Abstract
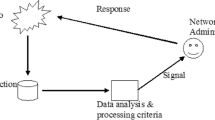
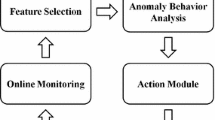
A novel constant false alarm rate (CFAR) intrusion detection method based on stochastic resonance (SR) is proposed in this paper. Using the SR technique improves the spectral power (SP) and the signal-to-noise ratio (SNR) of the network intrusion signal, hence enhancing the detectability of network attacks. The threshold and the detection probability of the proposed SR-CFAR method are derived theoretically. Computer simulations based on standard Defense Advanced Research Projects Agency (DARPA) network intrusion data show that this CFAR method outperforms the linear anomaly intrusion detection methods for various types of intrusions.
Similar content being viewed by others
References
V.S. Anishchenko, V.V. Astakhov, A.B. Neiman, T.E. Vadivasova, L. Schimansky-Geier, Nonlinear Dynamics of Chaotic and Stochastic Systems: Tutorial and Modern Developments (Springer, Berlin, 2002)
P.R. Chang, J.T. Hu, Optimal nonlinear adaptive prediction and modeling of MPEG video in ATM networks using pipelined recurrent neural networks. IEEE J. Sel. Areas Commun. 15(6), 1087–1100 (1997)
B.S. Chen, S.C. Peng, K.C. Wang, Traffic modeling, prediction, and congestion control for high-speed networks: a fuzzy AR approach. IEEE Trans. Fuzzy Syst. 8(5), 491–508 (2000)
R.K. Cunningham, R.P. Lippmann, S.E. Webster, Detecting and displaying novel computer attacks with Macroscope. IEEE Trans. Syst. Man, Cybern. A 31(4), 275–281 (2001)
A.K. Dhara, Enhancement of signal-to-noise ratio. J. Stat. Phys. 87(1–2), 251–271 (1997)
R.F. Erbacher, K.L. Walker, D.A. Frincke, Intrusion and misuse detection in large-scale systems. IEEE Comput. Graph. Appl. 22(1), 38–47 (2002)
D.J. Evans, G.P. Morriss, Statistical Mechanics of Nonequilibrium Liquids (Academic, London, 1990)
K. Gerlach, Spatially distributed target detection in non-Gaussian clutter. IEEE Trans. Aerosp. Electron. Syst. 35(3), 926–934 (1999)
G.P. Harmer, B.R. Davis, D. Abbott, A review of stochastic resonance: circuits and measurement. IEEE Trans. Instrum. Meas. 51(2), 299–309 (2002)
D. He, H. Leung, A novel CFAR intrusion detection method using chaotic stochastic resonance. IEEE 2004 Int. Symp. Circuits Syst. Proc. 4, 589–592 (2004)
C. Herringshaw, Detecting attacks on networks. Computer 30(12), 16–17 (1997)
K. Ilgun, R.A. Kemmerer, P.A. Porras, State transition analysis: a rule-based intrusion detection approach. IEEE Trans. Softw. Eng. 21(3), 181–199 (1995)
A. Karasaridis, D. Hatzinakos, Network heavy traffic modeling using α-stable self-similar processes. IEEE Trans. Commun. 49(7), 1203–1214 (2001)
R.A. Kemmerer, G. Vigna, Intrusion detection: a brief history and overview. Computer 35(4), 27–30 (2002)
S. Kent, On the trail of intrusions into information systems. IEEE Spectr. 37(12), 52–56 (2000)
A.P. Kosoresow, S.A. Hofmeyer, Intrusion detection via system call traces. IEEE Softw. 14(5), 35–42 (1997)
S.C. Lee, D.V. Heinbuch, Training a neural-network based intrusion detector to recognize novel attacks. IEEE Trans. Syst. Man Cybern. A 31(4), 294–299 (2001)
J. McHugh, A. Christie, J. Allen, Defending yourself: the role of intrusion detection systems. IEEE Softw. 17(5), 42–51 (2000)
S. Mitaim, B. Kosko, Adaptive stochastic resonance. Proc. IEEE 86(11), 2152–2183 (1998)
O. Oliaei, Stochastic resonance in sigma-delta modulators. Electron. Lett. 39(2), 173–174 (2003)
Y. Qiao, X.W. Xin, Y. Bin, S. Ge, Anomaly intrusion detection method based on HMM. Electron. Lett. 38(13), 663–664 (2002)
S.P. Shieh, V.D. Gligor, On a pattern-oriented model for intrusion detection. IEEE Trans. Knowl. Data Eng. 9(4), 661–667 (1997)
R. Srinivasan, Simulation of CFAR detection algorithms for arbitrary clutter distributions. IEE Proc. Radar Sonar Navig. 147(1), 31–40 (2000)
K.M.C. Tan, R.A. Maxion, Determining the operational limits of an anomaly-based intrusion detector. IEEE J. Sel. Areas Commun. 21(1), 96–110 (2003)
N. Ye, X.Y. Li, Q. Chen, S.M. Emran, M.M. Xu, Probabilistic techniques for intrusion detection based on computer audit data. IEEE Trans. Syst. Man Cybern. A 31(4), 266–274 (2001)
N. Ye, S.M. Emran, Q. Chen, S. Vilbert, Multivariate statistical analysis of audit trails for host-based intrusion detection. IEEE Trans. Comput. 51(7), 810–820 (2002)
S. Zozor, P.O. Amblard, Stochastic resonance in discrete time nonlinear AR(1) models. IEEE Trans. Signal Process. 47(1), 108–122 (1999)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
He, D., Leung, H. Network Intrusion Detection Using a Stochastic Resonance CFAR Technique. Circuits Syst Signal Process 28, 361–375 (2009). https://doi.org/10.1007/s00034-008-9087-y
Received:
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-008-9087-y