Abstract
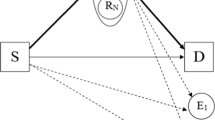
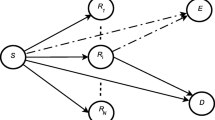
This paper investigates a cooperative network scenario involving a source, multiple users, and relays, all situated in the presence of multiple eavesdroppers attempting to intercept the secret message transmitted by the source node. To deal with this problem a novel secrecy maximization oriented relay selection (SMORS) scheme is proposed to enhance the physical layer security (PLS) of wireless systems. In this paper, the closed-form expression of intercept probability (IP) for projected SMORS and conventional max–min relay selection schemes over relay fading channels has been derived. It is observed that with an increasing the number of relays and users, the IP decreases significantly for SMORS scheme. Numerical results demonstrate that the presented SMORS scheme superior than the traditional max–min relay selection scheme.




Similar content being viewed by others
Availability of data and materials
Not applicable.
References
Wyner AD (1975) The wire-tap channel. Bell Syst Tech J 54(8):1355–1387
Chauhan SS, Mathur M, Agarwal M (2017) Secrecy performance analysis of TAS/MRC system in the presence of channel estimation error. Elsevier Int J Light Electron Opt 135:160–168
Chauhan SS, Agrawal V, Kamboj S, Narayan S (2016) Secrecy capacity and outage probability of multiuser MIMO systems with zero forcing receivers. Elsevier Int J Light Electron Opt 127:6390–6394
Shannon CE (1949) Communication theory of secrecy systems. Bell Syst Tech J 28:656–715
Chua W, Yuen C, Guan Y, Chin F (2013) Robust multi-antenna multi-user pre-coding based on generalised multi-unitary decomposition with partial CSI feedback. IEEE Trans Veh Technol 62(2):596–605
Leung-Yan-Cheong SK (1976) Multiple-user and wiretap channels including feedback. PhD dissertation. Stanford University Stanford, CA
Zhang J, Pan G (2017) Secrecy outage analysis with Kth best relay selection in dual-hop inter-vehicle communication systems. AEU-Int J Electron Commun 71:139–144
He X, Yener A (2010) Cooperation with an untrusted relay: a secrecy perspective. IEEE Trans Inf Theory 56(8):3807–3827
Zou Y, Champagne B, Zhu W, Hanzo L (2015) Relay-selection improves the secruity- reliabiltiy trade-off in cognitive radio systems. IEEE Trans Commun 63(1):215–228
Long H, Xiang W, Wang J, Zhang Y, Wang W (2014) Cooperative jamming and power allocation with un-trusty two-way relay nodes. IET Commun 8(13):2290–2297
Tran T, Kong H (2014) CSI-Secured orthogonal jamming method for wireless physical layer security. IEEE Commun Lett 18(5):841–844
Gong X, Long H, Yin H, Dong F, Ren B (2015) Robust amplify-and forward relay beam-forming for security with mean square error constraint. IET Commun 9(8):1081–1087
Jeong C, Kim I, Dong K (2012) Joint secure beam-forming design at the source and the relay for an amplify-and-forward MIMO untrusted relay system. IEEE Trans Signal Process 60(1):310–325
Zou Y, Wang X, Shen W (2013) Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE J Sel Areas Commun 31(10):2099–2111
Ismayil Siyad C, Tamilselvan S (2021) Data driven 3D channel estimation for massive MIMO. Int J Inf Technol 13(4):1395–1407
Chaudhary A, Tiwari VN, Kumar A (2014) Analysis of fuzzy logic based intrusion detection systems in mobile ad hoc networks. BVICA M’s Int J Inf Technol 6(1):690
Ghugar U, Pradhan J, Bhoi SK, Sahoo RR, Panda SK (2018) PL-IDS: physical layer trust based intrusion detection system for wireless sensor networks. Int J Inf Technol 10:489–494
Ismayil Siyad C, Tamilselvan S (2021) Chaotic deep neural network based physical layer key generation for massive MIMO. Int J Inf Technol 13:1901–1912
Rath M (2017) Resource provision and QoS support with added security for client side applications in cloud computing. Int J Inf Technol 11:357–364
Acknowledgements
Not applicable.
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
All authors contributed to the extensive literature survey and the proposed system model was suggested by SSC. The performance of the system was evaluated by SSC and RD. The numerical results & discussion part was done by RK and S. The first draft of the manuscript was written by SSC and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The author(s) declare that they have no conflict of interest.
Ethics approval and consent to participate
Yes.
Consent for publication
Yes.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chauhan, S.S., Devlal, R., Kumar, R. et al. Unified intercept probability analysis of multi-user multi-relay aided decode-and-forward wireless systems. Int. j. inf. tecnol. (2024). https://doi.org/10.1007/s41870-024-01763-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s41870-024-01763-8