Abstract
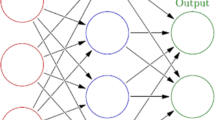
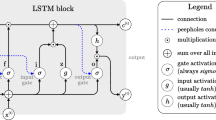
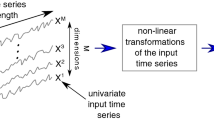
In order to improve the effectiveness of signal processing, according to the actual needs of signal processing and the current problems in signal processing, this paper introduces an improved LSTM recurrent neural network algorithm to construct the signal processing algorithm. Moreover, this paper sets up the functional structure of this paper based on the neural network model structure, and builds an intelligent analysis system for signal processing tasks based on the LSTM recurrent neural network algorithm. In addition, this paper analyzes the system algorithm flow in detail, and combines experimental research to carry out the effectiveness of the system constructed in this paper, and conducts quantitative analysis from two aspects of signal threshold prediction and signal processing effect. Finally, this paper conducts experimental results research with the support of mathematical statistics methods. From the research point of view, it can be known that the system constructed in this paper has good signal processing functions.














Similar content being viewed by others
References
Bello AA, Chiroma H, Gital AY et al (2020) Machine learning algorithms for improving security on touch screen devices: a survey, challenges and new perspectives. Neural Comput & Applic 32:13651–13678
Chatterjee S, Kar AK, Gupta MP (2018) Alignment of IT authority and citizens of proposed smart cities in India: System security and privacy perspective[J]. Glob J Flex Syst Manag 19(1):95–107
Blagorazumov A, Chernikov P, Glukhov G et al (2018) The background to the development of the information system for aviation security oversight in Russia[J]. International Journal of Mechanical Engineering and Technology (IJMET) 9(11):341–350
Özlen MK, Djedovic I (2017) Online banking acceptance: The influence of perceived system security on perceived system quality[J]. Accounting and Management Information Systems 16(1):164–178
Dotsenko S, Illiashenko O, Kamenskyi S et al (2019) Integrated security management system for enterprises in Industry 4.0[J]. Inform Security 43(3):294–304
Kim NY, Rathore S, Ryu JH et al (2018) A survey on cyber physical system security for IoT: issues, challenges, threats, solutions[J]. J Inform Process Syst 14(6):1361–1384
Hani SU, Alam AT (2017) Software development for information system-achieving optimum quality with security[J]. Int J Inform Syst Model Design (IJISMD) 8(4):1–20
Sun M, Konstantelos I, Strbac G (2018) A deep learning-based feature extraction framework for system security assessment[J]. IEEE transactions on smart grid 10(5):5007–5020
Choo KKR, Kermani MM, Azarderakhsh R et al (2017) Emerging embedded and cyber physical system security challenges and innovations[J]. IEEE Trans Dependable Secure Comput 14(3):235–236
Li D, Cai Z, Deng L et al (2019) Information security model of block chain based on intrusion sensing in the IoT environment[J]. Clust Comput 22(1):451–468
Safi A (2017) Improving the security of internet of things using encryption algorithms[J]. Int J Comput Inform Eng 11(5):558–561
Cram W A, D'arcy J, Proudfoot J G. 2019 Seeing the forest and the trees: a meta-analysis of the antecedents to information security policy compliance[J]. MIS Quarterly, 43(2): 525–554.
He R , X Li, Chen G , et al. 2020 Generative Adversarial Network-based Semi-supervised Learning for Real-time Risk Warning of Process Industries[J]. Expert Systems with Applications 150: 113244.
Le VH, Phung VO, Nguyen NH (2020) Information security risk management by a holistic approach: a case study for vietnamese e-government[J]. IJCSNS Int J Comput Sci Network Security 20(6):72–82
Lopez AB, Vatanparvar K, Nath APD et al (2017) A security perspective on battery systems of the Internet of Things[J]. J Hardware Syst Security 1(2):188–199
Lowry PB, Dinev T, Willison R (2017) Why security and privacy research lies at the centre of the information systems (IS) artefact: proposing a bold research agenda[J]. Eur J Inf Syst 26(6):546–563
Trang S, Brendel B (2019) A meta-analysis of deterrence theory in information security policy compliance research[J]. Inf Syst Front 21(6):1265–1284
Rajesh M (2018) A signature based information security system for vitality proficient information accumulation in wireless sensor systems[J]. Int J Pure Appl Mat 118(9):367–387
Na O, Park LW, Yu H et al (2019) The rating model of corporate information for economic security activities[J]. Secur J 32(4):435–456
Kavitha K, Neela R (2018) Optimal allocation of multi-type FACTS devices and its effect in enhancing system security using BBO, WIPSO & PSO[J]. J Electrical Syst Inform Technol 5(3):777–793
Turskis Z, Goranin N, Nurusheva A et al (2019) Information security risk assessment in critical infrastructure: a hybrid MCDM approach[J]. Informatica 30(1):187–211
Khan HU, AlShare KA (2019) Violators versus non-violators of information security measures in organizations—A study of distinguishing factors[J]. J Organ Comput Electron Commer 29(1):4–23
Choi SE, Martins JT, Bernik I (2018) Information security: listening to the perspective of organisational insiders[J]. J Inf Sci 44(6):752–767
Funding
The research is funded by Key Scientific Research Project of Xuchang University - Design of intelligent IOT management and control system at substation side based on BIM model and edge calculation (No. 2021ZD004).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhou, Y., Jiao, X. Intelligent analysis system for signal processing tasks based on LSTM recurrent neural network algorithm. Neural Comput & Applic 34, 12257–12269 (2022). https://doi.org/10.1007/s00521-021-06478-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-021-06478-6