants and/or animal.
Informed consent
All the authors of the manuscript declared that there is no material that required informed consent.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Raja, M.A.Z., Naz, H., Shoaib, M. et al. Design of backpropagated neurocomputing paradigm for Stuxnet virus dynamics in control infrastructure. Neural Comput & Applic 34, 5771–5790 (2022). https://doi.org/10.1007/s00521-021-06721-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-021-06721-0