Abstract
Grid-connection of new energy is highly important in promoting the use of clean and renewable energy. However, it will bring huge risks to the power grid operation security, such as frequency stability, voltage stability, small signal stability, and transient stability, etc.,. In the study, SWOT (Strengths, Weaknesses, Opportunities, and Threats) analysis has been employed to construct 24 kinds of internal and external evaluation factors and 8 kinds of improvement strategies, for assessing operation security prospective with new energy power system of HM in China. The weights of SWOT factors are determined with the fuzzy-AHP method. Moreover, the fuzzy-MARCOS approach is used to select the most suitable strategies for power system operation security effective implementation. The reported research reveals that new energy in HM area not only has an ample potential for full development and generating electricity, but also brings operation security problems due to large-scale grid connection. Therefore, 8 kinds of improvement strategies are suggested to encourage the government to exploit and develop new resources, improve the investment pay, power generation and transmission technologies to mitigate the current energy crisis, and increase the energy security for sustainable development of the country. The methodology proposed herein is applicable with a case study concerning the operation security prospective of HM power grid, and all phases of the comparative analysis and sensitivity analysis illustrate the validity of MARCOS method. Furthermore, the ranked order of strategies is obtained as A2 > A6 > A5 > A1 > A8 > A7 > A4 > A3. The three most important strategies are A2, A6 and A5, i.e., “improving the technical establishment to encourage efficient and cheap electricity production”, “strive to build local permanent load, and reduce the risk of long-distance and high-capacity transmission”, “taking advantage of government incentives and investment to modify the irrational energy policies and energy planning”, respectively.
Similar content being viewed by others
Introduction
HM is one of the rich regions in terms of new energy resources, which are wind and solar resources, and coal resources. Relying on the perfect Northwest China power transmission channel, HM has accelerated the construction of 10 million kW coal power base, 10 million kW wind power base and 1 million kW solar thermal power generation demonstration base; and has built the largest wind and fire binding transmission HVDC base in China. The development of wind power technology in HM has reached 75.498 million kW, accounting for 62.9% of the total technology development in Northwest China. In terms of solar energy resources, HM has 3170–3380 h of sunshine throughout the year, and is one of the areas with most abundant sunshine hours in China. Although HM power grid offers such great advantages in the development of new energy, the large-scale grid connection and long-distance transmission of new energy raises concerns about the operation security of HM power grid. Therefore, the security and stability of HM power grid has become the focus of our research.
Power system security is a characteristic of power system in the operation process, which reflects the ability of the system to continue supplying power to users with required parameters after experiencing possible disturbances1,2. Although most countries take “safety first” as a policy to guide the operation of power system, some countries even raise the power system to the national strategic defense system3,4, even so, blackouts still occur from time to time, indicating that the ability of current power systems is still unsatisfactory to deal with the emergencies5,6.
At present, with the continuous development of China’s power system and interconnection scale, China’s power workers have built a strong and stable protection and control system based on three lines of defense to ensure a stable operation, which ensures the stability of the power grid and the power quality supplied to users, to a great extent. Tant is so say, power outage accidents in large areas are almost impossible to occur in China. The first line of defense relies on the reliable and rapid action of relay protection elements, to ensure that the system can restore stable operation in time and supply power normally in case of a single fault. Progressively, the second line of defense includes a series of emergency control measures, which can ensure a stable operation of the system at a low cost, after suffering from low probability but serious disturbance. The main measures include machine cutting, load cutting, local splitting and DC modulation. In engineering practice, the control framework of “off-line pre-decision and real-time matching” is often used to form a large number of emergency control strategy tables of the expected faults in the off-line stage. The significance of the third line of defense is that when the system encounters some rare serious faults and can no longer maintain a stable operation, it must prevent the system collapse and minimize the load loss, that is, reasonable disconnection. However, there is no mature scientific connection between the three lines of defense at present. These lines of defense are still event driven and act gradually according to the development of events.
With the rapid development of national economy and the increasing improvement of people’s living standards, people’s demand and dependence on power are becoming greater and greater, and consequently, the requirements for power supply reliability are becoming stronger and stronger7,8. Certainly, due to the impact of natural environment, new energy power generation has some randomness and intermittency. For example, when wind power is connected to the power grid, the security and stability of the power grid will be affected by the wind power characteristics, wind power installed capacity, system scale of wind power connected to the power grid, power structure and layout, and load characteristics, etc. Moreover, the installed capacity of new energy affects the frequency stability of the system, thereby affecting the power quality of power grid and the normal operation of some frequency sensitive loads. In addition, new energy has weak inertia support, strong output uncertainty, poor frequency regulation ability and damping characteristics, resulting in the increasingly prominent problem related to system frequency stability. When the new energy loses its output due to energy shutdown or stall, the frequency of the power system will be reduced, especially when the penetration level of new energy is high, which will directly affect the frequency stability of the system. Hence, the new energy itself cannot provide reactive power compensation to the system, thus it worsens the voltage level, reduces the power quality of the system, and affects the voltage stability of the system. In addition, new energy is a source of interference for the power system, however, when the system fails, and the fault is not removed in time, transient voltage instability will occur. All these issues demand a higher amount of technical attention for the safe and stable operation of new energy power system9,10,11. Modern power system has gradually developed into a complex large-scale system with the characteristics of multi-level structure, multi time scale, multiple control parameters, dynamics, real-time, nonlinearity, openness, wide area, uncertainty, non-autonomy and social economy12,13,14. Therefore, the security level of a power system is difficult to be characterized using a single index. However, the conventional security analyses, whether static security analysis8,15,16,17 or dynamic security analysis18,19,20,21,22, usually can only analyze one aspect of the power system security, which is certainly not enough to describe the power system security as a whole. Therefore, only through comprehensive, multi-level and multi angle analysis of all the aspects of the system including the randomness and fuzziness of components, loads and external conditions, with the help of comprehensive evaluation method, can we obtain an objective and overall understanding of the power system security23.
The so-called comprehensive evaluation refers to the objective, fair and reasonable evaluation of different aspects of the evaluated object. Its core includes the index system of the evaluated object and the selected evaluation method24. At present, the Multi-Criteria Decision-Making (MCDM) method corresponds to a powerful tool being widely used for comprehensive evaluation, such as analytic hierarchy process (AHP)23,24,25,26,27, entropy weight (EW)25,26,27,28, cloud method (CM)24,28, grey relation analysis (GRA)29, analytic network process (ANP)30,31,32, Decision Making Trialand Evaluation Laboratory (DEMETEL)31,32,33,34,35, Više-Kriterijumska Optimizacija I Kompromisno Rešenje (VIKOR)33,34,35,36,37,38,39, and technique for order of preference by similarity to ideal solution (TOPSIS)28,36,37,38,39 evaluation method based on evidence theory. These MCDM evaluation methods are currently being used for ranking of indicators, risk identification and evaluation, sustainable development evaluation between countries, economic evaluation, social evaluation, environmental protection evaluation, technical evaluation, and other issues. However, it has been hardly ever used in the power system security evaluation. In addition, the SWOT analysis with internal (Strengths and Weaknesses) and external factors (Opportunities and Threats) is also a powerful tool, which helps to reveal different strategies for decision-makers and participants40. SWOT analysis is widely used in future prospective in different fields, but is not sufficient for decision making. Alternatively, MCDM methods can be helpful to overcome such problem41,42,43,44,45,46, which are used to make based on pair-wise comparison of both criteria and alternatives43. For this reason, one of the MCDM methods— AHP is used for SWOT analysis in this study. The SWOT-fuzzy AHP has been used to perform the strategic renewable energy resources selection for Pakistan47. Meanwhile, the integrated SWOT-AHP and Fuzzy-TOPSIS approach has been employed for evaluating the strategies for sustainable energy planning in Pakistan48. Nevertheless, there is no single study that utilizes SWOT-AHP approach to evaluate and select the optimal improvement strategy for power system operation security prospective.
In this study, the proposed SWOT-fuzzy AHP-MARCOS methodology is utilized for power system operation security perspective evaluation and investigating the strategic advantages in a case study of HM power grid in Northwest China. The obtained results are compared with VIKOR and TOPSIS methods to validate the proposed integrated SWOT-fuzzy AHP method and measurement of alternatives and ranking according to compromise solution (MARCOS) methodology39.
Proposed method
This section first explains the SWOT method, its components, and its use in the literature. Following that, the proposed methodology is presented.
SWOT analysis
The SWOT analysis is a commonly used strategic analysis method that helps to identify the capabilities or deficiencies of an organization while considering the grid opportunities and threats for the future. However, SWOT analysis method can not quantitatively evaluate the factors, and can not objectively compare the priority between factors. Furthermore, a SWOT matrix may contain different strategies concerning its dimensions and factors, which are prepared based on strength-opportunity (SO), weakness-opportunity (WO), strength-threat (ST) and weakness-threat (WT) strategies; The strategies related to SWOT dimensions are given in Fig. 1.
Some of the advantages of SWOT analysis are listed as follows:
-
It allows attention to the positive and negative aspects of the external and internal environment of the system;
-
By understanding the weaknesses, it helps to identify opportunities to take advantage of strengths and eliminate threats;
-
Determining the SWOT factors of the research object through group discussions provides the basis and support for the strategic decision-making;
-
It can be used at different levels in different industries, organizations, countries or governments, such as individual, national, organizational, and international levels.
The combination of SWOT analysis and MCDM method, such as AHP, has been used to determine the weight of each SWOT factor. Reference40 reveals that most of the studies use the AHP method for prioritizing the SWOT factors and determining their weights, and recent studies employ the fuzzy AHP method combined with SWOT analysis and other MCDM method, such as TOPSIS, MABAC, DEMATEL, VIKOR and MARCOS. The use of AHP method for calculating the weights of SWOT factors and the need for a selection method such as MARCOS——an integrated SWOT-based fuzzy AHP-MARCOS method illustrates and their advantages are introduced next.
The integrated SWOT-fuzzy AHP-MARCOS method
Various MCDM methods developed for decision-making processes in the literature have been utilized to solve different problems concerning the decision-making in various areas. Moreover, MCDM methods are also widely used in the studies focusing on power system security assessment.
The AHP method
AHP is a popular MCDM technology in comprehensive evaluation research proposed by American operations research scientists in 1970s24. It is one of the most suitable methods for natural resource planning and environmental assessment. This method requires less quantitative data and information, and is simple and practical. The SWOT analysis method needs to be quantified by incorporating the SWOT model into a hierarchical structure through AHP method, and therefore, it is completely reasonable to use AHP method in this study.
The MARCOS method
MARCOS is one of the novel MCDM methods proposed by Stevi´c et al., which is designed to evaluate alternatives concerning multiple decision factors based on ideal and anti-ideal solutions and provides the determination of utility degrees for both of these solutions. Recently, References48 utilized the MARCOS method, and integrated it with the AHP method. Owing to its flexibility about the analysis of the expert preferences without considering the type of scale, it maintains the stability even if the range of standards and alternatives is wide. They validated the advantages of MARCOS methodology compared to traditional multi-criteria techniques including: Multi-Attributive Border Approximation area Comparison (MABAC)26, Additive Ratio Assessment (ARAS)27, Weighted Aggregated Sum Product Assessment (WASPAS)28 and TOPSIS29. MARCOS has been successfully applied in different areas by considering the above-mentioned examples from the literature. However, the use of MARCOS method for the strategy selection emphasizes the contributions and originality of this study. Compared to other selection methods such as TOPSIS, MABAC, COPRAS and VIKOR, the proposed combined method generates quite consistent results. Moreover, it provides a compromise solution concerning ideal and anti-ideal solutions, thereby ensuring a satisfactory performance in a fuzzy environment.
The integrated methodology
In the proposed method, AHP is deployed to obtain the criteria weights with SWOT, and MARCOS is utilized to evaluate the alternatives and select the best alternative to benefit from their strengths. The general framework and the flow of proposed integrated methodology are presented in Fig. 2.
Proposed methodology
This section elaborates the computational steps of the integrated SWOT-fuzzy AHP-MARCOS methodology39.
Step 1: Construct the SWOT matrix and factors determined by the experts.
Step 2: Construct a hierarchical structure concerning the goal and SWOT factors.
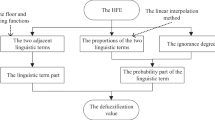
Step 3: Obtain the judgments of the experts: determine the priorities of the criteria using the linguistic terms given in Table 1.
A Fuzzy comparison matrix \({\tilde{\mathbf{A}}}\) is constructed at this step using the TFN as follows:
where \(\tilde{a}_{ij} = 1\), if i = j and \(\tilde{a}_{ij} = \tilde{1},{\kern 1pt} {\kern 1pt} \tilde{3},{\kern 1pt} {\kern 1pt} {\kern 1pt} \tilde{5},{\kern 1pt} {\kern 1pt} {\kern 1pt} \tilde{7},{\kern 1pt} {\kern 1pt} {\kern 1pt} \tilde{9}\) or \(\tilde{a}_{ij} = \tilde{1}^{ - 1} ,{\kern 1pt} {\kern 1pt} \tilde{3}^{ - 1} ,{\kern 1pt} {\kern 1pt} {\kern 1pt} \tilde{5}^{ - 1} ,{\kern 1pt} {\kern 1pt} {\kern 1pt} \tilde{7}^{ - 1} ,{\kern 1pt} {\kern 1pt} {\kern 1pt} \tilde{9}^{ - 1}\) where i ≠ j.
After constructing the fuzzy comparison matrix, AHP method and a MATLAB program are used to calculate the weights of fuzzy AHP.
Step 4: Get the judgments of the experts to evaluate the alternatives using Table 2, to obtain the group decision matrix \({\tilde{\mathbf{X}}}\), where \({\tilde{\mathbf{A}}}(AI)\) and \({\tilde{\mathbf{A}}}(AAI)\) are the ideal and anti-ideal solutions, respectively.
Step 5: Normalize the \({\tilde{\mathbf{X}}}\) to obtain \({\tilde{\mathbf{N}}} = \left[ {\tilde{n}_{ij} } \right]_{m \times n}\) as follows:
Step 6: Obtain the weighted fuzzy matrix \({\tilde{\mathbf{V}}}\) where weight coefficients of the criterion \(\tilde{\omega }_{j} = \left( {\omega_{j}^{l} ,\omega_{j}^{m} ,\omega_{j}^{u} } \right)\) are calculated using fuzzy-AHP method:
Step 7: Calculate the utility degree \({\tilde{\mathbf{K}}}_{i}\):
where \(\tilde{S}_{i} = (s_{i}^{l} ,s_{i}^{m} ,s_{i}^{u} )\) indicates the addition of elements of \({\tilde{\mathbf{V}}}\):
Step 8: Determine the utility functions for ideal \(f(\tilde{K}_{i}^{ + } )\) and anti-ideal \(f(\tilde{K}_{i}^{ - } )\) solutions as follows:
Step 9: Calculate the utility functions \(f\left( {K_{i} } \right)\) to determine the rank of the alternatives:
Application of the proposed methodology
This section explains the HM power grid and its effect on the power system security. Following that, the conducted case study is illustrated.
Introduction of HM power grid
In this section, the power system security is evaluated considering the actual specifications of HM power grid in China, which is a mainland city with a wealth of new energy resources. The HM power grid located in the hub of the “silk road” the ancient times. The unique natural environment makes the HM power grid extremely rich in wind and solar energy resources. In addition, it has a vast area and relatively flat terrain, where large scale wind farms and photovoltaic farms are distributed, and the distribution scale is gradually expanding. Moreover, HM is the first cross-regional UHV transmission channel to absorb wind power and other new energy resources in Northwest China. Also, it facilitates the first new energy and thermal power bundling through UHVDC power transmission project in China49.
According to the 13th five-year plan of HM Region, it was expected that the installed capacity of wind power would reach 12,100 MW and that of photovoltaic power would reach 9000 MW by 2020, of which the growth rate from 2012 to 2019 would increase year by year. Figure 3 shows the growth rate curve of wind and photovoltaic power installed capacity at HM power grid. The wind power scale and photovoltaic installed capacity of HM region continued to grow rapidly from 2012 to 2019, where the growth rate of wind power installed capacity was greater than that of the photovoltaic power. It can be seen that HM region, as the main gathering place of wind energy, is the key to new energy power generation in the whole China. As a hub connected with the mainland power grid, the energy security of HM region evidently affects the energy security of the whole China power system transmission.
SWOT factors
The SWOT factors are determined using the collected expert opinions, related studies and industry reports. These factors are listed in Fig. 4.
Case study
After gathering the SWOT factors, organizations usually use the AHP method to quantify the priority order of strategies and calculate the weights of the factors.
The SWOT matrix and its hierarchical structure constructed by 24 factors and 8 improvement strategies are shown in Fig. 4. A group of experts determine the priorities of SWOT dimensions and factors based on Table 1. The calculated weight values calculated and the results are given in Tables 3, 4, 5, 6, and 7. (C.R. ≤ 0.1).
Furthermore, Fig. 5 presents to show the distribution of the weights of SWOT dimensions and factors based on their global weights.
The ranked order of SWOT is obtained as S > O > T > W. Through the strengths of HM power grid, seizing more opportunities and daring to threats will effectively overcome the weaknesses and make the online education more successful. Here, the ranked order of the strength factors is obtained as S3 > S6 > S5 > S2 > S1 > S4. Firstly, vigorously develop the rich potential of new energy resources in HM power grid and develop the local new energy resources through advanced technology. Secondly, through the support of government policies and investment, reduce the cost of power production and benefit the public. Furthermore, the ranked order of the weakness factors is obtained as W3 > W1 > W6 > W2 > W4 > W5. Due to long service time of power grid equipment, coupled with the strong uncertainty of random fluctuation of new energy itself and the impact of quarterly changes on new energy, the system is prone to collapse and various faults, thus affecting the normal operation and power generation of the power system, which corresponds to an inevitable weakness of the HM power grid. Progressively, the ranked order of the opportunity factors is obtained as O2 > O1 > O6 > O4 > O3 > O5. By expanding the government policies, financial support and bidding opportunities, we will enable economic and technical support for the development of new energy, vigorously develop the undeveloped new energy, reduce the power production cost of new energy, and bring the economic and social benefits to the society. Lastly, the ranked order of the threat factors is extracted as T1 > T2 > T5 > T3 > T6 > T4. For North China power grids, especially the HM power grid, large-scale long-distance transmission, “West to East power transmission”, is not only a great project, but also a great technical challenge. The strong randomness of load and the lack of appropriate power transmission planning leads to power transmission security problems. At the same time, such power transmission requires strong support from economy, technology and government policies.
The alternative strategies shown in Fig. 4 are evaluated using the MARCOS method over the SWOT factors by the experts using linguistic terms given in Table 2, to obtain a group decision matrix given in Table 8.
The extended initial fuzzy matrix \({\tilde{\mathbf{X}}}\) of MARCOS method is first created, including fuzzy anti-ideal \({\tilde{\mathbf{A}}}\left( {AAI} \right)\) and ideal \({\tilde{\mathbf{A}}}\left( {AI} \right)\) solutions. Extended initial fuzzy matrix is then normalized based on the benefit criteria of the proposed SWOT model in step 7. Here, all SWOT factors are benefit criteria. The weighted fuzzy matrix \({\tilde{\mathbf{V}}}\) created using global weights of the SWOT factors is given in Fig. 6. The utility degree \({\tilde{\mathbf{K}}}_{j}\), \({\tilde{\mathbf{A}}}_{j}\) values, utility functions for the ideal \(f(K_{j}^{ + } )\) and anti-ideal \(f(K_{j}^{ - } )\) solutions, and \(\tilde{T}_{j}\) values of alternative strategies are calculated and provided in Table 9. In addition, the defuzzification of \({\tilde{\mathbf{K}}}_{j}^{ - }\), \({\tilde{\mathbf{K}}}_{j}^{ + }\), \(f(K_{j}^{ + } )\), \(f(K_{j}^{ - } )\) values and utility functions \(f(K_{j} )\) of alternative strategies are obtained and the results are given in Table 10. The ranked order of the strategies is obtained as A2 > A6 > A5 > A1 > A8 > A7 > A4 > A3.
The results of this study essentially demonstrated that the most important dimensions that the State Grid should focus on are the strengths and opportunities concerning the HM power grid, where the internal and external factors have almost the same importance. Therefore, we strive to maximize our strengths, weaken our weaknesses, dare to threats and seize the opportunities. Moreover, the ranked order of the strategies reveals that the three most important digital transformation strategies are A2, A6 and A5. These three strategies are defined as “improving the technical establishment to encourage efficient and cheap electricity production”, “strive to build local permanent load and reduce the risk of long-distance and high-capacity transmission”, and “taking advantage of government incentives and investment to modify the irrational energy policies and energy planning”, respectively.
Comparative analysis
This section provides the comparative analysis that is conducted to validate the proposed methodology. The comparison is made against the VIKOR and TOPSIS methods. Computational steps of VIKOR20 and TOPSIS32 are performed, and the corresponding results of VIKOR and TOPSIS are given in Tables 11 and 12, respectively. Besides, the utility function distribution in a three-dimensional space is shown in Fig. 6.
Furthermore, the ranked orders of the alternatives obtained from fuzzy VIKOR, TOPSIS, and MARCOS methods are compared in Fig. 7, which are found as VIKOR—— A6 > A5 > A2 > A8 > A1 > A4 > A7 > A3; TOPSIS—— A2 > A6 > A5 > A1 > A8 > A7 > A4 > A3. According to the results, the solutions from these three compared methods for the evaluation of operation security strategies produce similar results. There are both distance-based method, which are similar in their approach. However, the MARCOS method is a relatively new and practical method compared to the other two methods. Compared to the outcomes of other prominent MCDM methods, the integrated AHP-MARCOS methodology provides highly consistent final values, validating the potential of proposed method in solving similar MCDM problems.
Sensitivity analysis
The sensitivity analysis can confirm the final prioritization of changes in priority weights of criteria. Table 13 shows the SWOT dimensions have ± 10%, ± 20%, and ± 30% ranking of global weights change. Following that, through the fuzzy MARCOS method, update the utility function F(K) values based on these weights. Next, ranked orders of the strategies alternatives are obtained based on the updated utility function values as shown in Fig. 8, which demonstrates the robustness and credibility of the MARCOS method. Furthermore, “improving the technical establishment to encourage efficient and cheap electricity production” is the most appropriate strategy in most cases.
Conclusion and perspective
New energy offers enormous potential to generate electricity in Northwest China regions, which could potentially be enough to meet overall China’s energy demands. The vigorous development and utilization of new energy at HM power grid can not only reduce the dependence on traditional energy such as coal, oil and natural gas, but also improve the problem of energy shortage, create new employment opportunities, protect the natural environment, and make the rural regions with significant new energy potential wealthier. However, with the integration of new energy and microclimate-sensitive loads, power systems are becoming increasingly complex and vulnerable to faults. As the main power generation area of Northwest China power grid, the safe and economic operation of HM power grid is becoming a more important and complex problem in the field of power system security operation. The strategic evaluation of this paper shows that the proposed method can be effectively used to determine the best strategies with highest priority, and illustrates the importance of establishing the right strategy to exploit a significant developing opportunity and highlight the strength of rapidly growing new energy power grid.
The major contributions of this paper can be summarized as follows:
-
This article is the first study focusing on SWOT-AHP-MARCOS method for new energy power system operation security.
-
This study contributes to the HM power grid security operation prospective strategy selection problem by developing a new evaluation model. The effectiveness of the presented approach is validated via comparative analysis and sensitivity analysis. The results as follow:
It is concluded that the three most important strategies are A2, A6 and A5. These are “improving the technical establishment to encourage efficient and cheap electricity production”, “strive to build local permanent load and reduce the risk of long-distance and high-capacity transmission”, and “taking advantage of government incentives and investment to modify the irrational energy policies and energy planning”, respectively. Northwest region is a poor area in China with underdeveloped economy. Although it has a great potential for new energy, this energy cannot be consumed locally. Therefore, the government advocates the policy of “power transmission from the west to the East” to invest in the energy field in the northwest region. First, it aims to solve the problem of energy shortage in the eastern developed regions. Second, it aims to promote the economic development of the northwest region through the advantages of high new energy storage, so as to achieve the “Chinese dream” of energy coexistence and common prosperity. In this regard, the results of the presented SWOT analysis showed that despite various challenges, HM power grid could still provide numerous benefits to the country over conventional non-new energy resources in terms of production cost, environmental aspects with additional prospects of endless new energy potential, which will greatly promote the economic development of Northwest China.
In the future, it is worthwhile to further study the following aspects:
-
The MCDM methods such as HFL-AHP, ANP, CM, CRITIC, DEA, ELECTRE, MABAC, TOPSIS, and VIKOR can be applied to the similar-type of decision-problem.
-
Based on the construction of SWOT index system, the method in this paper can be used to evaluate the power system development prospect among different regions in the world.
However, one of the limitations of this study is the identification of the items within the SWOT factors. During the process, the researchers’ subjectivity may have affected the results. We believe that if the items were derived directly through interviews with experts and the top four items among them were selected, we could secure more objective results.
Data availablity
The datasets used and/or analysed during the current study available from the corresponding author on reasonable request.
References
Jhonatan, S. et al. Optimal power flow with security operation region. Int. J. Electr. Power Energy Syst. 124, 106272 (2021).
Astik, D., Vivek, P. & Praghnesh, B. Multi-class support vector machines for static security assessment of power system. Ain Shams Eng. J. 11(1), 57–65 (2020).
Liu, C. et al. The strategic power infrastructure defense system. IEEE Control Syst. Mag. 13(8), 40–52 (2003).
Massoud A. Conceptual design of a strategic power infrastructure defense (SPID) system. EPRI/DoD Complex Interactive Networks/Systems Initiative. First Annual Report: TP-114661, May 2000.
Anderson, G. et al. Causes of the 2003 major grid blackouts in North America and Europe, and recommended means to improve system dynamic performance. IEEE Trans. Power Syst. 20(4), 1922–1928 (2005).
Li C, Sun Y, Chen X. Analysis of the blackout in Europe. in Power Engineering Conference 2007; 939—944.
Liu, R., Gregor, V. & Ma, J. A new dynamic security assessment framework based on semi-supervised learning and data editing. Electric Power Syst. Res. 172, 221–229 (2019).
Maíra, R. M. et al. Network partitioning in coherent areas of static voltage stability applied to security region enhancement. Int. J. Electr. Power Energy Syst. 117, 105623 (2020).
Zhou, A. et al. A novel data-driven approach for transient stability prediction of power systems considering the operational variability. Int. J. Electr. Power Energy Syst. 107, 379–394 (2019).
Yue, Z. et al. Probabilistic transient stability assessment of power system considering wind power uncertainties and correlations. Int. J. Electr. Power Energy Syst. 117, 105649 (2020).
Huang, T. et al. A deep spatial-temporal data-driven approach considering microclimates for power system security assessment. Appl. Energy 237, 36–48 (2019).
Eshraghi A, Salehi G, Heibati S, et al. Developing operation of combined cooling, heat, and power system based on energy hub in a micro-energy grid: The application of energy storages. Energy Environ., 2019, 30.
Eshraghi, A. et al. An enhanced operation model for energy storage system of a typical combined cool, heat and power based on demand response program: The application of mixed integer linear programming. Build. Serv. Eng. Res. Technol. 40(1), 47–74 (2019).
Eshraghi, A. et al. An assessment of the effect of different energy storage technologies on solar power generators for different power sale scenarios: The case of Iran. Sustain. Energy Technol. Assessments 34, 62–67 (2019).
Hannes, H., Le, A. & Robert, E. Impact of static and dynamic load models on security margin estimation methods. Electric Power Syst. Res. 202, 107581 (2022).
Othon, F., João, A. & Wesley, P. Steady-state security assessment in distribution systems with high penetration of distributed energy resources. Electric Power Syst. Res. 201, 107500 (2021).
Chen, B., Lin, T., Chen, R., Li, Y. & Xu, X. Research on active power steady-state security region considering TCSC. J. Eng. 2017(13), 2378–2383 (2017).
Federica, B. et al. A causality based feature selection approach for data-driven dynamic security assessment. Electric Power Syst. Res. 201, 107537 (2021).
Jochen, L. & Goran, S. A machine-learning based probabilistic perspective on dynamic security assessment. Int. J. Electr. Power Energy Syst. 128, 106571 (2021).
Ren, J. et al. Online multi-fault power system dynamic security assessment driven by hybrid information of anticipated faults and pre-fault power flow. Int. J. Electr. Power Energy Syst. 136, 107651 (2022).
Liu, Y., Shi, X. & Xu, Y. A hybrid data-driven method for fast approximation of practical dynamic security region boundary of power systems. Int. J. Electr. Power Energy Syst. 117, 105658 (2020).
Saniye, M. et al. Dynamic security and stability region under different renewable energy permeability in IENGS system. IEEE Access 9, 19800–19817 (2021).
Wu, J. et al. Comprehensive evaluation of voltage stability based on EW-AHP and Fuzzy-TOPSIS. Heliyon 5(10), e02410 (2019).
Qin, G. et al. Comprehensive evaluation of regional energy internet using a fuzzy analytic hierarchy process based on cloud model: A case in China. Energy 228, 120569 (2021).
Li, J. et al. Analysis of China’s energy security evaluation system: Based on the energy security data from 30 provinces from 2010 to 2016. Energy 198, 117346 (2020).
Zhong, C. et al. Fuzzy comprehensive evaluation with AHP and entropy methods and health risk assessment of groundwater in Yinchuan Basin, northwest China. Environ. Res. 204(1), 111956 (2022).
Zhao, D. et al. Comprehensive evaluation of national electric power development based on cloud model and entropy method and TOPSIS: A case study in 11 countries. J. Clean. Prod. 277, 123190 (2020).
Wen, P. et al. Comprehensive evaluation method of the poultry house indoor environment based on grey relation analysis and analytic hierarchy process. Poul. Sci. 101(2), 101587 (2021).
Meng, W. & Niu, D. Research on project post-evaluation of wind power based on improved ANP and fuzzy comprehensive evaluation model of trapezoid subordinate function improved by interval number. Renewab. Energy 132, 255–265 (2019).
Rao, S. A hybrid MCDM model based on DEMATEL and ANP for improving the measurement of corporate sustainability indicators: A study of Taiwan High Speed Rail. Res. Transp. Bus. Manag. 41, 100657 (2021).
Mohammad, K., Hedieh, S. & Shakib, Z. Risk identification and assessment with the fuzzy DEMATEL-ANP method in oil and gas projects under uncertainty. Procedia Comput. Sci. 181, 277–284 (2021).
Tian, G. et al. Selection of take-back pattern of vehicle reverse logistics in China via Grey-DEMATEL and Fuzzy-VIKOR combined method. J. Clean. Prod. 220, 1088–1100 (2019).
Li, H. et al. A novel hybrid MCDM model for machine tool selection using fuzzy DEMATEL, entropy weighting and later defuzzification VIKOR. Appl. Soft Comput. 91, 106207 (2020).
Wang, Z. et al. Distributed energy system for sustainability transition: A comprehensive assessment under uncertainties based on interval multi-criteria decision making method by coupling interval DEMATEL and interval VIKOR. Energy 169, 750–761 (2019).
Andrii, S. & Wojciech, S. A comparative case study of the VIKOR and TOPSIS rankings similarity. Procedia Comput. Sci. 176, 3730–3740 (2020).
Sari, F. Forest fire susceptibility mapping via multi-criteria decision analysis techniques for Mugla, Turkey: A comparative analysis of VIKOR and TOPSIS. For. Ecol. Manage. 480, 118644 (2021).
Piwowarski, M. et al. TOPSIS and VIKOR methods in study of sustainable development in the EU countries. Procedia Comput. Sci. 126, 1683–1692 (2018).
Biswajit B, Pravat K, Nairita S, et al. Susceptibility of deforestation hotspots in Terai-Dooars belt of Himalayan Foothills: A comparative analysis of VIKOR and TOPSIS models. J. King Saud Univ. Comput. Inf. Sci. 2021.
Gülçin, B., Celal, A. & Orhan, F. An integrated SWOT based fuzzy AHP and fuzzy MARCOS methodology for digital transformation strategy analysis in airline industry. J. Air Transp. Manag. 97, 102142 (2021).
Gülçin, B., Esin, M. & Elif, K. Health tourism strategy selection via SWOT analysis and integrated hesitant fuzzy linguistic AHP-MABAC approach. Socioecon. Plann. Sci. 74, 100929 (2021).
Lee, J. et al. SWOT-AHP analysis of the Korean satellite and space industry: Strategy recommendations for development. Technol. Forecast. Soc. Chang. 164, 120515 (2021).
Nima, P. et al. Resolution of Internal conflicts for conservation of the Hour Al-Azim wetland using AHP-SWOT and game theory approach. Land Use Policy 107, 105495 (2021).
Seyyed, M., Mohammad, M. & Chefi, T. Implementing sustainable ecotourism in Lafour region, Iran: Applying a clustering method based on SWOT analysis. J. Clean. Prod. 329, 129716 (2021).
Moslem, S. & Mohammad, S. SWOT-FAHP-TOWS analysis for adaptation strategies development among small-scale farmers in drought conditions. Int. J. Disaster Risk Reduct. 67, 102695 (2022).
Imran, Q. A comparison of renewable and sustainable energy sector of the South Asian countries: An application of SWOT methodology. Renewable Energy 181, 417–425 (2022).
Wang, Y., Xu, L. & Yasir, A. Strategic renewable energy resources selection for Pakistan: Based on SWOT-Fuzzy AHP approach. Sustain. Cities Soc. 52, 101861 (2020).
Asir, A. et al. Evaluating the strategies for sustainable energy planning in Pakistan: An integrated SWOT-AHP and Fuzzy-TOPSIS approach. J. Clean. Prod. 236, 117655 (2019).
Stević, Ž & Brković, N. A novel integrated FUCOM-MARCOS model for evaluation of human resources in a transport company. Logistics 4(1), 4 (2020).
Maihemuti, S. et al. Voltage security operation region calculation based on improved particle swarm optimization and recursive least square hybrid algorithm. J. Mod. Power Syst. Clean Energy 9(1), 138–147 (2021).
Acknowledgements
The authors would like to express their sincere gratitude to the experts on their unlimited support in the validation of the framework and suggestions as well as providing some data. The authors want to thank the editor and anonymous reviewers for their valuable comments and suggestions to improve the version of this article. This work was supported in part by the Natural Science Foundation of Xinjiang Autonomous Region under grant (2020D01C068), in part by the National Natural Science Foundation of China under grant (51667020), in part by the Key R & D Plan of the Autonomous Region under grant (2020b02001), in the part by Innovation Team of the Ministry of Education under grant (IRT_16R63).
Author information
Authors and Affiliations
Contributions
S.M. is mainly responsible for the innovation and writing part of the paper; W.W. grasps the language grammar part of the thesis; H.W. and J.W. are responsible for figures drawing and format adjustment. All authors reviewed the manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Maihemuti, S., Wang, W., Wu, J. et al. New energy power system operation security evaluation based on the SWOT analysis. Sci Rep 12, 12680 (2022). https://doi.org/10.1038/s41598-022-16444-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-022-16444-4
- Springer Nature Limited