Abstract
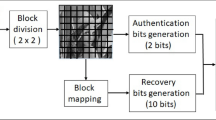
Image watermarking has been evidenced as a powerful tool for copyright protection and authentication applications. In this work, a novel approach, for colour image content authentication and restoration, is introduced. The proposed scheme is based on utilizing the wavelet-packets decomposition to perform semi-fragile watermarking for colour image authentication and recovery. The obtained wavelet packets, from each colour layer, are used to construct the so called spatio-frequency chains that are split into four common-featured containers. These containers are treated mutually to construct the inter-colour containers; then, the robust content-dependent watermark is embedded by modifying only locations when the image content is properly secure to hold mark bits. The recovery stage is based on embedding recovery bits, using a modified quantization-based approach. Simulations have shown that the proposed scheme exhibits a high robustness performance in the presence of different moderate-to-severe incident attacks, while, it has demonstrated a high authentication performance in the presence of several malicious attacks including cropping and object manipulations with the unauthentic regions being properly recovered.
























Similar content being viewed by others
Data Availability
This is to state that: the datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
Notes
Here, the number 4 represents half of the number of pixels within the 3 × 3 window with excluding the center pixel.
References
H.M. Al-Otum, A.W. Alansari, Image watermarking for tamper detection and content recovery applications based on a preservative bi-level moment approach with shuffling, in Proceedings of the 2019 5th International Conference on Computer and Technology Applications. ACM (2019)
H.M. Al-Otum, M. Ibrahim, Color image watermarking for content authentication and self-restoration applications based on a dual-domain approach. Multimed. Tools Appl. 80(8), 11739–11764 (2021)
H.M. Al-Otum, O.R. Qasaimeh, Novel watermarking technique based on the generalized squared interpoint distance for image copyright protection applications. J. Electron. Imaging 20(3), 033014 (2011)
H.M. Al-Otum, Semi-fragile watermarking for grayscale image authentication and tamper detection based on an adjusted expanded-bit multiscale quantization-based technique. J. Vis. Commun. Image Represent. 25(5), 1064–1081 (2014)
H.M. Al-Otum, Wavelet packets-based watermarking with preserved high color image quality and enhanced robustness for copyright protection applications. Multimed. Tools Appl. 78(2), 2199–2225 (2019)
A. Al-Gindy, H. Younes, A. Shaleen, A. Elsadi, A graphical user interface watermarking technique for the copyright protection of colour images using colour watermarks, in IEEE International Symposium on Signal Processing and Information Technology (ISSPIT). Bilbao, pp. 354–358 (2011)
G. Bhatnagar, B. Raman, Wavelet packet transform-based robust video watermarking technique. Sadhana 37(3), 371–388 (2012)
D. Blackman, V. Sebastiano, Scrambled linear pseudorandom number generators. Preprint http://arxiv.org/abs/1805.01407 (2018)
C.H. Chen et al., Image tamper detection and recovery by intersecting signatures. Telkomnika 12(4), 1123 (2014)
R.R. Coifman, Y. Meyer, S. Quake, M.V. Wickerhauser, Signal processing and compression with wavelet packet, in Wavelets and their applications (pp. 363–379). Springer, Dordrecht (1994)
J. Cong, et al. A wavelet packets watermarking algorithm based on chaos encryption, in International Conference on Computational Science and Its Applications. Springer, Berlin, Heidelberg (2006)
W. Dietl, A. Uhl, Watermark security via secret wavelet packet subband structures, in IFIP International Conference on Communications and Multimedia Security. Springer, Berlin, Heidelberg (2003)
M.Q. Fan, H.X. Wang, An enhanced fragile watermarking scheme to digital image protection and self-recovery. Signal Process. Image Commun. 66, 19–29 (2018)
S. Fazli, M. Moeini, A robust image watermarking method based on DWT, DCT, and SVD using a new technique for correction of main geometric attacks. Optik-Int. J. Light Electron Opt. 127(2), 964–972 (2016)
O. Hemida, H. He, A self-recovery watermarking scheme based on block truncation coding and quantum chaos map. Multimed. Tools Appl. 79, 1–31 (2020)
K.C. Liu, Self-embedding watermarking scheme for colour images by bi-level moment-preserving technique. IET Image Proc. 8(6), 363–372 (2014)
M.N. Maatouk, A.N. Amara, Intelligent hybrid watermarking ancient-document wavelet packet decomposition-singular value decomposition-based schema. IET Image Proc. 8(12), 708–717 (2014)
J. Molina-Garcia et al. An effective fragile watermarking scheme for color image tampering detection and self-recovery. Signal Processing: Image Communication (2020)
F.A.P. Petitcolas et al. Public automated web-based evaluation service for watermarking schemes: Stirmark benchmark. Security and Watermarking of Multimedia Contents III. Vol. 4314. International Society for Optics and Photonics (2001)
T.E. Posch, The wavelet packet transform (WPT) as applied to signal processing, in Proceedings of the IEEE-SP International Symposium on Time-Frequency and Time-Scale Analysis. IEEE (1992)
C. Qin et al., Self-embedding fragile watermarking based on reference-data interleaving and adaptive selection of embedding mode. Inf. Sci. 373, 233–250 (2016)
C. Qin et al., Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Signal Process. 138, 280–293 (2017)
S. Rawat, B. Raman, Best tree wavelet packet transform based copyright protection scheme for digital images. Opt. Commun. 285(10–11), 2563–2574 (2012)
L. Rosales-Rolda et al. Semi-fragile watermarking-based color image authentication with recovery capability, in 2015 38th International Conference on Telecommunications and Signal Processing (TSP). IEEE (2015)
P.A. Shabir et al., Robust and blind watermarking technique in DCT domain using inter-block coefficient differencing. Digital Signal Process. 53, 11–24 (2016)
F.Y. Shih, Digital Watermarking and Steganography: Fundamentals and Techniques (CRC Press, 2017)
D. Singh, S.K. Singh, DCT based efficient fragile watermarking scheme for image authentication and restoration. Multimed. Tools Appl. 76(1), 953–977 (2017). https://doi.org/10.1007/s11042-015-3010-x
L. Singh, A.K. Singh, P.K. Singh, Secure data hiding techniques: a survey. Multimed. Tools Appl. 79, 1–21 (2018)
R.K. Singh, D.K. Shaw, M.J. Alam, Experimental studies of LSB watermarking with different noise. Procedia Comput. Sci. 54, 612–620 (2015)
R.C. Streijl, S. Winkler, D.S. Hands, Mean opinion score (MOS) revisited: methods and applications, limitations and alternatives. Multimed. Syst. 22(2), 213–227 (2016)
K. Swaraja, K. Meenakshi, P. Kora, An optimized blind dual medical image watermarking framework for tamper localization and content authentication in secured telemedicine. Biomed. Signal Process. Control 55, 101665 (2020)
T.B. Taha, R. Ngadiran, P. Ehkan, Adaptive image watermarking algorithm based on an efficient perceptual mapping model. IEEE Access 6, 66254–66267 (2018)
W.L. Tai, Z.J. Liao, Image self-recovery with watermark self-embedding. Signal Process. Image Commun. 65, 11–25 (2018)
N. Tarhouni, M. Charfeddine, C. Ben Amar, Novel and robust image watermarking for copyright protection and integrity control. Circuits Syst. Signal Process 39, 5059–5103 (2020). https://doi.org/10.1007/s00034-020-01401-1
G. Thirugnanam, S. Arulselvi, Wavelet packet based robust digital image watermarking and extraction using independent component analysis. Int. J. Signal Image Process. 1, 2 (2010)
X. Tong et al., A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Process. Image Commun. 28(3), 301–308 (2013)
J. Wang et al., Color image watermarking based on orientation diversity and color complexity. Expert Syst. Appl. 140, 112868 (2020)
Q. Ying et al., Robust digital watermarking for color images in combined DFT and DT-CWT domains. Math. Biosci. Eng. MBE 16(5), 4788–4801 (2019)
Y. Zhang, Y. Li, Y. Sun, Digital watermarking based on joint DWT–DCT and OMP reconstruction. Circuits Syst. Signal Process 38, 5135–5148 (2019). https://doi.org/10.1007/s00034-019-01112-2
Funding
None. No funding to declare.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors have no conflict of interest to report.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Al-Otum, H.M. Colour Image Authentication and Recovery Using Wavelet Packets Watermarking. Circuits Syst Signal Process 41, 3222–3264 (2022). https://doi.org/10.1007/s00034-021-01927-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-021-01927-y