Abstract
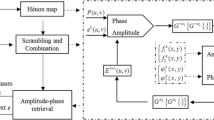
A novel four-image encryption scheme based on the quaternion Fresnel transforms (QFST), computer generated hologram and the two-dimensional (2D) Logistic-adjusted-Sine map (LASM) is presented. To treat the four images in a holistic manner, two types of the quaternion Fresnel transform (QFST) are defined and the corresponding calculation method for a quaternion matrix is derived. In the proposed method, the four original images, which are represented by quaternion algebra, are processed holistically in a vector manner by using QFST first. Then the input complex amplitude, which is constructed by the components of the QFST-transformed plaintext images, is encoded by Fresnel transform with two virtual independent random phase masks (RPM). In order to avoid sending entire RPMs to the receiver side for decryption, the RPMs are generated by utilizing 2D–LASM, which results that the amount of the key data is reduced dramatically. Subsequently, by using Burch’s method and the phase-shifting interferometry, the encrypted computer generated hologram is fabricated. To improve the security and weaken the correlation, the encrypted hologram is scrambled base on 2D–LASM. Experiments demonstrate the validity of the proposed image encryption technique.





















Similar content being viewed by others
References
Akhshani A, Behnia S, Akhavan A, Abu Hassan H, Hassan Z (2010) A novel scheme for image encryption based on 2D piecewise chaotic maps. Opt Commun 283:3259–3266
Belazi A, El-Latif AAA, Diaconu AV, Rhouma R, Belghit S (2017) Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt Lasers Eng 88:37–50
Cai LZ, Liu Q, Yang XL (2003) Phase-shift extraction and wave-front reconstruction in phase-shifting interferometry with arbitrary phase steps. Opt Lett 28(19):1808–1810
Chen BJ, Shu HZ, Coatrieux G, Chen G, Sun XM, Coatrieux JL (2015) Color image analysis by quaternion-type moments. J Math Imaging Vision 51:124–144
Fu ZJ, Huang FX, Sun XM, Vasilakos AV, Yang CN (2016) Enabling semantic search based on conceptual graphs over encrypted outsourced data. IEEE Trans Serv Comput. doi:10.1109/TSC.2016.2622697
Gonzalez RC, Woods RE (2007) Digital image processing, 3rd edn. Prentice Hall, New Jersey, USA Chapter 5
Hua ZY, Zhou YC (2016) Image encryption using 2D Logistic-adjusted-Sine map. Inf Sci 339:237–253
Li J, Chen XF, Li MQ, Li JW, Lee P, Lou WJ (2014) Secure deduplication with efficient and reliable convergent key management. IEEE Trans Parallel Distrib Syst 25:1615–1625
Li J, Li JW, Chen XF, Jia CF, Lou WJ (2015) Identity-based encryption with outsourced revocation in cloud computing. IEEE Trans Comput 64:425–437
Li J, Yan HY, Liu ZL, Chen XF, Huang XY, Wong DS Location-sharing systems with enhanced privacy in mobile online social networks. IEEE Sys J. doi:10.1109/JSYST.2015.2415835
Liu ZJ, Zhang Y, Zhao HF et al (2011) Optical multi-image encryption based on frequency shift. Optik 122:1010–1013
Liu Q, Cai WD, Shen J, Fu ZJ, Liu XD, Linge N (2016) A speculative approach to spatial-temporal efficiency with multi-objective optimization in a heterogeneous cloud environment. Secur Commun Networks 9:4002–4012
Nischal NK, Joseph J, Singh K (2004) Securing information using fractional Fourier transform in digital holography. Opt Commun 235:253–259
Refregier P, Javidi B (1995) Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett 20:767–769
Shao ZH, Shu HZ, Wu JS, Dong ZF, Coatrieux G, Coatrieux JL (2014) Double color image encryption using iterative phase retrieval algorithm in quaternion gyrator domain. Opt Express 22:4932–4943
Shen JJ, Ren JM (2010) A robust associative watermarking technique based on vector quantization. Digital Signal Process 20:1408–1423
Singh N, Sinha A (2008) Optical image encryption using fractional Fourier transform and chaos. Opt Lasers Eng 46:117–123
Situ GH, Zhang JJ (2004) Double random-phase encoding in the Fresnel domain. Opt Lett 29:1584–1586
Todd AE, Stephen JS (2007) Hypercomplex Fourier transforms of color images. IEEE Trans Image Process 16(2):22–35
Tudela R, Badosa EM, Labastida I, Vallmitjana S, Juvells I, Carnicer A (2003) Full complex Fresnel holograms displayed on liquid crystal devices. J Opt A Pure Appl Opt 5:S189–S194
Wang Q, Guo Q, Lei L (2013) Double image encryption based on phase-amplitude mixed encoding and multistage phase encoding in gyrator transform domains. Opt Laser Technol 48:267–279
Wang Y, Quan C, Tay CJ (2015) Optical color image encryption without information disclosure using phase-truncated Fresnel transform and a random amplitude mask. Opt Commun 344:147–155
Xia ZH, Wang XH, Zhang LG, Qin Z, Sun XM, Ren K (2016) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensics Secur 11:2594–2608
Xie EY, Li C, Yu S, Lü J (2017) On the cryptanalysis of Fridrich's chaotic image encryption scheme. Signal Process 132:150–154
Yu ZL, Jin GF (1984) Computer-generated hologram. Tsinghua University Press, Beijing Chap. 4
Yuan S, Xin YH, Liu MT, Yao SX, Sun XJ (2012) An improved method to enhance the security of double random-phase encoding in the Fresnel domain. Opt Laser Technol 44:51–56
Zhang S, Weide DVD, Oliver J (2010) Superfast phase-shifting method for 3-D shape measurement. Opt. Express 18(9):9684–9689
Zheng YH, Jeon B, Xu DH, Wu QM, Zhang H (2015) Image segmentation by generalized hierarchical fuzzy C-means algorithm. J Intell Fuzzy Syst 28:961–973
Zhou ZL, Yang CN, Chen BJ, Sun XM, Liu Q, Wu QM (2016) Effective and efficient image copy detection with resistance to arbitrary rotation. IEICE Trans Inf Syst E99-D:1531–1540
Acknowledgments
This work is partly supported by the Natural Science Foundation of Guangdong Province (No. 2014A030310038), the Educational Commission of Guangdong Province (No. 2013KJCX0127, No. 2015KTSCX089), the Fundamental Research Funds for the Central Universities (No. 20720160016), the Science and Technology Planning Project of Chaozhou (No. 2013G01), and the Research Fund of Hanshan Normal University (No. LT201201).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yu, C., Li, J., Li, X. et al. Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77, 4585–4608 (2018). https://doi.org/10.1007/s11042-017-4637-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4637-6