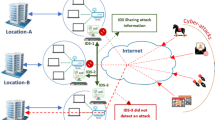
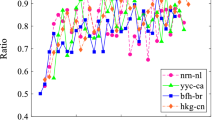
Abstract
Nowadays, Botnets have become one of the most serious cybersecurity threats and cyber crimes such as DDoS, spam, identity theft, and phishing. Because of constantly updating evasion techniques, the detection of botnets has been always an unaddressed challenge. To cope with this, we propose a new approach to detect botnet activity based on the dynamical modeling of traffic behavior. Indeed, some important features of network traffic such as packet length, sending protocol, source-IP, destination-IP, and sending time are extracted by the Wireshark software. To explore the effect of evasion methods on the network behavior, based on the extracted features, some time series have been plotted to analyze and classify the network traffic characteristics as bots are active. Due to the drastic changing of some features during evasion techniques, several suspicious behaviors are explored as chaotic dynamical behavior in the aforementioned time series to use in the definition of the final benchmark detection mechanism. To check the accuracy of the performance, two datasets ISCX IDS 2012 and CTU-Malware-Capture-Botnet-254-1 are used. The simulation results show that the proposed method has a detection rate of over 99%, the false positive rate less than 0.67%.










Similar content being viewed by others
References
Singh M, Singh M, Kaur S. Detecting bot-infected machines using DNS fingerprinting. Digit Investig. 2019;1(28):14–33.
Al-Nabki MW, Fidalgo E, Alegre E, Fernández-Robles L. Torank: identifying the most influential suspicious domains in the tor network. Expert Syst Appl. 2019;1(123):212–26.
Kirubavathi G, Anitha R. Botnet detection via mining of traffic flow characteristics. Comput Electr Eng. 2016;1(50):91–101.
Alieyan K, Almomani A, Anbar M, Alauthman M, Abdullah R, Gupta BB. DNS rule-based schema to botnet detection. Enterp Inf Syst. 2019;27:1–20.
Hoang XD, Nguyen QC. Botnet detection based on machine learning techniques using DNS query data. Future Internet. 2018;10(5):43.
Amini P, Azmi R, Araghizadeh MA. Analysis of network traffic flows for centralized botnet detection. J Telecommun Electron Comput Eng (JTEC). 2019;11(2):7–17.
Alauthman M, Aslam N, Al-Kasassbeh M, Khan S, Al-Qerem A, Choo KK. An efficient reinforcement learning-based Botnet detection approach. J Netw Comput Appl. 2020;15(150):102479.
Biradar AD, Padmavathi B. BotHook: a supervised machine learning approach for botnet detection using DNS query data. In: ICCCE 2019. Singapore: Springer; 2020. p. 261–69.
Tuan TA, Long HV, Kumar R, Priyadarshini I, Son NT. Performance evaluation of Botnet DDoS attack detection using machine learning. Evol Intel. 2019;20:1–2.
Perc M. Diffusion dynamics and information spreading in multilayer networks: an overview. 2019;2351–5.
Jalili M, Perc M. Information cascades in complex networks. J Complex Netw. 2017;5(5):665–93.
Wang W, Shang Y, He Y, Li Y, Liu J. BotMark: automated botnet detection with hybrid analysis of flow-based and graph-based traffic behaviors. Inf Sci. 2020;1(511):284–96.
Khoshhalpour E, Shahriari HR. BotRevealer: behavioral detection of botnets based on botnet life-cycle. In: ISeCure, vol 10, no 1. 2018.
Zhao D, Traore I, Sayed B, Lu W, Saad S, Ghorbani A, Garant D. Botnet detection based on traffic behavior analysis and flow intervals. Comput Secur. 2013;39:2–16.
Chen CM, Lin HC. Detecting botnet by anomalous traffic. J Inf Secur Appl. 2015;21:42–51.
Sharifnya R, Abadi M. Dfbotkiller: domain-flux botnet detection based on the history of group activities and failures in dns traffic. Digit Investig. 2015;1(12):15–26.
Nezhad SM, Nazari M, Gharavol EA. A novel DoS and DDoS attacks detection algorithm using ARIMA time series model and chaotic system in computer networks. IEEE Commun Lett. 2016;20(4):700–3.
Sebastian G. CTU-Malware-Capture-Botnet-254-1. Malware Capture Facility Project, May 2017, Retrieved from https://stratosphereips.org. Available from: https://mcfp.felk.cvut.cz/publicDatasets/CTU-Malware-Capture-Botnet-254-1/.
Shiravi A, Shiravi H, Tavallaee M, Ghorbani AA. Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput Secur. 2012;31(3):357–74. https://doi.org/10.1016/j.cose.2011.12.012. Available from: https://www.unb.ca/cic/datasets/botnet.html(ISSN 0167-4048).
Silva SS, Silva RM, Pinto RC, Salles RM. Botnets: a survey. Comput Netw. 2013;57(2):378–403.
Dietrich CJ, Rossow C, Freiling FC, Bos H, Van Steen M, Pohlmann N. On Botnets that use DNS for command and control. In: 2011 seventh european conference on computer network defense. IEEE. 2011. p. 9–16.
Khattak S, Ramay NR, Khan KR, Syed AA, Khayam SA. A taxonomy of botnet behavior, detection, and defense. IEEE Commun Surv Tutor. 2013;16(2):898–924.
Stinson E, Mitchell JC. Towards systematic evaluation of the evadability of Bot/Botnet detection methods. WOOT. 2008;28(8):1–9.
Zhang X. ActiBot: a botnet to evade active detection. 2011.
Ying W. Encrypted botnet detection scheme. In: 2014 ninth international conference on P2P, parallel, grid, cloud and internet computing. IEEE. 2014. p. 559–65.
Choi H, Lee H. Identifying botnets by capturing group activities in DNS traffic. Comput Netw. 2012;56(1):20–33.
Pomorova O, Savenko O, Lysenko S, Kryshchuk A, Bobrovnikova K. Anti-evasion technique for the botnets detection based on the passive DNS monitoring and active DNS probing. In: International conference on computer networks. Cham: Springer; 2016. p. 83–95.
Lysenko S, Pomorova O, Savenko O, Kryshchuk A, Bobrovnikova K. DNS-based anti-evasion technique for botnets detection. In: 2015 IEEE 8th international conference on intelligent data acquisition and advanced computing systems: technology and applications (IDAACS), vol. 1. IEEE. 2015. p. 453–58.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Cyber Security and Privacy in Communication Networks” guest edited by Rajiv Misra, R K Shyamsunder, Alexiei Dingli, Natalie Denk, Omer Rana, Alexander Pfeiffer, Ashok Patel and Nishtha Kesswani.
Rights and permissions
About this article
Cite this article
Nazari, M., Dahmardeh, Z. & Aliabady, S. A Novel Approach of Botnets Detection Based on Analyzing Dynamical Network Traffic Behavior. SN COMPUT. SCI. 2, 247 (2021). https://doi.org/10.1007/s42979-021-00634-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-021-00634-4