Abstract
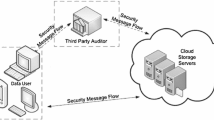
Public cloud data auditing allows a user to delegate an auditing job to a third party who is responsible for verifying whether a cloud server has faithfully stored a file or not. Proof of retrievability (PoR) is a widely used protocol for this kind of job. To the best of our knowledge, in the publicly verifiable setting with supporting data dynamics, all known PoR schemes are either rely on the random oracles or are built in the standard model but require nonstandard assumptions. In this paper, we present a scheme which explores the linear homomorphic signature and the sequence Merkle hash tree to construct the homomorphic linear authenticator for the PoR. The security of our proposed scheme can be proved in the standard model, assuming the hash function is collision resilient and the computational Diffie–Hellman assumption holds. The scheme also supports data modification, data insertion and data deletion. Furthermore, our technique can also be regarded as a novel paradigm by combining the homomorphic signature and authenticated data structure (with certain properties) to construct the homomorphic linear authenticator for the PoR protocols.









Similar content being viewed by others
Notes
\(\sigma _{i,2}\) is also stored by the CSS in \(\sigma \).
References
Ahn JH, Boneh D, Camenisch J, Hohenberger S, Shelat A, Waters B (2012) Computing on authenticated data. In: Cramer R (ed) Proceedings of theory of cryptography: 9th theory of cryptography conference, TCC 2012, Taormina, Sicily, Italy, March 19–21, 2012. Springer, Berlin, p 1–20
Ateniese G, Burns R, Curtmola R, Herring J, Kissner L, Peterson Z, Song D (2007) Provable data possession at untrusted stores. In: Proceedings of the 14th ACM conference on computer and communications security, ACM, New York, CCS ’07, p 598–609
Ateniese G, Di Pietro R, Mancini LV, Tsudik G (2008) Scalable and efficient provable data possession. In: Proceedings of the 4th international conference on security and privacy in communication networks, ACM, New York, SecureComm ’08, p 9:1–9:10
Ateniese G, Kamara S, Katz J (2009) Proofs of storage from homomorphic identification protocols. In: Matsui M (ed) Advances in cryptology—ASIACRYPT 2009: Proceedings of 15th international conference on the theory and application of cryptology and information security, Tokyo, Japan, December 6–10, 2009. Springer, Berlin, p 319–333
Attrapadung N, Libert B, Peters T (2012) Computing on authenticated data: new privacy definitions and constructions. In: Wang X, Sako K (eds) Proceedings of advances in cryptology—ASIACRYPT 2012: 18th international conference on the theory and application of cryptology and information security, Beijing, China, December 2–6, 2012. Springer, Berlin, p 367–385
Ateniese G, Burns R, Curtmola R, Herring J, Khan O, Kissner L, Peterson Z, Song D (2011) Remote data checking using provable data possession. ACM Trans Inf Syst Secur 14(1):12:1–12:34
Boneh D, Lynn B, Shacham H (2001) Short signatures from the weil pairing. In: Proceedings of the 7th international conference on the theory and application of cryptology and information security: advances in cryptology. Springer, London, ASIACRYPT ’01, p 514–532
Buyya R, Yeo CS, Venugopal S, Broberg J, Brandic I (2009) Cloud computing and emerging IT platforms: vision, hype, and reality for delivering computing as the 5th utility. Future Gener Comput Syst 25(6):599–616
Curtmola R, Khan O, Burns R, Ateniese G (2008) MR-PDP: Multiple-replica provable data possession. In: 2008 the 28th international conference on distributed computing systems, p 411–420
Diffie W, Hellman M (2006) New directions in cryptography. IEEE Trans Inf Theor 22(6):644–654
Dodis Y, Vadhan S, Wichs D (2009) Proofs of retrievability via hardness amplification. In: Reingold O (ed) Theory of cryptography: proceedings of 6th theory of cryptography conference, TCC 2009, San Francisco, March 15-17, 2009. Springer, Berlin, p 109–127
Erway C, Küpçü A, Papamanthou C, Tamassia R (2009) Dynamic provable data possession. In: Proceedings of the 16th ACM conference on computer and communications security, ACM, New York, CCS ’09, p 213–222
Freeman DM (2012) Improved security for linearly homomorphic signatures: a generic framework. In: Fischlin M, Buchmann J, Manulis M (eds) Public key cryptography—PKC 2012: Proceedings of 15th international conference on practice and theory in public key cryptography, Darmstadt, May 21–23, 2012, Springer, Berlin, p 697–714
Hao Z, Yu N (2010) A multiple-replica remote data possession checking protocol with public verifiability. In: 2010 second international symposium on data, privacy, and E-commerce, p 84–89
Hao Z, Zhong S, Yu N (2011) A privacy-preserving remote data integrity checking protocol with data dynamics and public verifiability. IEEE Trans Knowl Data Eng 23(9):1432–1437
Juels A, Kaliski BS Jr (2007) PORS: Proofs of retrievability for large files. In: Proceedings of the 14th ACM conference on computer and communications security, ACM, New York, CCS ’07, p 584–597
Li X, Li J, Huang F (2016) A secure cloud storage system supporting privacy-preserving fuzzy deduplication. Soft Comput 20(4):1437–1448
Liu C, Ranjan R, Yang C, Zhang X, Wang L, Chen J (2015) MUR-DPA: top-down levelled multi-replica merkle hash tree based secure public auditing for dynamic big data storage on cloud. IEEE Trans Comput 64(9):2609–2622
Lynn B (2013) The pairing-based cryptography library (0.5.13). http://crypto.stanford.edu/pbc/. Accessed 8 May 2017
Mao J, Zhang Y, Li P, Li T, Wu Q, Liu J (2017) A position-aware merkle tree for dynamic cloud data integrity verification. Soft Comput 21(8):2151–2164
Merkle RC (1980) Protocols for public key cryptosystems. In: 1980 IEEE symposium on security and privacy, p 122
Merkle RC (1990) A certified digital signature. In: Brassard G (ed) Advances in cryptology—CRYPTO’ 89 proceedings. Springer, New York, pp 218–238
Miller A, Hicks M, Katz J, Shi E (2014) Authenticated data structures, generically. In: Proceedings of the 41st ACM SIGPLAN-SIGACT symposium on principles of programming languages, ACM, New York, POPL’14, p 411–423
Paterson MB, Stinson DR, Upadhyay J (2016) Multi-prover proof-of-retrievability. The computing research repository arxiv:abs/1603.02671
Sebé F, Domingo-Ferrer J, Martinez-Balleste A, Deswarte Y, Quisquater JJ (2008) Efficient remote data possession checking in critical information infrastructures. IEEE Trans Knowl Data Eng 20(8):1034–1038
Shacham H, Waters B (2008) Compact proofs of retrievability. In: Pieprzyk J (ed) Advances in cryptology—ASIACRYPT 2008: proceedings of 14th international conference on the theory and application of cryptology and information security, Melbourne, Australia, December 7–11, 2008, Springer, Berlin, p 90–107
Shacham H, Waters B (2013) Compact proofs of retrievability. J Cryptol 26(3):442–483
Tamassia R (2003) Authenticated data structures. In: Di Battista G, Zwick U (eds) Algorithms–ESA 2003: Proceedings of 11th annual European symposium, Budapest, Hungary, September 16–19, 2003, Springer, Berlin, p 2–5
Tian H, Chen Z, Chang CC, Kuribayashi M, Huang Y, Cai Y, Chen Y, Wang T (2017) Enabling public auditability for operation behaviors in cloud storage. Soft Comput 21(8):2175–2187
Wang H (2015) Identity-based distributed provable data possession in multicloud storage. IEEE Trans Serv Comput 8(2):328–340
Wang Q, Wang C, Li J, Ren K, Lou W (2009) Enabling public verifiability and data dynamics for storage security in cloud computing. In: Proceedings of the 14th European conference on research in computer security. Springer, Berlin, ESORICS’09, p 355–370
Wang C, Chow SSM, Wang Q, Ren K, Lou W (2013) Privacy-preserving public auditing for secure cloud storage. IEEE Trans Comput 62(2):362–375
Wang H, He D, Shen J, Zheng Z, Zhao C, Zhao M (2016) Verifiable outsourced ciphertext-policy attribute-based encryption in cloud computing. Soft Comput 21:7325
Waters B (2005) Efficient identity-based encryption without random oracles. In: Cramer R (ed) Advances in cryptology—EUROCRYPT 2005: Proceedings of 24th annual international conference on the theory and applications of cryptographic techniques, Aarhus, Denmark, May 22–26, 2005. Springer, Berlin, p 114–127
Xue L, Ni J, Li Y, Shen J (2017) Provable data transfer from provable data possession and deletion in cloud storage. Comput Stand Interfaces 54:46–54
Yu Y, Au MH, Mu Y, Tang S, Ren J, Susilo W, Dong L (2015a) Enhanced privacy of a remote data integrity-checking protocol for secure cloud storage. Int J Inf Secur 14(4):307–318
Yu Y, Zhang Y, Mu Y, Susilo W, Liu H (2015b) Provably secure identity based provable data possession. Springer, Cham, pp 310–325
Yu Y, Zhang Y, Ni J, Au MH, Chen L, Liu H (2015c) Remote data possession checking with enhanced security for cloud storage. Future Gener Comput Syst 52(C):77–85
Yu Y, Li Y, Au MH, Susilo W, Choo KKR, Zhang X (2016a) Public cloud data auditing with practical key update and zero knowledge privacy. In: Liu JK, Steinfeld R (eds) Information security and privacy: proceedings of 21st Australasian conference, ACISP 2016, Melbourne, July 4–6, 2016, Part I, Springer, Cham, p 389–405
Yu Y, Xue L, Au MH, Susilo W, Ni J, Zhang Y, Vasilakos AV, Shen J (2016b) Cloud data integrity checking with an identity-based auditing mechanism from rsa. Future Gener Comput Syst 62:85–91
Yu Y, Au MH, Ateniese G, Huang X, Susilo W, Dai Y, Min G (2017) Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans Inf Foren Secur 12(4):767–778
Yuan J, Yu S (2013) Secure and constant cost public cloud storage auditing with deduplication. In: 2013 IEEE conference on communications and network security (CNS). National Harbor, p 145–153
Zhu Y, Hu H, Ahn GJ, Yu M (2012) Cooperative provable data possession for integrity verification in multicloud storage. IEEE Trans Parallel Distrib Syst 23(12):2231–2244
Acknowledgements
The authors would like to thank Xue Liang, Zhao Yi, Zhou Yanwei and Lai Qiqi for their valuable comments. This work is supported by the National Key R&D Program of China (2017YFB080 2000), the National Natural Science Foundation of China (61772326, 61572303), NSFC Research Fund for International Young Scientists (61750110528), National Cryptography Development Fund during the 13th Five-year Plan Period (MMJJ20170216), the Foundation of State Key Laboratory of Information Security (2017-MS-03) and the Fundamental Research Funds for the Central Universities (GK201603092, GK201702004, GK201603084). It is also supported by Fund of Key Laboratory of Modern Teaching Technology, Ministry of Education, P.R.China (2015kfkt3).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interests regarding the publication of this paper.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Communicated by V. Loia.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, T., Yang, B., Liu, H. et al. An alternative approach to public cloud data auditing supporting data dynamics. Soft Comput 23, 4939–4953 (2019). https://doi.org/10.1007/s00500-018-3155-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-018-3155-4