Abstract
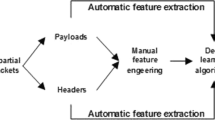
Over the decades, as the technology of Internet thrives rapidly, more and more kinds of cyber-attacks are blasting out around the world. Among them, botnet is one of the most noxious attacks which has always been challenging to overcome. The difficulties of botnet detection stem from the various forms of attack since the viruses keep evolving to avoid themselves from being found. Rule-based botnet detection has its shortcoming of detecting dynamically changing features. On the other hand, the more the Internet functionalities are developed, the severer the impacts botnets may cause. In recent years, many network devices have suffered from botnet attacks as the Internet of things technology prospers, which caused great damage in many industries. Consequently, botnet detection has always been a critical issue in computer security field. In this paper, we introduce a method to detect potential botnets by inspecting the behaviors of network traffics from network packets. In the beginning, we sample the given packets by a period of time and extract the behavioral features from a series of packets. By analyzing these features with proposed deep learning models, we can detect the threat of botnets and classify them into different categories.














Similar content being viewed by others
References
Bai S, Kolter JZ, Koltun V (2018) An empirical evaluation of generic convolutional and recurrent networks for sequence modeling. CoRR, vol abs/1803.01271 [Online]. arXiv:1803.01271
Behind the numbers: growth in the Internet of Things (2015). https://cdn.ihs.com/www/pdf/enabling-IOT.pdf
Binkley JR, Singh S (2006) An algorithm for anomaly-based botnet detection. In: Proceedings of the 2nd conference on steps to reducing unwanted traffic on the internet. USENIX Association [Online]. http://dl.acm.org/citation.cfm?id=1251296.1251303
Botnet topology. https://www.researchgate.net/figure/Typical-Client-Server-Botnet-Command-and-Control-Topology_fig1_266209917
Choi H, Lee H, Lee H, Kim H (Oct 2007) Botnet detection by monitoring group activities in DNS traffic. In: 7th IEEE international conference on computer and information technology
Dynamic generation algorithms. https://en.wikipedia.org/wiki/Domain_generation_algorithm
Feily M, Shahrestani A, Ramadass S (2009) A survey of botnet and botnet detection. In: Third international conference on emerging security information, systems and technologies
García S, Grill M, Stiborek J, Zunino A (2014) An empirical comparison of botnet detection methods. Comput Secur 45:100–123. https://doi.org/10.1016/j.cose.2014.05.011
Gu G, Perdisci R, Zhang J, Lee W (2008) Botminer: clustering analysis of network traffic for protocol- and structure-independent botnet detection. In: Proceedings of the 17th conference on security symposium, ser. SS’08. USENIX Association [Online]. http://dl.acm.org/citation.cfm?id=1496711.1496721
Hochreiter S (1998) The vanishing gradient problem during learning recurrent neural nets and problem solutions. Int J Uncertain Fuzziness Knowl-Based Syst. https://doi.org/10.1142/S0218488598000094
Hochreiter S, Schmidhuber J (1997) Long short-term memory. Neural Comput. https://doi.org/10.1162/neco.1997.9.8.1735
Homayoun S, Ahmadzadeh M, Hashemi S, Dehghantanha A, Khayami R (2018) BoTShark: a deep learning approach for botnet traffic detection. Springer, Cham, pp 137–153
Jain LC, Medsker LR (1999) Recurrent neural networks: design and applications, 1st edn. CRC Press Inc, Boca Raton
Karasaridis A, Rexroad B, Hoeflin D (2007) Wide-scale botnet detection and characterization. In: Proceedings of the first conference on first workshop on hot topics in understanding botnets. USENIX Association [Online]. http://dl.acm.org/citation.cfm?id=1323128.1323135
Mikolov T, Karafiat M, Burget L, Cernocky J, Khudanpur S (2010) Recurrent neural network based language model. In: International speech communication association, pp 1045–1048
Pysahrk. https://kiminewt.github.io/pyshark/
Siboni S, Cohen A (2014) Botnet identification via universal anomaly detection. In: 2014 IEEE international workshop on information forensics and security (WIFS), pp 101–106
Smominru (2018). https://www.cyber.nj.gov/threat-profiles/botnet-variants/smominru
Snort (2016). https://www.snort.org/
Srivastava N, Hinton G, Krizhevsky A, Sutskever I, Salakhutdinov R (2014) Dropout: a simple way to prevent neural networks from overfitting. J Mach Learn Res 15(1):1929–1958. http://dl.acm.org/citation.cfm?id=2627435.2670313
Sutskever I, Martens J, Hinton G (2011)Generating text with recurrent neural networks. In: Proceedings of the 28th international conference on machine learning (ICML-11), pp 1017–1024
Sutskever I, Vinyals O, Le QV (2014) Sequence to sequence learning with neural networks. In: Advances in neural information processing systems 27(NIPS 2014), pp 3104–1112
Tran D, Mac H, Tong VT, Tran HA, Nguyen LG (2018) A LSTM based framework for handling multiclass imbalance in dga botnet detection. Neurocomputing 275:2401–2413
Tshark. https://www.wireshark.org/docs/man-pages/tshark.html
Villamarin-Salomon R, Brustoloni JC (2008) Identifying botnets using anomaly detection techniques applied to DNS traffic. In: 2008 5th IEEE consumer communications and networking conference, pp 476–481
Vinayakumar R, Soman K, Poornachandran P, Alazab M, Jolfaei A (2019) DBD: deep learning dga-based botnet detection. In: Deep learning applications for cyber security. Springer, Cham, Switzerland, 2019, pp 127–149
Wang W, Zhu M, Zeng X, Ye X, Shengand Y (2017) Malware traffic classification using convolutional neural network for representation learning. In: 2017 International conference on information networking
Wikipedia: Mirai. https://en.wikipedia.org/wiki/Mirai_(malware)
Wikipedia: Softmax function. https://en.wikipedia.org/wiki/Softmax_function
Xu K, Ba J, Kiros R, Cho K, Courville A, Salakhutdinov R, Zemel R, Bengio Y (2015) Show, attend and tell: neural image caption generation with visual attention. In: Proceedings of the 32nd international conference on machine learning, vol 37
Ziv J, Lempel A (978) Compression of individual sequences via variable-rate coding. In: 1978 IEEE transactions on information theory, pp 530–536
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that they have no conflict of interest.
Additional information
Communicated by V. Loia.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Shi, WC., Sun, HM. DeepBot: a time-based botnet detection with deep learning. Soft Comput 24, 16605–16616 (2020). https://doi.org/10.1007/s00500-020-04963-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-020-04963-z