Abstract
We show how adaptive protocols of quantum and private communication through bosonic Gaussian channels can be simplifed into much easier block versions that involve resource states with finite energy. This is achieved by combining an adaptive-to-block reduction technique devised earlier, based on teleportation stretching and relative entropy of entanglement, with a recent finite-resource simulation of Gaussian channels. In this way, we derive weak converse upper bounds for the secret-key capacity of phase-insensitive Gaussian channels which approximate the optimal limit for infinite energy. Our results apply to both point-to-point and repeater-assisted private communications.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Introduction
Establishing the ultimate limits of quantum and private communications is important1,2, not only to explore the boundary of quantum mechanics but also to provide benchmarks for testing the practical performance of experimental and technological implementations. This problem is important for quantum systems of any dimension3,4 and, in particular, for infinite-dimensional ones, also known as continuous-variable (CV) systems5,6,7,8. In quantum information and quantum optics, the most important CV systems are the bosonic modes of the electromagnetic field6, which are typically used at the optical or telecom wavelengths. In any protocol of quantum communication, such modes are subject to loss and noise, and the most typical and basic model for such kind of decoherence is the single-mode Gaussian channel.
It is known that protocols of private communication and quantum key distribution (QKD) are limited in both rate and distance due to decoherence, no matter if the communication line is a free-space link or a fiber connection. This limitation is perhaps best simplified by the rate-loss scaling of ideal single-photon BB84 protocol9 whose optimal rate scales as η/2 secret bits per channel use, where η is the transmissivity of the channel. Recently, this fundamental rate-loss limit has been fully characterized. By optimizing over the most general key-generation protocols, Pirandola-Laurenza-Ottaviani-Banchi10 have established the secret-key capacity of the lossy channel to be \(K(\eta )=-\,{\mathrm{log}}_{{\rm{2}}}\mathrm{(1}-\eta )\), which is about 1.44η secret bits per channel use at long distances (\(\eta \simeq 0\)). This result sets a general benchmark for quantum repeaters11,12,13,14,15,16,17,18,19,20,21,22,23,24 and completes a long-standing investigation started back in 200925,26, when the best known lower bound was discovered.
The main technique that led to establishing the previous capacity is based on a suitable combination of two ingredients, the relative entropy of entanglement (REE)27,28,29 suitably extended from states to channels (using results from refs30,31,32), and teleportation stretching, which reduces any adaptive (feedback-assisted) quantum protocol over an arbitrary channel into a much simpler block version. This latter technique is a full extension and generalization of previous approaches33,34,35 that only worked for specific classes of channels and were designed to reduce quantum error correcting code protocols into entanglement distillation. Without doubts, the generalization to an arbitrary task over an arbitrary quantum channel has been one of the key insights of ref.10, and this has been widely exploited in recent literature, with a number of follow-up papers in the area of quantum Shannon theory4, e.g., on strong converse rates, broadcast capacities, etc. See ref.36 for a recent review on these topics and refs36,37 for rigorous proofs of some related claims.
The core of teleportation stretching is the idea of channel simulation, where an arbitrary quantum channel is replaced by local operations and classical communication (LOCC) applied to the input and a suitable resource state10. This powerful idea is rooted in the protocol of teleportation38,39 and first proposed in ref.33, despite originally limited to the simulation of Pauli channels40 (see also ref.41). Later, this core idea was extended to generalized teleportation protocols35,42 and CV teleportation43 in refs34,44. The final and more general form involves a simulation via arbitrary LOCCs, as formulated in ref.10. In particular, the simulation of bosonic channels is typically asymptotic, which means that they need a suitable limit over sequences of resource states, which comes from the fact that the Choi matrices of such channels are asymptotic states10. Most importantly, such a simulation needs a careful control of the simulation error as first considered in ref.10, otherwise technical divergences may appear in the results. This crucial aspect is discussed in detail in ref.36, which also provides a direct comparison of the various simulation techniques appeared in the literature.
Here we consider a different type of simulation for bosonic Gaussian channels, which is based on finite-energy two-mode Gaussian states as recently introduced in ref.45. We use this particular simulation at the core of teleportation stretching in order to simplify adaptive protocols. This not only represents an interesting design (with potential applications beyond this work) but also allows us to derive upper bounds for the secret-key capacities of phase-insensitive Gaussian channels which approximate well the asymptotic results of ref.10.
Results
Preliminaries on the simulation of bosonic channels
As discussed in ref.10 an arbitrary quantum channel \( {\mathcal E} \) can be simulated by a trace-preserving LOCC \({\mathscr{T}}\) and a suitable resource state σ, i.e.
A channel is called σ-stretchable if it has σ as a resource state via some LOCC simulation as in Eq. (1). An important case is when the channel is Choi-stretchable, which means that the resource state can be chosen to be its Choi matrix \(\sigma ={\rho }_{ {\mathcal E} }:\,=I\otimes {\mathcal E} ({\rm{\Phi }})\), with Φ being a maximally entangled state. For a bosonic channel, the maximally entangled state is an Einstein-Podolsky-Rosen (EPR) state with infinite energy, so that the Choi matrix of a bosonic channel is energy-unbounded. For this reason one has to work with a sequence of two-mode squeezed vacuum states5 Φμ with variance \(\mu =\bar{n}+\mathrm{1/2}\), where \(\bar{n}\) is the average number of thermal photons in each mode. By definition, the EPR state is defined as \({\rm{\Phi }}:=\mathop{\mathrm{lim}}\limits_{\mu }\,{{\rm{\Phi }}}^{\mu }\) and the Choi matrix of a bosonic channel \( {\mathcal E} \) is defined by
This means that the simulation needs to be asymptotic, i.e., of the type
(More generally, one also needs to consider sequences of LOCCs \({{\mathscr{T}}}^{\mu }\), so that the asymptotic simulation reads \( {\mathcal E} (\rho )={\mathrm{lim}}_{\mu }{{\mathscr{T}}}^{\mu }(\rho \otimes {\rho }_{ {\mathcal E} }^{\mu })\). For simplicity we omit this technicality, referring the reader to ref.10 for more details.)
In ref.10, we identified a simple sufficient condition for a quantum channel to be Choi-stretchable, even asymptotically as in Eq. (3): teleportation covariance. In the bosonic case, a channel \( {\mathcal E} \) is teleportation-covariant if, for any random displacement D (as induced by CV teleportation)39,43, we may write
for some unitary V. It is clear that bosonic Gaussian channels are teleportation covariant and, therefore, Choi-stretchable, with asymptotic simulation as in Eq. (3).
Simulation of Gaussian channels with finite-energy resource states
Recently, ref.45 proposed a variant of Gaussian channel simulation10, where single-mode phase-insensitive Gaussian channels are simulated by applying CV teleportation to a particular class of finite-energy Gaussian states as the resource. Consider a single-mode Gaussian state with mean value \(\bar{x}\) and covariance matrix (CM) V5. The action of a single-mode Gaussian channel can be expressed in terms of the statistical moments as
where T and \({\bf{N}}={{\bf{N}}}^{T}\) are 2 × 2 real matrices satisfying suitable conditions5. In particular, the channel is called phase-insensitive if these two matrices take the specific diagonal forms
where \(\eta \in {\mathbb{R}}\) is a transmissivity parameter, while \(\nu \ge 0\) represents added noise.
According to ref.45, a phase-insensitive Gaussian channel \({ {\mathcal E} }_{\eta ,\nu }\) can be simulated as follows
where \({{\mathscr{T}}}_{\eta }\) is the Braunstein-Kimble protocol with gain \(\sqrt{\eta }\) 43,46, and σv is a zero-mean two-mode Gaussian state with CM
where45
and the entanglement parameter r ≥ 0 is connected to the channel parameter via the relation
Note that, with respect to the fomulas of ref.45, we have an extra 1/2 factor in Eqs (8) and (11). This is due to the different notation we adopt here. We set the quadrature variance of the vacuum state to be 1/2, while it was equal to 1 in ref.45. Also note that, in the simulation of Eq. (7), one uses a Braunstein-Kimble protocol with an ideal CV Bell detection. The latter is an asymptotic measurement defined in the limit of infinite squeezing, i.e., infinite energy. For this reason, the finite-energy aspect of the simulation in Eq. (7) only refers to the resource state.
Finite-resource teleportation stretching of an adaptive protocol
Here we plug the previous finite-resource simulation into the tool of teleportation stretching. We start by providing some necessary definitions on adaptive protocols and secret-key capacity. Then, we review a general upper bound (weak converse) based on the REE. Finally, following the recipe of refs10,47. we show how to use the finite-resource simulation to simplify an adaptive protocol and reduce the REE bound to a single-letter quantity.
Adaptive protocols and secret-key capacity
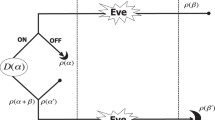
The most general protocol for key generation is based on adaptive LOCCs, i.e., local operations assisted by unlimited and two-way classical communication. Each transmission through the quantum channel is interleaved by two of such LOCCs. The general formalism can be found in ref.10 and goes as follows. Assume that two remote users, Alice and Bob, have two local registers of quantum systems (modes), a and b, which are in some fundamental state \({\rho }_{{\bf{a}}}\otimes {\rho }_{{\bf{b}}}\). The two parties applies an adaptive LOCC Λ0 before the first transmission.
In the first use of the channel, Alice picks a mode a1 from her register a and sends it through the channel \( {\mathcal E} \). Bob gets the output mode b1 which is included in his local register b. The parties apply another adaptive LOCC Λ1. Then, there is the second transmission and so on. After n uses, we have a sequence of LOCCs \(\{{{\rm{\Lambda }}}_{0},{{\rm{\Lambda }}}_{1},\,\ldots ,\,{{\rm{\Lambda }}}_{n}\}\) characterizing the protocol \( {\mathcal L} \) and an output state \({\rho }_{{\bf{a}}{\bf{b}}}^{n}\) which is ε-close to a target private state48 with nRn bits. Taking the limit of large n and optimizing over the protocols, we define the secret-key capacity of the channel
General upper bound
According to Theorem 1 (weak converse) in ref.10, a general upper bound for \(K( {\mathcal E} )\) is given in terms of the REE of the output state \({\rho }_{{\bf{a}}{\bf{b}}}^{n}\)
Recall that the REE of a state ρ is defined as \({E}_{R}(\rho )={{\rm{\inf }}}_{{\sigma }_{{\rm{sep}}}}S(\rho ||{\sigma }_{{\rm{sep}}})\), where σsep is a separable state and the relative entropy is defined by \(S(\rho ||{\sigma }_{{\rm{sep}}}):={\rm{Tr}}[\rho ({\mathrm{log}}_{{\rm{2}}}\,\rho -{\mathrm{log}}_{2}{\sigma }_{{\rm{sep}}})]\). These definitions can be easily adapted for asymptotic states of bosonic systems.
Note that the first and simplest proof of Eq. (13) can be found in ref.49 (the second arxiv version of ref.10). To avoid potential misunderstandings or misinterpretations of this proof, we report here the main points. For any protocol whose output \({\rho }_{{\bf{a}}{\bf{b}}}^{n}\) is ε-close (in trace norm) to target private state with rate Rn and dimension d, we may write
where H2 is the binary Shannon entropy. For distribution through a discrete variable (DV) channel, whose output is a DV state, we may write
for some constant α [see also Eq. (21) of ref.49]. The exponential scaling in Eq. (15) comes from previous results in refs31,32. The latter showed that, for any adaptive protocol with rate Rn, there is another protocol with the same asymptotic rate while having an exponential scaling for d.
The extension to a CV channel is achieved by a standard argument of truncation of the output Hilbert space. After the last LOCC Λn, Alice and Bob apply a truncation LOCC \({{\mathbb{T}}}_{d}\) which maps the output state \({\rho }_{{\bf{a}}{\bf{b}}}^{n}\) into a truncated version \({\rho }_{{\bf{a}}{\bf{b}}}^{n,d}={{\mathbb{T}}}_{d}({\rho }_{{\bf{a}}{\bf{b}}}^{n})\) with total dimension d. The total protocol \({{\mathbb{T}}}_{d}\,\circ \, {\mathcal L} =\{{{\rm{\Lambda }}}_{0},\,{{\rm{\Lambda }}}_{1},\,\cdots ,\,{{\rm{\Lambda }}}_{n},\,{{\mathbb{T}}}_{d}\}\) generates an output that is ε-close to a DV private state with nRn,d bits. Therefore, we may directly re-write Eq. (14) as
Both the output and the target are DV states, so that we may again write Eq. (15). In fact, since the Hilbert space is finite-dimensional, the proof of refs31,32 automatically applies, i.e., the protocol can be stopped after n0 uses, and then repeated m times in an i.i.d. fashion, with n = n0m. Key distillation applied to the m DV output copies implies a number of bits of CCs which is linear in m which, in turn, leads to an exponential scaling of d in n.
Because \({{\mathbb{T}}}_{d}\) is a trace-preserving LOCC, we exploit the monotonicity of the REE \({E}_{R}({\rho }_{{\bf{a}}{\bf{b}}}^{n,d})\le {E}_{R}({\rho }_{{\bf{a}}{\bf{b}}}^{n})\) and rewrite Eq. (16) as
Taking the limit for large n and small ε (weak converse), this leads to
The crucial observation is that in the right-hand side of the latter expression, there is no longer dependence on the truncation d. Therefore, in the optimization of Rn,d over all protocols \({{\mathbb{T}}}_{d}\,\circ \, {\mathcal L} \) we can implicitly remove the truncation. Pedantically, we may write
Remark 1
Note that the truncation argument was explicitly used in ref.49 to extend the bound to CV channels. See discussion after Eq. (23) of ref.49. There a cut-off was introduced for the total CV Hilbert space at the output. Under this cutoff, the derivation for DV systems was repeated, finding an upper bound which does not depend on the truncated dimension (this was done by using the monotonicity of the REE exactly as here). The cutoff was then relaxed in the final expression as above. The published version10 includes other equivalent proofs but they have been just given for completeness.
Simplification via teleportation stretching
One of the key insights of ref.10 has been the simplification of the general bound in Eq. (13) to a single-letter quantity. For bosonic Gaussian channels, this was achieved by using teleportation stretching with asymptotic simulations, where a channel is reproduced by CV teleportation over a sequence of Choi-approximating resource states. Here we repeat the procedure but we adopt the finite-resource simulation of ref.45. Recall that, differently from previous approaches33,34,35, teleportation stretching does not reduce a protocol into entanglement distillation but maintains the task of the original protocol, so that adaptive key generation is reduced to block (non-adaptive) key generation. See ref.36 for comparisons and clarifications.
Assume that the adaptive protocol is performed over a phase-insensitive Gaussian channel \({ {\mathcal E} }_{\eta ,\nu }\), so that we may use the simulation in Eq. (7), where \({{\mathscr{T}}}_{\eta }\) is the Braunstein-Kimble protocol with gain \(\sqrt{\eta }\) and σν is a zero-mean two-mode Gaussian state, specified by Eqs (8–11). We may re-organize an adaptive protocol in such a way that each transmission through \({ {\mathcal E} }_{\eta ,\nu }\) is replaced by its resource state σν. At the same time, each teleportation-LOCC \({{\mathscr{T}}}_{\eta }\) is included in the adaptive LOCCs of the protocol, which are all collapsed into a single LOCC \({\bar{{\rm{\Lambda }}}}_{\eta }\) (trace-preserving after averaging over all measurements). In this way, we may decompose the output state \({\rho }_{{\bf{a}}{\bf{b}}}^{n}:\,={\rho }_{{\bf{a}}{\bf{b}}}({ {\mathcal E} }_{\eta ,\nu }^{\otimes n})\) as
The computation of \({E}_{R}({\rho }_{{\bf{a}}{\bf{b}}}^{n})\) can now be remarkably simplified. In fact, we may write
where: (1) we consider the fact that \({\bar{{\rm{\Lambda }}}}_{\eta }({\sigma }_{{\rm{sep}}})\) form a subset of specific separable states, and (2) we use the monotonicity of the relative entropy under the trace-preserving LOCC \({\bar{{\rm{\Lambda }}}}_{\eta }\). Therefore, by replacing in Eq. (13), we get rid of the optimization over the protocol (disappearing with \({\bar{{\rm{\Lambda }}}}_{\eta }\)) and we may write
where we use the fact that the regularized REE is less than or equal to the REE. Thus, we may write the following theorem:
Theorem 2
Consider a phase-insensitive bosonic Gaussian channel \({ {\mathcal E} }_{\eta ,\nu }\), which is stretchable into a two-mode Gaussian state σν as given in Eqs (8–11). Its secret-key capacity must satisfy the bound
Note that the new bound in Eq. (23) cannot beat the asymptotic bound established by ref.10 for bosonic channels, i.e.,
where \({\rho }_{{ {\mathcal E} }_{\eta ,\nu }}^{\mu }\) is a Choi-approximating sequence as in Eq. (2), and \({\sigma }_{{\rm{sep}}}^{\mu }\) is an arbitrary sequence of separable states converging in trace norm. This can be seen from a quite simple argument50. In fact, according to Eqs (2) and (7), we may write
where Δ is a trace-preserving LOCC. Therefore, \({E}_{R}({\rho }_{{ {\mathcal E} }_{\eta ,\nu }}^{\mu })\le {E}_{R}({\sigma }_{\nu })\) and this relation is inherited by the bounds above. Notwithstanding this no go for the finite-resource simulation, we show that its performance is good and reasonably approximates the infinite-energy bounds that are found via Eq. (24).
Finite-resource bounds for phase insensitive Gaussian channels
We now proceed by computing the REE in Eq. (23) for the class of single-mode phase-insensitive Gaussian channels. For this, we exploit the closed formula for the quantum relative entropy between Gaussian states which has been derived in ref.10 by using the Gibbs representation for Gaussian states51. Given two Gaussian states \({\rho }_{1}({u}_{1},\,{V}_{1})\) and \({\rho }_{2}({u}_{2},\,{V}_{2})\), with respective statistical moments ui and Vi, their relative entropy is
where we have defined
with \(\delta ={u}_{1}-{u}_{2}\) and \({G}_{2}=2i{\rm{\Omega }}\,{\coth }^{-1}\mathrm{(2}i{V}_{2}{\rm{\Omega }})\) 51, where the matrix Ω is the symplectic form.
The computation of the REE involves an optimization over the set of separable states. Following the recipe of ref.10 we may construct a good candidate directly starting from the CM in Eq. (8). This separable state has CM with the same diagonal blocks as in Eq. (8), but where the off-diagonal term is replaced as follows
By using this separable state \({\tilde{\sigma }}_{{\rm{sep}}}\) we may write the further upper bound
In the following, we compute this bound for the various types of phase-insensitive Gaussian channels.
Thermal-loss channel
This channel can be modelled as a beam splitter of transmissivity η where the input signals are combined with a thermal environment such that the quadratures transform according to \(\hat{{\bf{x}}}\to \sqrt{\eta }\hat{{\bf{x}}}+\sqrt{1-\eta }{\hat{{\bf{x}}}}_{th}\), where \({\hat{{\bf{x}}}}_{th}\) is in a thermal state with \(\bar{n}\) photons. In terms of the statistical moments, the action of the thermal-loss channel \({ {\mathcal E} }_{\eta ,\bar{n}}\) can be described by the matrices in Eq. (6) with parameter \(\nu =\mathrm{(1}-\eta )(\bar{n}+\mathrm{1/2)}\). This means that the squeezing parameter r of the resource state now reads
By combining this relation with the ones in Eq. (10) and computing the relative entropy, we find the finite-resource bound \({\rm{\Psi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) which is plotted in Fig. 1 and therein compared with the infinite-energy bound \({\rm{\Phi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) derived in ref.10. The latter is given by10
for \(\bar{n} < \eta \mathrm{/(1}-\eta )\) and zero otherwise, and we set \(h(x):\,=(x+\mathrm{1)}\,{\mathrm{log}}_{2}(x+\mathrm{1)}-x\,{\mathrm{log}}_{2}\,x\). It is clear that we have
but the two upper bounds are reasonably close.
Finite-resource bound \({\rm{\Psi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) on the secret-key capacity of the thermal loss channel (red upper curve) as a function of the transmissivity η, compared with the infinite-energy bound \({\rm{\Phi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) (blue lower curve) derived in ref.10. The curves are plotted for \(\bar{n}=1\) thermal photons.
Noisy amplifier channel
A noisy quantum amplifier is described by \(\hat{{\bf{x}}}\to \sqrt{\eta }\hat{{\bf{x}}}+\sqrt{\eta -1}{\hat{{\bf{x}}}}_{th}\), where η > 1 is the gain and \({\hat{{\bf{x}}}}_{th}\) is in a thermal state with \(\bar{n}\) photons. This channel \({ {\mathcal E} }_{\eta ,\bar{n}}\) is described by the matrices in Eq. (6) with parameter \(\nu =(\eta -\mathrm{1)(}\bar{n}+\mathrm{1/2)}\). By repeating the previous calculations, we find the finite-resource bound \({\rm{\Psi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) plotted in Fig. 2 and where it is compared with the infinite-energy bound10
for \(\bar{n} < {(\eta -\mathrm{1)}}^{-1}\) and zero otherwise.
Finite-resource bound \({\rm{\Psi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) on the secret-key capacity of the noisy amplifier channel (red upper curve) as a function of the gain η, compared with the optimal bound for infinite energy \({\rm{\Phi }}({ {\mathcal E} }_{\eta ,\bar{n}})\) (blue lower curve). The two curves are plotted for \(\bar{n}=1\) thermal photons.
Additive-noise Gaussian channel
Another important channel is represented by the additive-noise Gaussian channel, which is the simplest model of bosonic decoherence. In terms of the input-output transformations, the quadratures transforms according to \(\hat{{\bf{x}}}\to \hat{{\bf{x}}}+{(z,z)}^{T}\) where z is a classical Gaussian variable with zero mean and variance ξ ≥ 0. This channel \({ {\mathcal E} }_{\xi }\) is described by the matrices in Eq. (6) with η = 1 and ν = ξ. The finite-resource bound \({\rm{\Psi }}({ {\mathcal E} }_{\xi })\) on the secret key capacity is plotted in Fig. 3 and compared with the infinite-energy bound10
for ξ < 1, while zero otherwise.
Pure-loss channel
For the pure-loss channel, the upper bound derived in the limit of infinite energy10 coincides with the lower bound computed with the reverse coherent information25,26. This means that we are able to fully characterize the secret-key capacity for this specific bosonic channel. This is also known as the Pirandola-Laurenza-Ottaviani-Banchi (PLOB) bound10
and fully characterizes the fundamental rate-loss scaling of point-to-point quantum optical communications.
Consider now the finite-resource teleportation simulation of a pure-loss channel. It is easy to check that we cannot use the parametrization in Eq. (10). In fact, for a pure-loss channel, we have \(\nu =\mathrm{(1}-\eta \mathrm{)/2}\) so that Eq. (11) provides \({e}^{2r}=\mathrm{(1}+\eta \mathrm{)/(1}-\eta )\). Replacing the latter in Eq. (10), we easily see that we have divergences (e.g., the denominator of b becomes zero). For the pure loss channel, we therefore use a different simulation, where the resource state is a two-mode squeezed state with CM50
By exploiting this resource state, we derive the bound \({\rm{\Psi }}({ {\mathcal E} }_{\eta })\) shown in Fig. 4, where it is compared with the secret-key capacity K(η).
Extension to repeater-assisted private communication
Here we extend the previous treatment to repeater-assisted private communication. We consider the basic scenario where Alice a and Bob b are connected by a chain of N quantum repeaters \(\{{{\bf{r}}}_{1},\,\ldots ,\,{{\bf{r}}}_{N}\}\), so that there are a total of N + 1 quantum channels \(\{{ {\mathcal E} }_{i}\}\) between them. Assume that these are phase-insensitive Gaussian channels \({ {\mathcal E} }_{i}:\,={ {\mathcal E} }_{{\eta }_{i},{\nu }_{i}}\) with parameters \(({\eta }_{i},{\nu }_{i})\). The most general adaptive protocol for key distribution through the chain is described in ref.52 and goes as follows.
Alice, Bob and all the repeaters prepare their local registers \(\{{\bf{a}},{{\bf{r}}}_{1},\ldots ,{{\bf{r}}}_{N},{\bf{b}}\}\) into a global initial state ρ0 by means of a network LOCC Λ0, where each node in the chain applies LOs assisted by unlimited and two-way CCs with all the other nodes. In the first transmission, Alice picks a system \({a}_{1}\in {\bf{a}}\) and sends it to the first repeater; after another network LOCC Λ1, the first repeater communicates with the second repeater; then there is another network LOCC Λ2 and so on, until Bob is eventually reached, which terminates the first use of the chain.
After n uses of the chain, we have a sequence of network LOCCs \( {\mathcal L} \) defining the protocol and an output state \({\rho }_{{\bf{a}}{\bf{b}}}^{n}\) for Alice and Bob which approximates some target private state with nRn bits. By taking the limit for large n and optimizing over the protocols, we define the end-to-end or repeater-assisted secret-key capacity52
As shown in ref.52, we may extend the upper bound of Eq. (13). Then, we may use teleportation stretching and optimize over cuts of the chain, to simplify the bound to a single-letter quantity.
The network-reduction technique of ref.52 can be implemented by using the specific finite-resource simulation of Eq. (7), which leads to the following possible decompositions of the output state
where \({\bar{{\rm{\Lambda }}}}_{i}\) is a trace-preserving LOCC and \({\sigma }_{{\nu }_{i}}\) is the resource state associated with the ith Gaussian channel. By repeating the derivation of ref.52, this leads to
where Ψ is the upper bound coming from our choice of the separable state \({\tilde{\sigma }}_{i,{\rm{sep}}}\) in the REE. This upper bound needs to be compared with the one \({\rm{\Phi }}(\{{ {\mathcal E} }_{i}\})\) obtained in the limit of infinite energy52. As an example, consider an additive-noise Gaussian channel with noise variance ξ. Let us split the communication line by using N “equidistant” repeaters, in such a way that each link is an additive-noise Gaussian channel \({ {\mathcal E} }_{i}\) with the same variance \({\xi }_{i}=\xi /(N+\mathrm{1)}\). It is easy to check that this is the optimal configuration for the repeaters. From Eq. (39), we derive \({\rm{\Psi }}(\{{ {\mathcal E} }_{i}\})={\rm{\Psi }}({ {\mathcal E} }_{\xi /(N+\mathrm{1)}})\). This bound is plotted in Fig. 5 where we can se an acceptable approximation of the corresponding infinite-energy bound \({\rm{\Phi }}(\{{ {\mathcal E} }_{i}\})\).
Secret-key capacity of a chain of N equidistant repeaters creating N + 1 additive-noise Gaussian channels with variances \({\xi }_{i}=\xi /(N+\mathrm{1)}\). We compare the finite-resource upper bound \({\rm{\Psi }}(\{{ {\mathcal E} }_{i}\})\) (solid lines) with the infinite-energy upper bound \({\rm{\Phi }}(\{{ {\mathcal E} }_{i}\})\) (dashed lines) for different values of N as a function of the overall added noise of the chain ξ.
Discussion
In this work we have presented a design for the technique of teleportation stretching10 for single-mode bosonic Gaussian channels, where the core channel simulation45 is based on a finite-energy two-mode Gaussian state processed by the Braunstein-Kimble protocol43 with suitable gains. Such an approach removes the need for using an asymptotic simulation where the sequence of states approximates the energy-unbounded Choi matrix of a Gaussian channel, even though the infinite energy limit remains at the level of Alice’s quantum measurement which is ideally a CV Bell detection (i.e., a projection onto displaced EPR states). Using this approach we compute the weak converse bound for the secret key capacity of all phase-insensitive single-mode Gaussian channels, which include the thermal-loss channel, the quantum amplifier and the additive-noise Gaussian channel. We find that the bounds so derived are reasonably close to the tightest known bound established in ref.10 by using asymptotic Choi matrices. We have considered not only for point-to-point communication but also a repeater-assisted scenario where Alice and Bob are connected by a chain of quantum repeaters.
The tools developed here may have other applications. For instance, they may be applied to multi-point protocols53 and more complex quantum networks52. In an arbitrary multi-hop quantum communication network, the end-to-end capacities under single- and multi-path routing strategies may be expressed in terms of the REE of finite-energy resource states. In particular, these states can be identified by solving classical problems of network information theory (widest path or maximum flow) following the same approach in ref.52. In the context of quantum metrology, a finite-resource simulation (different from the one employed in the present paper) has been recently exploited in ref.54. The stretching strategy adopted therein allows one to simplify the most general adaptive protocol for quantum parameter estimation into a block scheme, so that one can write an upper bound for the quantum Fisher information in terms of a finite-energy resource state. This allows one to lower-bound the minimum variance of the error that affects the adaptive estimation of noise parameters in Gaussian channels, with good approximation of the optimal bounds established in ref.55 but based on asymptotic Choi matrices.
Note added
Our work first appeared on the arXiv in June 201756. It has been revised after an imprecision in ref.45 was fixed in ref.57. Independently and simultaneously, a related work58 also built on the techniques of ref.10, but its claims were restricted to a point-to-point thermal-loss channel in the non-asymptotic scenario.
Data Availability Statement
The datasets generated during the current study are available from the corresponding author on reasonable request.
References
Kimble, H. J. The quantum internet. Nature 453, 1023 (2008).
Pirandola, S. & Braunstein, S. L. Nature 532, 169 (2016).
Watrous, J. The theory of quantum information (Cambridge University Press, Cambridge, 2018).
Hayashi, M. Quantum Information Theory: Mathematical Foundation (Springer-Verlag Berlin Heidelberg, 2017).
Weedbrook, C. et al. Gaussian quantum information. Rev. Mod. Phys. 84, 621 (2012).
Braunstein, S. L. & Van Loock, P. Quantum information with continuous variables. Rev. Mod. Phys. 77, 513 (2005).
Serafini, A., Illuminati, F. & De Siena, S. Symplectic invariants, entropic measures and correlations of Gaussian states. J. Phys. B 37, L21 (2004).
Adesso, G., Ragy, S. & Lee, A. R. Continuous variable quantum information: Gaussian states and beyond. Open Syst. Inf. Dyn. 21, 1440001 (2014).
Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Proc. IEEE International Conf. on Computers, Systems, and Signal Processing, Bangalore, pp. 175–179 (1984).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017). See also Preprint arXiv, 1510.08863 (Oct 2015).
Briegel, H.-J., Dür, W., Cirac, J. I. & Zoller, P. Quantum Repeaters: The Role of Imperfect Local Operations in Quantum Communication. Phys. Rev. Lett. 81, 5932–5935 (1998).
Dür, W., Briegel, H.-J., Cirac, J. I. & Zoller, P. Quantum repeaters based on entanglement purification. Phys. Rev. A 59, 169 (1999).
Van Loock, P., Lütkenhaus, N., Munro, W. J. & Nemoto, K. Quantum repeaters using coherent-state communication. Phys. Rev. A 78, 062319 (2008).
Alleaume, R., Roueff, F., Diamanti, E. & Lütkenhaus, N. QKD networks: topological optimization. New J. Phys. 11, 075002 (2009).
Sangouard, N., Simon, C., de Riedmatten, H. & Gisin, N. Quantum repeaters based on atomic ensembles and linear optics. Rev. Mod. Phys. 83, 33 (2011).
Bruschi, D. E., Barlow, T. M., Razavi, M. & Beige, A. Repeat-until-success quantum repeaters. Phys. Rev. A 90, 032306 (2014).
Muralidharan, S., Kim, J., Lütkenhaus, N., Lukin, M. D. & Jiang, L. Ultrafast and Fault-Tolerant Quantum Communication across Long Distances. Phys. Rev. Lett. 112, 250501 (2014).
Dias, J. & Ralph, T. C. Quantum repeaters using continuous-variable teleportation. Phys. Rev. A 95, 022312 (2017).
Pant, M., Krovi, H., Englund, D. & Guha, S. Rate-distance tradeoff and resource costs for all-optical quantum repeaters. Phys. Rev. A 95, 012304 (2017).
Christandl, M. & Muller-Hermes, A. Relative Entropy Bounds on Quantum, Private and Repeater Capacities. Commun. Math. Phys. 353, 821–852 (2017).
Rozpedek, F. et al. Parameter regimes for a single sequential quantum repeater. Quantum Sci. Technol. 3, 034002 (2018).
Lo Piparo, N., Sinclair, N. & Razavi, M. Memory-assisted quantum key distribution resilient against multiple-excitation effects Preprint arXiv, 1707.07814 (July 2017).
Lo Piparo, N., Razavi, M. & Munro, W. J. Memory-Assisted Quantum Key Distribution with a Single Nitrogen-Vacancy Center. Phys. Rev. A 96, 052313 (2017).
Pant, M. et al. Routing entanglement in the quantum internet. Preprint arXiv, 1708.07142 (Aug 2017).
Garca-Patrón, R., Pirandola, S., Lloyd, S. & Shapiro, J. H. Reverse coherent information. Phys. Rev. Lett. 102, 210501 (2009).
Pirandola, S., Garca-Patrón, R., Braunstein, S. L. & Lloyd, S. Direct and reverse secret-key capacities of a quantum channel. Phys. Rev. Lett. 102, 050503 (2009).
Vedral, V. The role of relative entropy in quantum information theory. Rev. Mod. Phys. 74, 197 (2002).
Vedral, V., Plenio, M. B., Rippin, M. A. & Knight, P. L. Quantifying Entanglement. Phys. Rev. Lett. 78, 2275–2279 (1997).
Vedral, V. & Plenio, M. B. Entanglement Measures and Purification Procedures. Phys. Rev. A 57, 1619 (1998).
Synak-Radtke, B. & Horodecki, M. J. On asymptotic continuity of functions of quantum states. Phys. A: Math. Gen. 39, L423–L437 (2006).
Christandl, M. et al Unifying classical and quantum key distillation. Proceedings of the 4th Theory of Cryptography Conference, Lecture Notes in Computer Science. 4392, 456–478 See also Preprint arXiv, quant-ph/0608199v3 for a more extended version (2007).
Christandl, M., Schuch, N. & Winter, A. Entanglement of the antisymmetric state. Comm. Math. Phys. 311, 397–422 (2012).
Bennett, C. H., DiVincenzo, D. P., Smolin, J. A. & Wootters, W. K. Mixed State Entanglement and Quantum Error Correction. Phys. Rev. A 54, 3824–3851 (1996).
Niset, J., Fiurasek, J. & Cerf, N. J. No-Go Theorem for Gaussian Quantum Error Correction. Phys. Rev. Lett. 102, 120501 (2009).
Müller-Hermes, A. Master’s thesis (Technical University of Munich, 2012).
Pirandola, S. et al. Theory of channel simulation and bounds for private communication. Quantum Sci. Technol. 3, 035009 (2018).
Pirandola, S., Laurenza, R. & Braunstein, S. L. Teleportation simulation of bosonic Gaussian channels: Strong and uniform convergence. Eur. Phys. J. D 72, 162 (2018). See also Preprint arXiv, 1712.01615 (2017).
Bennett, C. H. et al. Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels. Phys. Rev. Lett. 70, 1895 (1993).
Pirandola, S. et al. Advances in quantum teleportation. Nature Photon. 9, 641–652 (2015).
Bowen, G. & Bose, S. Teleportation as a Depolarizing Quantum Channel, Relative Entropy, and Classical Capacity. Phys. Rev. Lett. 87, 267901 (2001).
Cope, T. P. W., Hetzel, L., Banchi, L. & Pirandola, S. Simulation of non-Pauli channels. Phys. Rev. A 96, 022323 (2017).
Leung, D. & Matthews, W. On the power of PPT-preserving and non-signalling codes. IEEE Trans. Info. Theory 61, 4486–4499 (2015).
Braunstein, S. L. & Kimble, H. J. Teleportation of Continuous Quantum Variables. Phys. Rev. Lett. 80, 869–872 (1998).
Giedke, G. & Cirac, J. I. The characterization of Gaussian operations and Distillation of Gaussian States. Phys. Rev. A 66, 032316 (2002).
Liuzzo-Scorpo, P., Mari, A., Giovannetti, V. & Adesso, G. Optimal continuous variable quantum teleportation with limited resources. Phys. Rev. Lett. 119, 120503 (2017).
Pirandola, S. & Mancini, S. Quantum Teleportation with Continuous Variables: a survey. Laser Physics 16, 1418 (2006).
Pirandola, S. & Laurenza, R. General Benchmarks for Quantum Repeaters. Preprint arXiv, 1512.04945 (Dec 2015).
Horodecki, K., Horodecki, M., Horodecki, P. & Oppenheim, J. Secure key from bound entanglement. Phys. Rev. Lett. 94, 160502 (2005).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. The Ultimate Rate of Quantum Communications. Preprint arXiv, 1510.08863v2 (Dec 2015).
Mari, A. private communication (May and June 2017).
Banchi, L., Braunstein, S. L. & Pirandola, S. Quantum fidelity for arbitrary Gaussian states. Phys. Rev. Lett. 115, 260501 (2015).
Pirandola, S. Capacities of repeater-assisted quantum communications. Preprint arXiv, 1601.00966 (Jan 2016).
Laurenza, R. & Pirandola, S. General bounds for sender-receiver capacities in multipoint quantum communications. Phys. Rev. A 96, 032318 (2017).
Laurenza, R., Lupo, C., Spedalieri, G., Braunstein, S. L. & Pirandola, S. Channel Simulation in Quantum Metrology. Quantum Meas. Quantum Metrol. 5, 1–12 (2018).
Pirandola, S. & Lupo, C. Ultimate Precision of Adaptive Noise Estimation. Phys. Rev. Lett. 118, 100502 (2017).
Laurenza, R., Braunstein, S. L. & Pirandola, S. Finite-resource teleportation stretching for continuous-variable systems. Preprint arXiv, 1706.06065v1 (June 2017).
Liuzzo-Scorpo, P., Mari, A., Giovannetti, V. & Adesso, G. Erratum: Optimal Continuous Variable Quantum Teleportation with Limited Resources. Phys. Rev. Lett. 20, 029904(E) (2018).
Kaur, E. & Wilde, M. M. Upper bounds on secret key agreement over lossy thermal bosonic channels. Phys. Rev. A 96, 062318 (2017). See also Preprint arXiv, 1706.04590v1(June 2017).
Acknowledgements
This work has been supported by the EPSRC via the ‘UK Quantum Communications Hub’ (EP/M013472/1). The authors would like to thank G. Adesso for comments on our first developments soon after the appearance of ref.45, and A. Mari for discussions on the relations between the various bounds, and the finite-resource simulation of the pure-loss channel. The authors also thank C. Lupo, G. Spedalieri, C. Ottaviani, S. Tserkis, T. Ralph, and S. Lloyd.
Author information
Authors and Affiliations
Contributions
R.L. contributed to the theoretical derivations and found the finite-resource bounds. S.L.B. contributed to the general development of the ideas. S.P. developed the underlying theory and wrote the manuscript.
Corresponding author
Ethics declarations
Competing Interests
The authors declare no competing interests.
Additional information
Publisher's note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Laurenza, R., Braunstein, S.L. & Pirandola, S. Finite-resource teleportation stretching for continuous-variable systems. Sci Rep 8, 15267 (2018). https://doi.org/10.1038/s41598-018-33332-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-018-33332-y
- Springer Nature Limited
Keywords
This article is cited by
-
End-to-end capacities of a quantum communication network
Communications Physics (2019)
-
Fundamental limits to quantum channel discrimination
npj Quantum Information (2019)
-
Finite-resource teleportation stretching for continuous-variable systems
Scientific Reports (2018)