Abstract
The study proposed a novel multiple-image encryption scheme using spatial multiplexing under the illumination of a multi-petals structured light. The security is enhanced through the multi-petals structured light with coherent superposition of several vortex beams with different topological charges. Through the system, an image array is formed behind the sub-petals of the complex structured light. Using Fresnel diffraction, each image is encrypted into the ciphertext by the Fibonacci Lucas transform. The multi-petals structured light with different orbital angular momentum can integrate more system parameters as the additional keys resulting in rich key space with improved security level of the cryptosystem. The feasibility and security of the proposed methods are validated through both numerical simulation and experiments. The research has strong and practical applications for three-dimensional information encryption system.
Similar content being viewed by others
Image encryption is important for secure engineering and science applications1. In contrast to digital image encryption, optical image encryption has evident advantages including parallel processing through harness of properties of light2,3,4. Optical image encryption was started through the pioneer single image encryption work of double random phase encoding developed by Refregier and Javidi5, which is further extended by other work mostly including single image encryption algorithms and architectures6,7,8,9,10,11,12,13. Other single image optical encryption methods include Fresnel transform7, gyrator transform8, fractional Fourier transform9, ghost imaging10, diffractive imaging11, digital holography12 and optical scanning holography13 have also been proposed. The primary limitation of the single image optical encryption is due to its limited encryption efficiency thus compromising its practical uses.
Multiple-image encryption technology can encrypt multiple images simultaneously thus is more efficient2,14,15,16,17,18,19,20,21. A number of methods exist to achieve multiple-image optical encryption and decryption. Among them, Situ et al. 14,15 used wavelength and position multiplexing methods to achieve multiple-image encryption. Deepan et al.16 implemented a multiple-image encryption method using spatial multiplexing and compressive sensing in conjunction with double random phase encoding. Other methods include phase-only mask multiplexing17 and cascaded fractional Fourier transforms18, which are known able to reduce the cross-talk noise. The deep learning based multiple-image encryption has been developed, while effective, the encryption methods are still vulnerable to brute-force attacks and lack of strong security performance19,20. These schemes are effective, however, most of these algorithms have small key spaces making them weak against brute-force attacks and has shortcomings in security performance.
Orbital angular momentum characterized by the vortex phase structure has been extensively studied owing to its unique properties, which has attracted attention in the field of optical encryption22. Sui et al. proposed an optical multiple-image encryption method based on the chaotic structured phase masks under the illumination of a vortex beam in the gyrator domain23. Further discussion on multiple-image encryption based on optical vortex using fractional Hartley transform24, linear canonical transform25 and Gyrator transform26,27 has been stated by Singh et. al., which can enhance the security of cryptographic system. Yan et al. used the spiral phase key to replace the random phase key in the optical holography encryption system28. Compared with the random phase plate, the spiral phase plate has stronger resistance to ciphertext attack. The significant drawback of the current approach using vortex beam encryption is mostly due to its limited efficiency due to the single image encryption scheme, the target images are encoded by only one orbital angular momentum mode, which limits the encoded information security. The improvement of the vortex structure or combining the additional parameters have attracted attention29,30,31,32, such as phase jump gradient factors-based OAM multiplexing holography33, Coherent Multimode OAM Superposition34 and multiple-dimensional OAM holography35. So it is interesting and meaningful to develop a novel structured light carried multiple topological charges and apply it into the area of multiple-image encryption.
This paper presents a novel approach to multiple-image encryption by spatial multiplexing with a multi-petals structured light. The proposed structured light is generated by the coherent superposition of vortex beams with different topological charges. The proposed scheme has several advantages, including increased the capacity and strength of the encryption system, and convenience in optical execution. Specifically, multiple encryption parameters including the Fresnel diffraction distances, the wavelength of light, and the optical parameters of the vortex beams such as topological charge number are all used to expand the key space. The use of complex structured light with multi-petals intensity distribution in the Fresnel domain with spatial multiplexing has not been explored before. The proposed multiple-image encryption method has been verified with simulation and experiments. The novel coherent superposition method exhibits high effectiveness and strong robustness applicable to multiple different applications.
Principles and methods
Generation of multi-petals structured light
The overall vortex beam optical beam structure is shown in Fig. 1, which is calculated based on Eqs. (1) and (2) using the software Matlab (R2022b). The Laguerre-Gaussian (LG) vortex beam contains orbital angular momentum with a helical distribution of phase structure and a phase singularity at zero light intensity at the center of the beam. For the LG beam in the spatial domain, the light field is expressed as Ref.22:
where \(p\) is the radial index, \(l\) is the topological charge, \(\omega (z)\) is the spot size at a distance \(z\), \(\varphi\) is the azimuth angle, \(k=\frac{2\pi }{\lambda }\) is the wave number, \({\omega }_{0}\) is the waist width of Gaussian amplitude. Taking optical vortex array as the target beam, we consider the coherent superposition of multiple vortex beams loaded with discrete topological charge l, where centers are co-axis, and each sub-beam has the same radial index p = 0. The coherent superposition of vortex beams can generate multi-petals structured light, which can be expressed as
where N denotes the number of OAM modes and the value of topological charge l is arithmetic sequence, \(A(r)=\frac{\sqrt{2/\pi }}{w(z)}exp(-\frac{{r}^{2}}{{w(z)}^{2}})\), \(B(r,{l}_{n})=\sqrt{1/|{l}_{n}|!}{(r\sqrt{2}/w(z))}^{|{l}_{n}|}\).
Generation of the multi-petals structured light. (a1–a2) 3D, (b1–b2) 2D and (c1–c2) phase maps of the multi-petals structured light generated by the vortex beams with \({l}_{n}= {l}_{1}+\Delta l, {l}_{1}=1,\Delta l = 3 \text{and} 4\). The multi-petals structured light can be generated by illuminating a spatial light modulator which loads specific phase function as is shown in Fig. 1c1 and c2.
Figure 1 shows the example of the multi-petals structured light with sub-beams N = 3 and N = 4, \({l}_{n}= {l}_{1}+\Delta l.\) Fig. 1a1–c1 show the 3D, 2D maps and the phase diagram of the multi-petals structured light, which consists of three sub-beams, where \({l}_{1}=1,\Delta l\) = 3. These sub-beams can be used to encode the plain images. The number of \(\Delta l\) determines the number of sub-beams, which can be denoted as an additional key in the proposed method. Figure 1a2–c2 show the 3D, 2D maps and the phase diagram of the multi-petals structured light, which consists of four sub-beams, where \({l}_{1}=1,\Delta l\)= 4. The multi-petals structured light can be generated in experiment by illuminating a spatial light modulator which loads specific phase function as is shown in Fig. 1c1 and c2. It is evident that the beams are featured with intensity pattern of bright and dark spots, which is called as multi-petals structured light and formed due to the destructive interference of the co-axially superimposed vortex beams at equal intensities. As shown in Fig. 1b2, the four sub-beams of the multi-petals structured light will be used to encrypt four plain images. The number of \(\Delta l\) are able to be increased thus leading to the increased number of images to be encrypted indicating the scalability of the methods.
Encryption process
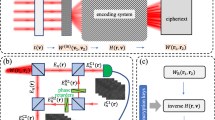
The process of multiple-image encryption is shown in Fig. 2. The proposed encryption process can be divided into three specific steps. First, the spatially separated optical vortex array is generated by coherent superposition of multiple vortex beams with different topological charge. It is followed by position multiplexing and Fresnel diffraction propagation to encode the multiple images. The images to be encrypted are put behind each sub-beams of the multi-petals structured light at different distances z1, z2, z3, z4. Finally, the Fibonacci Lucas transform is used to encrypt the Fresnel diffraction patterns to obtain the final ciphertext at the position z6.
The multi-image encryption scheme. It shows the process of encryption of the multiple images using multi-petals structured light. Each image is encrypted with a sub-beam profile of the multi-petals structured light. The encrypted images are subsequently encrypted with Fibonacci Lucas transform. Multi-petals Structured Light (MSL); Fibonacci Lucas transform (FLT).
After obtaining multiple images diffraction patterns, which shows the ability to encode 3D information and also work as space distance encryption keys, the Fibonacci Lucas transform is applied for another encryption36. The Fibonacci Lucas transform is used to mapped \({FL}_{n}\): \({T}^{2}\to {T}^{2}\), for example:
where(x,y), (x’,y’) ϵ (0,1,2…M-1), M is the size of the digital image, Fi is the ith Fibonacci number of the Fibonacci series, and Li is the ith Lucas number of the Lucas series. In our simulation and experiment, the Fibonacci number is set up as 30 and the output image is gained as encryption result. The encryption result is presented in Fig. 3, which evidently, is immune to the unauthorized access.
Decryption process
As a symmetric encryption algorithm framework, multiple original images can be recovered from the ciphertext image by utilizing the exact key stream and the corresponding inverse operations. The decryption process is shown in Fig. 4. Firstly, the ciphertext image was processed by Fibonacci Lucas inverse transform. Secondly, the Fresnel inverse diffraction is performed on the newly generated image and four sectional images are deduced at z1, z2, z3 and z4, which will yield the original images of “S”, “H”, “N” and “U” by the correlation operation.
Experiments
Experiment setup
Optical experiments have been carried out to further validate the execution of the proposed multiple-image encryption scheme shown in Fig. 5. The light source used in our experiment is a semiconductor Laser with wavelength of 514.5nm and the spot size of Gaussian beam is approximately 1.5mm. The spatial light modulator (SLM1) is used to generate the proposed multi-petals structured light. An expand system with two lens (L1 and L2) and a pinhole located in the focal plane of L1 and L2 is used to estimate the high frequency noise and expand the multi-petals structured light. It is followed by the four images arranged along different distances in the space to be encoded by the multi-petals structured light with certain diffraction. The second spatial light modulator (SLM2) is used for the encryption of the multi-petals structured light by Fibonacci Lucas transform and the ciphertext images are imaged by a charge-coupled device (CCD). Both of the spatial light modulators (PLUTO, NIR144) used in this experiment have a pixel pitch of 7.0 μm and a resolution of 1920 × 1080 pixels.
It is important to have precise phase distribution being loading on the SLMs to start the experiment. The phase generation methods are discussed in below. For this, we focus on the generation of the multi-petals structured light through the phase-only SLM1. The first step is to generate the holograms. We derive the amplitude and phase of the electric field of multi-petals structured light in Eq. (2). The desired computer-generated hologram loaded on the phase-only SLM1 is expressed as
where FOVA can be obtained by numerical inversion of J1(FOVA) = Abs[\(E(x,y,z)\)], which is the first-order Bessel function37. The hologram used in the experiment is shown in the sub-image in the upper left corner of Fig. 5. Grating is involved in the computer-generated hologram on the SLM1. The grating with the phase shift of \(2\uppi {f}_{x}x\) is a blazed grating, where \({f}_{x}\) is the grating frequency that determines the diffraction angle of the light reflected from the SLM1 in the x direction. The hologram contains the amplitude and phase modulations. The depth of the grating and spatial phase delay controls the intensity and wave-front of incident light, respectively.
For encryption of the image, the phase distributions loaded on SLM2 can be carried out by the gradient descent method38. Specifically, the physical process that encrypt the multi-petals structured light by SLM2 can be written as:
where \({E}_{in}\) is the incident light field carried plaintext images, \({E}_{out}\) is the encrypted light field, and \({e}^{iM\varphi }\) is the phase distribution loaded on the SLM to optically realized the Fibonacci Lucas transform. According to the gradient descent method, the phase distribution is provided at each iteration as follows:
where u and v represent the coordinates of the light field, \({\theta }_{uv}\) is the phase function, \({\gamma }_{t}\) is the step length coefficient for iteration, t is the iteration number, and L is the loss function used in the optimization, which is defined by the MSE factor:
where \({E}_{out}{\prime}\) is the simulation light field obtained by Fibonacci Lucas transform, U and V are the numbers of rows and columns of the light field. With these two-phase distributions produced and loaded perfectly, the proposed multi-petals structured light can be generated successfully and encrypted by Fibonacci Lucas transform in optical experiment.
Experiment results
The experimental results are shown in Fig. 6. Specifically, Fig. 6a is the intensity distribution of the multi-petals structured light output from the SLM at z0. Figure 6b to e are the Fresnel diffraction patterns at the position of \({z}_{1}\), \({z}_{2}\), \({z}_{3}\), and \({z}_{4}\), respectively. It is evident that based on Fig. 6b to e, the Fresnel diffraction pattern at the position z4 carries the information of four plaintext images. The unclear phase images with the increase of the Fresnel diffraction distance, shows that the distance of Fresnel diffraction is also useful for enhancing information security. Figure 6f shows the ciphertext image at \({z}_{6}\). It is evident that the proposed cryptosystem effectively encodes the input of multiple-images into ciphertext image having pixel distribution identical to stationary white noise, which cannot be recovered with wrong keys evident by the security analysis. Through the decryption process, the inverse transformation of the Fibonacci Lucas transform was used, and then performed the inverse transformation of Fresnel diffraction at different diffraction distances to obtain the decrypted images at the corresponding positions, as shown in Fig. 7.
System security analysis
Mean square error and peak signal-to-noise ratio analysis
To quantitatively analyze the ciphertext image and the decrypted image, the mean square error (MSE) and the peak signal-to-noise ratio (PSNR) are adopted. The mean square error is a common loss function,
where N2 is the size of test images, O(i, j) is the pixel value of the original image at position (i, j). C(i, j) denotes either a ciphertext or decrypted image derived from MSE39,40:
PSNR1 and MSE1 are calculated between the original image and the ciphertext image. PSNR2 and MSE2 are calculated between the original and the decrypted images. Higher MSE value indicates the greater the difference between the original image and ciphertext image. As shown in Table 1, it is evident that the value of MSE1 is higher than MSE2 thus showing the weak correlation between the original image and the ciphertext image. Correspondingly, the PSNR2 value increases along with the improved quality of the decrypted images.
Noise attack analysis
The performance of the encryption systems to withstand noise attacks is analyzed through the Salt & Pepper noise and the Gaussian noise analysis. The correlation coefficient (CC) is used to evaluate the quality of decryption and the CC value of the original image and the decrypted image is calculated mathematically as shown in the Eq. (10). Among them, A1(x, y) represents the pixel value of the original image with M × N pixels, A2(x, y) represents the pixel value in the decrypted image. \(\overline{{A_{1} (x,y)}}\) and \(\overline{{A_{2} (x,y)}}\) means taking the average of the gray values of all pixels. If the CC value between two images is closer to 1, the correlation between two images is larger, if the absolute value is closer to 0, the correlation between two images is weaker.
Figure 8 shows the decrypted images with different intensity of 0.01, 0.05 and 0.1 Salt & Pepper noises. The PSNR and the correlation coefficients between the original images and decrypted images are listed in Table 2 to evaluate the quality of the decrypted images. From Fig. 8 and Table 2, we can see that the ciphertext is immune to Salt & Pepper noise pollution. The decrypted images have a correlation with the original images given the presence of severe noises, where the original images are evident in the decrypted images. The impacts of Gaussian noise with intensities 0.2, 0.5 and 0.9 are also studied shown in Fig. 9 and Table 3. Figure 9a1–a4 are the decrypted images given the Gaussian noise intensity variance of 0.2, where the correlation coefficients are 0.7411, 0.8185, 0.6924, 0.7784. Figure 9b1–b4 show the decrypted images when the Gaussian noise intensities with variance of 0.5, where the correlation coefficients are 0.6130, 0.6958, 0.6658, 0.7080. Figure 9(c1—c4) are the decrypted images when the Gaussian noise intensities with variance of 0.9, where the correlation coefficients are 0.3173, 0.3699, 0.3702, 0.3736. It is proved that the proposed encryption system has strong anti-Gaussian noise pollution capability.
Occlusion attacks analysis
The system occlusion attacks are also evaluated. Figure 10 shows the ciphertext images with different degrees of occlusion and their corresponding reconstructed images. Four sub-blocks of various sizes are cropped in the ciphertext images resulting in the loss 1/5, 2/5, 3/5 and 4/5 of data. It is evident that given the decrypted images still clear even though the ciphertext is subjected to a various degrees of information loss due to occlusion. Similarly, the PSNR and CC values to measure the quality of decryption image are tabulated in Table 4. The primary properties of the original images have been dispersed across the entire ciphertext image, so even if the decryption images are blurred, the essential characteristics are still accessible under data loss. When the ciphertext is subjected to a partial clopping, the decryption image still has a certain correlation with the original image, indicating that the proposed encryption system has a good ability to resist occlusion attack.
Ciphertext subjected to different degrees of occlusion: (a1) 1/5 occlusion, (a2) 2/5 occlusion, (a3) 3/5 occlusion and (a4) 4/5 occlusion, respectively; (b1,c1,d1,e1) decryption images of (a1); (b2,c2,d2,e2) decryption images of (a2); (b3,c3,d3,e3) decryption images of (a3); (b4,c4,d4,e4) decryption images of (a4).
Adjacent pixel correlation analysis
To prevent the attackers to obtain useful information about images by analyzing the correlation among adjacent points of the decrypted images, the correlation coefficient of neighboring pixels including the correlation between pixels in the horizontal, diagonal, and vertical directions are analyzed. First, 2000 pairs of two adjacent (in horizontally, vertical, and diagonal direction) pixels from an image were randomly selected. A strong encryption of an image is able to reduce the correlation between adjacent pixels of an image. Figure 11a–d show the correlation distributions of the original images and their corresponding ciphertext images Fig. 11e in the horizontal, vertical and diagonal directions. It can be seen that the ciphertext image with the suggested multi-image encryption system display a low level correlation distribution, while the correlation distributions in the three directions of the original images show strong correlation.
Specific attack analysis
For an information encryption system, it could be described as robust and secure if only it were able to resist four basic attacks, such as cipher-text only attacks (COA), known plain text attacks (KPA), chosen plain text attacks (CPA), chosen cipher-text attacks (CCA). Among them, cipher-text only attack is the most powerful attack for the proposed multiple-image encryption scheme using spatial multiplexing under the illumination of a multi-petals structured light. The generation of the multi-petals structured light is related to the vortex parameters. So the proposed scheme is highly sensitive to the phase parameter. COA assumes that the attacker is familiar with the proposed encryption system and knows the ciphertext image but does not know the decryption keys. In this paper, we use the hybrid input–output (HIO) algorithm, a phase retrieval algorithm to perform the cipher-only attack41. Assuming the attacker intercepts the ciphertext image, as shown in Fig. 12a. With HIO algorithm, we can retrieve the decrypted image after 400 iterations, as shown in Fig. 12b. It is obvious that the relevant plaintext information cannot be attacked successfully. So, the proposed encryption system is secure enough to resist cipher-text only attacks.
Performance comparison
The comparison of the performance of the proposed scheme with some of the previous image encryption schemes has been done and is shown in Table 5. It can be seen from Table 5 that multi-petals structured light based encryption scheme expands the key space and improves the security of the cryptosystem.
Conclusions
Through the research, a novel multiple-image encryption scheme based on the coherent superposition of multiple vortex beams with different topological charges and Fresnel diffraction is proposed. Simulations and experimental results demonstrated that the proposed method is able to encrypt and decrypt the information of multiple-images effectively. The system benefits from multiple encryption parameters characteristic of the multi-petals structured light including Fresnel diffraction distance, the topological charges and spatially position to be considered to enhance system security. The security analyses show that the proposed method possesses the advantage of strong noise resistance and high robustness to noise and cropping attacks. The proposed method will be useful for highly efficient for real-world multiple-image encryption applications.
Data availability
The datasets presented in this study are available from the corresponding author on reasonable request.
References
Kolivand, H., Hamood, S. F. & Asadianfam, S. Image encryption techniques: A comprehensive review. Multimed. Tools Appl. https://doi.org/10.1007/s11042-023-17896-0 (2024).
Abdurrahman, H. & Yildirim, R. A review of single and multiple optical image encryption techniques. J. Opt. 23, 113501 (2021).
Liu, S., Guo, C. & Sheridan, J. T. Review of optical image encryption techniques. Opt. Laser Technol. 57, 327–342 (2014).
Javidi, B., Carnicer, A. & Yamaguchi, M. Roadmap on optical security. J. Opt. 18, 083001 (2016).
Refregier, P. & Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20, 767–769 (1995).
Matoba, O., Nomura, T., Perez-Cabre, E., Millan, M. Í. S. & Javidi, B. Optical techniques for information security. Proc. IEEE 97, 1128–1148 (2009).
Situ, G. & Zhang, J. Double random-phase encoding in the Fresnel domain. Opt. Lett. 29, 1584–1586 (2004).
Liu, Z., Xu, L., Lin, C., Dai, J. & Liu, S. Image encryption scheme by using iterative random phase encoding in gyrator transform domains. Opt. Lasers Eng. 49, 542–546 (2011).
Yu, S., Zhou, N. & Gong, L. Optical image encryption algorithm based on phase-truncated short-time fractional Fourier transform and hyper-chaotic system. Opt. Lasers Eng. 124, 105816 (2020).
Zafari, M., Kheradmand, R. & Ahmadi-Kandjani, S. Optical encryption with selective computational ghost imaging. J. Opt 16, 105405 (2014).
Chen, W., Chen, X. & Sheppard, C. J. R. Optical image encryption based on diffractive imaging. Opt. Lett. 35, 3817–3819 (2010).
Javidi, B. & Nomura, T. Securing information by use of digital holography. Opt. Lett. 25, 28–30 (2000).
Yan, A., Sun, J., Hu, Z., Zhang, J. & Liu, L. Novel optical scanning cryptography using Fresnel telescope imaging. Opt. Express 23, 18428–18434 (2015).
Situ, G. & Zhang, J. Multiple-image encryption by wavelength multiplexing. Opt. Lett. 30, 1306–1308 (2005).
Situ, G. & Zhang, J. Position multiplexing for multiple-image encryption. J. Opt. A Pure Appl. Opt. 8, 391–397 (2006).
Deepan, B., Quan, C., Wang, Y. & Tay, C. J. Multiple-image encryption by space multiplexing based on compressive sensing and the double-random phase-encoding technique. Appl. Opt. 53, 4539–4547 (2014).
Qin, Y., Jiang, H. & Gong, Q. Interference-based multiple-image encryption by phase-only mask multiplexing with high quality retrieved images. Opt. Lasers Eng. 62, 95–102 (2014).
Sui, L. S., Zhang, X. & Huang, C. T. Silhouette-free interference-based multiple-image encryption using cascaded fractional Fourier transforms. Opt. Lasers Eng. 113, 29–37 (2019).
Zhang, L., Zhou, X. & Wang, D. Multiple-image encryption based on optical scanning holography using orthogonal compressive sensing and random phase mask. Opt. Eng. 59, 1–6 (2020).
Zhuang, X., Yan, A., Tsang, P. W. M. & Poon, T.-C. Deep-learning based reconstruction in optical scanning holography. Opt. Lasers Eng. 158, 107161 (2022).
Li, W., Yan, A. & Zhang, H. Novel multiple-image encryption scheme based on coherent beam combining and equal modulus decomposition. Appl. Sci. 11, 9310 (2021).
Padgett, M. J. Orbital angular momentum 25 years on. Opt. Express 25, 11265–11274 (2017).
Sui, L., Zhou, B., Ning, X. & Tian, A. Optical multiple-image encryption based on the chaotic structured phase masks under the illumination of a vortex beam in the gyrator domain. Opt. Exp. 24, 499–515 (2015).
Singh, H. Nonlinear optical double image encryption using random-optical vortex in fractional Hartley transform domain. Optica Applicata 47, 557–578 (2017).
Singh, H. & Khurana, M. An asymmetric optical cryptosystem of double image encryption based on optical vortex phase mask using gyrator transform domain. Recent Adv. Comput. Sci. Commun. 13, 672–685 (2020).
Singh, H., Tirth, V., Singh, R. K., Algahtani, A. & Islam, S. Designing of an optical vortices phase mask and used in the frequency domain of linear canonical transform for double image encryption. Imaging Sci. J. 68, 288–304 (2022).
Hukum Singh, Poonam Yadav. An optical vortex-based asymmetric cryptosystem using QZ modulation for the double image encryption in the gyrator transform. Iran J Comput Sci (2024).
Yan, A. et al. Multiple-image encryption based on angular-multiplexing holography with quick response code and spiral phase keys. Appl. Opt. 58, G6–G10 (2019).
Zeng, R. & Yang, Y. Generation of an asymmetric optical vortex array with tunable singularity distribution. J. Opt. Soc. Am. A 38, 313–320 (2021).
Lin, Y. C., Lu, T. H., Huang, K. F. & Chen, Y. F. Generation of optical vortex array with transformation of standing-wave LaguerreGaussian mode. Opt. Exp. 19, 10293–10303 (2011).
Kumar, P., Nishchal, N. K. & AlFalou, A. Controllable optical vortex array for image encoding. IEEE Photon. Technol. Lett. 34, 521–524 (2022).
Shikder, A., Rao, S. K., Kumar, P. & Nishchal, N. K. Binary image encryption with a QR code-encoded optical beam having an array of vortices. J. Opt. Soc. Am. A 41, A73–A82 (2024).
Fang, X. Y., Ren, H. R. & Gu, M. Orbital angular momentum holography for high-security encryption. Nat. Photon. 14, 102–108 (2020).
Li, F., Ding, H., Nie, S., Ma, J. & Yuan, C. Multiple-image encryption using phase jump gradient factors-based OAM multiplexing holography. Opt. Lasers Eng. 160, 107303 (2023).
Anguita, J. A., Herreros, J. & Djordjevic, I. B. Coherent multimode OAM superpositions for multidimensional modulation. IEEE Photon. J. 6, 1–11 (2014).
M. Mishra, P. Mishra, M. Adhikary, S. Kumar. Image Encryption Using Fibonacci-Lucas Transformation. Inter. J. Crypto. Info. Secu. (IJCIS). 2012: 2312.
Liu, X. et al. Experimental realization of scalar and vector perfect Laguerre-Gaussian beams. Appl. Phys. Lett. 119, 021105 (2021).
Liu, S. & Takaki, Y. Optimization of phase-only computer-generated holograms based on the gradient descent method. Appl. Sci. 10, 2076–3417 (2020).
Shen, D., Jiang, X. & Teng, L. A novel Gauss-Laplace operator based on multi-scale convolution for dance motion image enhancement. Eur. Union Digit. Libr. 17, 172439 (2021).
Setiadi, D. PSNR vs SSIM: Imperceptibility quality assessment for image steganography. Multimed. Tools Appl. 80, 8423–8444 (2021).
Chang, X., Yan, A. & Zhang, H. Ciphertext-only attack on optical scanning cryptography. Opt. Las. Eng. 126, 105901 (2020).
Acknowledgements
The authors acknowledge the support from the National Nature Science Foundation of China (Grant No. 62075134).
Author information
Authors and Affiliations
Contributions
He-Ming Tian: Methodology, Investigation, Formal analysis, Writing –original draft. Xu-Sheng Zhuang: Methodology, Investigation, Formal analysis, Writing-review & editing. Ai-Min Yan and Hong-bo Zhang: Conceptualization, Investigation, Resources, Supervision, Project administration, Writing–review & editing.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Tian, H., Zhuang, X., Yan, A. et al. A novel multiple-image encryption with multi-petals structured light. Sci Rep 14, 19559 (2024). https://doi.org/10.1038/s41598-024-70425-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-024-70425-3
- Springer Nature Limited