Abstract
In this paper, a method for obtaining cryptographically strong 8 × 8 substitution boxes (S-boxes) is presented. The method is based on chaotic baker’s map and a “mini version” of a new block cipher with block size 8 bits and can be easily and efficiently performed on a computer. The cryptographic strength of some 8 × 8 S-boxes randomly produced by the method is analyzed. The results show (1) all of them are bijective; (2) the nonlinearity of each output bit of them is usually about 100; (3) all of them approximately satisfy the strict avalanche criterion and output bits independence criterion; (4) they all have an almost equiprobable input/output XOR distribution.
Graphical Abstract
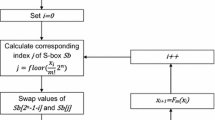
The computational graph for the encryption process of the proposed S-box.





Similar content being viewed by others
References
National Bureau of Standards: Data Encryption Standard, US. Department of Commerce, FIPS pub.46, January 1977.
Shimizu, A., Shiraishi, A., & Miyaguchi, S. (1987). Fast data encryption algorithm FEAL, advances in cryptology, proceedings of EUROCRYPT’87, Lecture Notes in Computer Science 304: 267–278.
Xusick, T., & Wood, W. (1990). The REDOC-cryptosystem, advances in cryptology, proceedings of CRYPTO’SO, Lecture Notes in Computer Science 526: 545–563.
Brown, L., Pieprzyk, J., & Seberry, J.: LOKI—A cryptographic primitive for authentication and secrecy applications, advances in cryptology, proceedings of AUSCRYPT’SO, Lecture Notes in Computer Science 453: 229–236.
Merkl, R. (1990). Fast software encryption functions, advances in cryptology, proceedings of CRYPTO’SO, Lecture Notes in Computer Science 526: 476–501.
Shannon, C. (1949). Communication theory of secrecy system. Bell Systems Technical Journal, 28, 656–715.
Biham, E., & Shamir, A. (1991). Differential cryptanalysis of DES-like cryptosystems. Journal of Cryptology, 4(1), 3–72.
Pieprzyk, J., & Finkelstein, G. (1988). Towards effective nonlinear cryptosystem design. IEEE Proceedings, Part E: Computers and Digital Techniques, 135, 325–335.
Adams, C., & Tavares, S. (1989). Good S-boxes Are easy to find, advances in cryptology, proceedings of CRYPT0’89, Lecture Notes in Computer Science pp. 612–6115.
Detombe, J., & Tavares, S. (1992). Constructing large cryptographically strong S-boxes, advances in cryptology, proceedings of CRYPTO’92, Lecture Notes in Computer Science.
Hussain, I., Azam, N. A., & Shah, T. (2014). Stego optical encryption based on chaotic S-box transformation. Optics & Laser Technology, 61, 50–56.
Hussain, I., Shah, T., & Gondal, M. A. (2013). Application of S-box and chaotic map for image encryption. Mathematical and Computer Modelling, 57(9–10), 2576–2579.
Hussain, I. (2013). A novel approach of audio watermarking based on S-box transformation. Mathematical and Computer Modelling, 57(3–4), 963–969.
Hussain, I., Shah, T., Gondal, M. A., & Mahmood, H. (2013). A novel method for designing nonlinear component for block cipher based on TD-ERCS chaotic sequence. Nonlinear Dynamics, 73, 633–637.
Hussain, I., Shah, T., Gondal, M. A., & Mahmood, H. (2013). A novel image encryption algorithm based on chaotic maps and GF(2^8) exponent transformation. Nonlinear Dynamics, 72, 399–406.
Anees, A., Siddiqui, A. M., Ahmed, J., & Hussain, I. (2014). A technique for digital steganography using chaotic maps. Nonlinear Dynamics, 75, 807–816.
Jamal, S. S., Shah, T., & Hussain, I. (2013). An efficient scheme for digital watermarking using chaotic map. Nonlinear Dynamics, 73, 1469–1474.
Hussain, I., Shah, T., Gondal, M. A., & Mahmood, H. (2013). An efficient approach for the construction of LFT S-boxes using chaotic logistic map. Nonlinear Dynamics, 71, 133–140.
Hussain, I., Shah, T., Gondal, M. A., & Mahmood, H. (2013). Efficient method for designing chaotic S-boxes based on generalized baker’s map and TDERC chaotic sequence. Nonlinear Dynamics, 74, 271–275.
Hussain, I., & Gondal, MA. An extended image encryption using chaotic coupled map and S-box transformation, Nonlinear Dynamics, doi:10.1007/s11071-013-1214-z.
Hussain, I., Shah, T., & Gondal, M. A. (2013). A group theoretic approach to construct cryptographically strong substitution boxes. Neural Comput & Applications, 23, 97–104.
Hussain, I., Shah, T., & Mahmood, H. (2013). A projective general linear group based algorithm for the construction of substitution box for block ciphers. Neural Comput & Applications, 22, 1085–1093.
Hussain, I., & Shah, T. (2013). Literature survey on nonlinear components and chaotic nonlinear components of block ciphers. Nonlinear Dynamics, 74, 869–904.
Anees, A., Khan, W. A., Gondal, M. A., & Hussain, I. (2013). Application of mean of absolute deviation method for the selection of best nonlinear component based on video encryption. Z. Naturforsch, 68a, 567–572.
Shah, T., Qamar, A., & Hussain, I. (2013). Substitution box on maximal cyclic subgroup of units of a galois ring. Z. Naturforsch, 68a, 479–482.
Gondal, M. A., & Anees, A. (2013). Analysis of optimized signal processing algorithms for smart antenna systems. Neural Computing and Applications, 23(3–4), 1083–1087.
Anees, A., Siddiqui, A. M., & Ahmed, F. (2014). Chaotic substitution for highly autocorrelated data in encryption algorithms. Communications in Nonlinear Science and Numerical Simulation, 19(9), 3106–3118.
Ahmed, F., Anees, A., & Siyal, M. Y. (2014). A noise channel tolerant image encryption scheme. Wireless Personal Communications,. doi:10.1007/s11277-014-1667-5.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gondal, M.A., Abdul Raheem & Hussain, I. A Scheme for Obtaining Secure S-Boxes Based on Chaotic Baker’s Map. 3D Res 5, 17 (2014). https://doi.org/10.1007/s13319-014-0017-4
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13319-014-0017-4