Abstract
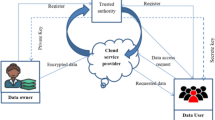
Secure storage of patients’ medical records (PMR) in a cloud-centric Internet of medical Things and sharing it with the authorized doctors require an efficient access control scheme capable of enforcing privacy, confidentiality and integrity requirements. In this paper we propose an authentication and key agreement scheme for cloud-centric healthcare systems involving two classes of patients; patients with wearable devices and patients without wearable devices. It stores the patients’ medical records (PMRs) into a medical cloud and enforces secure access to the PMRs among the authorized doctors. The scheme enforces integrity and confidentiality, terminates the patient-physician relationship through a time-based PMR upload and download validation procedure. To achieve this, we develop elliptic curve cryptography-based, time-based short group signature, and authentication procedures. A formal analysis based on the random-oracle model and informal analysis based on the features of the scheme is presented to show the security and efficiency of the scheme. The performance and security analyses indicate that the proposed scheme has overcome most of the weaknesses identified in the prior schemes at low computation and communication costs.








Similar content being viewed by others
Data availability
Not applicable.
Code availability
Not applicable.
References
Barua M, Lu R, Shen X (2013) Sps: Secure personal health information sharing with patient-centric access control in cloud computing, pp 647–652
Canetti R, Krawczyk H (2001) Analysis of key-exchange protocols and their use for building secure channels. Springer-Verlag, pp 453–474
Chiou SY, Ying Z, Liu J (2016) Improvement of a privacy authentication scheme based on cloud for medical environment. J Med Syst 40(4):1–15
Deebak BD, Al-Turjman F (2020) Smart mutual authentication protocol for cloud based medical healthcare systems using Internet of medical Things. IEEE J Selected Areas Commun 1(1):727–731
Deebak BD, Al-Turjman F, Aloqaily M, Alfandi O (2019) An authentic-based privacy preservation protocol for smart e-healthcare systems in IoT. IEEE Access 7:135632–135649. https://doi.org/10.1109/ACCESS.2019.2941575
Edemacu K, Jang B, Kim JW (2020) Collaborative ehealth privacy and security: an access control with attribute revocation based on obdd access structure. IEEE J Biomed Health Info 1(1):1–13
Garg N, Wazid M, Ashok KD, Devesh PS, Rodrigues JJPC, Park Y (2020) Bakmp-iomt: design of blockchain enabled authenticated key management protocol for internet of medical things deployment. IEEE Access 8:95956–95977. https://doi.org/10.1109/ACCESS.2020.2995917
Guo J, Siqi L, Chunxiang G, Xi C, Fushan W (2020) Security analysis and design of authentication key agreement protocol in medical internet of things. In: 2020 International Conference on Networking and Network Applications (NaNA), pp 233–240
Guo L, Zhang C, Sun J, Fang Y (2014) A privacy-preserving attribute-based authentication system for mobile health networks. IEEE Trans Mobile Comput 13(9):1927–1941
Huang H, Gong T, Ye N, Wang R, Dou Y (2017a) Private and secured medical data transmission and analysis for wireless sensing healthcare system. IEEE Trans Indus Info 13(3):1227–1237
Huang Q, Wang L, Yang Y (2017b) Secure and privacy-preserving data sharing and collaboration in mobile healthcare social networks of smart cities. J Security Commun Netw 1–12
Hur J, Noh D (2011) Attribute-based access control with efficient revocation in data outsourcing systems. IEEE Trans Parallel Distrib Syst 22(7):1214–1221
Ionescu B, Gadea C, Solomon B, Ionescu D, Stoicu-Tivadar V, and Trifan M (2015) A cloud based real-time collaborative platform for ehealth. In MIE, pp 919–923
Khemissa H, Tandjaoui D (2015) A lightweight authentication scheme for e-health applications in the context of internet of things. In 2015 9th International Conference on Next Generation Mobile Applications, Services and Technologies, pp 90–95
Koe V, Sandor A, Lin Y, Li X (2019) Efficient decentralized multi-authority attribute based encryption for mobile cloud data storage. J Netw Comput Appl 129:25–36
Li M, Yuand S, Zheng Y, Ren K, Lou W (2013) Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans Parallel Distrib Syst 24(1):131–143
Li X, Wen Q, Li W, Zhang H, Jin Z (2014) Secure privacy-preserving biometric authentication scheme for telecare medicine information systems. J Med Syst 38(11):139–201
Li W, Liu BM, Liu D, Liu RP, Wang P, Luo S, Ni W (2019) Unified fine-grained access control for personal health records in cloud computing. IEEE J Biomed Health Info 23(3):1278–1289
Li X, Niu J, Kumari S, Wu F, Choo Kim-Kwang R (2018) A robust biometrics based three-factor authentication scheme for global mobility networks in smart city. Future Generation Computer Systems, 83:607–618. ISSN 0167-739X. https://doi.org/10.1016/j.future.2017.04.012 URL https://www.sciencedirect.com/science/article/pii/S0167739X1730585X
Liu W, Liu X, Liu J, Wu Q, Zhang J, Li Y (2015) Auditing and revocation enabled role-based access control over outsourced private EHRs. In: 2015 IEEE 17th international conference on high performance computing and communications, 2015 IEEE 7th international symposium on cyberspace safety and security, and 2015 IEEE 12th international conference on embedded software and systems, pp 336–341. https://doi.org/10.1109/HPCC-CSS-ICESS.2015.10
Li W, Zhang H, Li X, Wen Q, Jin Z (2014) Secure privacy-preserving biometric authentication scheme for telecare medicine information systems. J Med Syst 38(11):139–201
Minahil Ayub MF, Mahmood K, Kumari S, Sangaiah AK (2021) Lightweight authentication protocol for e-health clouds in IoT-based applications through 5g technology. Dig Commun Netw 7(2):235–244. https://doi.org/10.1016/j.dcan.2020.06.003
Olakanmi O (2018) A lightweight security and privacy-aware routing scheme for energy-constraint multi-hop wireless sensor networks. Int J Inf Comput Security 15(2–3):231–253
Olakanmi O, Dada A (2018) Felas: fog enhanced look ahead secure framework with separable data aggregation scheme for efficient information management in internet of things networks. J Appl Security Res 14(4):468–488
Olakanmi O, Odeyemi K (2021) Compromise-resilient anonymous mutual authentication scheme for n by m-times ubiquitous mobile cloud computing services. Comput Security, 108:102369. ISSN 0167-4048. https://doi.org/10.1016/j.cose.2021.102369. URL https://www.sciencedirect.com/science/article/pii/S0167404821001930
Olakanmi O, Odeyemi KF (2020) A fog enhanced expressible access control scheme with secure services delegation among carers in e-health systems. Internet of Things, pp 727–731
Olakanmi O, Odeyemi K (2021a) Eacs: expressible access control scheme for secure services and data delegation in e-health system. Inf Security J: A Global Pers https://doi.org/10.1109/TCC.2020.3029878
Olakanmi O, Odeyemi K (2021b) Faster and efficient cloud-server-aided data de-duplication scheme with an authenticated key agreement for industrial internet-of-things. Internet of Things, 14
Olakanmi O, Odeyemi K (2021) Versa: verifiable and secure approach with provable security for fine-grained data distribution in scalable internet of things networks. Int J Inf Security Privacy (IJISP). https://doi.org/10.4018/IJISP.2021070105
Olakanmi O, Samuel O (2018) Mashed: security and privacy-aware mutual authentication scheme for heterogeneous and distributed mobile cloud computing services. J Inf Security J: A Global Persp 27(5–6):276–291
Raeve PD (2019) The world of cloud-based services: storing health data in the cloud. https://www.healtheuropa.eu/cloud-based-services-storing-health-data-in-the-cloud/93053/
Ruj S, Stojmenovic M, Nayak A (2014) Decentralized access control with anonymous authentication of data stored in clouds. IEEE Trans Parallel Distrib Syst 25(2):384–394. https://doi.org/10.1109/TPDS.2013.38
Xiong L, Li F, He M, Liu Z, Peng T (2020) An efficient privacy-aware authentication scheme with hierarchical access control for mobile cloud computing services. IEEE Trans Cloud Comput https://doi.org/10.1109/TCC.2020.3029878
Xu ZX, Cheng Xu, LW, Jianbo X, Chen H (2019) A lightweight mutual authentication and key agreement scheme for medical internet of things. IEEE Access 7:53922–53931. https://doi.org/10.1109/ACCESS.2019.2912870
Yeh L, Chiang P, Tsai Y, Huang J (2018) Cloud-based fine-grained health information access control framework for lightweight IoT devices with dynamic auditing and attribute revocation. IEEE Trans Cloud Comput 6(2):532–544
Zhong H, Zhu W, Xu Y, and Cui J (2017) Multi-authority attribute-based encryption access control scheme with policy hidden for cloud storage.133, pp 157–165
Funding
There is no funding sources.
Author information
Authors and Affiliations
Contributions
The two authors contribute equally.
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest on this article.
Ethical approval
Not applicale.
Informed consent
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Olakanmi, O.O., Odeyemi, K.O. Expressible access control scheme for data sharing and collaboration in cloud-centric Internet of medical Things system. J Ambient Intell Human Comput 14, 7189–7205 (2023). https://doi.org/10.1007/s12652-021-03572-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-021-03572-4