Abstract
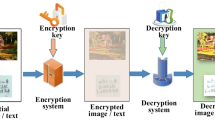
In order to overcome the problems of long encryption process, low data security and poor anti-attack rate of traditional tobacco enterprise trade data encryption methods, a trade data encryption of tobacco enterprises based on adversarial neural network is proposed. This method optimizes the traditional neural network by generating countermeasure network, so as to form adversarial neural network. In the adversarial neural network, the encryption processing of tobacco enterprise trade data is completed through data feature classification, design of tobacco enterprise trade data encryption protocol and data encryption channel. The experimental results show that the encryption process of this method takes between 6 s and 20 s, and the encryption efficiency is high, and this method can effectively scramble the original arrangement of the data, so as to effectively hide the effective information in the tobacco enterprise trade data, improve the anti-attack rate of the data, and effectively improve the security of the data.





Similar content being viewed by others
References
Azmi SD, Kusumaningrum R (2019) Relevance feedback using genetic algorithm on information retrieval for indonesian language documents. J Inf Syst Eng Bus Intell 5(2):171–182
Baagyere EY, Agbedemnab PA-N, Qin Z, Daabo MI, Qin Z (2020) A multi-layered data encryption and decryption scheme based on genetic algorithm and residual numbers. IEEE Access 8:100438–100447
Chabanne H, Despiegel V, Guiga L (2020) A protection against the extraction of neural network models. arXiv preprint arXiv:.12782
Elhadad A (2020) Data sharing using proxy re-encryption based on DNA computing. Soft Comput 24(3):2101–2108
He W, Zhao L, Cheng L (2021) A homomorphic encryption method for power data based on improved paillier algorithm. Paper presented at the International Conference on Artificial Intelligence and Security
Ikeda K, Sato Y, Koyama O, Yamada M (2019) Two-dimensional encryption system for secure free-space optical communication of time-series data streams. Electron Lett 55(13):752–754
Kumar P, Bhatt AK (2020) Enhancing multi-tenancy security in the cloud computing using hybrid ECC-based data encryption approach. IET Commun 14(18):3212–3222
Masuda H, Nakai T, Yoshida K, Kubota T, Shiozaki M, Fujino T (2020) Black-box adversarial attack against deep neural network classifier utilizing quantized probability output. J Signal Process 24(4):145–148
Pérez-Resa A, Garcia-Bosque M, Sánchez-Azqueta C, Celma S (2020) A new method for format preserving encryption in high-data rate communications. IEEE Access 8:21003–21016
Saračević MH, Adamović SZ, Miškovic VA, Elhoseny M, Maček ND, Selim MM, Shankar K (2020) Data encryption for Internet of Things applications based on catalan objects and two combinatorial structures. IEEE Trans Reliab
Sartakhti JS, Jalili S (2019) On the computational power of the light: A plan for breaking data encryption standard. Theoret Comput Sci 773:71–78
Sharma D, Jinwala D (2021) Simple index based symmetric searchable encryption with result verifiability. Front Comp Sci 15(2):1–3
Talha M, Sohail M, Tariq R, Ahmad MT (2021) Impact of oil prices, energy consumption and economic growth on the inflation rate in Malaysia. Cuadernos De Economía 44(124):26–32
Talha M, Azeem S, Sohail M, Javed A, Tariq R (2020) Mediating effects of reflexivity of top management team between team processes and decision performance. Azerbaijan J Educ Stud, 690
Talha M, Tariq R, Sohail M, Tariq A, Zia A, Zia M (2020) Review of international geographical education ISO 9000: (1987–2016) a trend's review Review of International Geographical Education Online, 10
Talha M (2021). Financial statement analysis of atlas honda motors, indus motors and pak suzuki motors (EVIDENCE FROM PAKISTAN). Ilkogretim Online, 20(4)
Vengala DVK, Kavitha D, Kumar AS (2020) Secure data transmission on a distributed cloud server with the help of HMCA and data encryption using optimized CP-ABE-ECC. Clust Comput 23(3):1683–1696
Vuppala A, Roshan RS, Nawaz S, Ravindra J (2020) An efficient optimization and secured triple data encryption standard using enhanced key scheduling algorithm. Procedia Computer Science 171:1054–1063
Yi, Z. (2021). Research on trade data encryption of tobacco enterprises based on adversarial neural network
Yoshida K, Fujino T (2020) Countermeasure against backdoor attack on neural networks utilizing knowledge distillation. J Signal Process 24(4):141–144
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Communicated by Irfan Uddin.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yi, Z. Research on trade data encryption of tobacco enterprises based on adversarial neural network. Soft Comput 26, 7501–7508 (2022). https://doi.org/10.1007/s00500-021-06479-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-021-06479-6