Abstract
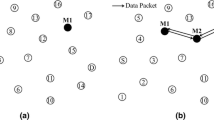
The requirement and the purpose of the IoT approach have developed substantially over the most recent few years. Here, IoT collects information from actual things, stores it, and then moves it to various organizations. Here, we use a Mobile Ad-Hoc Network (MANET) using IoT. MANET is highly delicate to malware which includes passive and active for the organization. Additionally, this paper shows the security angle-based IoT model utilizing AI. The black hole attack is one among these attacks which drops the entire information traffic and corrupts the organization's execution. In this way, it requires the designing of the novel Adaptive Defense Reinforcement Mountaineering Team Search (ADR-MTS) algorithm that distinguishes and safeguards the organization from the blackhole attack node. The role of ADR-MTS calculation recognizes the source directing and the sum of nodes that are been accomplished by the routing mechanism. This routing method assists with upgrading the course between the both objective node and the source node. The simulation analysis that performs MATLAB shows the improvement with regards to Packet Delivery Ratio (PDR). To improve the system efficiency a similar examination is performed against the current methodologies and from the study, the ADR-MTS calculation gives gainful outcomes concerning the location of black holes in the MANET-based IoT organizations The ADR-MTS method achieved a PDR of 98.7% and scalability of 98.5% and these results demonstrate the efficiency of the ADR-MTS method in comparison to existing methods.











Similar content being viewed by others
References
Tahboush M, Agoyi M (2021) A hybrid wormhole attack detection in mobile ad-hoc network (MANET). IEEE Access 9:11872–11883
Niu Z, Li Q, Ma C, Li H, Shan H, Yang F (2020) Identification of critical nodes for enhanced network defense in MANET-IoT networks. IEEE Access 8:183571–183582
Srilakshmi U, Veeraiah N, Alotaibi Y, Alghamdi SA, Khalaf OI, Subbayamma BV (2021) An improved hybrid secure multipath routing protocol for MANET. IEEE Access 9:163043–163053
Machado C, Westphall CM (2021) Blockchain incentivized data forwarding in MANETs: Strategies and challenges. Ad Hoc Netw 110:102321
Alghamdi SA (2021) Stable zone-based 5G clustered MANET using interest-region-based routing and gateway selection. Peer-to-Peer Networking Appl 14:3559–3577
Gautam D, Tokekar V (2020) A novel approach for detecting DDoS attack in MANET. Mater Today: Proceedings 29:674–677
Trivedi R, Khanpara P (2021) Robust and secure routing protocols for MANET-based internet of things systems—A survey. In Emergence of Cyber Physical System and IoT in Smart Automation and Robotics: Computer Engineering in Automation 175–188. Cham: Springer International Publishing
Muruganandam S, Renjit JA (2021) Real-time reliable clustering and secure transmission scheme for QoS development in MANET. Peer-to-Peer Networking Appl 14(6):3502–3517
Mankotia V, Sunkaria RK, Gurung S (2023) DT-AODV: A dynamic threshold protocol against black-hole attack in MANET. Sādhanā 48:190
Esiefarienrhe BM, Phakathi T, Lugayizi F (2022) Node-based QoS-aware security framework for sinkhole attacks in mobile Ad-Hoc networks. In Telecom 3:407–432. (MDPI)
RajaSuguna M, Jayabharathi R (2023) A hybrid effective trusted manet based on secure data transmission using artificial intelligence. In 2023 Eighth International Conference on Science Technology Engineering and Mathematics (ICONSTEM). 1–7 IEEE
Joardar S, Sinhababu N, Dey S, Choudhury P (2023) Mitigating DoS attack in MANETs considering node reputation with AI. J Netw Syst Manage 31:1–34
Jim LE, Islam N, Gregory MA (2022) Enhanced MANET security using artificial immune system-based danger theory to detect selfish nodes. Comput Secur 113:102538
Rani P, KavitaVerma S, Kaur N, Wozniak M, Shafi J, Ijaz MF (2021) Robust and secure data transmission using artificial intelligence techniques in ad-hoc networks. Sensors 22:251
Vijayalakshmi S, Bose S, Logeswari G, Anitha T (2023) Hybrid defense mechanism against malicious packet dropping attack for MANET using game theory. Cyber Secur Appl 1:100011
Singh P, Khari M, Vimal S (2022) EESSMT: An Energy Efficient Hybrid Scheme for Securing Mobile Ad hoc Networks Using IoT. Wireless Pers Commun 126:2149–2173. https://doi.org/10.1007/s11277-021-08764-x
Rani P, Verma S, Nguyen GN (2020) Mitigation of black hole and gray hole attack using swarm inspired algorithm with artificial neural network. IEEE access 8:121755–121764
Zhang H, Mi Y, Fu Y, Liu X, Zhang Y, Wang J, Tan J (2023) Security defense decision method based on potential differential game for complex networks. Comput Secur 129:103187
Zhang H, Mi Y, Liu X, Zhang Y, Wang J, Tan J (2023) A differential game approach for real-time security defense decision in scale-free networks. Comput Netw 224:109635
Li C, Dong M, Xin X, Li J, Ota Chen XB, K, (2023) Efficient privacy-preserving in IoMT with blockchain and lightweight secret sharing. IEEE Internet Things J 10(24):22051–22064
Yao Y, Zhao J, Li Z, Cheng X, Wu L (2023) Jamming and eavesdropping defense scheme based on deep reinforcement learning in autonomous vehicle networks. IEEE Trans Inf Forensics Secur 18:1211–1224
Luo J, Zhao C, Chen Q, Li G (2022) Using deep belief network to construct the agricultural information system based on Internet of things. J Supercomput 78:379–405
Liu C, Wu T, Li Z, Ma T, Huang J (2022) Robust online tensor completion for IoT streaming data recovery. IEEE Trans Neural Networks Learn Syst 34(12):10178–10192
Seyfollahi A, Moodi M, Ghaffari A (2022) MFO-RPL: A secure RPL-based routing protocol utilizing moth-flame optimizer for the IoT applications. Comput Standards Interfaces 82:103622
Mowla NI, Tran NH, Doh I, Chae K (2020) AFRL: Adaptive federated reinforcement learning for intelligent jamming defense in FANET. J Commun Networks 22:244–258
Yang H, Zhao J, Xiong Z, Lam KY, Sun S, Xiao L (2021) Privacy-preserving federated learning for UAV-enabled networks: Learning-based joint scheduling and resource management. IEEE J Sel Areas Commun 39:3144–3159
Zhong S, Guo S, Yu H, Wang Q (2021) Cooperative service caching and computation offloading in multi-access edge computing. Comput Netw 189:107916
Chen YJ, Liao KM, Ku ML, Tso FP, Chen GY (2021) Multi-agent reinforcement learning based 3D trajectory design in aerial-terrestrial wireless caching networks. IEEE Trans Veh Technol 70(8):8201–8215
Faridmehr I, Nehdi ML, Davoudkhani IF, Poolad A (2023) Mountaineering team-based optimization: a novel human-based metaheuristic algorithm. Mathematics 11:1273
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
SS agreed on the content of the study. SS, VS, VV and NE collected all the data for analysis.SS agreed on the methodology. SS, VS, VV and NE completed the analysis based on agreed steps. Results and conclusions are discussed and written together. The author read and approved the final manuscript.
Corresponding author
Ethics declarations
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Human and animal rights
This article does not contain any studies with human or animal subjects performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Saravanan, S., Surya, V., Valarmathi, V. et al. Enhancing IoT security in MANETs: A novel adaptive defense reinforcement approach. Peer-to-Peer Netw. Appl. (2024). https://doi.org/10.1007/s12083-024-01702-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12083-024-01702-1