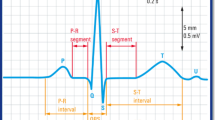
Abstract
This research suggests a unique ECG security solution based on the data pattern-based encryption paradigm to address security issues in ECG signal transmission or storage environments. According to this concept, the encryption system controls the data security process by extracting key signatures from the ECG signal peaks to identify the characteristics or attributes of the data and encrypt it. To estimate the hashing qualities, the approach is to build a random key pattern based on the signal peaks and extract the signature. The signal was then encrypted and sent to a doctor or signal analyzer. Bilateral random hashing (BRH) is used to achieve this. This updates the hashing generation model by analyzing the parameters using probabilistic distributional characteristics. This crucial motif was applied. This key pattern was utilized to encrypt the data samples using the downhill peak follow (DPF) encryption technique, which follows the strength of the peak value in the ECG waveform. This suggested project is carried out using MATLAB scripting.








Similar content being viewed by others
Data availability
The datasets analysed during the current study are not publicly available, but can be shared by the corresponding author on reasonable request.
References
Algarni AD et al (2021) Encryption of ECG signals for telemedicine applications. Multim Tools Appl 2021(80):10679–10703
Aung TM and Hla NN. (2019). A complex polyalphabetic cipher technique Myanmar polyalphabetic cipher. In: International conference on computer communication and informatics (ICCCI)
Azmi AS et al (2021) Smartphone-based ECG signals encryption for transmission and analyzing via IoMTs. J Discr Math Sci Cryptogr. https://doi.org/10.1080/09720529.2021.1958996
Chen TH et al (2008) The sorting method of ECG signals based on neural network. Proc Int Conf Bio Inform Biomed Eng 16:543–546
Chen KJ, Chien P (2017) A fast ECG diagnosis using frequency-based compressive neural network. In: Proceedings on 2017 IEEE 6th Global Conference on Consumer Electronics (GCCE), pp 3–4
Halperin D et al (2008) Security and privacy for implantable medical devices. IEEE Pervasive Comput 7(1):30–39
Jalil MM et al. (2014) Arrhythmia modelling via ECG characteristic frequencies and artificial neural network. In: Proceedings 2014 IEEE conference on systems, process and control (ICSPC 2014), pp 121–126
Karim F et al (2018) LSTM fully convolutional networks for time series classification. IEEE Access 6:1662–1669
Ko H et al. (2019). ECG-based advanced personal identification study with adjusted (Qi *Si), IEEE Access
Li C, Lin D, Lü J, Hao F (2018) Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multim 25(4):46–56. https://doi.org/10.1109/MMUL.2018.2873472
Mahsa R et al (2016) Compression and encryption of ECG signal using wavelet and chaotically Huffman code in telemedicine application. J Med Syst 40:1–8
Omolara AE et al. (2019) A deception model robust to eavesdropping over communication for social network systems, IEEE Access
Pirbhulal S et al. (2018) Heartbeats based biometric random binary sequences generation to secure wireless body sensor networks
Premkumar S, Mohana J (2020) A novel ECG based encryption algorithm for securing patient confidential information. Int J Electr Eng Technol 11(2):35–43
Rai HM, Trivedi A (2012) ECG signal classification using wavelet transform and back propagation neural network. In: 2012 Proceedings on 5th international conference on computers and devices for communication, pp 1–4
Sanjeev Kumar AN, Ramesh Naik NB (2022) VIHS with ROTR technique for enhanced light-weighted cryptographic system. Int J Adv Comput Sci Appl (IJACSA) 13(6).https://doi.org/10.14569/IJACSA.2022.01306110
Seena V, Yomas J (2014) A Review on Feature Extraction and Denoising of ECG Signal Using Wavelet Transform. In: Proceedings on 2nd International conference on devices, circuits and systems, pp 1–6
Vishnupriya TH, Jucy V (2018) Cryptographic method to provide confidentiality and integrity in implantable medical devices. In: 2018 second international conference on inventive communication and computational technologies (ICICCT), Coimbatore, India, 2018, pp 239–243. https://doi.org/10.1109/ICICCT.2018.8473358.
Wang F et al (2019) A novel ECG signal compression method using spindle convolutional auto-encoder. Comput Methods Progr Biomed J 175:139–150
Zaher AA, Hussain GA (2019) Chaos-based cryptography for transmitting multimedia data over public channels. In: 7th international conference on information and communication technology (ICoICT)
Zanddizari H et al (2022) Privacy assured recovery of compressively sensed ECG signals. IEEE Digital Object Identif 10:122
Zheng G et al. (2014) A non-key based security scheme supporting emergency treatment of wireless implants. In: Proceedings on IEEE international conference on communications (ICC), pp 647–652
Zheng G et al (2019) A critical analysis of ECG-based key distribution for securing wearable and implantable medical devices. IEEE Sens J 19:1186
Acknowledgements
A heartfelt thanks to professor, college, place, by authors for providing them the mandatory facilities to complete the project effectively.
Funding
Authors Sanjeev Kumar A N and Ramesh Naik B have not received research grants from organizations.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Author Sanjeev Kumar A N declares that he has no conflict of interest. Author Ramesh Naik B declares that he has no conflict of interest.
Ethical approval
This article contains no studies with human participants performed by authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kumar, A.N.S., Naik, B.R. Bilateral hashing model of ECG signal encryption system using downhill peak follow (DPF)-based encryption technique. Soft Comput 27, 11843–11851 (2023). https://doi.org/10.1007/s00500-023-08684-x
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-023-08684-x