Abstract
Purpose
Computer-assisted audit techniques (CAATs) are used by auditors to automate some of their tasks. Since most transactions in accounting are computerized, auditing of accounting data follows this process as well. During the last two decades, many studies on technology acceptance have been published, and several new models proposed. This study aims to develop and empirically test a model to predict the factors affecting internal auditors’ behavioral intentions regarding CAATs.
Design/methodology/approach
This study explored the behavioral intention to use CAATs from the perspective of internal auditors by applying the extended unified theory of acceptance and use of technology (UTAUT) model. Added to this were satisfaction, trust, and organizational influence to understand people’s usage traits. Through an online survey the data were gathered from internal auditors in all Saudi public sector agencies. Structural equation modeling helped to analyze the data and support hypotheses or otherwise.
Findings
Effort expectancy, performance expectancy, social and organizational influences, facilitating conditions, trust, satisfaction, and behavioral intention are the main drivers of CAATs.
Practical implications
This study contributes to existing technology theory by expanding our understanding of the factors influencing CAATs adoption. Moreover, comprehending those determinants is extremely important to legislators. regulators and policymakers in the public sector. This study increases our knowledge about the adoption of CAATs by addressing it at the individual level instead of the organizational level. The results are consistent with the UTAUT model and deliver a practical reference for public sector officials and decision-makers involved in designing CAATs for government departments.
Similar content being viewed by others
Introduction
The last two decades have witnessed a substantial increase in Information Technology (IT) acceptance in most sectors of the economy [25, 70, 85]. As a consequence of the day-to-day process of automation, operation and overheads expenses have fallen, while productivity has risen. There have been significant breakthroughs in the speed and efficiency of transaction processing as a result of this [8, 50, 85]. These are the techniques and processes used by auditors to collect and evaluate relevant data [9, 17, 48, 70, 85]. These tools are employed by auditors to carry out relevant procedures, such as browsing, analyzing, sorting, summarizing, stratifying, sampling, performing computations, converting, and other data extraction and data analysis tasks [2, 3, 9, 66]. According to Siew et al. [85], the low or slow rate of CAATs implementation in economically developing countries requires more detailed consideration from practitioners, policymakers, and researchers.
In the information system (IS) research area, post-adoption IT behavior intentions are now very much the focus of attention (see [13, 25, 67, 88, 99]). Various strategies have been used to encourage prospective users to embrace innovations, and behavioral intention of users determine adoption of innovative technologies for auditing tasks. In this study, the model devised by Venkatesh et al. [99] is extended to highlight the post-adoption behavioral intentions of CAATs users. Currently, there is a lack of empirical studies that distinguish between users' before and post-adoption beliefs and attitudes [20, 91, 99, 100]. This distinction is critical in reinforcing the comprehension and administration of technology-related events [13]. An adopter's attitude/ use of technology hinges on a variety of factors, such as ease of use, perception of usability, demonstrability of outcomes, trialability, visibility, etc. [51, 99, 100]. Researchers who have devoted their work to understanding users’ behaviors [46] and cognitive dissonance theories [29] have suggested various explanations. Generally, however, they confirmed that product use can alter an individual's perception, attitude, and need.
Deploying CAATs as an IS is now compulsory for delivering services competently, improving efficiency, making good decisions, and managing procedures or routines [13, 25, 67]. In other words, the application of CAATs is vital for generating best practices and maintaining them. Auditing information and its process provided by CAATs is required by decision-makers to establish and predict the organization’s strategic objectives [9, 17, 85]. When used successfully and effectively, CAATs can significantly improve the organization's performance and objectives. While auditors’ awareness of the many advantages (strategic and operational) of CAAT implementation is high, current research reveals that acceptance rates have not increased as predicted, especially with reference to internal auditing [9, 58, 66]. Hence, internal audit units have so far been unable to completely incorporate CAAT into their duties. The advantages of CAATs have been studied recently [17, 70, 85]. Yet it seems that fewer researchers have looked into the adoption and use of CAAT within the internal audit function. A few studies have tried to examine CAAT adoption by focusing on large organizational and environmental variables rather than on the behavior of individuals [9, 17, 85]. Al-Saedi et al. [10] and Chao [25] argue that it is critical to investigate IT adoption at the individual level.
CAATs employment in internal audits has evident consequences [85]. Auditor efficiency, accuracy and effectiveness improve with the use of CAATs. Nevertheless, concerns regarding the high cost of implementing CAATs and the time it takes to set up the systems are key issues. When employing CAATs, it is important to be aware of concerns about client consent and the possibility of cyber-attack or hacking [42]. With this in mind, this paper focuses on internal audit function and CAATs in Saudi Arabia (KSA). KSA is presently encountering challenges linked to technology accessibility and ineffective management. As a result of such issues, employee performance suffers and compromises productivity [17]. The end result may actually be to revert to paper-based information management and documentation.
Comprehending user behavior is necessary for organizations to reap the benefits of IT [83]. Long-term viability of new information systems (ISs) mainly depends on the users’ behavioral intention rather than their primary adoption decisions [100]. There is a perceived lack of understanding of CAATs [14]. Numerous factors such as these affect user retention and user demand for CAATs [11]. Limited research has been published on the behavioral aspects of IT implementation as it applies to external auditors [2, 78, 85, 88]. There is also only limited research on behavioral intentions of internal auditors in relation to CAATs [17, 55].
User acceptability is critical to the successful adoption of any information technology [33]. During the last few decades, numerous theoretical models have been created in psychology, ISs, and sociology to predict and explain users’ adoption of IT or ISs. According to Chauhan and Jaiswal [26] and Cimperman et al. [28], the technology acceptance model (TAM) is one of the most commonly used frameworks in the IT and IS fields. Yet some researchers [81, 88, 96] have argued that the TAM has several disadvantages, such as: (1) not providing good insight into individuals' perspectives of novel systems, (2) neglecting its indicators and directly investigating the external variables of perceived usability (PEOU and perceived usefulness (PU; and (3 ignoring the relationship between usage attitude and intention of use. Venkatesh et al. [99] integrated core elements from eight models and prominent theories (including the theory of reasoned action [TRA], innovation diffusion theory [IDT], theory of planned behavior [TPB], the TAM], the combined TAM-TPB, the motivational model (MM), the model of PC utilization [MPCU], and social cognitive theory [SCT]) to predict or explain new technological developments. They did this to address the weaknesses of the TAM variant.
In various fields such as interactive whiteboards [52], near-field communication technology [88, 89], mobile health [45], home telehealth services [28], and acceptance of ERP, the UTAUT model has been applied and tested extensively since its introduction for predicting system usage as well as making technology acceptable [26]. The UTAUT model has been the subject of a great deal of applied study. This model offers a framework for explaining IT and IS adoption and the actual utilization of these systems and technologies. The UTAUT model contributes to the investigation of technology acceptance and usage due to its capacity to incorporate various TAMs [99]. For these reasons, this study utilized the UTAUT model to assess the impact of technological variables on CAATs uptake.
Despite its structure, this model has been criticized for its inability to explain individuals' acceptance of technology-based systems. This critique is understandable given the fact that both humans and technology are continually developing. The initial UTAUT model should, according to some scholars, be expanded depending on the nature of the research. Some tried to alleviate concerns about the model's capacity to forecast individual acceptance of technologically based solutions by adding factors. The addition of other internal and external elements that might improve the model's ability to predict the adoption of technology-based systems is suggested by several researchers [61, 67, 90]. Toolkits for CAATs handling large amounts of data may be used to audit financial data, control the risk management in the organisation, among other things. Consequently, CAATs have a wide range of consumers and are put to many uses. For financial data processing, research, and any inaccuracy that might impact an organisation's situation, CAATs tools are employed.
The original UTAUT model is intended to play a significant role in the acceptance and use of CAATs tools for the objectives of this research. Several studies, for example, used the trust component as a predictor in their model [61]. Earlier research [24] has shown that trust is critical in influencing users' behavioral intentions to utilize technology-based services (such as online tax filing). Meanwhile, Khalilzadeh, Ozturk, and Bilgihan [52] revealed that trust is a crucial factor determining users’ behavioral intentions to adopt technology. [74] posited that satisfaction is critical in explaining XBRL adoption. Pedrosa et al. [70] stated that the organization has a large effect in explaining the acceptance of CAATs. Consequently, the model of UTAUT will not only be adopted in this study, but expanded by incorporating the constructs of organization influence, and trust and satisfaction components to investigate internal auditors’ behavioral intentions for CAATs users in the internal audit department.
The UTAUT was used in this study, and the trust and satisfaction components were included. To find out how users feel about using CAATs create and validate the work in the internal audit department and evaluate them. In contrast to adopting CAATs, adopting CAATs as a worldwide framework for sharing corporate information has one framework named CAATs and no other alternative. Even while CAATs are accessible for a wide range of purposes and may thus be studied differently than whether or not they can be accepted as a worldwide framework for corporate information exchange, numerous tools are available for a wide range of uses. Examination of the factors influencing them may differ from the examination of the factors that influence the adoption of CAATs as a potentially adopted global framework for transferring information in the internal audit department. The two primary objectives in this research are: (1) developing an expanded UTAUT model incorporating trust, satisfaction and Organizational Influence; and (2) testing the model to predict the factors affecting internal auditors’ behavioral intentions toward CAATs, as well as their perceived impact on individuals. These are the key contributions of this research.
The main motivation for undertaking this research is to expand our knowledge on the determinants and behavioral intention for IT in public sector agencies. This study contributes a theoretical model and experimentally tests it with internal auditors in the public sector in order to better determine the core variables of CAATs usage. The main CAATs adoption factors are supported by the findings. Moreover, comprehending those determinants is extremely important to regulatory bodies, i.e., legislators and policymakers who govern or oversee the public sector and its operations. Lastly, this study adds to the existing knowledge about the adoption of CAATs by addressing it at the individual level instead of the organizational level.
This paper is organized into seven sections. The next section is the literature review regarding CAATs. It is followed by a discussion of the theoretical framework and hypotheses are presented in section three. Methodology, data gathering and analysis techniques are explained in section four. Presentation of results and discussion are contained in section five and six, respectively. Finally, conclusions, and implications of the study’s limitations and future research are presented in section seven.
Literature review
Technology for auditing
Technology which is used for auditing is referred to as Computer-assisted Audit Tools or CAATs. This category includes traditional text/word processing tools, automated working papers, and any other software [15, 22, 70]. The "(broad) definition would encompass automated working papers and standard word processing programmes" [22] or "the use of specific software by the auditor to execute audits and accomplish auditing goals" [82]. Innovative methods, including GAS, Web 2.0, utility software, and programmed queries or scripts, etc., are taken into account when undertaking auditing assignments [50]. Data stratification, data queries, sample extractions for statistical analysis, pivot tables, missing sequence detection, identification of duplicate transactions, cross-tabulation, and calculations are some methods that are an important part of this category [50].
The phrase "computer-assisted audit techniques" first appeared in a publication in 1974 [4]. For this reason computer-based financial systems have grown significantly in recent years. Many more instruments have been devised since then [2, 17, 70] IT now greatly shapes the auditing industry. General audit software (GAS) is one of the tools most widely utilized as a computer-assisted audit approach [2]. According to Yang and Guan [102], only a handful of U.S. standards exist in relation to CAATs, for example the AICPA standards SAS No. 3, SAS No. 48 [5], and SAS No. 94 (the impact of IT on the auditor's considerations of internal control in a financial statement audit). A review of the internal control system, tests of compliance, and substantive procedures, including checks on transaction details and balances, are all part of global audit processes which employ these approaches [2, 70].
Prior studies using technology adoption models
CAATS are now generally accepted by auditors [48], and this is confirmed by several studies [30, 31, 48, 70, 85, 101]. Siew et al. [85] contend, however, that CAATs are only partially accepted, with acceptance rates varying according to a firm’s requirement and size. The use of CAATs in data analysis is now widely recognized, in part because the tools improve auditors' performance, especially when processing vast volumes of data or analyzing complicated data connections becomes necessary [8, 21, 48, 50, 70]. The Unified Theory of Acceptance and Use of Technology (UTAUT) was employed by Curtis and Payne [30] to investigate auditors' acceptance of IT. To this end, these scholars determined that long-term budget and software assessment periods and input from superiors are all closely linked to new IT acceptance and their impact on corporate procedures. When it comes to software implementation and acceptance, there are various factors such as risk and budget pressure affecting whether or not particular types of software are implemented and accepted, according to this study.
Regarding how nations organize the acceptance of CAATs into their economic systems, it is reasonable to say that their legal system, which may be based on common law or civil or code law, will decide this issue. Unlike civil law nations, where the legal system grew out of Roman law and is very much linked to government requirements, those countries with common law traditions established a legal system based on English law which is precedent-based and more investor-friendly [12, 57]. Researchers utilized a map created by these authors, which depicted a categorization of nations' legal systems, including common law and code law, as a point of reference for classifying the papers they studied. One study by Mahzan and Lymer [60] used elements similar to UTAUT, and it included "Motivation" instead of Behavioral Intention and Experience in the revised theoretical view on studying motivations for successful CAATs adoption" (novice versus expert users).
In the context of internal auditors' work, Kim et al. [55] utilized the technology acceptance model (TAM). More recent literature which has utilized TAM includes Gonzalez et al. [40], Mahzan and Lymer [60] and Kim et al. [53]. Variables such as TAM and technological characteristics [92] and tool complexity were linked to organizational, societal, and individual aspects. Support and training (both internal and external to the company) and managerial support are examples of organizational variables [55]. In terms of social variables, internalization and image indicate how people can shape IT usage [55]. Individual considerations include the importance of the work, quality of the product or service, and the presentation of outcomes [17, 54, 55]. However, internal auditors reject sophisticated features (classification, regression, and digital analysis). Kim and Mannino [54] and Kim et al. [55] both found that internal auditors accept fundamental technological features (such as database queries and sampling). The perceived ease of use diminishes as the feature set becomes more complex. Advanced features can exert a more significant impact on acceptance than basic features due to increased perceptions of usefulness and ease of use [55, 71].
Existing research has looked at a number of procedures that are carried out in relation to the use of CAATs in auditing generally. Pedrosa et al. [70] conducted their analysis based on data from Portugal and found that the drivers of adopting CAATs are perceived usefulness, facilitating conditions, number of auditors, and effort expectancy. Computer audits were shown to have an effect on the overall performance of the internal auditing process [101]. These authors investigated the usage of CAATs in the mobile communications sector in Taiwan. Their findings indicate that effective computer auditing is absolutely necessary for the internal audit department. According to Belfo and Trigo [19], CAATs are one of the most pressing accounting concerns for the future to consider. They pointed out that these tools and methods may boost productivity and capacities with very little effort and outlay. According to Flowerday et al. [37], real-time auditing is reliant on the technology that is now available, and CAATs will continue to be significant in order to accomplish continuous auditing. Only a few studies have looked at how CAATs may be employed in developing countries. For example, Siew et al. [85] looked at how Malaysian auditing firms employ the TOE framework. Siew et al.’s [85] key finding was that customers’ perceptions of professional accounting organizations' level of support and degree of complexity of the accounting ISs are two of the most important influences on adoption.
Organizational traits including the amount of IT experience among employees, senior management commitment, and the size of the organization were also shown to be predictors of embracing new technology. GAS is the most extensively used CAAT available to internal auditors at a number of firms in the UK and Malaysia [60]. To interpret the findings, researchers used the unified theory of human attitudes to study use of diverse technologies. This paper adds to the growing literature which considers CAATs in the context of economically developing public sector internal auditing departments (see for example [3, 32, 63]).
Theoretical framework and hypothesis development
User acceptability is critical to the successful adoption of any IT system [34]. According to Chauhan and Jaiswal [26] and Cimperman et al. [28], the technology acceptance model (TAM) is one of the most commonly used frameworks. Other researchers such as Šumak et al. [88] and Tsai et al. [96] argued that TAM has several disadvantages. Firstly, it does not give good insights into individuals' perspectives and ignores the relationship between usage attitude and intention of use. Secondly, it neglects its indicators and only investigates the external components of perceived usefulness [PU] and perceived usability [PEOU]. Venkatesh et al. [99] integrated key components from eight models and key theories into their model: IDT [75], TRA [34, 84], TPB [6],, TAM [34, 98], combined TAM-TPB [94], MM [97], SCT [18] and MPCU [95]. These served to predict or explain new technological developments, acceptance, and usage, and led to what became known as the UTAUT model.
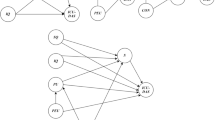
Venkatesh et al. [99] have presented a combined model—termed the UTAUT model—which is able to describe 70% of the variance in user intention, based on a systematic examination and comparison of the models above. Findings of the empirical investigation revealed that the UTAUT model is the most effective one for assessing the adoption of new technologies which is 40% of the variance in the usage of technology. Six major components make up the UTAUT model: performance expectation (PE), effort expectation (EE), social influence (SI), facilitating conditions (FCs), behavioral intention (BI) to utilize the system, and usage behavior (UB) as depicted in Fig. 1. Using the UTAUT paradigm, there are four key determinants and four moderators to consider. The model asserts that BI and consumption behavior are determined by four factors: PE, EE, SI, and FC [99]. Some moderators influence how people utilize technology, such as gender, age, experience, and willingness to learn new skills as presented in Fig. 1.
The unified theory of acceptance and use of technology (UTAUT) model [99]
The UTAUT model contributes to the investigation of technology acceptance and usage due to its capacity to incorporate various TAMs [79, 99]. For these reasons, this study employs UTAUT model to assess the influence of technological variables on CAATs uptake. A number of factors have been suggested to complement the UTAUT model. For instance, Kabra et al. [49] combined personal innovations precise to IT and trust in the UTAUT model in order to assess the impact on users’ behavioral intentions to accept IT. Khalilzadeh et al. [52] incorporated risk, self-efficacy, trust, attitude and security to assess the factors that guide users’ behavioral intentions to make payments via mobile phone. Carter et al. [24] have shown that trust is critical in influencing users' behavioral intentions to use technology-based services (such as online tax filing). Khalilzadeh et al. [52] revealed that trust is a crucial factor determining users’ behavioral intentions to adopt technology. Rawashdeh and Rawashdeh [74] posited that satisfaction is critical in explaining XBRL adoption. [70] stated that the organization greatly influences explanations for the acceptance of CAATs. Consequently, the UTAUT model will not only be adopted in this study, but expanded by incorporating the constructs of organizational influence, trust and satisfaction components so that internal auditors’ behavioral intentions for CAATs can be investigated. The modified model will then be empirically tested. The primary objective here is to explain how the model can predict factors affecting internal auditors’ behavioral intentions toward CAATs, as well as their perceived impact on individuals. The hypotheses are explained in more detail below, and the proposed conceptual model is illustrated in Fig. 1.
Effort expectancy and performance expectancy
To standardize concepts and ideas linked to incorporating technology into a single unified model, researchers devised what they term the UTAUT model. The UTAUT model now includes effort expectation, which is an important indicator of whether or not a technology will be accepted. EE is defined as "the system's degree of ease of use" [99]. Cimperman et al. [28] state that ease of use, complexity, and perceived ease of uses are all precursors of EE. The UTAUT model includes PE, which is defined as "the degree to which a person feels that the system aids in improving work performance" [99]. BI is described as "the extent to which a person has made conscious plans regarding whether to undertake a specific future activity" [99]. EE thus reflects internal auditors' opinions about ease of use of CAATs in the current study.
Internal auditors' views about whether CAATs would improve their performance are reflected in their PE scores. According to [99], PE is the most critical factor in determining whether or not a user would decide to implement a new technology. Moreover, people may believe that employing certain technologies is critical to achieving their goals, but they may also think that the system itself is cumbersome [34]. EE measures how easy someone thinks using technology will be and how certain they are that using it will not cause them to make any mistakes [34]. Subsequently, internal auditors' use of CAATs in this context has transformed the profession from a typically manual to an automated job [17]. Thus, for instance, the auditor must first make sure the information system from which the data are taken is secure before implementing the specified CAATs [82].
Employing CAATs necessitates internal auditors to become proficient in the utilization of these automated tools [2]. The roadblocks noted above may lead to an increase in effort required by internal auditors to implement CAATs. Because they feel the system is simple to use and requires little work on their part, the likelihood that those internal auditors would accept and utilize CAATs increased [60]. Prior studies have noted that internal auditors' expectation of work plays a significant role in determining their desire to conduct continuous auditing [70]. Because of these advantages, internal auditors are more inclined to accept CAATs if they feel that standard audit procedures will assist them in improving how they work. We anticipate that internal auditors' intention to use CAATs is positively correlated with performance expectation, following the reasoning given above.
Individuals who believe that implementing new technologies would help them do their work better have a high-performance expectation [99]. Internal auditors will undoubtedly get many advantages from CAATs. For example, automated technologies make it possible for them to review all transactions rather than a selection, making it more difficult for fraudsters to hide their crimes [86]. Internal auditing teams can use CAATs tools to swiftly analyze vast amounts of transaction data [17]. As a result, auditors will be better equipped to focus on high-risk areas, which will lead to enhanced audit efficiency and effectiveness [21]. The upshot of this is that CAATs are now considered an essential tool for internal auditors [60]. Model variables have little impact on the final results. One study [99] found that users’ behavioral intentions to embrace technology-based systems are strongly influenced by their performance and effort expectations. As a result, this study posits that expectations about them mainly determine intentions about acceptance of CAAT tools. As a consequence of the provided data, the following hypotheses are formulated:
Hypothesis 1
Effort expectancy has a significant influence on the behavioral intentions of using CAAT tools.
Hypothesis 2
Performance expectancy has a significant influence on the behavioral intentions of using CAAT tools.
Satisfaction
While trust is a personal conviction, user engagement with applications leads to happiness. As one of the most significant indicators of their ensuing behavior, the satisfaction factor evaluates the level of effort and performance expectations connected with the application or tools for analysis-type tasks [93]. CAAT tools must satisfy users by providing a positive value. A user's level of satisfaction can predict their behavioral intentions for CAAT tools in the future. Users' desire to adopt a specific tool may be influenced significantly by their satisfaction with technology-based systems [25, 36]. Satisfaction is measured by how pleased customers are with tagging, validation, and analysis services [36]. Satisfaction is defined in this study as being pleased with something or being pleased with a particular CAAT tool and satisfaction with a specific CAAT tool (continuous satisfaction). Chao [25] stated that the expectation of effort greatly affected the level of satisfaction. Asiati et al. [16] found that trust influenced pleasure and it predicted that user satisfaction ratings might substantially shape users' behavioral intention to utilize CAAT tools. Based on this argument the following hypotheses are formulated:
Hypothesis 3
Effort expectancy has a significant influence on users’ satisfaction with CAAT tools.
Hypothesis 4
Performance expectancy has a significant influence on users’ satisfaction with CAAT tools.
Hypothesis 5
Satisfaction has a significant influence on the behavioral intentions to use CAAT tools.
Trust
One of the obstacles to utilizing new applications is the feeling of insecurity, especially if one is working with sensitive data like financial accounts, where a single error may have serious ramifications for a company's financial position or result in a poor investment choice. For this reason, trust plays a vital role in determining how consumers use technology-based services (e.g., CAAT tools). Trust is a significant component of users' behavioral intentions, and this study assumes that trust plays an important role. A user's perception that CAAT tools providers operate ethically may be described as trust in this study setting [25]. The degree to which consumers trust a technology-based system can affect how happy they are with it on a personal level [16]. As a result, user confidence in the CAAT tools is governed by their faith in the technology tools regarding the correctness, speed, and time saved [2, 17, 70]. Furthermore, trust is a crucial part of the Social Exchange Theory model [76]. As long as the user believes that a CAAT tool is trustworthy, they are more inclined to continue doing business with the companies who supply it. Since the perceived quality of a tool influences user confidence in CAAT tools, trust is essential. One study argued that trust in applications influenced conviction [24]. Based on this viewpoint, two hypotheses are posited below:
Hypothesis 6
Trust has a significant influence on the behavioral intentions of users of CAAT tools.
Hypothesis 7
Trust has a significant influence on the satisfaction of using CAAT tools.
Social influence
Social influence (SI) refers to a person's perspective of how significant others (e.g., superiors) believe they should use a system [99]. Research has shown that user acceptance and use of technology are strongly influenced by social pressure [8, 31, 67]. People who can influence internal auditors' decisions on whether or not CAATS should be accepted and used in an audit setting are known as social influencers [60]. Prior studies revealed evidence that social influence significantly shapes internal auditors' behavioral intentions to use CAATs [31]. For this reason, we expect internal auditors to use CAATs more often if they believe that their immediate superiors expect the practice [21]. Nevertheless, SI has a direct influence on behavioral intention to use the technology [30, 75, 88]. With this in mind the following hypothesis is put forward:
Hypothesis 8
Social influence has a significant influence on behavioral intention to use CAATs tools.
Organizational influence
Organizations have a substantial and favorable impact on the usage of CAATs since it shows senior managerial and widespread support for them [55]. On the other hand, higher degrees of influence may engender the idea that particular services are required, weakening the link between purpose and implementation. The usage of CAATs was shown to benefit from substantial support for them [55]. According to Rosli et al. [78], senior/executive management will guide what CAATs firms choose to implement. The use of CAATs has been hypothesized as having an impact on individuals. However, as the organization’s influence grows, the link between usage and desired personal outcomes will weaken the obligation to use technology. Auditors are likely to utilize CAATs if firms' partners support and promote their usage [30]. As a result the following hypotheses are posited:
Hypothesis 9
Organizational influence has a significant influence on the use of CAATs tools.
Hypothesis 10
Organizational influence has a significant influence on behavioral intention to use CAATs tools.
Facilitating conditions
Facilitating conditions (FCs) refer to a person's belief in the availability of sufficient resources and technological infrastructure to enable system use [99]. CAATs require internal auditors to be proficient in establishing input files and creating complicated commands to carry out the tests [17]. Internal auditors who use CAATs will find it easier to spend more money on IT audit training [82]. To make CAATs adoption easier, Mahzan and Lymer [60] contend that organizational conditions and support from senior management are critical, as are software vendors' assistance. Without these enabling criteria, internal auditors will be reluctant to accept and use CAATs. Internal auditors' intent to use CAATs was shown to be strongly guided by enabling conditions [60, 62]. However, based on the study conducted by Venkatesh et al. [99], FC directly influences the behavioral use of technology [6, 61, 78]. Based on this the following hypothesis is put forward:
Hypothesis 11
Facilitating conditions have a significant influence on the use of CAATs tools.
Behavioral intention
The phrase "individual's intention to do a behaviour" describes behavioral intention (BI) [6]. According to Ajzen [6], BI is the most accurate predictor of future behavior and is a precursor to actual usage in the real world. As stated by UTAUT, the desire to use and adopt CAATs is a function of several factors, including performance expectations, effort expectations, social influence, and enabling circumstances [99]. The relationship between behavioral intention and usage of a system is frequently discussed in the literature [33, 99]. It has been shown by Davis et al. [35, p. 478], that "attitude toward utilizing has a significant beneficial influence on actual system use," and confirmed by Venkatesh et al. [99]. Several writers have examined the relationship between CAATs and the surrounding environment [8, 31, 48, 103]. Based on the study conducted by Venkatesh et al. [99], BI influences the utilization behavior of the technology. Prior studies pointed out that BI is significant when it comes to utilizing a given technology [7, 67, 87]. Based on this argument the following hypothesis is formulated:
Hypothesis 12
Behavioral intention to use CAATs has a positive impact on their acceptance.
Figure 2 displays the conceptual model, while the relationships between the constructs (arrows) represent the research hypotheses.
Research methodology
Research instrument
The research instrument was designed to be separated into two stages for this investigation. Nominal demographic data were presented in the first. Age, gender, education and experience were among the details gleaned from the survey's questions; it is examined in Sect. "Research instrument" and summarized in Table 1. With its 41 elements, the second stage served to determine the model's nine variables (Fig. 2). These nine variables are endogenous (EE, SI, PE, OI, FC, TRU, SAT, BI and Use of CAATs tools). Several items serve to evaluate each aspect. A 5-point Likert scale ranked the questionnaire responses to gauge the answers. The Likert scale had five response possibilities, with "1 = strongly disagree" as the least option and "5 = strongly agree" as the highest. This technique was devised to gather data from respondents utilizing the UTAUT model. Likewise, the critical metrics for this investigation were chosen. While the UTAUT model provided some inspiration, additional variables such as the adoption of new technologies and ISs were introduced, as shown in Table 1.
Sample and data collection
This study’s participants comprise internal auditors working in the Saudi public sector. Respondents were selected through the use of convenience sampling [47]. The researchers had to find out if the questionnaire is suitable and participants understood it, so a pilot study was conducted. The participants for the pilot study were chosen based on their education/qualification, expertise, and current position. They were internal auditors, IT experts and academics in the field of accounting, auditing, and information systems. The researchers received twenty responses. Amendments were made based on the feedback provided by the respondents. Before distributing the survey the researchers obtained ethical approval, all participants were notified that their identities would not be revealed, and their answers will solely be used for research purposes. Also, they were notified their contribution is voluntary, and they can withdraw from the study at any time.
The survey was distributed in the Arabic language given that all those taking part are Arabic speakers. The majority participants finished the survey in 10–15 min. In order to acquire the empirical Fig. 2. 530 Research model. data needed to validate the developed conceptual model and to examine the formulated hypotheses, Researchers can disagree over the suitable sample size; preferably, it ought to be determined by the variance, margin of error, level of confidence, and the size population [20, 62]. Roscoe [77] proposed that the sample size should be calculated according to the total number of items. Muthén & Muthén [68] contend that the sample size should be more than 150 people. So, after the questionnaire surveys were distributed, out of 540 responses we acquired—for the purposes of data analysis—239 valid samples and this amounts to 44.2% of the response rate.
Data analysis
To conduct a thorough data investigation, firstly the researchers implemented exploratory factor analysis (EFA). It was utilized in the initial phases of model development or theory. Secondly, the Measurement Model Evaluation measured overall model fitness employing a variety of statistical methods, namely Chi-square test, model fitness evaluation including, comparative fit index (CFI), root mean square error of approximation (RMSEA) test and goodness-of-fit index (GFI), adjusted goodness-of-fit index (AGFI), and Tucker–Lewis index (TLI). Furthermore, Confirmatory factor analysis (CFA) served to validate the measurement model [23, 56]. Hypotheses testing was completed using the structural equation model (SEM) to test the relationships between the constructs, utilizing SPSS 24 and AMOS 24.
Demographic characteristics of respondents
The demographic characteristics of this study’s respondents are summarized in Table 2. In terms of gender, there were 82% male and 18% female, with the majority of participants were in the 30 to 39 age cohort. Internal auditors responded characteristically in terms of having simple access to the questions. Approximately 62.8% have a Bachelor degree. Regarding length of employment, approximately 69.9% of internal auditors have worked for between 5 to 9 years.
Exploratory factor analysis (EFA)
An EFA was undertaken by means of principal component analysis and varimax rotation. The lowest factor loading benchmark was fixed to 0.50. The commonality of the scale, which specifies the volume of variance in each measurement, was also calculated to confirm adequate levels of clarification. Results demonstrate that all communalities were greater than 0.50 while the lowest communality after initial analysis was 239. It was important to assess the whole significance of the correlation matrix via Bartlett’s test of sphericity, which can measure the statistical situation wherein the correlation matrix has significant correlations amongst some constituents. The results were significant, x2(n = 239) = 4790.740, df = 780 with P value (p < 0.001), confirming its appropriateness for factor analysis.
The Kaiser–Meyer–Olkin measure of sampling adequacy (MSA) specifies the correctness of the data for factor analysis, which was 0.761. In this regard, data with MSA estimates above 0.700 are considered appropriate for factor analysis. The eigenvalues of the components ranged from 1.00 to 5.188. The threshold eigenvalues for each component/factor must be equal to or greater than 1.00. Finally, the researchers found 15% non-redundant residuals with absolute values greater than 0.05. However, in this initial EFA, four items possessed loadings smaller than 0.50, i.e., “TRU5, SI1, FC1 and BI2 and failed to give significant weight to any element. As well, the items “USE1, USE7, USE8, and USE9” were overloaded onto a factor other than its original factor. Consequently, eight items were eliminated for the purposes of further analysis.
The researchers repeated the EFA after eliminating the above-mentioned items; the Kaiser–Meyer–Olkin MSA was 0.785. The Bartlett’s test of sphericity was verified as significant, i.e., x2 = 3875.919, df = 496, with P value (p < 0.001) and all communalities were over the threshold value of 0.500. After further analyses the researchers discovered there are 12% on non-redundant residuals with the absolute value greater than 0.05. Factor 1 included items TRU1 to TRU4, factor 2 gathers items SI2 and SI3, factor 3 consists of items EE1 to EE4, factor 4 is composed of items PE2 to PE4, and factor 5 includes items from FI1 to FI4. Factor 6 gathered items FC2 to FC4, factor 7 consists of items SAT1 to SAT4, factor 8 comprises items BI1 and BI3. Lastly, factor 9 incorporated items from USE2 to USE6. Factor loadings of the exploratory factor analysis are presented in Table 3.
Measurement model/ the CFA
Survey data SEM involves two main stages: (1) confirmatory factor analysis and (2) structural model/path analysis. Researchers first measured overall model fitness using a variety of statistical methods, namely Chi-square, RMSEA, CFI, GFI, AGFI and TLI [23, 27, 38]. For the CFA, tests were used to validate the measurement model: firstly, goodness-of-fit indices, secondly, discriminant validity; and thirdly, convergent validity [23]. This study’s measurement model achieved satisfactory levels of GFI indices as shown in Table 4.
Cronbach's alpha and composite reliability (CR) were checked for reliability testing. The CR and Cronbach's alpha values have to be at least 0.70 or greater. CR gives internal consistency to the construct and can serve as a substitute for Cronbach's alpha [41]. The above noted requirements for reliability analysis were attained. Cronbach's alpha ranged from 0.700 to 0.884, with Cronbach's CRs ranging from 0.701 to 0.885 (see Table 3). The model's discriminant validity and construct validity were also tested. Every factor loading must be equal to or more than 0.60 [44]. Each construct's CR value must be at least 0.70 or higher [27]. Extracted average variance (AVE) value must be at least 0.50 [38]. All constructs and items met the necessary criteria for convergent validity. All item CR values range from 0.701 to 0.885, AVE values range from 0.510 to 0.641, and factor loading values range from 0.60 to 0.90, indicating high convergent validity [44]. Table 5 summarizes the convergent validity and reliability outcomes.
In the test for discriminant validity, the square root of the average variance extracted (AVE) must be higher than the corresponding correlations between that construct and the residual of other constructs, in order to get appropriate discriminant validity [27]. The authors of this paper tested the square root of AVE from each construct and its correlation coefficient with other constructs, the objective being to obtain adequate discriminant validity results (see Table 6).
Results
Referring to the path analysis, this involves testing a structural model for assessing the influence of all independent variables on dependent variables [23, 27, 69]. The goodness-of-fit helped to accomplish the value of the cut-off threshold of χ2/df, RMSEA, CFI, AGFI, GFI, and TLI. They are displayed in Table 7.
According to the structural model analysis results, 9 hypotheses were supported but the other three were not. TRU has a significant effect on SAT (β = 0.27, p < 0.01), so H1 is supported. TRU has a significant influence on BI (β = 0.29, p < 0.01), and therefore H2 is sustained. H3, which corresponds to SI significantly influenced BI (β = 0.21, p < 0.05), so the third hypothesis is accepted. H4 which denotes EE exerts only an insignificant influence on BI (β = 0.12, p≰0.100), and this why this particular hypothesis does not hold up. According to H5, EE has a significant effect on SAT (β = 0.0.23, p < 0.05); hypothesis 5 is significant and supported. For H6 which argues that PE has an insignificant effect on SAT (β = −0.04, p ≰ 0.100), it is not supported. H7 which contends that PE has a significant effect on BI (β = 0.24, p < 0.05) is declared to be significant and subsequently supported.
Elsewhere, OI is related to hypothesis 8 which wields a significant effect on BI (β = 0.19, p < 0.050), so H8 is supported. H9, which asserts that OI has an insignificant effect on USE (β = −0.03, p ≰ 0.100). For H10, it represents a significant and supportive relationship between FC and USE (0.28, p < 0.001). Furthermore, the relationship between SAT and BI corresponds to a significant relationship as argued by H11; (β = 0.26, p < 0.01), so H11 is supported. Finally, hypothesis H12 is concerned with a significant and supportive relationship between BI and USE, i.e., (β = 0.34, p < 0.001); it is supported. For further details see Fig. 3 and Table 8. Apart from this the independent factors (TRU, SI, EE, PE, and FC) revealed 69% of variance. Furthermore, TRU, SI, EE, PE, OI, and SAT highlighted a combined effect on BI, i.e., 58%. The factors BI, OI and FC expressed 51% of combined variance effect or R2.
Discussion
The aim of this study was to investigate the various factors that influence users' intentions to utilize CAATs. Prior research has not thoroughly examined the factors influencing the adoption of analytical instruments which the current study has done. Consequently, this research model incorporates specific elements, such as trust and satisfaction, to enhance the predictive capability of the original model. The analysis revealed the significant factors influencing users' behavioral intentions to use CAATs. The findings reported here documented the influence of TRU on SAT. The coefficient for TRU (β = 0.27, t = 3.058, p = 0.002) was significant at the 0.05 level of significance. This level indicates that the coefficient is markedly different from zero, hence SAT is predicted at a high degree of certainty. This study also hypothesized that EE (H5) wields a significant influence on SAT. EE (β = 0.23, t = 2.490, p = 0.013) was a significant predictor of SAT and this finding is in line with those of recent studies [25, 74]. The satisfaction value throughout the effort expectancy has a foremost influence on the developers of CAATs. Thus, the establishment and evaluation of CAATs for the tagging and analysis and audit of financial statements, organization information and its operations, will depend more on what is expected of CAATs. Because they utilize CAATs, auditors submit their work and this in turn has an influence on the work they do in the future. It should be noted that this might lead to inaccuracies if CAATs is difficult to use, so it could constitute a waste of time. However, PE (β = −0.04, t = −0.511, p = 0.603) was not a significant predictor of SAT.
Nonetheless, TRU and SAT had a direct influence on the BI to utilize CAATs. It emerged that the influence of TRU on BI was significant, with the coefficient (β = 0.29, t = 2.855, p = 0.004) and the influence of SAT on BI was also significant, with the coefficient (β = 0.26, t = 2,949, p = 0,003). TRU and SAT were significant with a medium effect on BI. Having high levels of satisfaction with CAATs increases auditors’ BI to employ such technologies. Previous research has demonstrated the important role played by trust and satisfaction in technology adoption decisions [24, 25, 71,72,74]. As Carter et al. [24] suggested in the context of the exchange of sensitive exchange, CAATs help with auditing sensitive financial data. If there is not enough trust in CAATs then it will not be deployed, and this makes sense to the rational user. Frequently, trust (e.g., error-free, accurate, up-to-date, certified) is valued by internal auditors and encourages them to use CAATs in order to make more reliable and credible comparisons between financial statements. Moreover, the findings reported here support the observations of Ratten [73], who demonstrates that TRU is a significant predictor of BI to use CAATs. Thus, the higher internal auditors’ trust in and satisfaction with CAATs, the higher are their BIs.
On the other hand, behavioral intention (BI) to do so significantly predicts the acceptance rate of a technology. The effect of BI on the use of CAATs is large (β = 0.34, t = 3.689, p = 0.001). A person’s intention to use a system consistently, given that the system is available, reflects genuine interest in utilization [43, 72]. Consequently, the present study suggests that BI measures the internal auditors’ intentions to use CAATs. This study found that an increase in the BI to use CAATs increases the likelihood of using the system. These results align with previous studies, which have reported positive effects of BI regarding usage of IT [8, 59, 103].
The SI and EE have a significant effect on BI. However, the effect of SI (β = 0.21, t = 1.960, p = 0.049) was small and significant at the 0.05 level of significance while the effect of EE (β = 0.12, t = 1.055, p = 0.291) was not. These results suggest that SI is a significant predictor of BI and this outcome agrees with other research [10, 67, 98],it should be noted that EE does not have a significant influence on the intention. These results, nonetheless, conflict with other studies; for instance [1, 65, 67, 87]. for instance Mohammad et al. [65] who reported that SI does not have much to do with BI on auditors’ use of CAATs. Their research reported that encouragement from peers and even senior management did not increase the intention of auditors to use CAATs. However, Chao [25], Al-Saedi et al. [10], and Mohammad et al. [65] found that EE significantly guides BI. Although the effect reported by the researchers was significant, it was small since the significance level implied that EE was not a vital factor in predicting auditors’ decisions in using CAATs. The findings of this study, however, align with Mohammad et al. [65], and Al-Hiyari et al. [8], who reported that SI did significantly predict CAATs use. Similarly, the study by Curtis and Payne [31] supports the findings of this present study.
The hypothesis is that PE has a significant influence on BI. Sair and Danish [80] define PE as the degree to which an individual believes their job performance will improve through enhanced technology innovation. This study established that PE significantly influenced BI. The effect was, nevertheless, small with a significance value of 0.027. Although the results show that the influence is notable, the significance value suggests that PE is not a vital factor in predicting BI. In their work, Mohammad et al. [65] reported that PE is a significant predictor for using the technology.
The eighth and ninth hypotheses theorized that OI wielded a significant influence on BI and use of CAATs. The findings argue that this influence had a small but significant effect on BI. Conversely, it was not a significant factor on CAATs. It represents support for senior management or technical staff advising other personnel to implement computer technologies [50]. The factor of FCs had a significant influence on the use of CAATs (β = 0.28, t = 3.719, p = 0.001). These findings agree with what Mohamed et al. [64] reported, they observed that when resources are made available, auditors increase their intention to use CAATs. According to Al-Hiyari et al. [8] having assistance, adequate information, and enough resources encourages auditors’ intention to employ CAATs.
Overall, the findings demonstrate that the most important factors guiding the use of CAATs are FCs and BI. Internal auditors are more likely to use CAATs when they have access to the right information, resources, and support from other personnel. Satisfaction with auditing techniques had a medium effect on BI. The more auditors are satisfied with CAATs, the higher the BI will be to accept and employ the technology. Conversely, TRU, SI, PE and OI had only a small effect on BI. The study also established that OI is not a significant predictors of CAATs. As well, EE was not a significant influencer of BI.
Conclusion
The significance of CAATs in the audit process is well known. Despite the benefits they offer as stated by academics and regulators, many internal auditors do not still use these technologies when conducting some internal audit tasks. The purpose of this study is to develop and empirically test a model to predict the factors affecting internal auditors’ behavioral intentions toward CAATs. The research model displayed in this article comprises twelve hypotheses of which 9 were supported but 3 were not. Two of the supported hypotheses had a large effect (FCs on use of CAATs and BI on use of these tools); three had a medium effect (TRU on SAT, TRU on BI, and SAT on BI); and four had little effect (SI on BI, EE on SAT, PE on BI, and OI on BI). An interpretation of the findings based on a survey of 239 participants.
Implications
This study has two major implications, the first in terms of theoretical contributions. A number of studies have been published on the topic of CAATs and devised their own models. The model proposed here contained constructs present in numerous prior studies but these works did not completely validate them. Thus, these constructs serve as new contributions to the research on this topic. The results enrich the existing research by expanding and incorporating the constructs of OI, and TRU and SAT components to investigate internal auditors’ behavioral intentions for CAATs. Furthermore, the proposed model explains generally the amount of variance whereby the independent factors (TRU, SI, EE, PE, and FC) showed 69% of variance. Furthermore, TRU, SI, EE, PE,FI, and SAT exerted a combined influence on BI, i.e., 58%. In addition, the factors of BI, OI and FC expressed 51% of combined variance effect or R2 in the BI to utilize CAATs. However, taken together, the empirical results signal that the proposed conceptual model does influence BI, and especially in the area of CAATs. Secondly, concerning the practical implications, the current study is the first to report on factors guiding internal auditors’ behavioral intentions regarding CAATs in Saudi Arabia. In practical terms this study will help public sector officials and other decision-makers to comprehend the role of these factors in framing CAATs in Saudi government departments.
Limitations and future research
It is very important to draw attention to the limitations since they may open up promising new directions for future research. Firstly, the data for this study were collected in the form of answers to a survey that was solely quantitative in design. With this in mind, future research should gather other forms (i.e., qualitative) of evidence concerning participants’ perspectives, opinions, beliefs, etc., about those factors that greatly shape their usage of CAATs. Secondly, in spite of the fact that the extended UTAUT model is validated as far as the use of CAATs in Saudi Arabia is concerned, the findings cannot be generalized. Therefore, future research should expand on this topic to confirm the generalization of the model to other countries.
Availability of data and materials
The datasets used and/or analyzed during the current study are available from the corresponding author on reasonable request.
Abbreviations
- CAATs:
-
Computer-assisted audit techniques
- GAS:
-
General audit software
- UTAUT model:
-
The unified theory of acceptance and use of technology model
- SEM:
-
Structural equation modeling
- ISs:
-
Information systems
- IT:
-
Information technology
- TAM:
-
Technology acceptance model
- SI:
-
Social influences
- FC:
-
Facilitating conditions
- GAS:
-
General audit software
- IDT:
-
Innovation diffusion theory
- TOE:
-
Technology–organisation–environment
References
Abbaszadeh MR, Salehi M, Faiz SM (2019) Association of information technology and internal controls of Iranian state agencies. Int J Law Manag 61:133–150
Ahmi A, Kent S (2013) The utilisation of generalized audit software (GAS) by external auditors. Manag Audit J 28:88–113
Ahmi A, Saidin SZ, Abdullah A, Ahmad AC, Ismail NA (2016) State of information technology adoption by internal audit department in Malaysian public sector. Int J Econ Financ Issues 6(7):103–108
AICPA (1979) Audit and accounting guide: computer assisted audit techniques. American Institute of Certified Public Accountants. https://egrove.olemiss.edu/cgi/viewcontent.cgi?article=1588&context=aicpa_indev
AICPA (1984) Statement on auditing standards no. 48—the effects of computer processing on the examination of financial statements. AICPA, Durham
Ajzen I (1991) The theory of planned behavior. Organ Behav Hum Decis Process 50(2):179–211
Al-Adwan AS, Al-Madadha A, Zvirzdinaite Z (2018) Modeling students’ readiness to adopt mobile learning in higher education: an empirical study. Int Rev Res Open Distrib Learn 19(1):1
Al-Hiyari A, Al Said N, Hattab E (2019) Factors that influence the use of computer assisted audit techniques (CAATs) by internal auditors in Jordan. Acad Account Financ Stud J 23(3):1–15
Al-Okaily M, Alqudah HM, Al-Qudah AA, Alkhwaldi AF (2022) Examining the critical factors of computer-assisted audit tools and techniques adoption in the post-COVID-19 period: internal auditors perspective. VINE J Inf Knowl Manag Syst (ahead-of-print)
Al-Saedi K, Al-Emran M, Ramayah T, Abusham E (2020) Developing a general extended UTAUT model for M-payment adoption. Technol Soc 62:101293
Albashrawi M, Motiwalla L (2019) Privacy and personalization in continued usage intention of mobile banking: an integrative perspective. Inf Syst Front 21(5):1031–1043
Alexander N (2001) What’s law got to do with it? Mapping modern mediation movements in civil and common law jurisdictions. Bond Law Review 13(2):335–363
Almaiah MA, Al-Khasawneh A, Althunibat A (2020) Exploring the critical challenges and factors influencing the E-learning system usage during COVID-19 pandemic. Educ Inf Technol 25:5261–5280
Alsyouf A, Ishak AK (2018) Understanding EHRs continuance intention to use from the perspectives of UTAUT: practice environment moderating effect and top management support as predictor variables. Int J Electron Healthc 10(1–2):24–59
Alturki UT, Aldraiweesh A (2016) Evaluating the usability and accessibility of LMS “Blackboard” at King Saud University. Contemp Issues Educ Res (CIER) 9(1):33–44
Asiati DI, Umar H, Sitinjak T (2019) The effects of service quality, image and trust on satisfaction and its impact on syari¡ ah bank customer loyalty in palembang. Bus Econ Res 9(1):295–316
Awuah B, Onumah JM, Duho KCT (2022) Determinants of adoption of computer-assisted audit tools and techniques among internal audit units in Ghana. Electron J Inf Syst Dev Countries 88(2):e12203
Bandura A (1986) Prentice-Hall series in social learning theory. Social foundations of thought and action: a social cognitive theory. Englewood Cliffs, NJ.
Belfo F, Trigo A (2013) Accounting information systems: tradition and future directions. Procedia Technol 9:536–546
Bhattacherjee A, Lin C-P (2015) A unified model of IT continuance: three complementary perspectives and crossover effects. Eur J Inf Syst 24(4):364–373
Bierstaker J, Janvrin D, Lowe DJ (2014) What factors influence auditors’ use of computer-assisted audit techniques? Adv Account 30(1):67–74
Braun RL, Davis HE (2003) Computer‐assisted audit tools and techniques: analysis and perspectives. Manag Audit J
Byrne BM (2013) Structural equation modeling with LISREL, PRELIS, and SIMPLIS: basic concepts, applications, and programming. Psychology Press
Carter L, Shaupp LC, Hobbs J, Campbell R (2011) The role of security and trust in the adoption of online tax filing. Transforming Government: People, Process and Policy
Chao C-M (2019) Factors determining the behavioral intention to use mobile learning: an application and extension of the UTAUT model. Front Psychol 10:1652
Chauhan S, Jaiswal M (2016) Determinants of acceptance of ERP software training in business schools: empirical investigation using UTAUT model. Int J Manag Educ 14(3):248–262
Chin WW (1998) The partial least squares approach to structural equation modeling. Modern Methods Bus Res 295(2):295–336
Cimperman M, Brenčič MM, Trkman P (2016) Analyzing older users’ home telehealth services acceptance behavior—applying an Extended UTAUT model. Int J Med Inform 90:22–31
Cummings WH, Venkatesan M (1976) Cognitive dissonance and consumer behavior: a review of the evidence. J Mark Res 13(3):303–308
Curtis MB, Payne EA (2008) An examination of contextual factors and individual characteristics affecting technology implementation decisions in auditing. Int J Account Inf Syst 9(2):104–121
Curtis MB, Payne EA (2014) Modeling voluntary CAAT utilization decisions in auditing. Manag Audit J
Daoud L, Marei A, Al-Jabaly S, Aldaas A (2021) Moderating the role of top management commitment in usage of computer-assisted auditing techniques. Accounting 7(2):457–468
Davis FD (1989) Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q 1:319–340
Davis FD, Bagozzi RP, Warshaw PR (1989) User acceptance of computer technology: a comparison of two theoretical models. Manage Sci 35(8):982–1003
Davis FD, Bagozzi RP, Warshaw PR (1992) Extrinsic and intrinsic motivation to use computers in the workplace 1. J Appl Soc Psychol 22(14):1111–1132
DeLone WH, McLean ER (2016) Information systems success measurement. Found Trends® Inf Syst 2(1):1–116
Flowerday S, Blundell AW, Von Solms R (2006) Continuous auditing technologies and models: a discussion. Comput Secur 25(5):325–331
Fornell C, Larcker DF (1981) Evaluating structural equation models with unobservable variables and measurement error. J Mark Res 18(1):39–50
Gefen D (2000) E-commerce: the role of familiarity and trust. Omega 28(6):725–737
Gonzalez GC, Sharma PN, Galletta DF (2012) The antecedents of the use of continuous auditing in the internal auditing context. Int J Account Inf Syst 13(3):248–262
Hair JF, Black WC, Babin BJ, Anderson RE, Tatham RL (2010) Multivariate Data Analysis (7th ed.). New Jersey: Pearson Education Inc
Hammouchi H, Cherqi O, Mezzour G, Ghogho M, El Koutbi M (2019) Digging deeper into data breaches: an exploratory data analysis of hacking breaches over time. Procedia Computer Science 151:1004–1009
Handoko BL, Chu NC (2021) UTAUT model in predicting auditor intention in adopting CAATs. In: The 2021 12th international conference on E-business, management and economics, pp 144–153
Henseler J, Ringle CM, Sarstedt M (2015) A new criterion for assessing discriminant validity in variance-based structural equation modeling. J Acad Mark Sci 43(1):115–135
Hoque R, Sorwar G (2017) Understanding factors influencing the adoption of mHealth by the elderly: an extension of the UTAUT model. Int J Med Informatics 101:75–84
Howard JA, Sheth JN (1969) The theory of buyer behavior. N Y 63:145
Iacovou CL, Benbasat I, Dexter AS (1995) Electronic data interchange and small organizations: Adoption and impact of technology. MIS Q 1:465–485
Janvrin D, Bierstaker J, Lowe DJ (2009) An investigation of factors influencing the use of computer-related audit procedures. J Inf Syst 23(1):97–118
Kabra G, Ramesh A, Akhtar P, Dash MK (2017) Understanding behavioural intention to use information technology: insights from humanitarian practitioners. Telematics Inform 34(7):1250–1261
Kahyaoglu SB, Aksoy T (2021) Artificial intelligence in internal audit and risk assessment. In: Financial ecosystem and strategy in the digital era. Springer, pp 179–192
Karahanna E, Straub DW, Chervany NL (1999) Information technology adoption across time: a cross-sectional comparison of pre-adoption and post-adoption beliefs. MIS Q 1:183–213
Khalilzadeh J, Ozturk AB, Bilgihan A (2017) Security-related factors in extended UTAUT model for NFC based mobile payment in the restaurant industry. Comput Hum Behav 70:460–474
Kim H-J, Kotb A, Eldaly MK (2016) The use of generalized audit software by Egyptian external auditors: the effect of audit software features. J Appl Acc Res 17(4):456–478
Kim H-J, Mannino M (2012) Effect of software feature training on beliefs, use, and performance: using the benford’s law feature of generalized audit software
Kim H-J, Mannino M, Nieschwietz RJ (2009) Information technology acceptance in the internal audit profession: impact of technology features and complexity. Int J Account Inf Syst 10(4):214–228
Kline RB (2011) Principles and practice of structural equation modeling (3. Baskı). Guilford, New York, NY
La Porta R, Lopez-de-Silanes F, Shleifer A (2008) The economic consequences of legal origins. J Econ Lit 46(2):285–332
Li H, Dai J, Gershberg T, Vasarhelyi MA (2018) Understanding usage and value of audit analytics for internal auditors: an organizational approach. Int J Account Inf Syst 28:59–76
Lněnička M, Nikiforova A, Saxena S, Singh P (2022) Investigation into the adoption of open government data among students: the behavioural intention-based comparative analysis of three countries. Aslib J Inf Manag 74(3):549–567
Mahzan N, Lymer A (2014) Examining the adoption of computer-assisted audit tools and techniques: Cases of generalized audit software use by internal auditors. Manag Audit J
Manrai R, Gupta KP (2020) Integrating utaut with trust and perceived benefits to explain user adoption of mobile payments. In: Strategic system assurance and business analytics. Springer, pp 109–121
Mansour EM (2016) Factors affecting the adoption of computer assisted audit techniques in audit process: findings from Jordan. Bus Econ Res 6(1):248–271
Meyyappan G, Lee HS (2011) The impact of information technology on internal auditing. Afr J Bus Manag 5(9):3523–3539
Mohamed IS, Muhayyidin NHM, Rozzani N (2019) Auditing and data analytics via computer assisted audit techniques (CAATS) determinants of adoption intention among auditors in Malaysia. In: Proceedings of the 3rd international conference on big data and internet of things, pp 35–40
Mohammad A-K, Kamil SB, Noor IBM (2017) Factors affecting adoption of computer assisted audit techniques and tools (caats) among external auditors in Jordan. Int J Eng Sci Manag Res 4(2):28–32
Mujalli A, Almgrashi A (2020) A Conceptual Framework for Generalised Audit Software Adoption in Saudi Arabia by Government Internal Auditing Departments using an Integrated Institutional Theory-TOE Model. IEEE Asia-Pacific Conference on Computer Science and Data Engineering (CSDE) 2020:1–8
Mujalli A, Khan T, Almgrashi A (2022) University accounting students and faculty members using the blackboard platform during COVID-19; Proposed modification of the UTAUT model and an empirical study. Sustainability 14(4):2360
Muthén LK, Muthén BO (2002) How to use a Monte Carlo study to decide on sample size and determine power. Struct Equ Model 9(4):599–620
Oliver RL (1981) Measurement and evaluation of satisfaction processes in retail settings. J Retail 57:25
Pedrosa I, Costa CJ, Aparicio M (2020) Determinants adoption of computer-assisted auditing tools (CAATs). Cogn Technol Work 22(3):565–583
Pizzi S, Venturelli A, Variale M, Macario GP (2021) Assessing the impacts of digital transformation on internal auditing: a bibliometric analysis. Technol Soc 67:101738
Ramen M, Jugurnath B, Ramhit P (2015) UTR-CTOE: a new paradigm explaining CAATs adoption. J Mod Account Audit 11(12):615–631
Ratten V (2014) Behavioral intentions to adopt technological innovations: the role of trust, innovation and performance. Int J Enterprise Inf Syst (IJEIS) 10(3):1–12
Rawashdeh B, Rawashdeh A (2021) Factors influencing the usage of XBRL tools. Manag Sci Lett 11(4):1345–1356
Rogers EM (2003) Diffusion of innovations. Simon & Shuster. Inc.,
Roloff ME (1981) Interpersonal communication. Sage Publications Beverly Hills
Roscoe JT (1975) Fundamental research statistics for the behavioral sciences
Rosli K, Yeow PHP, Siew E-G (2012) Computer-assisted auditing tools acceptance using I-Toe: a new paradigm. Computer 7:15–2012
Rouidi M, Hamdoune A, Choujtani K, Chati A (2022) TAM-UTAUT and the acceptance of remote healthcare technologies by healthcare professionals: a systematic review. Inf Med Unlocked 32:101008
Sair SA, Danish RQ (2018) Effect of performance expectancy and effort expectancy on the mobile commerce adoption intention through personal innovativeness among Pakistani consumers. Pak J Commerce Soc Sci (PJCSS) 12(2):501–520
Sánchez-Prieto JC, Olmos-Migueláñez S, García-Peñalvo FJ (2016) Informal tools in formal contexts: development of a model to assess the acceptance of mobile technologies among teachers. Comput Hum Behav 55:519–528
Sayana SA, Cisa C (2003) Using CAATs to support IS audit. Inf Syst Control J 1:21–23
Seethamraju R, Diatha KS, Garg S (2018) Intention to use a mobile-based information technology solution for tuberculosis treatment monitoring–applying a UTAUT model. Inf Syst Front 20(1):163–181
Sheppard BH, Hartwick J, Warshaw PR (1988) The theory of reasoned action: a meta-analysis of past research with recommendations for modifications and future research. J Consum Res 15(3):325–343
Siew E-G, Rosli K, Yeow PHP (2020) Organizational and environmental influences in the adoption of computer-assisted audit tools and techniques (CAATTs) by audit firms in Malaysia. Int J Account Inf Syst 36:100445
Singleton TW (2011) IT audit basics: how the it auditor can make substantive contributions to a financial audit. ISACA Journal 1:7
Sultana J (2020) Determining the factors that affect the uses of Mobile Cloud Learning (MCL) platform Blackboard-a modification of the UTAUT model. Educ Inf Technol 25(1):223–238
Šumak B, Pušnik M, Heričko M, Šorgo A (2017) Differences between prospective, existing, and former users of interactive whiteboards on external factors affecting their adoption, usage and abandonment. Comput Hum Behav 72:733–756
Šumak B, Šorgo A (2016) The acceptance and use of interactive whiteboards among teachers: Differences in UTAUT determinants between pre-and post-adopters. Comput Hum Behav 64:602–620
Taiwo AA, Downe AG (2013) The theory of user acceptance and use of technology (UTAUT): A meta-analytic review of empirical findings. J Theoret Appl Inf Technol 49(1):1
Tam C, Santos D, Oliveira T (2020) Exploring the influential factors of continuance intention to use mobile Apps: extending the expectation confirmation model. Inf Syst Front 22(1):243–257
Tangke N (2004) Analisa Penerimaan Penerapan Teknik Audit Berbantuan Komputer (TABK) Dengan Menggunakan Technology Acceptance Model (TAM) Pada Badan Pemeriksa Keuangan (BPK) RI. Jurnal Akuntansi Dan Keuangan 6(1):10–28
Taylor DG, Strutton D (2010) Has e-marketing come of age? Modeling historical influences on post-adoption era Internet consumer behaviors. J Bus Res 63(9–10):950–956
Taylor S, Todd P (1995) Decomposition and crossover effects in the theory of planned behavior: a study of consumer adoption intentions. Int J Res Mark 12(2):137–155
Thompson RL, Higgins CA, Howell JM (1991) Personal computing: toward a conceptual model of utilization. MIS Q 1:125–143
Tsai Y-Y, Chao C-M, Lin H-M, Cheng B-W (2018) Nursing staff intentions to continuously use a blended e-learning system from an integrative perspective. Qual Quant 52(6):2495–2513
Vallerand RJ (1997) Toward a hierarchical model of intrinsic and extrinsic motivation. In: Advances in experimental social psychology, vol 29. Elsevier, pp 271–360
Venkatesh V, Davis FD (2000) A theoretical extension of the technology acceptance model: Four longitudinal field studies. Manag Sci 46(2):186–204
Venkatesh V, Morris MG, Davis GB, Davis FD (2003) User acceptance of information technology: toward a unified view. MIS Q 1:425–478
Venkatesh V, Thong JYL, Xu X (2012) Consumer acceptance and use of information technology: extending the unified theory of acceptance and use of technology. MIS Q 1:157–178
Wu T-H, Huang SY, Lin C-W (2020) Relationship quality, computer auditing and information security for mobile industry. Int J Mobile Commun 18(4):405–419
Yang DC, Guan L (2004) The evolution of IT auditing and internal control standards in financial statement audits: the case of the United States. Manag Auditing J 19:544
Zainol SS, Samsuri AS, Tunku Arifin TR, Hussin S, Othman MS, Jie SJ (2017) Determinants of computer assisted audit techniques (Caats) adoption: A study in small and medium practices in Malaysia. Eur J Bus Soc Sci 6(2):135–150
Acknowledgements
Not applicable.
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
AM, the first author, wrote the original draft, collected and analyzed the data and designed the methodology and revisions. AA, the second author, contributed to the conceptualization, supervision, Writing the original draft, data analysis, editing and revision. TK was involved in the theoretical and empirical justification, English editing, and proofreading. OA, the corresponding author, drafted the introductory and literature review sections, also drafted the conclusion and recommendation section and harmonized the different sections of the paper in line with the Journal Template. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
The research study was approved by Jazan University, Research Ethics Committee on 15 May 2022 with the approval number REC-43/10/228.
Consent for publication
Not applicable.
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Almagrashi, A., Mujalli, A., Khan, T. et al. Factors determining internal auditors’ behavioral intention to use computer-assisted auditing techniques: an extension of the UTAUT model and an empirical study. Futur Bus J 9, 74 (2023). https://doi.org/10.1186/s43093-023-00231-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s43093-023-00231-2