Abstract
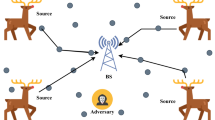
The rapidly advancing Internet of things has eventually led to both dependency and efficiency in almost all walks of life. However, with every benefit, there comes a threat to the privacy of data of numerous forms, thus posing a challenge to security. Increasing concern has been observed over the undesiring location privacy leaks/theft to unauthorized entities, which demands attention and, more importantly, efficient data transmission techniques. The vulnerability of location privacy is compromised by attacking or maliciously intervening in the wireless sensor nodes by attackers. By monitoring the transmission and scrutinizing the information in packets, the attackers can attain the location of the source, which sets a heavy blow to the efficiency of wireless sensor networks (WSNs). There is an adhering need for location privacy protection techniques for wireless networks. This work provides a detailed analysis of the persisting source location privacy protection techniques along with the trade-offs between different parameters affecting their performance against attackers. In particular, we review context-oriented privacy-preserving techniques against passive attacks, taking into account the three different models- The network model, the Adversary model, and the proposed model. Challenges and attacks on the reviewed techniques have been discussed in brief with the hope of facilitating exemplary future research on source location preservation in WSNs.



















Similar content being viewed by others
Data Availability
There has been no use of data sets in this manuscript.
References
Yick J, Mukherjee B, Ghosal D. Wireless sensor network survey. Comput Netw. 2008;52:2292–330. https://doi.org/10.1016/j.comnet.2008.04.002.
Akyildiz IF, Su W, Sankarasubramaniam Y, Cayirci E. A survey on sensor networks. IEEE Commun Mag. 2002;40(8):102–14.
Kim, B. S., Park, H., Kim, K. H., Godfrey, D., & Kim, K. I. (2017). A survey on real-time communications in wireless sensor networks. Wireless communications and mobile computing, 2017.
Tyagi AK, Sreenath N. A comparative study on privacy preserving techniques for location based services. British Journal of Mathematics & Computer Science. 2015;10(4):1–25.
Rajalakshmi K, Goyal M. Location-based services: Current state of the art and future prospects. Optical and Wireless Technologies: Proceedings of OWT. 2018;2017:625–32.
Wang H, Han G, Hou Y, Guizani M, Peng Y. A multi-channel interference based source location privacy protection scheme in underwater acoustic sensor networks. IEEE Trans Veh Technol. 2021;71(2):2058–69.
Liu Y, Han G, Wang H, Jiang J. FPTSA-SLP: a fake packet time slot assignment-based source location privacy protection scheme in underwater acoustic sensor networks. In: 2021 Computing, Communications and IoT Applications (ComComAp). IEEE; 2021, p. 307–311.
Han G, Wang H, Ansere JA, Jiang J, Peng Y. SSLP: A stratification-based source location privacy scheme in underwater acoustic sensor networks. IEEE Network. 2020;34(4):188–95.
Conti M, Willemsen J, Crispo B. Providing source location privacy in wireless sensor networks: a survey. Commun Surv Tutor IEEE. 2013;15:1238–80. https://doi.org/10.1109/SURV.2013.011413.00118.
de Fuentes, J. M., González-Manzano, L., & Mirzaei, O. (2016). Privacy models in wireless sensor networks: A survey. Journal of Sensors, 2016.
Jiang J, Han G, Wang H, Guizani M. A survey on location privacy protection in Wireless Sensor Networks. J Netw Comput Appl. 2019;125:93–114.
Karimi R, Kalantari M. Enhancing security and confidentiality in location-based data encryption algorithms. In: Fourth International Conference on the Applications of Digital Information and Web Technologies (ICADIWT 2011). IEEE; 2011, p. 30–35. https://doi.org/10.1109/ICADIWT.2011.6041421.
Mohd Shamsuddin, N. S., & Ali Pitchay, S. (2019). Location-Based Cryptographic Techniques for Data Protection. Malaysian Journal of Science, Health & Technology.
Vinodha D, Mary Anita EA. Secure data aggregation techniques for wireless sensor networks: a review. Arch Comput Methods Eng. 2019;26(4):1007–27.
Ren J, Zhang Y, Liu K. An energy-efficient cyclic diversionary routing strategy against global eavesdroppers in wireless sensor networks. Int J Distrib Sens Netw. 2013;9(4): 834245.
Avramopoulos I, Kobayashi H, Wang R, Krishnamurthy A. Highly secure and efficient routing. In: IEEE INFOCOM, vol. 1. IEEE; 2004.
Lim H, Kim C. Flooding in wireless ad hoc networks. Comput Commun. 2001. https://doi.org/10.1016/S0140-3664(00)00233-4.
Chen J, Lin Z, Hu Y, Wang B. Hiding the source based on limited flooding for sensor networks. Sensors. 2015;15(11):29129–48. https://doi.org/10.3390/s151129129.
Ozturk C, Zhang Y, Trappe W. Source-location privacy in energy-constrained sensor network routing. In: Proceedings of the 2nd ACM workshop on Security of Ad hoc and Sensor Networks; 2004, p. 88–93.
Kamat P, Zhang Y, Trappe W, Ozturk C. Enhancing source-location privacy in sensor network routing. In: 25th IEEE International Conference on distributed computing systems (ICDCS’05). IEEE; 2005, p. 599–608.
Wang WP, Chen L, Wang JX. A source-location privacy protocol in WSN based on locational angle. In: 2008 IEEE International Conference on Communications. IEEE; 2008, p. 1630–1634.
Lightfoot L, Li Y, Ren J. Preserving source-location privacy in wireless sensor network using STaR routing. In: 2010 IEEE Global Telecommunications Conference GLOBECOM. IEEE; 2010, p. 1–5.
Li Y, Ren J, Wu J. Quantitative measurement and design of source-location privacy schemes for wireless sensor networks. IEEE Trans Parallel Distrib Syst. 2011;23(7):1302–11. https://doi.org/10.1109/TPDS.2011.260.
Long J, Dong M, Ota K, Liu A. Achieving source location privacy and network lifetime maximization through tree-based diversionary routing in wireless sensor networks. IEEE Access. 2014;2:633–51.
Huang J, Sun M, Zhu S, Sun Y, Xing CC, Duan Q. A source-location privacy protection strategy via pseudo normal distribution-based phantom routing in WSNs. In: Proceedings of the 30th annual ACM symposium on applied computing; 2015, p. 688–694.
Gupta S, Kumar P, Singh JP, Singh MP. Privacy preservation of source location using phantom nodes. In: Latifi S, editors Information technology: new generations. Advances in Intelligent Systems and Computing, vol 448. Cham: Springer; 2016. https://doi.org/10.1007/978-3-319-32467-8_23
Mutalemwa LC, Shin S. Achieving source location privacy protection in monitoring wireless sensor networks through proxy node routing. Sensors. 2019;19(5):1037. https://doi.org/10.3390/s19051037.
Wang Q, Zhan J, Ouyang X, Ren Y. SPS and DPS: two new grid-based source location privacy protection schemes in wireless sensor networks. Sensors. 2019;19(9):2074. https://doi.org/10.3390/s1909207.
Abizar, Farman, H., Jan, B., Khan, Z., & Koubaa, A. (2022). A smart energy‐based source location privacy preservation model for Internet of Things‐based vehicular ad hoc networks. Transactions on Emerging Telecommunications Technologies, 33(2), e3973.
Manjula R, Koduru T, Datta R. Protecting source location privacy in IoT-Enabled wireless sensor networks: the case of multiple Assets. IEEE Internet of Things Journal. 2021;9(13):10807–20.
Jhumka A, Leeke M, Shrestha S. On the use of fake sources for source location privacy: trade-offs between energy and privacy. Comput J. 2011;54(6):860–74.
Jhumka A, Bradbury M, Leeke M. Fake source-based source location privacy in wireless sensor networks. Concurrency Computat Pract Exper. 2015;27:2999–3020. https://doi.org/10.1002/cpe.3242.
Roy PK, Singh JP, Kumar P, Singh MP. Source location privacy using fake source and phantom routing (FSAPR) technique in wireless sensor networks. Proc Comput Sci. 2015;57:936–41. https://doi.org/10.1016/j.procs.2015.07.486.
Bradbury M, Leeke M, Jhumka A. A dynamic fake source algorithm for source location privacy in wireless sensor networks. In: 2015 IEEE Trustcom/BigDataSE/ISPA, vol. 1. IEEE; 2015, p. 531–538.
Bradbury M, Jhumka A, Leeke M. Hybrid online protocols for source location privacy in wireless sensor networks. J Parall Distrib Comp. 2018;115:67–81. https://doi.org/10.1016/j.jpdc.2018.01.006.
Wang H, Han G, Zhang W, Guizani M, Chan S. A probabilistic source location privacy protection scheme in wireless sensor networks. IEEE Trans Veh Technol. 2019;68(6):5917–27. https://doi.org/10.1109/TVT.2019.2909505.
Jan N, Al-Bayatti AH, Alalwan N, Alzahrani AI. An enhanced source location privacy based on data dissemination in wireless sensor networks (DeLP). Sensors. 2019;19(9):2050. https://doi.org/10.3390/s19092050.
He Y, Han G, Wang H, Ansere JA, Zhang W. A sector-based random routing scheme for protecting the source location privacy in WSNs for the Internet of Things. Futur Gener Comput Syst. 2019;96:438–48.
He, Y., Han, G., Xu, M., & Martínez-García, M. A pseudopacket scheduling algorithm for protecting source location privacy in the Internet of Things. IEEE Internet Things J. 2021;9(12):9999–10009.
Tian H, Shen H, Matsuzawa T. Randomwalk routing for wireless sensor networks. In: Sixth International Conference on Parallel and Distributed Computing Applications and Technologies (PDCAT'05). IEEE; 2005, p. 196–200. https://doi.org/10.1109/PDCAT.2005.193.
Mabrouki, I., Froc, G., & Lagrange, X. (2008, November). Analytical evaluation of unbiased random walks in wireless sensor networks. In Autonomous and Spontaneous Networks Symposium. p. 20–21.
Kharratzadeh, M. RANDOM WALK ROUTING IN WIRELESS SENSOR NETWORKS.
Raja M, Datta R. An enhanced source location privacy protection technique for wireless sensor networks using randomized routes. IETE J Res. 2018;64(6):764–76. https://doi.org/10.1080/03772063.2017.1371652.
Wang N, Zeng J. All-direction random routing for source-location privacy protecting against parasitic sensor networks. Sensors. 2017;17(3):614. https://doi.org/10.3390/s17030614.
Mukamanzi, F., Raja, M., Datta, R., Koduru, T., Hanyurwimfura, D., & Mukanyirigira, D. (2022). Hop Threshold-based Random Walk Routing for Improved Privacy and Network Lifetime in WSNs.
Kazatzopoulos, L., Delakouridis, C., Marias, G. F., & Georgiadis, P. (2006, June). ihide: Hiding sources of information in wsns. In Second International Workshop on Security, Privacy and Trust in Pervasive and Ubiquitous Computing (SecPerU'06) (pp. 8-pp). IEEE.
Zeng, Z., Zeng, M., & Liu, H. (2014). Source-Location privacy protection in wireless sensor networks using AZR routing. In Proceedings of the International Conference on Wireless Networks (ICWN) (p. 1). The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp).
Yao L, Kang L, Deng F, Deng J, Wu G. Protecting source–location privacy based on multirings in wireless sensor networks. Concurr Computat Pract Exper. 2015;27:3863–76. https://doi.org/10.1002/cpe.3075.
Han G, Zhou L, Wang H, Zhang W, Chan S. A source location protection protocol based on dynamic routing in WSNs for the Social Internet of Things. Futur Gener Comput Syst. 2018;82:689–97.
Wang H, Han G, Zhou L, Ansere JA, Zhang W. A source location privacy protection scheme based on ring-loop routing for the IoT. Comput Netw. 2019;148:142–50.
Wang Y, Liu L, Gao W. An efficient source location privacy protection algorithm based on circular trap for wireless sensor networks. Symmetry. 2019;11:632. https://doi.org/10.3390/sym11050632.
Shukla A, Singh D, Sajwan M, Kumar M, Kumari D, Kumar A, Panthi M. SLP-RRFPR: a source location privacy protection scheme based on random ring and limited hop fake packet routing for wireless sensor networks. Multimedia Tools Appl. 2022;81(8):11145–85.
Shukla A, Singh D, Sajwan M, Verma A, Kumar A. A source location privacy preservation scheme in WSN-assisted IoT network by randomized ring and confounding transmission. Wireless Netw. 2022;28(2):827–52.
Mukamanzi, F., Raja, M., Koduru, T., & Datta, R. (2022). Position-independent and section-based source location privacy protection in WSN. IEEE Transactions on Industrial Informatics.
Sharma, N., & Bhatt, R. (2022). Source location privacy preservation in IoT-enabled event-driven WSNs. International Journal of Pervasive Computing and Communications.
Roy PK, Singh SK. Privacy preserving monitoring protocol for cyber-physical system. Comput Electr Eng. 2022;102: 108232.
Bettini C, Wang XS, Jajodia S. Protecting privacy against location-based personal identification. In: Workshop on secure data management. Berlin: Springer; 2005, p. 185–199. https://doi.org/10.1007/11552338_13
Gedik B, Liu L. Protecting location privacy with personalized k-anonymity: architecture and algorithms. IEEE Trans Mob Comput. 2007;7(1):1–18. https://doi.org/10.1109/TMC.2007.1062.
Xu T, Cai Y. Exploring historical location data for anonymity preservation in location-based services. In: IEEE INFOCOM 2008—the 27th Conference on Computer Communications. IEEE; 2008, p. 547–555. https://doi.org/10.1109/INFOCOM.2008.103.
Gkoulalas-Divanis A, Kalnis P, Verykios V. Providing K-anonymity in location based services. SIGKDD Explor. 2010;12:3–10. https://doi.org/10.1145/1882471.1882473.
Wang H, Huang H, Qin Y, Wang Y, Wu M. Efficient location privacy-preserving k-anonymity method based on the credible chain. ISPRS Int J Geo Inf. 2017;6:163. https://doi.org/10.3390/ijgi6060163.
Zhang H, Wu C, Chen Z, Liu Z, Zhu Y. A novel on-line spatial-temporal k-anonymity method for location privacy protection from sequence rules-based inference attacks. PLoS ONE. 2017;12(8):e0182232. https://doi.org/10.1371/journal.pone.0182232.
Guo, X., Wang, W., Huang, H., Li, Q., & Malekian, R. (2020). Location privacy-preserving method based on historical proximity location. Wireless Communications and mobile computing, 2020, 1–16.
Shaham S, Ding M, Liu B, Dang S, Lin Z, Li J. Privacy preservation in location-based services: a novel metric and attack model. IEEE Trans Mob Comput. 2021;20(10):3006–19. https://doi.org/10.1109/TMC.2020.2993599.
Watson L, Mediratta A, Elahi T, Sarkar R. Privacy preserving detection of path bias attacks in Tor. Proc Privacy Enhancing Technol. 2020;4:111–30.
Zhang, Q., & Zhang, K. (2022). Protecting Location Privacy in IoT Wireless Sensor Networks through Addresses Anonymity. Security and Communication Networks, 2022.
Groschupp, F. (2017). Location privacy preserving mechanisms. Future Internet (FI) and Innovative Internet Technologies and Mobile Communication (IITM) Focal Topic: Advanced Persistent Threats, 9.
Zhang C, Huang Y. Cloaking locations for anonymous location based services: a hybrid approach. GeoInformatica. 2009;13:159–82. https://doi.org/10.1007/s10707-008-0047-2.
Khoshgozaran A, Shahabi C, Shirani-Mehr H. Location privacy: going beyond K-anonymity, cloaking and anonymizers. Knowl Inf Syst. 2011;26(3):435–65. https://doi.org/10.1007/s10115-010-0286-z.
Xiao Y, Xiong L, Zhang S, Cao Y. Loclok: Location cloaking with differential privacy via hidden markov model. Proc VLDB Endowment. 2017;10(12):1901–4. https://doi.org/10.14778/3137765.3137804.
Yu R, Bai Z, Yang L, Wang P, Move OA, Liu Y. A location cloaking algorithm based on combinatorial optimization for location-based services in 5G networks. IEEE Access. 2016;4:6515–27.
Sun B, Gui C, Song Y, Chen H. A novel network coding and multi-path routing approach for wireless sensor network. Wirel Pers Commun. 2014;77(1):87–99. https://doi.org/10.1007/s11277-013-1496-y.
Liu J, Wang Q. A network coding based privacy-preservation scheme for online service access in VANET. Int J Secur Appl. 2014; 8:185–194. https://doi.org/10.14257/ijsia.2014.8.5.17.
Wang J, Wang J, Wu C, Lu K, Gu N. Anonymous communication with network coding against traffic analysis attack. In: 2011 Proceedings IEEE INFOCOM. IEEE; 2011, p. 1008–1016. https://doi.org/10.1109/INFCOM.2011.5934873.
Fan Y, Jiang Y, Zhu H, Chen J, Shen XS. Network coding based privacy preservation against traffic analysis in multi-hop wireless networks. IEEE Trans Wirel Commun. 2010;10(3):834–43. https://doi.org/10.1109/TWC.2011.122010.100087.
Li N, Raj M, Liu D, Wright M, Das S. Using data mules to preserve source location privacy in wireless sensor networks. In: 13th International Conference on Distributed Computing and Networking, ser. ICDCN 2012, The Hong Kong Polytechnic University. Berlin: Springer; 2012, pp. 309–324.
Funding
The authors declare that no funds, grants, or other support was received during the preparation of this manuscript.
Author information
Authors and Affiliations
Contributions
Both authors contributed to the study conception and design. Material preparation and analysis were performed by Nisha under the supervision of Dr. S. Suresh. The first draft of the manuscript was written by Nisha and Dr. S.Suresh commented on previous versions of the manuscript. Both authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of Interest
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Research Trends in Communication and Network Technologies” guest edited by Anshul Verma, Pradeepika Verma and Kiran Kumar Pattanaik.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Singh, N., Suresh, S. Analysis of Context-Oriented Source Location Privacy Preservation Techniques for Wireless Sensor Networks. SN COMPUT. SCI. 4, 790 (2023). https://doi.org/10.1007/s42979-023-02219-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-023-02219-9