Abstract
The field of quantum communications promises the faithful distribution of quantum information, quantum entanglement, and absolutely secret keys, however, the highest rates of these tasks are fundamentally limited by the transmission distance between quantum repeaters. The ultimate end-to-end rates of quantum communication networks are known to be achievable by an optimal entanglement distillation protocol followed by teleportation. In this work, we give a practical design for this achievability. Our ultimate design is an iterative approach, where each purification step operates on shared entangled states and detects loss errors at the highest rates allowed by physics. As a simpler design, we show that the first round of iterations can purify completely at high rates. We propose an experimental implementation using linear optics and photon-number measurements which is robust to inefficient operations and measurements, showcasing its near-term potential for real-world practical applications.
Similar content being viewed by others
Introduction
The great challenge for quantum communication1 is how to overcome loss2, the dominant source of noise through free space and telecom fibres. Many applications3,4,5,6,7, including quantum key distribution (QKD)8,9 (i.e., the task of sharing a secret random key between two distant parties), suffer from an exponential rate-distance scaling10,11. Determining the most efficient protocols for distributing quantum information, entanglement, and secure keys is of vital importance to realise the full capability of the quantum internet12.
It is known that the reverse coherent information (RCI)13 is an achievable rate for entanglement distillation by an implicit optimal protocol based on one-way classical communication. For the bosonic pure-loss channel, this rate is \(R=-{\log }_{2}(1-\eta )\)10, where η ∈ [0, 1] is the channel transmissivity. This is an achievable rate for entanglement distillation, ED, over the lossy channel and is also an achievable rate for secret key distribution, K, since an ebit is a specific form of secret key bit. To summarise, we have \(K\ge {E}_{{{{\rm{D}}}}}\ge R=-{\log }_{2}(1-\eta )\). Ref. 14 proved the upper bound, the so-called Pirandola–Laurenza–Ottaviani–Banchi (PLOB) bound, that is, \(K\le -{\log }_{2}(1-\eta )\). This, together with the lower bound, R, from ref. 10, establishes \(K={E}_{{{{\rm{D}}}}}=R=-{\log }_{2}(1-\eta )=C\), the two-way-assisted entanglement distribution capacity and secret key distribution capacity of the pure-loss channel.
Likewise, there are fundamental limits to the highest end-to-end rates of arbitrary quantum communication networks15, where untrusted quantum repeaters divide the total distances into shorter quantum channels (links). Quantum repeaters are strictly required to beat the PLOB bound16,17. For a linear repeater chain, it is optimal to place repeaters equidistantly, then the ultimate end-to-end rate is given by \(-{\log }_{2}(1-\eta )\)15, where η now refers to the transmissivity of each link. For a multiband network, consisting of m generally entangled channels in parallel, the rate is additive, \(-m{\log }_{2}(1-\eta )\)15. These ultimate repeater bounds are achievable by using an optimal entanglement distillation protocol followed by quantum teleportation (entanglement swapping), while ideal quantum memories are most likely required to achieve the highest rates.
The goal of this paper is to give a physical realisation for achieving these ultimate rates, which could pave the way for experimental implementations. While the highest achievable secret key rate for point-to-point CV QKD saturates the PLOB bound8, it does not provide a physical design for entanglement distillation. Furthermore, it is impossible to distil Gaussian entanglement using Gaussian operations only18,19 so quantum repeaters must use non-Gaussian elements20.
Protocols based on infinite-dimensional systems are required to saturate the ultimate limits. However, the majority of quantum-information-processing tasks and techniques are for discrete-variable (DV) systems21 where the quantum information is finite-dimensional. In contrast, for continuous-variable (CV) systems2,22,23,24, the quantum information is infinite-dimensional and encoded in the quadrature amplitudes, and in principle offer easier state manipulation22 and compatibility with existing optical telecom infrastructure25. Previous practical quantum repeater designs are unable to distil entanglement at the ultimate rates26,27,28,29,30,31.
Quantum repeaters have previously been categorised into three generations depending on how they combat loss and other sources of noise16,17. With respect to CV systems, the first two generations remove loss via teleportation-based techniques, for instance, entanglement swapping and/or noiseless linear amplification32,33,34,35,36,37,38. These techniques fail to achieve the ultimate limits under pure loss since the output state is not pure and the success probability is zero for high-energy input states. For instance, the schemes based on noiseless linear amplification29,30,31 have the same rate-distance scaling as the ultimate bounds but do not saturate them. A simple explanation is given in Supplementary Note 1, also see ref. 39.
The third generation of quantum repeaters40 uses quantum error correction and is a purely one-way communication scheme. It promises high rates since it does not require back-and-forth classical signalling, however, here the ultimate rates are bounded by the unassisted quantum capacity of each link14, \({\log }_{2}(\frac{\eta }{1-\eta })\, < \,C\). This means the third-generation rate is zero if η ≤ 0.5, which translates to a maximum link distance of about 15 km for optical fibre with a loss rate of 0.2 dB km−1. In contrast, the two-way assisted capacity of pure loss allows a nonzero achievable rate at all distances. It is interesting to note that the family of GKP codes41 achieves the unassisted capacity of general Gaussian thermal-loss channels with added thermal noise, where pure loss is the zero-temperature case, up to at most a constant gap42. Likewise, our main result is to give a practical protocol that achieves the two-way assisted capacity of the pure-loss channel.
In summary, all three generations of quantum repeaters are unable to operate at rates that saturate the ultimate limits of quantum communications. Motivated by this reality, we introduce an iterative protocol to purify completely from pure loss and achieve the capacity of the channel. Our schemes are inspired by refs. 43,44. The idea is that neighbouring nodes locally perform photon-number measurements on copies of shared CV entanglement across the lossy channel, followed by two-way classical communication to compare photon-number outcomes. We show that the highest rates of our purification scheme, requiring two-way classical communication, achieve the fundamental limits of quantum communications for pure-loss channels. In contrast to quantum error correction, we describe purification as a quantum-error-detection scheme against loss. We consider a much-simpler design with good rates requiring only one-way classical communication and no iteration.
In this work, the required measurements are quantum non-demolition measurements (QND) of the total photon number of multiple modes and can be implemented experimentally using linear optics and photon-number measurements. This implementation is naturally robust against the inefficiencies of the detectors and gates. Alternatively, these QND measurements can be implemented using high finesse cavities and cross-Kerr nonlinearities44.
Results
First, we introduce our iterative protocol for the complete purification of high-dimensional entanglement, saturating the two-way assisted capacity of the bosonic pure-loss channel. Then, we show that our protocol without iteration (i.e. single-shot) still gives high rates which fall short of the ultimate limits by at worst a factor of 0.24. Finally, we explain how to implement our protocol using linear optics and photon-number measurements.
Iterative purification
Alice and Bob share multiple copies of a state which is entangled in photon number, such that in a lossless situation they will always measure the same number of photons. Our purification technique, in a pure loss situation, is for Alice and Bob to each locally count the total number of photons contained in multiple copies of the shared entangled states, and then compare the results. If they locally find a different total number of photons, this means photons were lost. Alice and Bob then iteratively perform total photon-number measurements over smaller subsets of states until their outcomes are the same, and hence distil pure entanglement. We prove that the highest average rate of the protocol achieves the capacity of the pure-loss channel.
We now consider our protocol in detail. The protocol is shown in Fig. 1. Consider two neighbouring nodes in a network, Alice and Bob, separated by a repeaterless link. Round one of our iterative protocol is identical to the entanglement purification of Gaussian CV quantum states from ref. 44, however, our protocol includes an iterative procedure. Alice prepares m copies of a pure two-mode squeezed vacuum (TMSV) state, \(\left|\chi \right\rangle =\sqrt{1-{\chi }^{2}}\mathop{\sum }\nolimits_{n = 0}^{\infty }{\chi }^{n}\left|n\right\rangle \left|n\right\rangle\) in the Fock photon-number basis, with squeezing parameter χ ∈ [0, 1]. The unique entanglement measure, E, for a bipartite pure state, \(\left|\phi \right\rangle\), is given by the von Neumann entropy, S, of the reduced state, i.e., \(E=-{{{\rm{tr}}}}({\rho }_{{\rm{A}}}{\log }_{2}{\rho }_{\rm{{A}}})\), where \({\rho }_{{\rm{A}}}={{{{\rm{tr}}}}}_{{\rm{B}}}\left|\phi \right\rangle \left\langle \phi \right|\). This means Alice initially prepares mEχ ebits of entanglement, where Eχ = G[(λk−1)/2], where \(G(x)=(x+1){\log }_{2}(x+1)-x{\log }_{2}(x)\), \({\lambda }_{k}=2\bar{n}+1\), \(\bar{n}=\sinh^{2} {r}\), and \(r={\tanh }^{-1}\chi\).
Alice shares m two-mode-squeezed-vacuum states with Bob across independent pure-loss channels with transmissivity η. Iterative QND measurements of total photon number at Alice’s and Bob’s sides followed by classical communication herald pure states whenever kn = jn, which means round n is successful and the protocol is complete. The highest average rate of quantum communication achieves the capacity (the PLOB bound14). Alice’s measurements encode the quantum information onto the rails, and Bob’s measurements purify the entanglement and decode the quantum information.
Alice shares the second mode of each of the m pairs with Bob across the link. The error channel we consider is bosonic pure loss, modelled by mixing the data rails with vacuum modes of the environment, or a potential eavesdropper (Eve), on a beamsplitter with transmissivity η.
Alice encodes the quantum information into a quantum-error-detecting code so that Bob can detect errors on his side. To do this, she performs a QND measurement of total photon number on the m modes and obtains outcome k1 (where subscript 1 refers to round one of iteration), and shares this information with Bob via classical communication. Alice’s measurement projects the system before the channel onto a maximally-entangled state44
where \(|{\mu }_{{k}_{1},m}\rangle =|{n}_{1}^{(\mu )},{n}_{2}^{(\mu )},\cdots \,,{n}_{m}^{(\mu )}\rangle\) can be viewed as orthogonal basis states which form a quantum-error-detecting code, each composed of \(\mathop{\sum }\nolimits_{i = 1}^{m}{n}_{i}^{(\mu )}={k}_{1}\) photons. We discuss the code in detail later. The pure maximally entangled state \({\left|{\phi }_{{k}_{1},m}\right\rangle }_{\rm{{AB}}}\) has entanglement \({E}_{{k}_{1},m}={\log }_{2}{d}_{{k}_{1},m}\) ebits with dimension \({d}_{{k}_{1},m}={{{k}_{1}+m-1}\choose{{k}_{1}}}\), and the probability of Alice’s measurement outcome, k1, is \({P}_{{k}_{1},m}^{{{{\rm{Alice}}}}}={(1-{\chi }^{2})}^{m}{\chi }^{2{k}_{1}}{d}_{{k}_{1},m}\). The dimension, \({d}_{{k}_{1},m}\), is the total number of ways k1 identical photons can be arranged among the m distinct rails.
Bob then performs a QND measurement of the total photon number across the m rails on his side to detect loss errors. If Bob obtains the outcome j1 photons and knows that Alice sent k1 photons, then both Alice and Bob know that k1−j1 photons were lost. Bob’s QND measurement, with success probability \({P}_{{k}_{1},{j}_{1}}^{{{{\rm{Bob}}}}}={(1-\eta )}^{{k}_{1}-{j}_{1}}{\eta }^{{j}_{1}}{{{k}_{1}}\choose{{j}_{1}}}\), heralds a renormalised mixed state shared between Alice and Bob which does not depend on loss for any outcome j1. That is, together Alice’s and Bob’s QND measurements remove all dependence on loss and have exchanged success probability for entanglement, while they learn that k1−j1 photons were lost to the environment. All outcomes besides zero at Alice and Bob herald useful entanglement. If j1 ≠ k1, they must do further rounds of purification (iteration) since the output state is not pure. If j1 = k1, then the output state is strictly pure and purification is complete in a single round. For a simpler protocol, Alice and Bob may post-select on outcomes j1 = k1 without further iteration. We show later in the paper that this single-shot protocol still gives excellent rates.
Explicitly, the global output state heralded by outcomes k1 and j1 is
where A, B, e refer to the m-rail quantum systems owned by Alice, Bob, and the environment, respectively, as shown in Fig. 1. The full derivation of this state is in Supplementary Note 2. The factor \({(1-\eta )}^{\frac{{k}_{1}-{j}_{1}}{2}}{\eta }^{\frac{{j}_{1}}{2}}\) is outside the sum, thus, we have the remarkable result that the renormalised output state shared between Alice and Bob does not depend on η. Therefore, the entanglement shared between Alice and Bob also has no dependence on η, which has been exchanged for probabilities.
Additional rounds of purification can purify more entanglement after the initial round. One approach is for Alice and Bob to locally perform QND measurements as in round one but on m−n + 1 rails, and obtain outcomes kn, jn, where n refers to the round number. At round n, there is no entanglement shared between Alice and Bob on the last n−1 rails and the photon number of each of these rails is completely known. At round n, these last n−1 rails can be discarded while the m−n + 1 rails should be kept.
Rate of iterative purification for finite numbers of rails
The rate of our purification protocol (in ebits per use) is maximised if Alice performs her first measurement offline (i.e., setting \({P}_{{k}_{1},m}^{{{{\rm{Alice}}}}}=1\)), where she obtains outcome k1. For finite m, there is a finite k1 which optimises the rate. However, for large squeezing χ → 1 outcomes k1 is dominated by k1 → ∞ with unity probability. Therefore, the large squeezing limit χ → ∞ without k1 pre-selection is equivalent to k1 → ∞ with offline k1 pre-selection.
Taking Alice’s first measurement to be done with result k1 offline (which can be chosen in advance to optimise the rate or, for example, the practicality of the protocol), the rate for finite m is
where the sum is constrained by
where the probability of success for a particular combination of outcomes, j1, k2, j2, …, kn, jn, for a given k1 and m is
where a maximally entangled state is generated with entanglement
The rate \({E}_{{k}_{1},m}(\eta )\) for finite m can be optimised over Alice’s initial outcome k1 prepared offline and the number of rails m as a function of η. We numerically compute the rate in Supplementary Note 3 for small k1 and m. We show next that the highest rate of our iterative protocol achieves the capacity, C, for m → ∞ and k1 → ∞ (i.e., χ → 1). We show this without having to compute Eq. (4) directly which would be arduous.
Optimality of our protocol
The RCI10,13, R, gives an achievable lower bound on the distillable entanglement, ED, and on the optimal secret key rate. The RCI is defined in the “Methods” section. We will show that our protocol is optimal for entanglement distillation as m → ∞ and χ → 1 and that no entanglement is lost between rounds. We use the RCI as a benchmark to test the quality of our distillation procedure. The optimal distillation protocol implicit by the RCI is not required here since our scheme gives the same performance as the implicit optimal protocol round after round for large m.
We require that the weighted average von Neumann entropy of the reduced pure states heralded after round one, S1, plus the average RCI of the failure states heralded after round one, F1, equals the RCI of the state before round one. Note that the RCI equals the von Neumann entropy for pure states. We have
in units of ebits per channel use, where
where \({P}_{{k}_{1},{j}_{1},m}={P}_{{k}_{1},m}^{{{{\rm{Alice}}}}}{P}_{{k}_{1},{j}_{1}}^{{{{\rm{Bob}}}}}\), where \({P}_{{k}_{1},m}^{{{{\rm{Alice}}}}}={(1-{\chi }^{2})}^{m}{\chi }^{2{k}_{1}}{d}_{{k}_{1},m}\) and \({P}_{{k}_{1},{j}_{1}}^{{{{\rm{Bob}}}}}={(1-\eta )}^{{k}_{1}-{j}_{1}}{\eta }^{{j}_{1}}{{{k}_{1}}\choose{{j}_{1}}}\). When the first round succeeds, the entanglement of the renormalised maximally entangled pure-state shared between Alice and Bob heralded by outcomes k1 = j1 is given by the von Neumann entropy of the reduced state:
which does not depend on the transmissivity, η, nor the amount of two-mode squeezing, χ. When the first round fails, the RCI of the renormalised mixed state shared between Alice and Bob heralded by each pair of outcomes k1 and j1 is
which also does not depend on the transmissivity, η, nor the amount of two-mode squeezing, χ. See Supplementary Note 2 for the derivation.
The amount of squeezing is scaled to infinity χ → 1, such that Alice initially measures a large amount of photons k1 → ∞ and m/k1 → 0. Furthermore, from the fact that \({P}_{{k}_{1},{j}_{1}}^{{{{\rm{Bob}}}}}\) is a binomial distribution, Bob will most likely measure j1 ≈ ηk1 photons. Using these conditions, we show in Supplementary Note 3 that Eq. (12) approaches
which ensures that round one of purification is optimal since there is no loss of rate after round one as m → ∞, given that the average RCI at the end of the round equals the initial RCI of the protocol. Thus, there exists an optimal protocol to follow round one which can saturate the two-way assisted quantum capacity (the PLOB bound) using our protocol as an initial step. The entanglement is optimally exchanged for success probability.
Similarly, we prove in Supplementary Note 3 that round n is optimal since there is no loss of rate at round n as m → ∞, up to the same factor, \(\frac{m-1}{m}\). This factor comes from Alice’s and Bob’s measurements of photon numbers.
To quantify this loss of entanglement, consider the protocol before the channel. We will see that for finite m some entanglement is immediately lost after Alice’s QND measurement. Ref. 44 defined the entanglement ratio, denoted by Γ1, as the average entanglement heralded by Alice’s QND measurement divided by the total initial entanglement mEχ, that is,
In the limit of a large number of rails \(\mathop{\lim }\nolimits_{m\to \infty }{\Gamma }_{1}=1\) for all 0 < χ ≤ 1, which means asymptotically Alice’s QND measurement heralds no loss of entanglement. However, for finite m in the limit of large squeezing, \(\mathop{\lim }\nolimits_{\chi \to 1}{\Gamma }_{1}=(m-1)/m\). So, for a finite number of rails m some entanglement is lost since 1/2 < (m−1)/m < 1. This means we must take m → ∞ to get the highest rates.
Similarly, to quantify the entanglement lost at round n > 1, we define the entanglement ratio, \({\Gamma }_{{k}_{n-1}}\), as the weighted average entanglement heralded at round n overall outcomes kn normalised by the weighted entanglement heralded by outcome kn−1 at the previous round, n−1, that is,
where \({d}_{{k}_{n}}={{{k}_{n}+m-n}\choose{{k}_{n}}}\) and \({d}_{{k}_{n-1}}={{{k}_{n-1}+m-n+1}\choose{{k}_{n-1}}}\). \({P}_{{k}_{n}}\) (\({P}_{{k}_{n-1}}\)) and \({E}_{{k}_{n}}\) (\({E}_{{k}_{n-1}}\)) are defined in Eqs. (10) and (11), for a given kn(kn−1), and of course, we can take ji = ki for all i since here we consider no loss channel. Many of the factors cancel giving the simple expression in Eq. (19). Curiously, for large numbers of rails, the amount of entanglement lost at round n is the same as for round one, i.e., \(\mathop{\lim }\nolimits_{m\to \infty }{\Gamma }_{{k}_{n-1}}=(m-1)/m\) for all kn−1. This result ensures that "encoding” into kn photons is asymptotically optimal throughout the entire duration of our iterative procedure up to the factor (m−1)/m, which approaches unity for large m.
Achieving the capacity
The average rate in case of success of pure entanglement distilled at round n in ebits per use of the channel is
and the average rate in case of failure of entanglement distilled at round n in ebits per use of the channel is lower bounded by the average RCI
where P is the probability from Eq. (10) and \(R={\log }_{2}\left[\frac{\left({{{k}_{n}+m-n}\atop{{k}_{n}}}\right)}{\left({{k}_{n}-{j}_{n}+m-n}\atop{{k}_{n}-{j}_{n}}\right)}\right]\) is the RCI of the heralded states. Note \({\delta }_{{k}_{n},{j}_{n}}\) is the Kronecker delta function. For the rate in case of success, the RCI equals the von Neumann entropy since the states are pure, R = E. The entanglement in case of failure at round n will be purified at a later round.
Since our protocol is optimal at round n for χ → 1 and m → ∞, we have the following expressions:
for 2 ≤ n ≤ m. We solve this system of equations by addition, and we find that the average rate in case of success of purification using our iterative procedure for m → ∞ and χ → 1 is
We achieve the capacity (PLOB) in the limit of a large number of rails, where \(\mathop{\lim }\nolimits_{m\to \infty }\mathop{\sum }\nolimits_{n = 1}^{m-1}\frac{{F}_{n}}{m}\to 0\) and \(\mathop{\lim }\nolimits_{m\to \infty }(m-1)/m\to 1\). See Supplementary Note 3 for the proof.
Achievable rates of repeater networks
Our protocol purifies completely at the PLOB rate. Assuming ideal quantum memories are available, after teleportation (entanglement swapping) we achieve the ultimate end-to-end rates of quantum communication networks by adopting the routing methods of ref. 15. That is, the results can be extended beyond chains to consider more complex topologies and routing protocols15. We describe details about entanglement swapping in Supplementary Note 4. We plot the highest rates of iterative purification as a function of total distance with no repeater and one repeater in Fig. 2a (black lines) which coincide with the capacities. We also plot rates in Fig. 2a for single-shot purification for finite m where Alice and Bob stop after the first round which is a much more practical design. We discuss in detail those single-shot rates next.
a We plot the highest rates of iterative purification (black), single-shot purification (red), and single-shot purification for qubits (blue dashed) as a function of the total end-to-end distance, for optical fibre with a loss rate of 0.2 dB km−1. Purification is used to distribute and purify entanglement between nodes and entanglement swapping connects the end users. To illustrate, we plot rates without a repeater and with one repeater. Equivalently, these rates are secret key rates since ebits are specific types of secret bits62. Our highest rates coincide with the ultimate limits of quantum communications (black), shown here the repeaterless PLOB bound14 and the one-repeater bound15. At all distances, the output states are strictly pure. The scaling improves for increased numbers of repeaters (not shown). b The ratio of the optimised rate of our single-shot purification protocol without a repeater with the repeaterless PLOB bound as a function of distance, showing how close it comes to saturating the bound (and therefore end-to-end quantum-repeater networks in general). The optimal number of photons, k, at each distance is shown in rounded brackets. At shorter distances codes with more photons are optimal. The three-rail encoding (m = 3) is optimal at most distances, with sometimes a larger m optimal at distances less than about 1.6 km. At large distances, the ratio \({E}_{k,m}^{{{{\rm{single}}\,{\rm{shot}}}}}/C\) approaches \(\ln (3)/3 \sim 0.366\). As the distance goes to zero, \({E}_{k,m}^{{{{\rm{single}}\,{\rm{shot}}}}}/C=1/2\).
Single-shot purification
Purification is complete after a single round if no photons are lost and Alice and Bob detect the same number of photons, j1 = k1. If Bob detects fewer photons than Alice, j1 < k1, further purification is required, however, it is most practical to disregard those outcomes and keep only the outcome j1 = k1 which purifies in one shot. Alice’s measurement can be pre-selected and prepared offline, thus, improving the rate of a particular pair of outcomes. The single-shot rate for a given m and k ≡ k1 = j1 can be quite close to the PLOB rate.
Recall that the optimal protocol implicit by the RCI is based on one-way classical communication13, whereas, our iterative procedure requires two-way classical communication. Here, the single-shot protocol requires only one-way classical communication, like the implicit optimal protocol. Alice and Bob agree on the quantum-error-detecting code (k and m) in advance, so Alice does not need to send any classical information towards Bob. Bob only needs to send classical information towards Alice, telling her when the protocol succeeds. This greatly simplifies the required back-and-forth signalling in a quantum network.
Highest achievable rate of single-shot purification
The rate of single-shot purification is as follows. The probability that Alice obtains outcome k is \({P}_{k,m}^{{{{\rm{Alice}}}}}={(1-{\chi }^{2})}^{m}{\chi }^{2k}{d}_{k,m}\), however, for the single-shot protocol we can incorporate this step into Alice’s state preparation and assume this is done offline such that \({P}_{k,m}^{{{{\rm{Alice}}}}}=1\). This means the rate will not depend on χ. When Bob obtains the outcome which matches Alice’s, k, his probability is \({P}_{k}^{{{{\rm{Bob}}}}}={\eta }^{k}\) and the output state is pure with entanglement \({E}_{k,m}={\log }_{2}{d}_{k,m}\). Thus, the achievable rate of single-shot entanglement purification in ebits per use of the channel is
The rate is divided by the number of rails, m, to compare directly with the PLOB bound14. This is required because Alice and Bob exploit a quantum channel whose single use involves the simultaneous transmission of m distinct systems in a generally entangled state.
This rate is for a perfect implementation without any additional losses, errors, or noise. The protocol heralds pure states in a single attempt, so if we have ideal quantum memories, after entanglement swapping (see Supplementary Note 4 for details on entanglement swapping) we can distribute entanglement between ends of a network without any loss of rate, i.e., at the rate given by Eq. (27) where η is the transmissivity of the most destructive link.
Our optimised rate over k and m is shown in Fig. 2a, without and with one quantum repeater (with a repeater, we assume ideal quantum memories). The PLOB bound can ultimately be broken at 46.3 km using single-shot purification between nodes and a single repeater for entanglement swapping. In Fig. 2b, we show the ratio of our optimised single-shot rate with the PLOB bound, showing that at long distances the protocol falls short of the PLOB bound by just a factor of \(\ln (3)/3 \sim 0.366\), and remarkably, our rate approaches \(C/2\) at short distances. At short distances, the rate is optimised for larger k while at long distances k = 1 is always optimal since the probability that photons arrive scales like ηk at long distances. The optimal number of rails is about m = 3 at most distances (including long distances) since increasing the number of rails decreases the rate like 1/m. Larger m is sometimes optimal at short distances.
The rate of our single-shot purification protocol is unable to saturate the ultimate limit because we post-select on Bob’s outcomes, throwing away useful entanglement when j ≠ k and j > 0. Keeping all measurement outcomes, the rate increases, however, it is less practical to do so.
Quantum error detection
In this section, we describe our single-shot purification protocol as quantum error detection. Consider encoding an arbitrary finite-dimensional single-rail state with dimension dk,m:
where \({N}_{\psi }=\mathop{\sum }\nolimits_{\mu = 0}^{{d}_{k,m}-1}| {c}_{\mu }{| }^{2}\).
The code is a subspace with dk,m dimensions (dk,m-dimensional), a subspace of the infinite-dimensional Hilbert space chosen to detect loss errors nondeterministically. It is represented by the projector onto the subspace
where \(\left|{\mu }_{k,m}\right\rangle =|{n}_{1}^{(\mu )},{n}_{2}^{(\mu )},{n}_{3}^{(\mu )},\cdots \,,{n}_{m}^{(\mu )}\rangle\) are the orthogonal basis states (code words) which make up the code subspace (code space), where μ is the logical label. Note \({n}_{i}^{(\mu )}\) is the number of photons in the ith rail, which depends on the logical label μ, as well as k and m where \(\mathop{\sum }\nolimits_{i = 1}^{m}{n}_{i}^{(\mu )}=k\). There are dk,m code words, i.e., for a given code the set of code words is \(\{\left|{\mu }_{k,m}\right\rangle \}=\{\left|{0}_{k,m}\right\rangle ,\left|{1}_{k,m}\right\rangle ,\left|{2}_{k,m}\right\rangle ,\cdots \,\}\). Quantum information up to dimension dk,m can faithfully be transmitted to Bob, conditioned that he detects no errors. Photon loss (and photon gains) will result in states outside of code space, which we can distinguish as an error.
The set of logical states forming the dk,m-dimensional basis of the code consists of all possible ways k identical photons can be arranged among the m distinct rails. For example, \(\left|{\mu }_{k = 2,m = 3}\right\rangle \in \{\left|0,0,2\right\rangle ,\left|0,2,0\right\rangle ,\left|2,0,0\right\rangle ,\left|0,1,1\right\rangle ,\left|1,0,1\right\rangle ,\left|1,1,0\right\rangle \}\). The code space is a subspace of the full Hilbert space of the m rails which introduces the redundancy required for error detection, that is, k photons and m rails can encode dk,m-dimensional states. The dimension grows rapidly with k and m. For example, with just k = 4 photons and m = 5 rails, we can efficiently encode 70-dimensional states, i.e., truncated at Fock number \(\left|69\right\rangle\), with success probability \({P}_{j = k = 4}^{{{{\rm{Bob}}}}}={\eta }^{k}={\eta }^{4}\). This is a great advantage over noiseless linear amplification, for example, if we choose the gain of the amplifier to be \(g=1/\sqrt{\eta }\) to overcome the loss then the success probability is \({P}_{{{{\rm{NLA}}}}}=1/{g}^{2({d}_{k,m}-1)}={\eta }^{({d}_{k,m}-1)}={\eta }^{69}\), totally impractical. Furthermore, noiseless linear amplification fails to purify completely and cannot completely overcome the loss.
The encoding step is
which maps Fock states, \(\left|\mu \right\rangle\), from a single mode to the code words, \(\left|{\mu }_{k,m}\right\rangle =|{n}_{1}^{(\mu )},{n}_{2}^{(\mu )},\cdots \,,{n}_{m}^{(\mu )}\rangle\). The combined operation of encoding, loss, and decoding is a completely-positive trace-non-increasing map
where \({{{{\mathcal{L}}}}}^{\otimes m}\) is the map for independent applications of the pure-loss channel on the m rails, the decoding step, \({{{{\mathcal{S}}}}}^{-1}\), performs a QND measurement of the total photon number, and if k photons arrive, then it successfully decodes back to a single rail. The decoding step succeeds only if no photons are lost. The combined operation, \({{{\mathcal{E}}}}\), is a scaled identity map up to the (dk,m−1)th Fock state, thus, the protocol succeeds with success probability \({P}_{k}^{{{{\rm{Bob}}}}}={{{\rm{tr}}}}({\rho }_{\rm{{AB}}})={\eta }^{k}\) with unit fidelity.
The input state may be entangled with another mode. For example, we may consider encoding one arm of an arbitrary entangled state, \(\left|{\psi }_{k,m}\right\rangle \propto \mathop{\sum }\nolimits_{\mu = 0}^{{d}_{k,m}-1}{c}_{\mu }{\left|\mu \right\rangle }_{{\rm{A}}}{\left|\mu \right\rangle }_{{\rm{B}}}\). In this case, the operation, \({{{\mathcal{E}}}}\), acts on Bob’s mode only and Alice leaves her mode alone. The final state shared between Alice and Bob is \({\rho }_{{\rm{AB}}}=({\mathbb{1}}\otimes {{{\mathcal{E}}}}){\rho }_{{{{\rm{in}}}}}\), where ρin is the initial state and \({\mathbb{1}}\) is the identity on mode A. Note there is still useful entanglement if photons are lost. The entanglement-distribution rate of single-shot error detection for a maximally entangled initial state \({\left|{\phi }_{k,m}\right\rangle }_{{\rm{AB}}}=\frac{1}{\sqrt{{d}_{k,m}-1}}\mathop{\sum }\nolimits_{\mu = 0}^{{d}_{k,m}-1}{\left|\mu \right\rangle }_{{\rm{A}}}{\left|\mu \right\rangle }_{{\rm{B}}}\) is given by Eq. (27), showing that error detection and purification indeed are equivalent.
One might consider using purification to distribute Gaussian entanglement for long-distance CV QKD between trusted end users of a network, performing the entanglement-based CV-QKD protocol based on homodyne detection45,46 or heterodyne detection47. Consider the initial data state to be a truncated TMSV state with dimension dk,m given by
The state is Gaussian except for the hard truncation in Fock space. The protocol works as follows. First, truncated TMSV states, \(\left|{\chi }_{k,m}\right\rangle\), are distributed using our single-shot purification scheme between all repeater nodes and held in quantum memories. Once successful, CV entanglement swapping is used to entangle the end users who use the entanglement to perform CV QKD. While the purification scheme can be complex (depending on the chosen protocol size), the CV entanglement swapping is simple. It works by performing dual-homodyne measurements on some of the modes, followed by conditional displacements, swapping the entanglement48, see Supplementary Note 4 for details on how to compute the secret key rate.
A simple example: the qubit code
The simplest nontrivial code uses a single photon, k = 1, in two rails, m = 2, (i.e., unary dual-rail) and protects qubit systems, dk=1,m=2 = 2, from loss. It is equivalent to the original purification protocol from ref. 43, but in this context, we use it to purify entanglement completely from pure loss to first order in Fock space and we can protect arbitrary single-rail qubit states from loss. The code words can be defined \(\left|{0}_{k = 1,m = 2}\right\rangle \equiv \left|0,1\right\rangle\) and \(\left|{1}_{k = 1,m = 2}\right\rangle \equiv \left|1,0\right\rangle\). The projector onto the code space is \({{{\mathcal{P}}}}=\left|0,1\right\rangle \left\langle 0,1\right|+\left|1,0\right\rangle \left\langle 1,0\right|\). The encoding step is
which maps the vacuum component of the data mode onto a single photon of the second rail and the single-photon component of the data mode onto a single photon of the first rail. If either of these photons is lost, the protocol fails. The success probability is \({P}_{j = k = 1}^{{{{\rm{Bob}}}}}=\eta\). The maximum single-shot rate in ebits per use is \({D}_{k = 1,m = 2}^{{{{\rm{single}}}}\,{{{\rm{shot}}}}}(\eta )=\eta /2\), as shown by the dashed line in Fig. 2a (with and without a repeater).
Physical implementation
Entanglement purification (iterative and single shot) requires joint QND measurements on multiple rails. These measurements can be performed via controlled-SUM quantum gates and photon number-resolving measurements (see Supplementary Note 5, for example). Another technique is to use high finesse cavities and cross-Kerr nonlinearities44.
More simply, our scheme can be implemented using beamsplitters and photon-number-resolving detectors, however, it also requires an entangled resource state, \(\left|{\Omega }_{k,m}\right\rangle\). This is a common technique in linear optics49,50. See ref. 51 for a review of quantum information processing using linear optics. The resource state can also be generated using linear optics and photon-number measurements. That is, we have a simple method of implementing our protocol, though at some cost to the success probability.
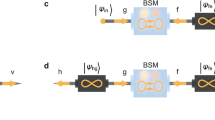
We focus on the single-shot linear-optics protocol, shown in Fig. 3. Alice shares m entangled states, \(\left|\chi \right\rangle\), with Bob. Note each rail could have a different χ, distiling different amounts of entanglement between Alice and Bob at the end of the protocol, however, maximal entanglement is heralded when all rails have the same value of χ. Alice and Bob each prepare locally multimode resource states, \(\left|{\Omega }_{k,m}\right\rangle\), consisting of (m + 1) modes. We assume they do this offline so it does not affect the quantum communication rate:
where \(\left|\mu \right\rangle\) are Fock states, \(|{\mu }_{\widetilde{k,m}}\rangle\) are “anticorrelated” code words. Writing the usual code words in the Fock basis as \(|{\mu }_{k,m}\rangle =|{n}_{1}^{(\mu )},{n}_{2}^{(\mu )},{n}_{3}^{(\mu )},\cdots \,,{n}_{m}^{(\mu )}\rangle\), where \({n}_{i}^{(\mu )}\) is the number of photons in the ith rail, and where \(\mathop{\sum }\nolimits_{i = 1}^{m}{n}_{i}^{(\mu )}=k\), recalling that the code space was defined as the set of all states with this property, then \(|{\mu }_{\widetilde{k,m}}\rangle =|k-{n}_{1}^{(\mu )},k-{n}_{2}^{(\mu )},k-{n}_{3}^{(\mu )},\cdots \,,k-{n}_{m}^{(\mu )}\rangle\). The coefficients, fn, are
The aim of the protocol is for Alice to share quantum information contained in a dk,m-dimensional pure state, \(\left|{\psi }_{k,m}\right\rangle\), which can be entangled with another system which Alice keeps, with Bob separated by a pure-loss channel. Shown in this figure, the aim is to distribute a pure maximally entangled state between Alice and Bob. Alice shares m entangled states, \(\left|\chi \right\rangle\), with Bob. Encoding/decoding simply requires beamsplitters, photon detectors, and (m + 1)-mode entangled resource states, \(\left|{\Omega }_{k,m}\right\rangle\). We can assume Alice’s encoding (the state heralded after Alice’s measurement) is prepared offline so that the success probability of the protocol is the probability of Bob’s side only. There is, however, a success-probability penalty for using linear optics, noting crucially that this penalty does not depend on the loss. The protocol succeeds when Bob detects the same number of photons Alice sent, k. If Bob detects less photons, multiple rounds of error detection are required or Alice and Bob can simply disregard those states.
The last m modes of \(\left|{\Omega }_{k,m}\right\rangle\) are fed into the beamsplitters with the distributed entanglement and are measured by photon-number detectors. The first mode is kept locally by the user and remains at the end of the protocol, as shown in Fig. 3.
Detecting k photons means there were no loss events since \({n}_{i}^{(\mu )}+k-{n}_{i}^{(\mu )}=k\). That is, all photons are accounted for in the circuit and the output state is strictly pure. There may be useful entanglement for measurement outcomes other than \(\left|0,k\right\rangle \left\langle 0,k\right|\) at each pair of detectors, and further purification (iteration) can increase the rate, but we do not consider it due to practicality.
Adjusting the amount of entanglement prepared for each rail, adjusting the loss on each rail, or selecting different coefficients in the resource state, fn, results in a different output state, which may be useful for certain tasks. For example, if the entangled states prepared for each rail are identical and have the same amount of squeezing and fn is chosen as in Eq. (36), then a maximally entangled state will be heralded between Alice and Bob at the output. For another example, consider the dual-rail case (m = 2), if the second rail is maximally entangled and fn is chosen as in Eq. (36), then the output state is the initial state of the top rail. This tuning of the circuit parameters is useful, for instance, for CV QKD where the target state is a truncated TMSV state.
The linear-optics scheme detects all errors and outputs a pure state. There is, however, an additional success probability penalty using linear optics because of Bob’s decoding measurement. We assume Alice prepares offline, then the success probability is
which depends on m. Compare this with the ideal purification protocol where \({P}_{k}^{{{{\rm{Bob}}}}}={\eta }^{k}\) which does not depend on m. The penalty paid for using linear optics is mainly due to the exponential 2m(k−1) factor, which is painful for anything other than k = 1, where \({P}_{k = 1}^{{{{\rm{Bob}}\,{\rm{linear}}\,{\rm{optics}}}}}=\eta /m\). For more details we refer you to Supplementary Note 6.
The linear-optics circuit leads naturally to a controlled-SUM gate using linear optics and number measurements, albeit with distorted coefficients (this distortion ultimately has no effect in our protocol since we immediately measure the state). For the interested reader, we refer you to Supplementary Note 5 for more details.
Since Alice’s encoded state is prepared offline, it is useful to consider more generally that she encodes an arbitrary state into the code: \(({\mathbb{1}}\otimes {{{\mathcal{S}}}})\left|{\psi }_{k,m}\right\rangle\).
Preparation of resource states
For our linear optics and number measurement circuit, the resource state, \(\left|{\Omega }_{k,m}\right\rangle\), and Alice’s encoded state she prepares offline, are multi-mode entangled states. Once these states are prepared, our scheme requires just beamsplitters and photon detectors. One practical way to prepare these states is to use a Gaussian Boson Sampler (GBS)52 and post-selecting on a specific photon-number-resolving measurement click pattern on some of the modes of the output53,54. This allows our scheme to be implemented entirely using linear optics and number measurements. Using the GBS method for the simplest scheme with k = 1 and m = 2, we have found the resource state, \(\left|{\Omega }_{k = 1,m = 2}\right\rangle =(\left|0,1,0\right\rangle +\left|1,0,1\right\rangle )/\sqrt{2}\), can be prepared with high fidelity, F > 0.999, with success probability ≈ 10−6. This was found by optimising the parameters of a GBS network via a machine learning algorithm called “basin hopping”55. In https://github.com/JGuanzon/state-finder, we have provided our code that implements this algorithm, as well as the parameter set we found that generates this resource state. Alternatively, adaptive phase measurements56 can be used to prepare the needed resource states directly from dual-rail Bell pairs or GHZ-like states which may have a higher probability of success.
Experimental imperfections
Our linear-optics circuit is robust to loss. The quality of the state Alice sends can be managed since her encoding is done offline. In any case, we are interested in the noise introduced by the protocol, not the noise in the initial state we are trying to transmit. The measurement and detection scheme at Bob’s side is such that all photons are accounted for, so if Alice’s encoding is perfect, the protocol can correctly identify if any photons are lost in the channel or at the detectors. More details are presented in Supplementary Note 6, where we also perform a numerical simulation incorporating inefficient detectors with dark counts and a thermal-noise channel. Our protocol is robust to the practical values of these imperfections.
The directionality issue
Often in quantum communications, it is best if quantum states propagate in one preferred direction (from Alice towards Bob) when reverse reconciliation is used. This is a persistent problem in CV quantum communications. For instance, CV measurement-device-independent protocols57,58,59,60 work only in an extremely asymmetric configuration, with the node (ineffective as a repeater) positioned close to one of the trusted parties. This directionality problem is also present in the repeater protocols considered in ref. 29,30, where they work best in one direction, which for reverse reconciliation is again from Alice towards Bob. Our purification schemes allow states to propagate in any direction in a quantum network since the output states are pure. Using purification for CV-QKD works the same for both direct and reverse reconciliations. We have no directionality problem. This is an important requirement for large CV networks. Note that the memoryless CV repeater protocol introduced in ref. 31 also fixes the directionality problem.
Discussion
We have presented a physical protocol that achieves the two-way assisted quantum capacity of the pure-loss channel14. Error correction requires short distances between neighbouring repeater nodes, while in contrast, we showed simple error detection can saturate the PLOB bound. An open question is what protocol can saturate the fundamental limits for added thermal noise and close the gap between the theoretical upper and lower bounds14.
Our protocol is an optimal one and can be performed using CSUM quantum gates and measurements. However, it is unknown whether other gates and measurements may also achieve the capacity, and if they can do so more efficiently, i.e., approaching the PLOB bound more quickly with the number of iteration rounds, n.
Our ultimate protocol is experimentally challenging since it requires iterative purification steps. However, we show that by simplifying our protocol to just a single round of purification, we can still achieve excellent rates. This is superior to other nondeterministic techniques such as noiseless linear amplification where it is impossible to remove all effects of loss.
Our purification protocol can be implemented using linear optics and number measurements. This does introduce some probability penalty (which does not depend on the loss), however, having an all-optical design is experimentally convenient.
One limitation of our results is the requirement for high-performance quantum memories. However, purification outputs pure states which is extremely beneficial. Firstly, pure states can handle a higher amount of decoherence coming from nonideal quantum memories. Secondly, distributing pure states will prevent how much thermal noise builds up across a network during entanglement swapping. Finally, purity may be beneficial for both point-to-point and repeater-assisted CV QKD, improving the signal-to-noise ratio and decreasing Eve’s knowledge of the key, speeding up the classical post-processing part of the protocol.
Thus, purification is inherently a useful technique for overcoming the unavoidable losses in quantum communication networks. Remarkably, purification can be employed totally using linear optics and number measurements and is compatible with existing DV and CV infrastructure. Finally, we remark that since the lossy entanglement is completely purified, it can be used for exotic tasks, such as device-independent quantum key distribution and demonstrating Bell nonlocalities, over long distances.
Methods
Noise model
Bosonic pure loss is the dominant source of noise for many quantum communication tasks. The pure-loss channel is equivalent to introducing a vacuum mode and mixing the data state on a beamsplitter with transmissivity η ∈ [0, 1]. The Kraus-operator representation of the single-mode pure-loss channel is61
with Kraus operators \({A}_{l}=\sqrt{\frac{{(1-\eta )}^{l}}{l!}}{\eta }^{\hat{\frac{n}{2}}}{\hat{a}}^{l}\) associated with losing l photons to the environment, where \(\hat{a}\) and \({\hat{a}}^{{\dagger} }\) are the single-mode annihilation and creation operators, respectively, and \(\hat{n}={\hat{a}}^{{\dagger} }\hat{a}\) is the photon-number operator.
Reverse coherent information
Take a maximally entangled state of two systems A and B. Propagating the B system through the quantum channel defines the Choi state of the channel. Then the reverse coherent information represents a lower bound for the distillable entanglement and for the optimal secret key rate. The reverse coherent information of a state ρAB is defined as13
where S(ρA) and S(ρAB) are von Neumann entropies of \({\rho }_{{\rm{A}}}={{{{\rm{tr}}}}}_{{\rm{B}}}({\rho }_{{\rm{AB}}})\) and ρAB respectively. The von Neumann entropy of ρ is \(-{{{\rm{tr}}}}(\rho {\log }_{2}\rho )\).
Data availability
The datasets generated during and analysed during the current study are available from the corresponding author on reasonable request.
References
Gisin, N. & Thew, R. Quantum communication. Nat. Photonics 1, 165–171 (2007).
Cerf, N., Leuchs, G. & Polzik, E. Quantum Information with Continuous Variables of Atoms and Light (Imperial College Press, 2007).
Proctor, T. J., Knott, P. A. & Dunningham, J. A. Multiparameter estimation in networked quantum sensors. Phys. Rev. Lett. 120, 080501 (2018).
Ge, W., Jacobs, K., Eldredge, Z., Gorshkov, A. V. & Foss-Feig, M. Distributed quantum metrology with linear networks and separable inputs. Phys. Rev. Lett. 121, 043604 (2018).
Zhuang, Q., Zhang, Z. & Shapiro, J. H. Distributed quantum sensing using continuous-variable multipartite entanglement. Phys. Rev. A 97, 032329 (2018).
Van Meter, R. & Devitt, S. J. The path to scalable distributed quantum computing. Computer 49, 31–42 (2016).
Danos, V., D’Hondt, E., Kashefi, E. & Panangaden, P. Distributed measurement-based quantum computation. Electron. Notes Theor. Comput. Sci. 170, 73–94 (2007). Proceedings of the 3rd International Workshop on Quantum Programming Languages (QPL 2005).
Pirandola, S. et al. Advances in quantum cryptography. Adv. Opt. Photonics 12, 1012–1236 (2020).
Xu, F., Ma, X., Zhang, Q., Lo, H.-K. & Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 92, 025002 (2020).
Pirandola, S., García-Patrón, R., Braunstein, S. L. & Lloyd, S. Direct and reverse secret-key capacities of a quantum channel. Phys. Rev. Lett. 102, 050503 (2009).
Takeoka, M., Guha, S. & Wilde, M. M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 5, 5235 (2014).
Kimble, H. J. The quantum internet. Nature 453, 1023–1030 (2008).
García-Patrón, R., Pirandola, S., Lloyd, S. & Shapiro, J. H. Reverse coherent information. Phys. Rev. Lett. 102, 210501 (2009).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017).
Pirandola, S. End-to-end capacities of a quantum communication network. Commun. Phys. 2, 51 (2019).
Munro, W. J., Azuma, K., Tamaki, K. & Nemoto, K. Inside quantum repeaters. IEEE J. Sel. Top. Quantum Electron. 21, 78–90 (2015).
Muralidharan, S. et al. Optimal architectures for long distance quantum communication. Sci. Rep. 6, 20463 (2016).
Giedke, G. & Ignacio Cirac, J. Characterization of gaussian operations and distillation of Gaussian states. Phys. Rev. A 66, 032316 (2002).
Eisert, J., Scheel, S. & Plenio, M. B. Distilling gaussian states with gaussian operations is impossible. Phys. Rev. Lett. 89, 137903 (2002).
Namiki, R., Gittsovich, O., Guha, S. & Lütkenhaus, N. Gaussian-only regenerative stations cannot act as quantum repeaters. Phys. Rev. A 90, 062316 (2014).
Nielsen, M. A. & Chuang, I. L. Quantum Computation and Quantum Information: 10th Anniversary Edition (Cambridge University Press, USA, 2011).
Braunstein, S. L. & van Loock, P. Quantum information with continuous variables. Rev. Mod. Phys. 77, 513–577 (2005).
Weedbrook, C. et al. Gaussian quantum information. Rev. Mod. Phys. 84, 621–669 (2012).
Serafini, A. Quantum Continuous Variables: A Primer of Theoretical Methods (CRC Press, 2017).
Kumar, R., Qin, H. & Alléaume, R. Coexistence of continuous variable QKD with intense DWDM classical channels. New J. Phys. 17, 043027 (2015).
Dias, J. & Ralph, T. C. Quantum repeaters using continuous-variable teleportation. Phys. Rev. A 95, 022312 (2017).
Furrer, F. & Munro, W. J. Repeaters for continuous-variable quantum communication. Phys. Rev. A 98, 032335 (2018).
Seshadreesan, K. P., Krovi, H. & Guha, S. Continuous-variable quantum repeater based on quantum scissors and mode multiplexing. Phys. Rev. Res. 2, 013310 (2020).
Ghalaii, M. & Pirandola, S. Capacity-approaching quantum repeaters for quantum communications. Phys. Rev. A 102, 062412 (2020).
Dias, J., Winnel, M. S., Hosseinidehaj, N. & Ralph, T. C. Quantum repeater for continuous-variable entanglement distribution. Phys. Rev. A 102, 052425 (2020).
Winnel, M. S., Guanzon, J. J., Hosseinidehaj, N. & Ralph, T. C. Overcoming the repeaterless bound in continuous-variable quantum communication without quantum memories. Preprint at bioRxiv https://arxiv.org/abs/2105.03586 (2021).
Ralph, T. C. & Lund, A. P. Nondeterministic noiseless linear amplification of quantum systems. AIP Conf. Proc. 1110, 155–160 (2009).
Winnel, M. S., Hosseinidehaj, N. & Ralph, T. C. Generalized quantum scissors for noiseless linear amplification. Phys. Rev. A 102, 063715 (2020).
Guanzon, J. J., Winnel, M. S., Lund, A. P. & Ralph, T. C. Ideal quantum teleamplification up to a selected energy cutoff using linear optics. Phys. Rev. Lett. 128, 160501 (2022).
Fiurášek, J. Teleportation-based noiseless quantum amplification of coherent states of light. Opt. Express 30, 1466–1489 (2022).
Blandino, R. et al. Improving the maximum transmission distance of continuous-variable quantum key distribution using a noiseless amplifier. Phys. Rev. A 86, 012327 (2012).
McMahon, N. A., Lund, A. P. & Ralph, T. C. Optimal architecture for a nondeterministic noiseless linear amplifier. Phys. Rev. A 89, 023846 (2014).
Blandino, R., Barbieri, M., Grangier, P. & Tualle-Brouri, R. Heralded noiseless linear amplification and quantum channels. Phys. Rev. A 91, 062305 (2015).
Pandey, S., Jiang, Z., Combes, J. & Caves, C. M. Quantum limits on probabilistic amplifiers. Phys. Rev. A 88, 033852 (2013).
Fowler, A. G. et al. Surface code quantum communication. Phys. Rev. Lett. 104, 180503 (2010).
Gottesman, D., Kitaev, A. & Preskill, J. Encoding a qubit in an oscillator. Phys. Rev. A 64, 012310 (2001).
Noh, K., Albert, V. V. & Jiang, L. Quantum capacity bounds of gaussian thermal loss channels and achievable rates with Gottesman–Kitaev–Preskill codes. IEEE Trans. Inf. Theory 65, 2563–2582 (2019).
Bennett, C. H. et al. Purification of noisy entanglement and faithful teleportation via noisy channels. Phys. Rev. Lett. 76, 722–725 (1996).
Duan, L.-M., Giedke, G., Cirac, J. I. & Zoller, P. Entanglement purification of gaussian continuous variable quantum states. Phys. Rev. Lett. 84, 4002–4005 (2000).
J. Cerf, N., Lévy, M. & Van Assche, G. Quantum distribution of gaussian keys using squeezed states. Phys. Rev. A 63, 052311 (2001).
Gottesman, D. & Preskill, J. Secure quantum key distribution using squeezed states. Phys. Rev. A 63, 022309 (2001).
Weedbrook, C. et al. Quantum cryptography without switching. Phys. Rev. Lett. 93, 170504 (2004).
Hoelscher-Obermaier, J. & van Loock, P. Optimal gaussian entanglement swapping. Phys. Rev. A 83, 012319 (2011).
Yan, P.-S., Zhou, L., Zhong, W. & Sheng, Y.-B. Feasible measurement-based entanglement purification in linear optics. Opt. Express 29, 9363–9384 (2021).
Yan, P.-S., Zhou, L., Zhong, W. & Sheng, Y.-B. Measurement-based entanglement purification for entangled coherent states. Front. Phys. 17, 21501 (2021).
Kok, P. et al. Linear optical quantum computing with photonic qubits. Rev. Mod. Phys. 79, 135–174 (2007).
Hamilton, C. S. et al. Gaussian boson sampling. Phys. Rev. Lett. 119, 170501 (2017).
Su, D., Myers, C. R. & Sabapathy, K. K. Conversion of gaussian states to non-gaussian states using photon-number-resolving detectors. Phys. Rev. A 100, 052301 (2019).
Quesada, N. et al. Simulating realistic non-gaussian state preparation. Phys. Rev. A 100, 022341 (2019).
Sabapathy, K. K., Qi, H., Izaac, J. & Weedbrook, C. Production of photonic universal quantum gates enhanced by machine learning. Phys. Rev. A 100, 012326 (2019).
Ralph, T. C., Lund, A. P. & Wiseman, H. M. Adaptive phase measurements in linear optical quantum computation. J Opt B Quantum Semiclass. Opt. 7, S245–S249 (2005).
Ma, X.-C., Sun, S.-H., Jiang, M.-S., Gui, M. & Liang, L.-M. Gaussian-modulated coherent-state measurement-device-independent quantum key distribution. Phys. Rev. A 89, 042335 (2014).
Zhang, Y.-C. et al. Continuous-variable measurement-device-independent quantum key distribution using squeezed states. Phys. Rev. A 90, 052325 (2014).
Ottaviani, C., Spedalieri, G., Braunstein, S. L. & Pirandola, S. Continuous-variable quantum cryptography with an untrusted relay: detailed security analysis of the symmetric configuration. Phys. Rev. A 91, 022320 (2015).
Pirandola, S. et al. High-rate measurement-device-independent quantum cryptography. Nat. Photonics 9, 397–402 (2015).
Chuang, I. L., Leung, D. W. & Yamamoto, Y. Bosonic quantum codes for amplitude damping. Phys. Rev. A 56, 1114–1125 (1997).
Horodecki, K., Horodecki, M., Horodecki, P. & Oppenheim, J. Secure key from bound entanglement. Phys. Rev. Lett. 94, 160502 (2005).
Acknowledgements
We thank Ozlem Erkilic, Sebastian Kish, Ping Koy Lam, Syed Assad, Deepesh Singh, and Josephine Dias for valuable discussions during this investigation. We thank Deepesh Singh for the alternative proof given in Supplementary Note 7. This research was supported by the Australian Research Council (ARC) under the Centre of Excellence for Quantum Computation and Communication Technology (CE170100012).
Author information
Authors and Affiliations
Contributions
M.W. and J.J.G. conceived the idea. T.R. supervised the research and actively contributed to the discussions. N.H. provided important feedback on the manuscript and security considerations. M.W. and J.J.G. prepared the manuscript. M.W. prepared the figures and did the simulations for the numerical data. J.J.G. derived many of the analytical results including the success probability linear-optics closed expressions, and implemented the “basin hopping” algorithm for resource state preparation. All authors read and contributed to the paper.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Winnel, M.S., Guanzon, J.J., Hosseinidehaj, N. et al. Achieving the ultimate end-to-end rates of lossy quantum communication networks. npj Quantum Inf 8, 129 (2022). https://doi.org/10.1038/s41534-022-00641-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41534-022-00641-0
- Springer Nature Limited