Abstract
Nowadays, multimedia security is a major issue. Images, video, audio, and text files lose credibility in most times, because they face several attacks related to illegal distribution, duplication, and manipulation of the information conveyed by them. Digital watermarking is an important tool for protecting digital content. This paper introduces an efficient hybrid digital image watermarking scheme. It consists of two stages of Singular Value Decomposition (SVD). The first one is the embedding stage, which is performed by using SVD followed by block-based SVD (B-SVD). The second stage is the extraction stage, which depends on the SVD on the whole image and then B-SVD to get the original watermarks. In this scheme, the watermarking requirements are satisfied, while capacity is increased. Furthermore, watermark detection, robustness, and security are improved. The performance of the proposed scheme is evaluated by the correlation coefficient Cr between the original and extracted watermarks, and the Peak Signal-to-Noise Ratio (PSNR) between the original and watermarked images. The experimental results demonstrate that the proposed scheme has a good performance, where Cr reaches 0.9975 and PSNR reaches 45.8605. It is more secure than the previous schemes, when subjected to attacks. In addition, the proposed scheme is compared to the most recent schemes, revealing its superiority.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
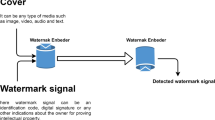
Today, the Internet is the most important and easiest way to connect people all over the world. It allows users to communicate and share multimedia content, such as text, images, audio, and video, with low cost and high quality. However, the most important problem that arises is how to protect critical data during transmission from illegal use [1, 2]. Protecting confidential information is a moral and legal requirement. Data hiding is a method for protecting information by hiding it in a multimedia object for the authentication purpose. This process is carried out in such a way that the embedded data is not visible to the naked eye, but it is easily detected by a detector. Data hiding has two main types: digital watermarking and steganography [3, 4]. The insertion of a part of information into the multimedia content, where it is not visible to the human eye but can be detected with a detector, is called digital watermarking. Figure 1 introduces the watermarking framework, which consists of the embedding and detection processes. It is suitable for several applications such as fingerprinting, copyright protection, and content authentication, because it has a very important feature that the content is inseparable from the watermark [5, 6].
Digital watermarking techniques include embedding of a watermark in a multimedia content to ensure authenticity and protect copyright holders from unauthorized data alteration [7]. Consequently, it is vital to specify the prerequisites or properties of a watermarking scheme. The specifications for watermarking schemes are shown in Fig. 2.
These requirements guarantee the effectiveness of watermarking schemes. The ideal characteristics of digital watermarking include imperceptibility, robustness, capacity, and security [8, 9].
-
1.
Imperceptibility: Imperceptibility is crucial, when assessing the watermarking scheme effectiveness. It is reflected in faithfulness and invisibility. The watermarked image in this instance needs to look exactly like the original image [10].
-
2.
Robustness: Robustness is the property that a watermark must have to be detectable after various typical signal-processing operations used in digital image watermarking systems have been applied. Among them are spatial filtering, color mapping, scanning and printing, compression, scaling, translation, and rotation [10].
-
3.
Capacity: The amount of embedded data in the host signal should be as large as possible.
-
4.
Security: The authorized person is the only one, who can detect the watermark.
Consequently, Fig. 2 summarizes the general requirements for a digital watermarking scheme [9].
The motivation of this paper is introducing an efficient image watermarking scheme for different applications. This scheme depends on two cascaded stages of the SVD and B-SVD. It achieves a trade-off between the watermarking requirements, where embedding of more than one watermark increases capacity, robustness, and imperceptibility. Furthermore, the security is improved through the scheme complexity.
The paper organization is as follows. Section "Traditional singular value decomposition (SVD) watermarking" gives an explanation of the traditional SVD watermarking with the method of Liu. Section "The block-based SVD (B-SVD) watermarking algorithm" presents the B-SVD watermarking algorithm. Section "Obtain the SVs of each (Swi matrix) by applying SVD on each Di matrix." presents an explanation of the proposed watermarking scheme. Section "The watermarked blocks in the spatial domain will be built by using the SVs of each Di matrix (Swi matrix)." shows the experimental results. Finally, Section 6 provides the conclusion.
Traditional singular value decomposition (SVD) watermarking
In the traditional method of Liu for SVD watermarking, a matrix is decomposed into three matrices. A matrix B can be decomposed into a product of three matrices as follows [12]:
where X and Y are orthogonal matrices, such that XT X = I, and YT Y = I, and I is an identity matrix. S is a diagonal matrix, where its diagonal elements are the singular values of B.
From the perspective of image processing, the traditional SVD method of Liu is a mathematical technique with the following main properties:
-
(a)
Image Singular Values (SVs) have good stability, which means that even if a small change is made to an image, its SVs do not change noticeably, making the method resistant to various attacks.
-
(b)
The image algebric properties can be represented by its SVs.
Using these properties of the SVs of an image, the watermark can be settled into this matrix without great variations in the watermarked image. Liu et al. [9] introduced a watermarking algorithm based on the spatial SVD. Recently, watermarking schemes based on the SVD have gained popularity due to their simplicity of implementation and the attractive mathematical features of the SVD.
Figure 3 presents the traditional method of Liu et al. [13], and the steps of the watermark embedding process are explained as follows:
The original image (B matrix) is decomposed with the SVD.
The matrix D can be obtained by adding the watermark (W matrix) to the SVs of the original matrix.
The new modified matrix (D) is decomposed with SVD.
By knowing the obtained matrix (Sw), the watermarked image can be obtained.
With Xw, S, and Yw matrices and the potentially distorted image Bw*, the corrupted watermark is extracted from the potentially-corrupted watermarked image, and it is presented as follows:
-
1.
The corrupted watermarked image (Bw* matrix) is decomposed with SVD.
-
2.
By knowing Xw and YwT, the matrix D* can be obtained.
-
3.
Using the D* and S matrices, the watermark is obtained.
$${\mathbf{W}}^{*} = \, \left( {{\mathbf{D}}^{*} - {\mathbf{S}}} \right) \, /K$$(8)where K is the watermark gain and the corruption caused by the attacks is denoted by the symbol *.
Block-based SVD (B-SVD) watermarking
To give the chance for embedding of more watermarks to override attacks, the B-SVD watermarking is used. The original image is divided into non-overlapping blocks before embedding the watermark in the SVs of each block, separately [14, 15].
Watermark embedding
The steps of B-SVD watermarking are presented as follows. First, the original image (G matrix) is segmented into several blocks, none of which overlapping with others. The new matrices are obtained by inserting the watermark into the SVs (S matrix) of each block. To get the S matrices of the watermarked blocks, we apply an SVD to each of these new matrices. The watermarked image Gw is built in the spatial domain. By rearranging the blocks again into one matrix of the same dimensions as the original image, the watermarked image is obtained.
The steps of the embedding process are explained as follows [14]:
-
1.
The original image (G matrix) is divided into non-overlapping blocks.
-
2.
To obtain the SVs of the Si matrix of each block, the SVD is performed on each block Ci matrix, where i = 1, 2, 3…, N, and N is the number of blocks.
-
3.
The watermark image (W matrix) is added to the S matrix of each block, giving the new matrices Di.
$${\mathbf{D}}_{{{i}}} = {\mathbf{S}}_{{{i}}} + K{\mathbf{W}}$$(10)
-
4.
The SVs of each (Swi matrix) are obtained by applying SVD on each Di matrix.
$${\mathbf{D}}_{{{i}}} = {\mathbf{X}}_{{{{wi}}}} {\mathbf{S}}_{{{{wi}}}}$$(11)
-
5.
The watermarked blocks in the spatial domain are built using the SVs of each Di matrix (Swi matrix).
$${\mathbf{C}}_{{{{wi}}}} = {\mathbf{X}}_{{{i}}} {\mathbf{S}}_{{{{wi}}}} {\mathbf{Y}}_{{{i}}}^{{{T}}}$$(12)
-
6.
The watermarked image in the time domain (Gw matrix) is obtained by combining the watermarked blocks back into a single matrix.
Watermark detection
To get the watermark that may be corrupted, by knowing the Xwi, Ywi, Si, matrices, and the corrupted watermarked image G*w, we apply the following steps [15].
-
1.
Before applying the SVD, the corrupted watermarked image (G*w matrix) is divided into the same-size blocks as in the embedding process.
-
2.
The SVs of each one (S*wi matrix) are obtained and the SVD is applied on each possibly-corrupted watermarked block (C*wi matrix).
-
3.
Using Xwi, Ywi, and S*wi matrices, the matrices that contain the watermark are obtained
$${\mathbf{D}}_{{{i}}}^{*} = {\mathbf{X}}_{{{{wi}}}} {\mathbf{S}}^{*}_{{{{wi}}}} {\mathbf{Y}}_{{{{wi}}}}^{{{T}}}$$(14)$$\left( {{\mathbf{D}}^{*}_{{{i}}} - {\mathbf{S}}_{{{i}}} } \right) \, /K = {\mathbf{W}}^{*}_{{{i}}}$$(15)
The proposed hybrid digital image watermarking scheme
The proposed scheme depends on two cascaded stages of the SVD and B-SVD. The suggested scheme aims to fulfill the following watermarking requirements:
-
1.
Improving the level of security through the scheme complexity.
-
2.
Maintaining imperceptibility by increasing the capacity of embedded information without affecting the quality of the original image.
-
3.
Enhancement of the correlation coefficient (Cr) to increase watermarking robustness.
-
4.
Increasing Peak Signal-to-Noise Ratio (PSNR) of the watermarked image to enhance its fidelity by ensuring that the watermark is not noticeable to the human eye.
Basic idea
The proposed watermarking scheme consists of embedding and (detection/extraction) processes. Figure 4 shows the watermark embedding process, which consists of two stages. In the first stage, watermark 1 is embedded into the original image using the B-SVD algorithm to obtain the primary watermarked image. Then, watermark 2 is embedded into the primary watermarked image using the SVD watermarking algorithm in the second stage to obtain the final watermarked image. Figure 5 shows the detection/extraction process, which consists of two stages: first, the extracted watermark 1 is detected and extracted from the final watermarked image. Then, the extracted watermark 2 is extracted from the primary watermarked image in the second stage.
The scheme description
Embedding process
In the embedding process, we apply the B-SVD and the SVD algorithms, respectively as shown in Fig. 6.
-
1.
First, the original image (A matrix) is divided into non-overlapping blocks with the same size. The size of the block is chosen to be 16 × 16 as indicated in [19]. Then, the SVD is applied on each block (Ci matrix) for obtaining the SVs (Si matrix) of each block, where i = 1, 2, 3..., N and N is the number of blocks.
$${\mathbf{C}}_{{{{i }} }} = {\mathbf{X}}_{{{i}}} {\mathbf{S}}_{{{i}}} {\mathbf{Y}}_{{{i}}}^{{{T}}}$$(16) -
2.
The watermark image (W1 matrix) is added to each block S matrix.
$${\mathbf{D}}_{{{i}}} = {\mathbf{S}}_{{{i}}} + K{\mathbf{W}}_{{1}}$$(17) -
3.
The SVD is applied on each Di matrix to obtain the SVs of each (Swi matrix).
$${\mathbf{D}}_{{{i}}} = {\mathbf{X}}_{{{{wi}}}} {\mathbf{S}}_{{{{wi}}}} {\mathbf{Y}}^{{{T}}}_{{{{wi}}}}$$(18) -
4.
The watermarked blocks in the spatial domain are built by using the SVs of each Di matrix (Swi matrix).
$${\mathbf{C}}_{{{{wi}}}} = {\mathbf{X}}_{{{i}}} {\mathbf{S}}_{{{{wi}}}} {\mathbf{Y}}_{{{i}}}^{{{T}}}$$(19) -
5.
The watermarked image in the time domain (Awp matrix) is built by combining the watermarked blocks back into one matrix.
From the previous steps, we get the primary watermarked image which will be the input for the second stage.
-
6.
The SVD is applied on the primary watermarked image.
-
7.
To obtain the matrix D, the watermark (W2 matrix) is added to the SVs of the primary watermarked matrix, then the SVD is applied
$${\mathbf{D}} = {\mathbf{S}}_{{{{wp}}}} + K{\mathbf{W}}_{{2}}$$(21)$${\mathbf{D}} = {\mathbf{X}}_{{{w}}} {\mathbf{S}}_{{{{wp}}}} {\mathbf{Y}}^{{{T}}}$$(22)
-
8.
Using the modified matrix (Swp), the final watermarked image (Awf) is obtained.
$${\mathbf{A}}_{{{{wf}}}} = {\mathbf{XS}}_{{{{wp}}}} {\mathbf{Y}}^{{{T}}}$$(23)
(Extraction/Detection) Process
Figure 7 shows the watermarking (extraction/detection) process, which comprises application of the SVD and B-SVD watermarking algorithms, respectively. The new extraction process consists of several steps as follows:
The SVD is applied on the distorted final watermarked image (A*wf matrix).
The matrix which contains the watermark is computed.
Using the matrix D* and Swf, we get the watermark 2, which may be corrupted.
The corruption due to attacks will be referred to as *.
To get the watermark that may be corrupted, by knowing Xwi, Ywi, Si matrices, and the possibly corrupted primary watermarked image A*wp, the steps below are applied.
The corrupted primary watermarked image (A*wp) is divided into blocks that have the same size as that in the embedding process.
The SVs of each matrix (S*wpi) are obtained by applying SVD on each corrupted watermarked block (C*wpi matrix) to get
The Xwi, Ywi, and Swi, matrices are used to obtain the Di* matrices that contain the watermark.
From the Di* matrices, the corrupted watermark 1 (W1i*) is extracted.
Experimental results
Performance metrics
The performance evaluation for most work in watermarking techniques depends mainly on two image quality metrics [16, 17]:
-
1.
Imperceptibility Quality Metric.
PSNR is a metric used to describe the quality of a watermarked image. A large PSNR is desirable. The PSNR should be infinite, but this is not possible for a watermarked image. The mathematical representation of the PSNR is given as:
where: A (x, y) is the original image and Aw (x, y) is the watermarked image.
-
2.
Robustness Quality Metric:
The difference between the extracted and the original watermarks is measured by the correlation coefficient (Cr), which is a metric of resilience. The mathematical expression of the Cr is shown below. The stronger the robustness, the closer the Cr value to one [17].
where W and \(\varvec{\rm{W}}^{\prime} \) are the original and extracted watermarks, respectively.
Experimental result analysis
The performance of the proposed hybrid scheme is assessed in this section, along with that of the Liu et al. for a single watermark [13], the DWT-SVD with fused watermark [18], and the hybrid digital image watermarking scheme (SVD-BSVD).
The proposed hybrid digital image watermarking scheme (BSVD-SVD) is simulated using MATLAB on an Intel(R) Core(TM) i3 CPU with 2GB RAM, and several simulations are carried out. The used parameters in the simulations are summarized in Table 1.
To evaluate and illustrate the performance of the proposed algorithm, several test experiments are carried out for different original images with and without attacks. In each test, both the Cr of the extracted watermark and PSNR of the watermarked images are measured.
Figures 8 and 9 show the variation of Cr and PSNR with the gain factor of the watermark K. The figures indicate that the optimum value of K equals 0.01, where the best values of Cr and PSNR are obtained. If the K is lower than 0.01, the Cr will decrease and the watermark cannot be successfully extracted. If K is larger than 0.01, PSNR will decrease and the original image will be distorted.
Figure 10 shows the outcome of the Liu method with this sequence, 10 (a) is the original image, 10 (b) is the watermark of the same size as the original image, 10 (c) is the watermarked image, and 10 (d) is the extracted watermark without attacks. The correlation coefficient Cr between the extracted watermark and the original one is 0.8543 in the case of using a single watermark.
The proposed algorithm BSVD-SVD simulation results in the embedding process and extraction process in the absence of attacks are shown in Fig 11 as follows: 11(a) is the original image, 11(b) is the watermark added to each block, 11(c) is the primary watermarked image using B-SVD, which gives PSNR=45.8605 and 11(d) is the final watermarked image using BSVD-SVD, which gives PSNR=45.5193. On the other hand, the extraction process has been completed. The extracted watermark1 from the final watermarked image by SVD has a Cr2 equal to 0.0121, while the extracted watermark 1 (from BSVD) has a Crmax of 0.9975, as shown in Fig. 11e,f, g. The proposed scheme gives a high correlation coefficient between the original watermark and the extracted watermark, closer to 1. According to the results, the proposed scheme extracts watermarks perfectly in the absence of attacks, increasing the capacity of embedded information.
a Original image, Size = 63.5 KB. b Watermark image, Size = 1.3 KB with block size (16 × 16). c Primary Watermarked image, PSNR 1 = 45.8605. d Final watermarked image, PSNR 2 = 45.5193. e Extracted watermark1 (from the final watermarked image by SVD), Cr1 = 0.0121 f Extracted watermark 2 (From stage 2 by using BSVD). g The Extracted watermark 2 (From stage 2 by using BSVD) which gives max correlation (Cr2max = 0.9975), after magnification
The high fidelity of the proposed scheme is noticed, where there is no visual difference between the original image and the watermarked image. An improved level of security is achieved by increasing the scheme complexity. The proposed scheme is also tested on different original images, as shown in Fig. 12. From the behavior of the proposed schemes it is proved that it is not dependent on the type of image used as the original image. The correlation coefficients for extracted watermarks are high and close to one in the absence of attacks. This means that the proposed scheme works efficiently with different original images.
As shown in Figs. 13 and 14, the Liu method and the proposed scheme were tested in the presence of some attacks, such as cropping with 50%, Gaussian noise with zero mean and 0.01 variance, and blurring with the LPF window of size 3×3. Figs. 15 and 16 represent the extracted watermarks and their correlation coefficients between the original watermark and each extracted watermark for the method of Liu and the proposed scheme, respectively.
Table 2 gives the numerical values of correlation coefficient for different noise variances. The table indicates that there is a degradation in the correlation values with the increase in noise variance, in addition to the degradation in PSNR due to the noise. Table 3 indicates the effect of increasing the filter window in blurring attack on the Cr and PSNR. It is clear that increasing the filter window has a negative effect on the watermarking process. Rotation attack has a different effect on the watermarking process, where Cr and PSNR increase with rotation angle. The best values are obtained at 90 degree rotation (Table 4).
The same simulation is repeated on a reverse hybrid digital image watermarking scheme by reversing the stages of the proposed scheme (SVD-BSVD), and its results are shown in Figs. 17, 18 and 19. The results of this simulation reveal the superiority of the proposed hybrid digital image watermarking scheme (BSVD-SVD) over the reverse hybrid digital image watermarking scheme (SVD-BSVD). Tables 5 and 6 give a comparison study of the Cr and PSNR for the proposed scheme and other schemes for different attacks. In the presence of attacks such as low-pass filtering attack, Gaussian noise attack, and cropping attack, the proposed scheme proves its superiority over the other compared ones. Table 5 presents the Cr using SVD with only one watermark, hybrid DWT-SVD with a fused watermark, a reverse hybrid digital image watermarking scheme (SVD-BSVD), and the proposed scheme. The results show that the proposed scheme (BSVD-SVD) improves the Cr compared with other ones, where the value of Cr for the proposed scheme is higher than that for other ones. From these results, the proposed scheme proves its ability to extract watermarks perfectly compared to other ones (Fig. 19).
a Original image with Size = 63.5 KB. b Watermark image with Size (256 × 256) c Primary watermarked image by (SVD), PSNR 1 = 113.3409. d Watermark image with block size (16 × 16). e Final watermarked image by (BSVD) PSNR 2 = 45.1884. f Extracted watermark1 from the final watermarked image by (BSVD). g Extracted watermark 1 from stage 1 using BSVD which gives max correlation Cr1max = 0.9975 (f) Extracted watermark 2 (From stage 2 by using BSVD). h The Extracted watermark 2 from stage 2 by using SVD (Cr2 = 0.0030), after magnification
Table 6 presents the PSNR using SVD with only one watermark, hybrid DWT-SVD with a fused watermark, a reverse hybrid digital image watermarking scheme (SVD-BSVD), and the proposed scheme. The results show that the proposed scheme has a higher PSNR and a better chance of detecting watermarks, even in the presence of severe attacks, ensuring its fidelity. Table 7 gives the comparison of the processing time (sec) between the SVD with only one watermark and the proposed scheme. Despite increasing the processing time for the proposed scheme, this scheme improves the level of security by increasing the complexity of the system.
Conclusion
In this paper, an efficient image watermarking scheme has been presented. The proposed scheme is implemented through the SVD and B-SVD. The SVD is recognized as a robust watermarking algorithm by exploiting its stability characteristic. The proposed scheme is used to embed more than one watermark into the original image, which means a large capacity. The B-SVD implementation gives more chances to survive different attacks and achieve robust watermarking. The watermarks are embedded with a weight equal to 0.01 to preserve the original image quality and achieve imperceptibility. The complexity of the proposed scheme increases the security level. In addition, improving fidelity means achieving suitable values for PSNR, where there is no visual difference between the original image and the watermarked image. We have concluded that the proposed algorithm is superior to other methods, because it satisfies the watermarking requirement, but the complexity will increase.
References
S. Laura, “Cryptography Role in Information Security”, Proceedings of the 5th World Scientific and Engineering Academy and Society (WSEAS), international conference on Communications and information technology. 36–41 (2011)
C-S. Lu, “Multimedia Security: Steganography and Digital Watermarking for Protection of Intellectual Property”, Idea Group Publishing. (2005)
D. Mistry, Comparison of digital watermarking methods. Int J Comput Sci Eng. 02(09), 2905–2909 (2010)
L. Singh, A.K. Singh, P.K. Singh, Secure data hiding techniques: a survey. Multimed Tools and Appl. 79, 15901–15921 (2020)
M. Begum, M.S. Uddin, Digital image watermarking techniques: a review. Information 11, 110 (2020)
M. Miller, I. Cox, J. Linnartz, T. Kalker, “A review of watermarking principles and practices”, IEEE International Conference on image processing. 461–485 (1999)
H. Kayarka, S. Sanyal, A survey on various data hiding techniques and their comparative analysis. ACTA Technica Corviniensis. 5(3), 35–40 (2012)
A. Dixit, R. Dixit, A review on digital image watermarking techniques. Int. J. Image Graph. Signal Process 9, 56 (2017)
S. Kumar, B.K. Singh, M. Yadav, A recent survey on multimedia and database watermarking. Multimed. Tools Appl. 79, 20149–20197 (2020)
V. Singh, “Digital Watermarking: A Tutorial”, Cyber Journals: Multidisciplinary Journals in Science and Technology, Journal of Selected Areas in Telecommunications (JSAT). 10–21 (2011)
S. Lee, S. Jung, A survey of watermarking techniques applied to multimedia. IEEE Trans. Industr. Electron. 1, 272–277 (2001)
Z. hang, H. Wang, C. Zhou, (2017) A robust image watermarking scheme based on SVD in the Spatial Domain. 9, 45
R. Liu, T. tan, “An SVD-Based Watermarking Scheme for protecting rightful ownership”, IEEE Trans. on multimedia. 4 (1), (2002)
HN. Huang, DF. Chen, CC. Lin, “Improving SVD-based image watermarking via block-by-block optimization on singular values”, J Image Video Proc. 25 (2015)
R. Ghazy, N. El-Fishawy, M. Hadhoud, M. Dessouky, F. El-Samie, Block-by-block SVD-based image watermarking scheme. Natl. Radio Sci. Conf. 1(9), 13–15 (2007)
Z. Wang, A.-C. Bovik, Modern image quality assessment. Synthesis Lectures on Image, Video, and Multimed Process. 2(1), 1–156 (2006)
Z. Wang, A-C. Bovik, (2002) Why is Image Quality Assessment So Difficult?”, Proceeding of the IEEE International Conference on Acoustics, Speech, & Signal Processing (ICASSP). (4), 3313–3316
E. Hemdan, N. El-Fishawy, G. Attiya, F. El-Samie, “Hybrid Digital Image Watermarking Technique for Data Hiding”, Proceedings of the 27th National Radio Science Conference. 220–227 (2013)
A. F. Eldaoshy, M. I. Dessouky, S. Al-Dalil, F. E. Abd El-Samie, “Block-By-Block SVD Image Watermarking with Variable Block Sizes”, CIIT Digital image processing. 5(12), (2013)
Funding
Open access funding provided by The Science, Technology & Innovation Funding Authority (STDF) in cooperation with The Egyptian Knowledge Bank (EKB).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Eldaoushy, A.F., Desouky, M.I., El-Dolil, S.A. et al. Efficient hybrid digital image watermarking. J Opt 52, 2224–2238 (2023). https://doi.org/10.1007/s12596-023-01144-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12596-023-01144-7