Abstract
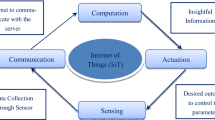
The Internet of Things refers to an interrelated connected network of smart devices, sensors, and embedded computers that store, process, and communicate heterogeneous data. As an emerging technology breakthrough, IoT has enabled the collection, processing, and communication of information for smart applications. These novel features have attracted city designers and health professionals as IoT are gaining popularity in real-time applications such as eHealth and smart homes. As the demand is increasing so security would be the primary concern for adopting smart home applications. To solve the security issue, we introduced a correlation and regression-based intrusion detection system for IoT smart home applications. In this paper, the clustering technique has been used to improve the results. We have also evaluated the performance on the basis of the true positive rate and the false positive rate. Our results show the 99% true positive rate in the comparison of the state of the art techniques.




Similar content being viewed by others
References
Aburomman AA, Reaz MBI. A novel svm-knn-pso ensemble method for intrusion detection system. Appl Soft Comput. 2016;38:360–72.
Ali B, Awad AI. Cyber and physical security vulnerability assessment for IoT-based smart homes. Sensors. 2018;18(3):817.
Azmoodeh A, Dehghantanha A, Choo KKR. Robust malware detection for internet of (battlefield) things devices using deep eigenspace learning. IEEE transactions on sustainable computing 2018a.
Azmoodeh A, Dehghantanha A, Conti M, Choo KKR. Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J Ambient Intell Human Comput. 2018b;9(4):1141–52.
Bostani H, Sheikhan M. Hybrid of anomaly-based and specification-based ids for internet of things using unsupervised OPF based on map reduce approach. Comput Commun. 2017;98:52–71.
Cao X, Shila DM, Cheng Y, Yang Z, Zhou Y, Chen J. Ghost-in-zigbee: Energy depletion attack on zigbee-based wireless networks. IEEE Internet Things J. 2016;3(5):816–29.
Chen Q, Abdelwahed S, Erradi A. A model-based validated autonomic approach to self-protect computing systems. IEEE Internet Things J. 2014;1(5):446–60.
Choi H, Lee H, Lee H, Kim H. Botnet detection by monitoring group activities in dns traffic. In: 7th IEEE International conference on computer and information technology (CIT 2007), IEEE; 2007. p. 715–720
Choudhary S, Kesswani N. Detection and prevention of routing attacks in internet of things. In: 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE); 2018. p. 1537–1540.
Choudhary S, Kesswani N. Cluster-based intrusion detection method for internet of things. In: 2019 IEEE/ACS 16th international conference on computer systems and applications (AICCSA), IEEE; 2019a. p. 1–8.
Choudhary S, Kesswani N. A survey: intrusion detection techniques for internet of things. Int J Inform Security Privacy (IJISP). 2019b;13(1):86–105.
Diro AA, Chilamkurti N. Distributed attack detection scheme using deep learning approach for internet of things. Future Generation Comput Syst. 2018;82:761–8.
Jain SK, Kesswani N. Smart judiciary system: A smart dust based iot application. In: International conference on emerging technologies in computer engineering, Springer; 2019. p. 128–140.
Jose AC, Malekian R. Improving smart home security: integrating logical sensing into smart home. IEEE Sens J. 2017;17(13):4269–86.
Kim H, Smith J, Shin KG. Detecting energy-greedy anomalies and mobile malware variants. In: Proceedings of the 6th international conference on mobile systems, applications, and services, ACM, New York, NY, USA, MobiSys ’08; 2008. p. 239–252. https://doi.org/10.1145/1378600.1378627.
Marchal S, Jiang X, State R, Engel T. A big data architecture for large scale security monitoring. In: 2014 IEEE international congress on big data, IEEE; 2014. p. 56–63.
Merlo A, Migliardi M, Fontanelli P. Measuring and estimating power consumption in android to support energy-based intrusion detection. J Comput Security. 2015;23(5):611–37.
Pajouh HH, Javidan R, Khayami R, Ali D, Choo KKR. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in iot backbone networks. IEEE Transactions on Emerging Topics in Computing 2016.
Teixeira FA, Vieira GM, Fonseca PM, Pereira FMQ, Wong HC, Nogueira JMS, Oliveira LB. Defending internet of things against exploits. IEEE Latin Am Trans. 2015;13(4):1112–9.
Yang A, Zhang C, Chen Y, Zhuansun Y, Liu H. Security and privacy of smart home systems based on the internet of things and stereo matching algorithms. IEEE Internet Things J. 2020;7(4):2521–30.
Yang H. Tang R (2016) Power consumption based android malware detection. J Electr Comput Eng 2016.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Consent for publication
All the authors gave their consent for publication.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Cyber Security and Privacy in Communication Networks” guest edited by Rajiv Misra, R K Shyamsunder, Alexiei Dingli, Natalie Denk, Omer Rana, Alexander Pfeiffer, Ashok Patel and Nishtha Kesswani.
Rights and permissions
About this article
Cite this article
Choudhary, S., Dey, A. & Kesswani, N. CRIDS: Correlation and Regression-Based Network Intrusion Detection System for IoT. SN COMPUT. SCI. 2, 168 (2021). https://doi.org/10.1007/s42979-021-00555-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-021-00555-2