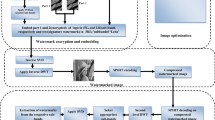
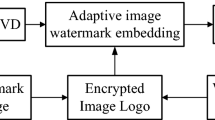
Abstract
In recent times, data security is an emerging and highly challenging issue due to the rapid growth of digital technologies and their uses. Copyright protection can be considered as one of the major security concerns for digital data (e.g., images), and efficient security techniques are needed to provide effective solutions. Digital watermarking is extensively used for protection of copyrights and ownership. This work proposes a transform domain-based robust image watermarking scheme for color and gray images. The watermarking scheme uses the concept of tunable Q-factor wavelet transform (TQWT), discrete cosine transform (DCT), logistic mapping and antlion optimization (ALO). The host image (Y channel of YCbCr color space in case of a color image) is first transformed using TQWT transform, and the low frequency subband is selected. DCT transform is applied on each elected block, and the selected DCT coefficient is modified based on the watermark bit. The logistic mapping-based approach is employed to encrypt the watermark information before embedding. The ALO optimization is used on a large data set (including different types of images) to get optimize parametric values (Q-factor, redundancy and embedding strength). Experimental results show that the scheme has significant imperceptibility, high robustness, high security, low processing time and acceptable embedding capacity. Investigational results and relative comparisons confirm that the proposed scheme has superior performance as compared to other recently proposed schemes.









Similar content being viewed by others
Data Availability
The dataset used is publicly available on the internet.
Code Availability
The code will be made available on reasonable demand.
References
L. Abualigah, M. Shehab, M. Alshinwan et al., Ant lion optimizer: a comprehensive survey of its variants and applications. Arch. Comput. Methods Eng. 28, 1397–1416 (2021). https://doi.org/10.1007/S11831-020-09420-6/TABLES/3
M. Ali, C.W. Ahn, P. Siarry, Differential evolution algorithm for the selection of optimal scaling factors in image watermarking. Eng. Appl. Artif. Intell. 31, 15–26 (2014). https://doi.org/10.1016/J.ENGAPPAI.2013.07.009
I.A. Ansari, M. Pant, C.W. Ahn, ABC optimized secured image watermarking scheme to find out the rightful ownership. Optik (Stuttg) 127, 5711–5721 (2016). https://doi.org/10.1016/j.ijleo.2016.03.070
I.A. Ansari, M. Pant, C.W. Ahn, J. Jeong, PSO optimized multipurpose image watermarking using SVD and chaotic sequence, in Communications in Computer and Information Science. (Springer, Berlin, 2015), pp. 1–17
F. Arab, S.M. Abdullah, S.Z.M. Hashim et al., A robust video watermarking technique for the tamper detection of surveillance systems. Multimed. Tools Appl. 75, 10855–10885 (2016). https://doi.org/10.1007/S11042-015-2800-5/TABLES/13
T.K. Araghi, A. Bt, A. Manaf et al., A survey on digital image watermarking techniques in spatial and transform domains. Int. J. Adv. Image Process Tech. 3(1), 6–10 (2016)
A.S. Assiri, A.G. Hussien, M. Amin, Ant lion optimization: variants, hybrids, and applications. IEEE Access 8, 77746–77764 (2020). https://doi.org/10.1109/ACCESS.2020.2990338
M. Barni, F. Bartolini, V. Cappellini, A. Piva, A DCT-domain system for robust image watermarking. Signal Process 66, 357–372 (1998). https://doi.org/10.1016/S0165-1684(98)00015-2
C. Das, S. Panigrahi, V.K. Sharma, K.K. Mahapatra, A novel blind robust image watermarking in DCT domain using inter-block coefficient correlation. AEU—Int. J. Electron Commun. 68, 244–253 (2014). https://doi.org/10.1016/J.AEUE.2013.08.018
F. Ernawan, M.N. Kabir, A block-based RDWT-SVD image watermarking method using human visual system characteristics. Vis. Comput. 36, 19–37 (2020). https://doi.org/10.1007/S00371-018-1567-X/FIGURES/10
K. Hameed, A. Khan, M. Ahmed et al., Towards a formally verified zero watermarking scheme for data integrity in the internet of things based-wireless sensor networks. Futur. Gener. Comput. Syst. 82, 274–289 (2018). https://doi.org/10.1016/J.FUTURE.2017.12.009
M. Hamidi, H.M. El, H. Cherifi, H.M. El, Hybrid blind robust image watermarking technique based on DFT-DCT and Arnold transform. Multimed. Tools Appl. 77, 27181–27214 (2018). https://doi.org/10.1007/S11042-018-5913-9/TABLES/13
Hering H, Hagmüller M, Kubin G (2003) Safety and security increase for air traffic management through unnoticeable watermark aircraft identification tag transmitted with the VHF voice communication. In: AIAA/IEEE Digital Avionics Systems Conference—Proceedings
“Image databases,” Accessed Sep. 2020. [Online]. Available: http://www.imageprocessingplace.com/root_ files_V3/
Jagannatam A (2008) Mersenne Twister—A Pseudo random number generator and its variants. Available: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.175.9735
O.U. Juarez-Sandoval, M. Cedillo-Hernandez, M. Nakano-Miyatake et al., Digital image ownership authentication via camouflaged unseen-visible watermarking. Multimed. Tools Appl. 77, 26601–26634 (2018). https://doi.org/10.1007/s11042-018-5881-0
Kaur A, Singh P, Nayyar A (2020) Robust multimedia watermarking. In: https://services.igi-global.com/resolvedoi/resolve.aspx?doi=https://doi.org/10.4018/978-1-7998-2701-6.ch004. IGI Global, pp 73–89
C. Kumar, A.K. Singh, P. Kumar, A recent survey on image watermarking techniques and its application in e-governance. Multimed. Tools Appl. 77, 3597–3622 (2018). https://doi.org/10.1007/S11042-017-5222-8/TABLES/2
C.C. Lai, An improved SVD-based watermarking scheme using human visual characteristics. Opt. Commun. 284, 938–944 (2011). https://doi.org/10.1016/J.OPTCOM.2010.10.047
X.L. Liu, C.C. Lin, S.M. Yuan, Blind dual watermarking for color images’ authentication and copyright protection. IEEE Trans. Circuits Syst. Video Technol. 28, 1047–1055 (2018). https://doi.org/10.1109/TCSVT.2016.2633878
Y. Liu, S. Tang, R. Liu et al., Secure and robust digital image watermarking scheme using logistic and RSA encryption. Expert. Syst. Appl. 97, 95–105 (2018). https://doi.org/10.1016/J.ESWA.2017.12.003
C. Lu, Multimedia security: steganography and digital watermarking techniques for protection of intellectual property. Choice Rev. Online (2004). https://doi.org/10.5860/choice.42-2260
N.M. Makbol, B.E. Khoo, T.H. Rassem, Block-based discrete wavelet transform-singular value decomposition image watermarking scheme using human visual system characteristics. IET Image Process 10, 34–52 (2016). https://doi.org/10.1049/iet-ipr.2014.0965
M. Matsumoto, T. Nishimura, Mersenne Twister: A 623-dimensionally equidistributed uniform pseudo-random number generator, in ACM Transactions on Modeling and Computer Simulation. (ACM PUB27, New York, NY, USA, 1998), pp. 3–30
S. Mirjalili, The ant lion optimizer. Adv. Eng. Softw. 83, 80–98 (2015). https://doi.org/10.1016/J.ADVENGSOFT.2015.01.010
M. Moosazadeh, G. Ekbatanifard, A new DCT-based robust image watermarking method using teaching-learning-based optimization. J. Inf. Secur. Appl. 47, 28–38 (2019). https://doi.org/10.1016/J.JISA.2019.04.001
N. Nikolaidis, I. Pitas, Robust image watermarking in the spatial domain. Signal Process. 66, 385–403 (1998). https://doi.org/10.1016/S0165-1684(98)00017-6
A. Nishad, R.B. Pachori, U.R. Acharya, Application of TQWT based filter-bank for sleep apnea screening using ECG signals. J. Ambient. Intell. Humaniz Comput. 1, 1–12 (2018). https://doi.org/10.1007/S12652-018-0867-3/TABLES/4
Nwaiwu F, Kwarteng MA, Jibril AB, et al (2020) Impact of security and trust as factors that influence the adoption and use of digital technologies that generate, collect and transmit user data. In: ICCWS 2020 15th International Conference on Cyber Warfare and Security
J.H. Park, S.E. Jeong, C.S. Kim, Robust and Fragile watermarking techniques for documents using bi-directional diagonal profiles. Lect. Notes Comput. Sci. (including Subser Lect Notes Artif Intell Lect Notes Bioinformatics) 2229, 483–494 (2001). https://doi.org/10.1007/3-540-45600-7_55/COVER/
A. Pourhadi, H. Mahdavi-Nasab, A robust digital image watermarking scheme based on bat algorithm optimization and SURF detector in SWT domain. Multimed. Tools Appl. 79, 21653–21677 (2020). https://doi.org/10.1007/S11042-020-08960-0/TABLES/6
M. Saito, M. Matsumoto, SIMD-oriented fast mersenne twister: a 128-bit pseudorandom number generator. Monte Carlo Quasi-Monte Carlo Methods 2006, 607–622 (2008). https://doi.org/10.1007/978-3-540-74496-2_36/COVER/
Selesnick IW (2011) TQWT toolbox guide. Electrical and Computer Engineering Polytechnic Institute of New York University (2011). Available online: https://eeweb.engineering.nyu.edu/iselesni/TQWT/TQWT_guide.pdf
Selesnick IW (2011) Sparse signal representations using the tunable Q-factor wavelet transform. In: Wavelets and Sparsity XIV.8138,477-491,SPIE (2011). https://doi.org/10.1117/12.894280
F.Y. Shih, Digital Watermarking and Steganography: FUNDAMENTALS and Techniques, (second edition) (CRC Press, USA, 2017)
A.K. Singh, B. Kumar, G. Singh, A. Mohan, Medical Image Watermarking: Techniques and Applications, Book Series on Multimedia Systems and Applications (Springer, USA, 2017)
P. Singh, B. Raman, P.P. Roy, A multimodal biometric watermarking system for digital images in redundant discrete wavelet transform. Multimed. Tools Appl. 76, 3871–3897 (2017). https://doi.org/10.1007/S11042-016-4048-0/FIGURES/21
P. Singh, B. Raman, P.P. Roy, Detection of seal and signature entities with hierarchical recovery based on watermark self embedding in tampered digital documents. Displays 54, 47–59 (2018). https://doi.org/10.1016/J.DISPLA.2018.09.004
R. Sinhal, D.K. Jain, I.A. Ansari, Machine learning based blind color image watermarking scheme for copyright protection. Pattern Recognit. Lett. 145, 171–177 (2021). https://doi.org/10.1016/J.PATREC.2021.02.011
V. Sisaudia, V.P. Vishwakarma, Copyright protection using KELM-PSO based multi-spectral image watermarking in DCT domain with local texture information based selection. Multimed. Tools Appl. 80, 8667–8688 (2021). https://doi.org/10.1007/S11042-020-10028-Y/TABLES/6
A. Subasi, S.M. Qaisar, Surface EMG signal classification using TQWT, bagging and boosting for hand movement recognition. J. Ambient Intell. Humaniz. Comput. 13, 3539–3554 (2020). https://doi.org/10.1007/S12652-020-01980-6/TABLES/9
Y. Tang, M. Zhu, Z. Chen et al., Seismic performance evaluation of recycled aggregate concrete-filled steel tubular columns with field strain detected via a novel mark-free vision method. Structures 37, 426–441 (2022). https://doi.org/10.1016/J.ISTRUC.2021.12.055
H.H. Tsai, Y.J. Jhuang, Y.S. Lai, An SVD-based image watermarking in wavelet domain using SVR and PSO. Appl. Soft. Comput. 12, 2442–2453 (2012). https://doi.org/10.1016/J.ASOC.2012.02.021
USC-SIPI image database, Available online at: https://sipi.usc.edu/database/.
W.C. Peng, W.X. Yuan, C.X. Jun, C. Zhang, Robust zero-watermarking algorithm based on polar complex exponential transform and logistic mapping. Multimed. Tools Appl 76, 26355–26376 (2017). https://doi.org/10.1007/S11042-016-4130-7/TABLES/7
F. Wu, J. Duan, S. Chen et al., Multi-target recognition of bananas and automatic positioning for the inflorescence axis cutting point. Front. Plant Sci. (2021). https://doi.org/10.3389/sFPLS.2021.705021
Funding
Not Applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sinhal, R., Ansari, I.A. Tunable Q-Factor Wavelet Transform-Based Robust Image Watermarking Scheme Using Logistic Mapping and Antlion Optimization. Circuits Syst Signal Process 41, 6370–6410 (2022). https://doi.org/10.1007/s00034-022-02090-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-022-02090-8