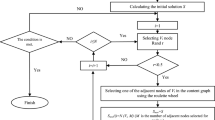
Abstract
In recent decades, the world of social media became the most popular. Social media have transformed the world. The rapid and large choice of these technologies is transforming how we find communities, how we get information from the news. According to this growth of social media, cyber terrorism has become an international issue that threatens world peace. Cyberterrorism is becoming more famous on social media now. While the Internet grows more pervasive in every area interested users or organizations can use the anonymity provided by cyberspace to terrorize citizens, communities, specific groups, and entire countries, without the internal threat of capture, damage, or death to the criminal that being physically existing would begin. Besides, Social network analysis plays a key research field for detecting different groups in a cyber-terrorist network. Many researchers are interested to find these communities, the managers, and the influencers which present a predictive way to protect users of social media networks. Then, the enormous evolution of terrorist communities over time presents a big problem to analyze and detect them. In this article, we introduce a new method for communities detection according to the network of contact, the publications, and their evolution based on Twitter as a social network. Also, we find the managers and the influencers in terrorist communities using swarm techniques. Our proposed method object is to optimize our proposed objective function to have a coherent partitioning inspired by the artificial bees comportment and using the data warehouse to save data in every evolution over time. Finally, we illustrate the performance of our proposed method by an experimental study on the real and artificial network and with a comparative study with the same related recent works. We test the performance of our approach by applying different quality functions on the terrorist communities detected.

















Similar content being viewed by others
Notes
BCTTC is an acronym for Bee colonies for Tracking Terrorist Communities
References
Brandes U, Gaertler M (2003) Experiments on graph clustering algorithms. LNCS 14(1):51–65
Carley KM, Lee J-S, Krackhardt D (2002) Destabilizing networks. Connections 24(3):79–92
Chaabani Y, Akaichi J (2016) Bees colonies for meaningfull communities detection in social medias network. In: 2016 International IEEE conferences on ubiquitous intelligence and computing, advanced and trusted computing, scalable computing and communications, cloud and big data computing, internet of people, and smart world congress (UIC-ATC-ScalCom-CBDCom-IoP-SmartWorld)
Chaabani Y, Akaichi J (2017) Meaningful communities detection in medias network. Soc Netw Anal Min 7(1):11
Chaurasia N, Dhakar M, Tiwari A, Gupta RK (2012) A survey on terrorist network mining: current trends and opportunities. Int J Comput Sci Eng Surv 3(4):59
Dutta S, Ghatak S, Roy M, Ghosh S, Das AK (2015) A graph based clustering technique for tweet summarization. pp 1–6
Edith W, Carleton R, Davies G (2014) Discovering bin-laden’s replacement in al-qaeda, using social network analysis: a methodological investigation. Perspect Terror 8(1):57–73
Everett MG, Borgatti SP (1999) The centrality of groups and classes. J Math Sociol 23(3):181–201
Everton SF (2009) Network topography, key players and terrorist networks
Everton SF, Cunningham D (2013) Detecting significant changes in dark networks. Behav Sci Terror Polit Aggress 5(2):94–114
Everton SF, Cunningham D (2013) Terrorist network adaptation to a changing environment. Crime and networks pp. 287–308
Ferrara E, De Meo P, Catanese S, Fiumara G (2014) Detecting criminal organizations in mobile phone networks. Exp Syst Appl 41(13):5733–5750
Fortunato San Benchmark graphs to test community detection algorithms. http://sites.google.com/site/santofortunato/inthepress2
Gialampoukidis I, Kalpakis G, Tsikrika T, Papadopoulos S, Stefanos V, and Ioannis K (2017) Detection of terrorism-related twitter communities using centrality scores. pp 21–25
Goddard C (2011) Semantic analysis: a practical introduction. Oxford University Press, Oxford
Gulbahce N, Lehmann S (2008) The art of community detection. BioEssays 30(10):934–938
In: Actes du 8e symposium international sur la recherche et la technologie du commandement et du contrôle
Jennifer X, Chen H (2005) Criminal network analysis and visualization. Commun ACM 48(6):100–107
Karthika S, Bose S (2011) Analyzing various social networking approaches for covert networks. Springer, Berlin, pp 558–566
Kim Y, Son S-W, Jeong H (2010) Finding communities in directed networks. Phys Rev E 81:016103
Knoke D (2015) Emerging trends in social network analysis of terrorism and counterterrorism. Emerging trends in the social and behavioral sciences: an interdisciplinary, searchable, and linkable. Resource
Koschade S (2006) A social network analysis of jemaah islamiyah: the applications to counterterrorism and intelligence. Stud Conflict Terror 29(6):559–575
Krebs VE (2002) Mapping networks of terrorist cells. Connections 24(3):43–52
Lancichinetti A, Fortunato S, Radicchi F (2008) Benchmark graphs for testing community detection algorithms. Phys Rev E 78(4):046110
Liben-Nowell D, Kleinberg J (2007) The link-prediction problem for social networks. J Am Soc Inf Sci Technol 58(7):1019–1031
Lucic P (2002) Modeling transportation problems using concepts of swarm intelligence and soft computing. Virginia Tech, Blacksburg (PhD thesis)
Medina RM (2014) Social network analysis: a case study of the Islamist terrorist network. Sec J 27(1):97–121
Memon N, Larsen HL (2006) Practical algorithms for destabilizing terrorist networks. Springer, Berlin, pp 389–400
Mullins S, Dolnik A (2010) An exploratory, dynamic application of social network analysis for modelling the development of islamist terror-cells in the west. Behav Sci Terror Polit Aggress 2(1):3–29
Nizamani S, Memon N (2014) Analyzing news summaries for identification of terrorism incident type. Educ Res Int 3(4):10
Pang B, Lee L et al (2008) Opinion mining and sentiment analysis. Foundations and Trends. Information Retrieval 2(1–2):1–135
Ressler S (2006) Social network analysis as an approach to combat terrorism: past, present, and future research. Homeland Security Affairs 2(2)
Romdhane LB, Chaabani Y, Zardi H et al (2013) A robust ant colony optimization-based algorithm for community mining in large scale oriented social graphs. Exp Syst Appl 40(14):5709–5718
Sarvari H, Abozinadah E, Mbaziira A, Mccoy D (2014) Constructing and analyzing criminal networks. pp 84–91
The elements of statistical learning: data mining, inference, and prediction. J R Stat Soc Ser A, 173:693–694
Wiil UK, Gniadek J, Memon N (2010) Crimefighter assistant: a knowledge management tool for terrorist network analysis. In: international conference on knowledge management and information sharing institute for systems and technologies of information, control and communication, pp. 15–24
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chaabani, Y., Akaichi, J. Bees colonies for terrorist communities evolution detection. Soc. Netw. Anal. Min. 12, 8 (2022). https://doi.org/10.1007/s13278-021-00835-y
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13278-021-00835-y