Abstract
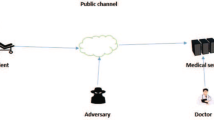
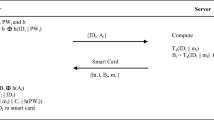
Telecare Medicine Information System (TMIS) provides patient’s efficient and convenient e-healthcare services where the patient private health related information is stored in TMIS server. However, it has also resulted a major privacy and security concerns. Thus, by considering privacy preserving and user anonymity, a major concern, a secure mutual authentication and key establishment protocol needed for creating a secure connection between patients and medical TMIS servers. In research we found major security flaws in already existing authentication schemes. To ensure user anonymity, we propose an efficient, provably secure, lightweight mutually authentication and key establishment protocol using extended chaotic map for TMIS. As the unpredictable behavior of extended chaotic map can provide a possible security solution, a contemporary cryptography. For security and correctness proof of the proposed authentication protocol, BAN (Burrows–Abadi–Needham) logic is adopted. Furthermore, the proposed authentication protocol is secure against various well-known attacks which is proved by formal and informal security analysis. The AVISPA (Automated validation of internet security protocols and application) is utilized to test the correctness of the proposed authentication protocol. Moreover, the proposed protocol satisfies the most required security requirements, with less communication and computation overhead, and outperforms the other existing authentication techniques in terms of computation, communication, storage overheads, and security.







Similar content being viewed by others
Data availability
Data is not applicable for this work.
References
Kumar D, Grover HS (2019) A secure authentication protocol for wearable devices environment using ECC. J Inf Secur Appl 47:8–15
Dodangeh P, Jahangir AH (2018) A biometric security scheme for wireless body area networks. J Inf Secur Appl 41:62–74
Dharminder D, Kumar U, Gupta P (2021) A construction of a conformal Chebyshev chaotic map based authentication protocol for healthcare telemedicine services. Complex Intell Syst. https://doi.org/10.1007/s40747-021-00441-7
Mishra D, Mukhopadhyay S, Kumari S, Khan MK, Chaturvedi A (2014) Security enhancement of a biometric based authentication scheme for telecare medicine information systems with nonce. J Med Syst 38(5):1–11
Qiu S, Xu G, Ahmad H, Wang L (2017) A robust mutual authentication scheme based on elliptic curve cryptography for telecare medical information systems. IEEE access 6:7452–7463
He D, Chen Y, Chen J (2012) Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dyn 69(3):1149–1157
Zhao F, Gong P, Li S, Li M, Li P (2013) Cryptanalysis and improvement of a three-party key agreement protocol using enhanced Chebyshev polynomials. Nonlinear Dyn 74(1):419–427
Lee TF (2013) An efficient chaotic maps-based authentication and key agreement scheme using smartcards for telecare medicine information systems. J Med Syst 37(6):1–9
Mishra D, Srinivas J, Mukhopadhyay S (2014) A secure and efficient chaotic map-based authenticated key agreement scheme for telecare medicine information systems. J Med Syst 38(10):1–10
Mullai A, Mani K (2021) Enhancing the security in RSA and elliptic curve cryptography based on addition chain using simplified Swarm Optimization and Particle Swarm Optimization for mobile devices. Int J Inf Technol 13:551–564
Lawal OM, Vincent OR, Agboola AAA, Folorunso O (2021) An improved hybrid scheme for e-payment security using elliptic curve cryptography. Int J Inf Technol 13:139–153
Lin HY (2015) Improved chaotic maps-based password-authenticated key agreement using smart cards. Commun Nonlinear Sci Numer Simul 20(2):482–488
Obaidat MS, Traore I, Woungang I (eds) (2019) Biometric-based physical and cybersecurity systems. Springer International Publishing, Cham
Yoon EJ, Jeon IS (2011) An efficient and secure Diffie-Hellman key agreement protocol based on Chebyshev chaotic map. Commun Nonlinear Sci Numer Simul 16(6):2383–2389
Meshram C, Lee CC, Meshram SG, Khan MK (2019) An identity-based encryption technique using subtree for fuzzy user data sharing under cloud computing environment. Soft Comput 23(24):13127–13138
Li CT, Lee CC, Weng CY (2014) A secure chaotic maps and smart cards based password authentication and key agreement scheme with user anonymity for telecare medicine information systems. J Med Syst 38(9):1–11
Wu ZY, Lee YC, Lai F, Lee HC, Chung Y (2012) A secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1529–1535
Wei J, Hu X, Liu W (2012) An improved authentication scheme for telecare medicine information systems. J Med Syst 36(6):3597–3604
Zhu Z (2012) An efficient authentication scheme for telecare medicine information systems. J Med Syst 36(6):3833–3838
Chen HM, Lo JW, Yeh CK (2012) An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. J Med Syst 36(6):3907–3915
Lin HY (2013) On the security of a dynamic id-based authentication scheme for telecare medical information systems. J Med Syst 37(2):1–5
Cao T, Zhai J (2013) Improved dynamic id-based authentication scheme for telecare medical information systems. J Med Syst 37(2):1–7
Guo C, Chang CC (2013) Chaotic maps-based password-authenticated key agreement using smart cards. Commun Nonlinear Sci Numer Simul 18(6):1433–1440
Jiang Q, Ma J, Ma Z, Li G (2013) A privacy enhanced authentication scheme for telecare medical information systems. J Med Syst 37(1):1–8
Yan X, Li W, Li P, Wang J, Hao X, Gong P (2013) A secure biometrics-based authentication scheme for telecare medicine information systems. J Med Syst 37(5):1–6
Li CT, Lee CC, Weng CY, Chen SJ (2016) A secure dynamic identity and chaotic maps based user authentication and key agreement scheme for e-healthcare systems. J Med Syst 40(11):1–10
Madhusudhan R, Nayak CS (2019) A robust authentication scheme for telecare medical information systems. Multimed Tools Appl 78(11):15255–15273
Radhakrishnan N, Karuppiah M (2019) An efficient and secure remote user mutual authentication scheme using smart cards for telecare medical information systems. Inf Med Unlocked 16:100092
Zhang L, Zhu S, Tang S (2016) Privacy protection for telecare medicine information systems using a chaotic map-based three-factor authenticated key agreement scheme. IEEE J Biomed Health Inform 21(2):465–475
Hsieh Y-P, Lee K-C, Lee T-F, Su G-J (2022) Extended chaotic-map-based user authentication and key agreement for HIPAA privacy/security regulations. Appl Sci 12:5701. https://doi.org/10.3390/app1211570
Yu Z, Guangmin S, Peng Z (2022) CCMbAS: a provably secure CCM-based authentication scheme for mobile internet. Mob Inf Syst 2022:7318948. https://doi.org/10.1155/2022/7318948
Wu F, Xu L, Li X, Kumari S, Karuppiah M, Obaidat MS (2018) A lightweight and provably secure key agreement system for a smart grid with elliptic curve cryptography. IEEE Syst J 13(3):2830–2838
Sureshkumar V, Amin R, Vijaykumar VR, Sekar SR (2019) Robust secure communication protocol for smart healthcare system with FPGA implementation. Futur Gener Comput Syst 100:938–951
Muttoo SK, Kumar S (2012) A robust source coding watermark technique based on magnitude DFT decomposition. BIJIT, p 480
Srikanth GU, Geetha R, Prabhu S (2023) An efficient Key Agreement and Authentication Scheme (KAAS) with enhanced security control for IIoT systems. Int J Inf Technol. https://doi.org/10.1007/s41870-023-01173-2
Renuka K, Kumari S, Li X (2019) Design of a secure three-factor authentication scheme for smart healthcare. J Med Syst 43(5):1–12
Dharminder D, Gupta P (2021) Security analysis and application of Chebyshev chaotic map in the authentication protocols. Int J Comput Appl 43(10):1095–1103
Gaikwad VP, Tembhurne JV, Meshram C, Lee CC, Li CT (2021) An efficient provably secure verifier-based three-factor authentication technique using PDL for data exchange in TMIS. IEEE Access 9:108586–108600
Dharminder D, Mishra D, Li X (2020) Construction of RSA-based authentication scheme in authorized access to healthcare services. J Med Syst 44(1):1–9
Giri D, Maitra T, Amin R, Srivastava PD (2015) An efficient and robust rsa-based remote user authentication for telecare medical information systems. J Med Syst 39(1):1–9
Lee TF, Chang IP, Lin TH, Wang CC (2013) A secure and efficient password-based user authentication scheme using smart cards for the integrated epr information system. J Med Syst 37(3):1–7
Awasthi AK, Srivastava K (2013) A biometric authentication scheme for telecare medicine information systems with nonce. J Med Syst 37(5):9964
Chaudhry SA, Naqvi H, Shon T, Sher M, Farash MS (2015) Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J Med Syst 39(6):661–6611
Mason JC, Handscomb DC (2002) Chebyshev polynomials. CRC Press
Bergamo P, D’Arco P, De Santis A, Kocarev L (2005) Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans Circuits Syst I Regul Pap 52(7):1382–1393
Han S, Chang E (2009) Chaotic map based key agreement with/out clock synchronization. Chaos, Solitons Fractals 39(3):1283–1289
Li CT, Chen CL, Lee CC, Weng CY, Chen CM (2018) A novel three-party password-based authenticated key exchange protocol with user anonymity based on chaotic maps. Soft Comput 22(8):2495–2506
Zhang L (2008) Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons Fractals 37(3):669–674
Meshram C, Li CT, Meshram SG (2019) An efficient online/offline ID-based short signature procedure using extended chaotic maps. Soft Comput 23(3):747–753
Chen F, Liao X, Wong KW, Han Q, Li Y (2012) Period distribution analysis of some linear maps. Commun Nonlinear Sci Numer Simul 17(10):3848–3856
Meshram C, Lee CC, Meshram SG, Meshram A (2020) OOS-SSS: An efficient online/offline subtree-based short signature scheme using Chebyshev chaotic maps for wireless sensor network. IEEE Access 8:80063–80073
Gaikwad VP, Tembhurne JV, Meshram C, Lee CC (2021) Provably secure lightweight client authentication scheme with anonymity for TMIS using chaotic hash function. J Supercomput. https://doi.org/10.1007/s11227-020-03553-y
Liu W, Liu J, Wu Q, Qin B, Naccache D, Ferradi H (2018) Efficient subtree-based encryption for fuzzy-entity data sharing. Soft Comput 22(23):7961–7976
Meshram C, Lee CC, Ranadive AS, Li CT, Meshram SG, Tembhurne JV (2020) A subtree-based transformation model for cryptosystem using chaotic maps under cloud computing environment for fuzzy user data sharing. Int J Commun Syst 33(7):e4307
Xiao D, Liao X, Deng S (2005) One-way hash function construction based on the chaotic map with changeable-parameter. Chaos Solitons Fract 241:65–71
(2003). The AVISPA Project, Funded By the European Union in the Future and Emerging Technologies (FET Open) Programme, Project Number: IST-2001–39252. Accessed: Jul. 11, 2020. [Online]. Available: http://www.avispa-project.org/
SPAN (2020) A security protocol animator for AVISPA. http://www.avispa-project.org/. Accessed: Jul. 11, 2020
Truong TT, Tran MT, Duong AD (2020) Chebyshev polynomial-based authentication scheme in multiserver environment polynomial-based authentication scheme. Secur Commun Netw. https://doi.org/10.1155/2020/3579705
Zhang L, Zhu Y, Ren W, Wang Y, Xiong NN (2020) An energy efficient authentication scheme using Chebyshev chaotic map for smart grid environment. Arxiv preprint arXiv:2008.11366
Chaudhry SA, Naqvi H, Khan MK (2018) An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimed Tools Appl 77(5):5503–5524
Burrows M, Abadi M, Needham RM (1989) A logic of authentication. Proc R Soc Lond A 426(1871):233–271
Mishra D, Vijayakumar P, Sureshkumar V, Amin R, Islam SH, Gope P (2018) Efficient authentication protocol for secure multimedia communications in IoT-enabled wireless sensor networks. Multimed Tools Appl 77(14):18295–18325
Sureshkumar V, Amin R, Anitha R (2018) A robust mutual authentication scheme for session initiation protocol with key establishment. Peer-to-Peer Netw Appl 11(5):900–916
Funding
This work is supported by SERB, Govt. of India. File No.: EEQ/2020/000053.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
We declare that we have no conflict of interest.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kamble, A., Gaikwad, V. & Tembhurne, J. A provably lightweight mutually authentication and key establishment protocol using extended chaotic map for telecare medicine information system. Int. j. inf. tecnol. 15, 3211–3227 (2023). https://doi.org/10.1007/s41870-023-01314-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41870-023-01314-7