Abstract
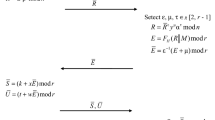
A new blind signature scheme is proposed which is characterized in that it is based on a hidden discrete logarithm problem defined in a finite commutative associative algebra. The used algebraic support represents a 4-dimensional commutative associative algebra defined over the ground finite field GF(p), commutative group of which possesses 4-dimensional cyclicity. The public key represents a triple of vectors contained in different cyclic subgroup of the multiplicative group. Correspondingly, three different blinding factors are used to insure the anonymity property of the introduced blind signature protocol.
Similar content being viewed by others
References
Rivest RL, Shamir A, Adleman LM (1978) A method for obtaining digital signatures and public key cryptosystems. Commun ACM 21(2):120–126
ElGamal T (1985) A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans Inform Theory 31(4):469–472
Chaum D (1988) Blind Signature Systems. U.S. Patent # 4,759,063
Chaum D (1983) Blind signatures for untraceable payments. advances in cryptology: Proc. of CRYPTO’82. Plenum Press, pp. 199–203
Camenisch JL, Piveteau JM, Stadler MA (1995) Blind Signatures Based on the Discrete Logarithm Problem. Advances in Cryptology - EUROCRYPT '94 volume 950 of LNCS, Springer Verlang, pp 428–432
Yan SY (2014) Quantum attacks on public-key cryptosystems. Springer, US, p 207
Ding J, Steinwandt R (2018) Post-Quantum Cryptography. 10th International Conference, PQCrypto 2019, Chongqing, China, May 8–10, 2019, Proceedings. Lecture Notes in Computer Science series. Springer, vol. 11505
Shor PW (1997) Polynomial-time algorithms for prime factorization and discrete logarithms on quantum computer. SIAM J Comput 26:1484–1509
Smolin JA, Smith G, Vargo A (2013) Oversimplifying quantum factoring. Nature 499(7457):163–165
Jozsa R (1988) Quantum algorithms and the Fourier transform. Proc Royal Soc A 454:323–337
Ekert A, Jozsa R (1996) Quantum computation and Shor’s factoring algorithm. Rev Mod Phys 68:733–752
NIST (2016) Federal Register. announcing request for nominations for public-key post-quantum cryptographic algorithms. Available at: https://www.gpo.gov/fdsys/pkg/FR-2016-12-20/pdf/2016-30615.pdf (accessed January 10, 2021)
NIST (2020) Post-Quantum Cryptography. Round 3 Submissions. Available at: https://csrc.nist.gov/projects/post-quantum-cryptography/round-3-submissions (accessed January 10, 2021)
Kuzmin AS, Markov VT, Mikhalev AA, Mikhalev AV, Nechaev AA (2017) Cryptographic algorithms on groups and algebras. J Math Sci 223(5):629–641
Moldovyan-Dmitriy N (2019) Post-quantum public key-agreement scheme based on a new form of the hidden logarithm problem. Comput Sci J Moldova 27(79):56–72
Moldovyan-Dmitriy N, Moldovyan-Nikolay A, Moldovyan-Alexander A (2020) Commutative encryption method based on hidden logarithm problem. Bullet South Ural State Univ Ser Math Model Programm Comput Softw 13(2):54–68
Moldovyan-Nikolay A, Moldovyan-Alexander A (2019) Finite non-commutative associative algebras as carriers of hidden discrete logarithm problem. Bullet South Ural State Univ Ser Math Model Programm Comput Softw 12(1):66–81
Moldovyan-Nikolay A, Abrosimov IK (2019) Post-quantum electronic digital signature scheme based on the enhanced form of the hidden discrete logarithm problem. Vestnik Saint Petersburg Univ Appl Math Comput Sci Control Process 15(2):212–220 ((In Russian))
Moldovyan-Nikolay A, Moldovyan-Alexander A (2020) Candidate for practical post-quantum signature scheme. Vestnik Saint Petersburg Univ Appl Math Comput Sci Control Process 16(4):455–461
Moldovyan-Dmitriy N (2010) Non-commutative finite groups as primitive of public-key cryptoschemes. Quasigroups Relat Syst 18:165–176
Moldovyan-Nikolay A (2020) Unified method for defining finite associative algebras of arbitrary even dimensions. Quasigroups Relat Syst 26(2):263–270
Minh NH, Moldovyan-Alexander A, Moldovyan-Nikolay A, Canh HN (2020) A new method for designing post-quantum signature schemes. J Commun 15(10):747–754
Moldovyan-Dmitriy N, Moldovyan-Alexander A, Moldovyan-Nikolay A (2020) Digital signature scheme with doubled verification equation. Comput Sci J Moldova 28(82):80–103
Moldovyan-Nikolay A, Moldovyanu-Peter A (2009) New primitives for digital signature algorithms. Quasigroups Relat Syst 17(2):271–282
Pointcheval D, Stern J (2000) Security arguments for digital signatures and blind signatures. J Cryptol 13:361–396
Koblitz N, Menezes AJ (2007) Another look at “provable security.” J Cryptol 20:3–37
Schnorr CP (1991) Efficient signature generation by smart cards. J Cryptol 4:161–174
Acknowledgements
We would like to express our sincere gratitude to the anonymous referee for his/her helpful comments that will help to improve the quality of the manuscript.
Funding
This research is supported by RFBR (project # 21–57-54001-Bьeт_a) and by Vietnam Academy of Science and Technology (project # QTRU01.13/21–22).
Author information
Authors and Affiliations
Contributions
Minh N.H and Moldovyan N.A has directed the conceptualization, formal analysis, writing—original draft preparation, writing—review & editing. Modovyan D.N, Minh L.Q and Giang N.L have directed the conceptualization, formal analysis, writing—review & editing. All authors reviewed and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no competing interests.
Availability of data and material
Not applicable.
Code availability
Not applicable.
Ethical approval
Not applicable.
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Rights and permissions
About this article
Cite this article
Nguyen, M.H., Moldovyan, D.N., Moldovyan, N.A. et al. Blind Signature Protocol Based on Hidden Discrete Logarithm Problem Set in a Commutative Algebra. Iran J Sci Technol Trans Sci 46, 323–332 (2022). https://doi.org/10.1007/s40995-021-01257-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40995-021-01257-3