Abstract
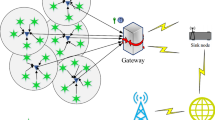
Internet of Things (IoT) is the collection of physical objects which consists of integrated technologies to sense, interact and collaborate with other smart objects to collect the data from the deployed environment and send it to the base station. Data dissemination is a network management service which is provided to devices of IoT, by the base station to monitor and manage the device related configuration parameter in the network. In data dissemination, it is very much essential to identify the legitimate nodes which are required for reprogramming and reconfiguring for device configuration during data transmission in order to ensure the security and reliability of the network. Since a greater number of devices are being reprogrammed to exchange data and commands autonomously in IoT, providing security to the disseminated configuration parameters is very essential. Therefore, efficient security authentication mechanism is required to prevent the various types of attacks which occurs during data dissemination. In this paper, an energy efficient Swan Intelligent based Clustering Technique (SICT) has been proposed to provide efficient clustering of nodes in the network. Moreover, trust based secured lightweight authentication protocol is proposed to provide better authentication and secure data dissemination to the devices of IoT. Additionally, the proposed protocol employs fuzzy logic to discover optimal route by selecting only trusted nodes during routing process. The advantages of the proposed system are it improves the security during data dissemination and optimizes the energy by identifying the relevant devices which are required for configuration parameters during data dissemination. The proposed system is implemented in NS3 simulation with realistic simulation parameters namely energy efficiency, network lifetime, throughput, computational cost, communication cost, average signing time, average verification time, packet delivery ratio and network delay. The simulation results justifies that the proposed protocol improves average energy consumption by 34%, computational cost by 41.85%, communication cost by 36.83%, network delay by 31.66%, signing time by 26.25% and verification time by 33.46%. Moreover, the proposed system improves packet delivery ratio by 30% and provides efficient authentication to mitigate various types of attacks during data dissemination when it is compared with other existing protocols in IoT environment.




















Similar content being viewed by others
Data availability
Data is available based on the request.
References
Santhosh Kumar S, Palanichamy Y (2017) Energy efficient and secured distributed data dissemination using hop by hop authentication in WSN. Wireless Netw 24(4):1343–1360
Shanmugapriya R, Santhosh Kumar SVN (2022) Comprehensive survey on data dissemination protocols for efficient reprogramming in Internet of Things. Concurrency and computation: practice and experience 34(26):e7280
Santhosh Kumar S, Palanichamy Y, Selvi M, Ganapathy S, Kannan A, Perumal S (2021) Energy efficient secured K means based unequal fuzzy clustering algorithm for efficient reprogramming in wireless sensor networks. Wireless Netw 27(6):3873–3894
Thangaramya K, Kulothungan K, Logambigai R, Selvi M, Ganapathy S (2019) Energy aware cluster and neuro-fuzzy based directing route algorithm for wireless sensor networks in IoT. J Comput Netw 151:211–223
Selvi M, Thangaramya K, Ganapathy S, Kulothungan K, Nehemiah HK, Kannan A (2019) An energy aware trust based secure directing route algorithm for effective communication in wireless sensor networks. Wirel Pers Commun 105(4):1475–1490
Chandna M, Singla B (2019) An energy-efficient gossiping protocol for wireless sensor networks using Chebyshev interval. Procedia Comput Sci 151:1066–1071. https://doi.org/10.1016/j.procs.2019.04.151
Haseeb K, Bakar KA, Abdullah AH, Darwish T (2017) Adaptive energy aware cluster-based directing route protocol for wireless sensor networks. Wireless Netw 23(3):1953–1966
Mazumdar N, Roy S, Nag A, Nandi S (2021) An adaptive hierarchical data dissemination mechanism for mobile data collector enabled dynamic wireless sensor network. J Netw Comput Appl 186:103097
Seyfollahi A, Ghaffari A (2020) Reliable data dissemination for the Internet of Things using Harris hawks optimization. Peer Peer Netw Appl 13(6):1886–1902
Yarinezhad R (2019) Reducing delay and prolonging the assume that time of wireless sensor network using efficient directing route protocol based on mobile sink and virtual infrastructure. Ad Hoc Netw 84:42–55. https://doi.org/10.1016/j.adhoc.2018.09.016
Chowdhury S, Giri C (2019) EETC: energy efficient tree-clustering in delay constrained wireless sensor network. Wireless Pers Commun 109(1):189–210. https://doi.org/10.1007/s11277-019-06559-9
Muthurajkumar S, Ganapathy S, Vijayalakshmi M, Kannan A (2017) An intelligent secured and energy efficient directing route algorithm for MANETs. Wirel Pers Commun 96(2):1753–1769
Logambigai R, Ganapathy S, Kannan A (2018) Energy–efficient grid-based directing route algorithm using intelligent fuzzy rules for wireless sensor networks. Comput Electr Eng 68:62–75
Li S, Zhao S, Wang X, Zhang K, Li L (2014) Adaptive and secure load-balancing directing route protocol for service-oriented wireless sensor networks. IEEE Syst J 8(3):858–867
Mazinani A, Mazinani SM, Mirzaie M (2019) FMCR-CT: an energyefficient fuzzy multi cluster-based directing route with a constant threshold in wireless sensor network. Alex Eng J 58:127–141
Saidi A, Benahmed K, Seddiki N (2020) Secure cluster head election algorithm and misbehavior detection approach based on trust management technique for clustered wireless sensor networks. Ad Hoc Netw 106:102215
Maivizhi R, Yogesh P (2022) Fuzzy directing route for in-network aggregation in wireless sensor networks. Peer Peer Netw Appl 15(1):592–611
Kalidoss T, Rajasekaran L, Kanagasabai K, Sannasi G, Kannan A (2019) QoS aware trust based directing route algorithm for wireless sensor networks. Wirel Pers Commun 110(4):1637–1658
Hsu CM (2003) A group digital signature technique for authentication. In: IEEE 37th annual 2003 international Carnahan conference on security technology, 2003. Proceedings. IEEE, pp 253–256
Gaber T, Abdelwahab S, Elhoseny M, Hassanien A (2018) Trust-based secure clustering in WSN-based intelligent transportation systems. Comput Netw 146:151–158
Gulati K, Kumar Boddu R, Kapila D, Bangare S, Chandnani N, Saravanan G (2022) A review paper on wireless sensor network techniques in Internet of Things (IoT). Mater Today Proc 51:161–165
Al-Omaisi H, Sundararajan E, Alsaqour R, Abdullah N, Abdelhaq M (2021) A survey of data dissemination schemes in vehicular named data networking. Veh Commun 30:100353
Abhishek Badholia K (2021) Cluster based directing route protocols in wsn sensor. Inf Technol Ind 9(1):198–206
Al-Naji F, Zagrouba R (2020) A survey on continuous authentication methods in Internet of Things environment. Comput Commun 163:109–133
Fan Q, Chen J, Deborah L, Luo M (2021) A secure and efficient authentication and data sharing scheme for Internet of Things based on blockchain. J Syst Architect 117:102112
Li J, Zhang Z, Hui L, Zhou Z (2020) A novel message authentication scheme with absolute privacy for the internet of things networks. IEEE Access 8:39689–39699
Wu F, Li X, Xu L, Vijayakumar P, Kumar N (2021) A novel three-factor authentication protocol for wireless sensor networks with IoT notion. IEEE Syst J 15(1):1120–1129
Kar J, Naik K, Abdelkader T (2021) A secure and lightweight protocol for message authentication in wireless sensor networks. IEEE Syst J 15(3):3808–3819
Xiong L, Xiong N, Wang C, Yu X, Shuai M (2021) An efficient lightweight authentication scheme with adaptive resilience of asynchronization attacks for wireless sensor networks. IEEE Trans Syst Man Cybern Syst 51(9):5626–5638
Hussain M, Mehmood A, Khan S, Khan M, Iqbal Z (2019) Authentication techniques and methodologies used in wireless body area networks. J Syst Architect 101:101655
Harbi Y, Aliouat Z, Refoufi A, Harous S, Bentaleb A (2019) Enhanced authentication and key management scheme for securing data transmission in the internet of things. Ad Hoc Netw 94:101948
Hu H, Han Y, Yao M, Song X (2022) Trust based secure and energy efficient directing route protocol for wireless sensor networks. IEEE Access 10:10585–10596
Abbas Ahmad S, Krishnahari E, Yousuf Khan M, Prabhakara Rao S (2020) Neighbor node intimacy (N2i) for trust management in WSN. Mater Today Proc
K.P A (2021) Comparison of fuzzy-based cluster head selection algorithm with LEACH algorithm in wireless sensor networks to maximize network LAssume thatetime. Rev Gestão Inovação Tecnol 11(4):1277–1288
Abanto-Leon LF et al (2020) Swan: swarm-based low-complexity scheme for PAPR reduction. GLOBECOM 2020 - 2020 IEEE Global Communications Conference [Preprint]. https://doi.org/10.1109/globecom42002.2020.9322272
Yang XS, Deb S (2010) Engineering optimisation by cuckoo search. Int J Math Model Numer Optim 1(4):330–343
Afianti F, Wirawan, Suryani T (2019) Lightweight and DoS resistant multiuser authentication in wireless sensor networks for smart grid environments. IEEE Access 7:67107–67122
Gope P, Sikdar B (2019) Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J 6(1):580–589
Patil P, Deshpande R, Mane P (2020) Trust and opportunity based directing route framework in wireless sensor network using hybrid optimization algorithm. Wirel Pers Commun 115(1):415–437
De P, Liu Y, Das SK (2008, March) ReMo: An energy efficient reprogramming protocol for mobile sensor networks. In: 2008 sixth annual IEEE international conference on pervasive computing and communications (PerCom). IEEE, pp 60–69
Wang Q, Zhu Y, Cheng L (2006) Reprogramming wireless sensor networks: challenges and approaches. IEEE Network 20(3):48–55
Wang, L. (2004). MNP: Multihop network reprogramming service for sensor networks. In: Proceedings of the 2nd ACM conference on embedded networked sensor systems, USA. 12. Hyun S, Ning P, Liu A, Du W (2008) – MOAP
Hui JW, Culler D (2004) The dynamic behavior of a data dissemination protocol for network programming at scale. In: Proceedings of the 2nd international conference on embedded networked sensor systems (Sensys 04). ACM, New York, pp 81–94. - Deluge
Hyun S, Ning P, Liu A, Du W (2008) Seluge: Secure and dos-resistant code dissemination in wireless sensor networks. In: 2008 international conference on information processing in sensor networks (IPSN 2008). IEEE, pp 445–456
Zhang R, Zhang Y (2011) LR-Seluge: Loss-resilient and secure code dissemination in wireless sensor networks. In: 2011 31st international conference on distributed computing Systems. IEEE, pp 497–506
Naik V, Arora A, Sinha P, Zhang H (2005) Sprinkler: A reliable and energy efficient data dissemination service for wireless embedded devices. In: 26th IEEE international real-time systems symposium (RTSS'05). IEEE, p 10
Levis P, Patel N, Culler D, Shenker S (2004) Trickle: a self-regulating algorithm for code maintenance and propagation in wirelesssensor networks. In: Proceedings of 1st conference symposium network systems design implementation. 17, pp 15–28
Huang L, Setia S (2008) CORD: Energy-efficient reliable bulk data dissemination in sensor networks. In: IEEE INFOCOM 2008-The 27th conference on computer communications. IEEE, pp 574–582
Lin K, Levis P (2008) Data discovery and dissemination with dip. In: 2008 international conference on information processing in sensor networks (IPSN 2008). IEEE, pp 433–444
He D, Chan S, Tang S, Guizani M (2013) Secure data discovery and dissemination based on hash tree for wireless sensor networks. IEEE Trans Wireless Commun 12(9):4638–4646
He D, Chan S, Tang S, Guizani M (2015) Secure and distributed data discovery and dissemination in wireless sensor networks. IEEE Trans Wireless Commun 26(4):1129–1139
Hawbani A, Wang X, Kuhlani H, Karmoshi S, Ghoul R, Sharabi Y, Torbosh E (2018) Sink-oriented tree-based data dissemination protocol for mobile sinks in wireless sensor networks. Wireless Netw 24(7):2723–2734
Ahim KA (2017) BASIS: a practical multi-user broadcast authentication scheme in wireless sensor networks. IEEE Trans Inf Forensics Secur 12(7):1545–1553
Ma K et al (2021) Reliability-constrained throughput optimization of industrial wireless sensor networks with energy harvesting relay. IEEE Internet Things J 8(17):13343–13354. https://doi.org/10.1109/jiot.2021.3065966
Cao K et al (2021) Achieving reliable and secure communications in wireless-powered Noma systems. IEEE Trans Veh Technol 70(2):1978–1983. https://doi.org/10.1109/tvt.2021.3053093
Guo F et al (2022) Path extension similarity link prediction method based on matrix algebra in directed networks. Comput Commun 187:83–92. https://doi.org/10.1016/j.comcom.2022.02.002
Li L, Yao L (2023) Fault tolerant control of fuzzy stochastic distribution systems with packet dropout and time delay. IEEE transactions on automation science and engineering. pp 1–10. https://doi.org/10.1109/tase.2023.3266065
Dai X et al (2023) Task co-offloading for D2D-assisted Mobile edge computing in industrial internet of things. IEEE Trans Industr Inf 19(1):480–490. https://doi.org/10.1109/tii.2022.3158974
Jiang H et al (2022) An energy-efficient framework for internet of things underlaying heterogeneous small cell networks. IEEE Trans Mob Comput 21(1):31–43. https://doi.org/10.1109/tmc.2020.3005908
Luo J et al (2021) Using deep belief network to construct the agricultural information system based on internet of things. J Supercomput 78(1):379–405. https://doi.org/10.1007/s11227-021-03898-y
Liu C et al (2023) Robust online tensor completion for IOT streaming data recovery. IEEE Trans Neural Netw Learn Syst 34(12):10178–10192. https://doi.org/10.1109/tnnls.2022.3165076
Cao B et al (2020) Security-aware industrial wireless sensor network deployment optimization. IEEE Trans Industr Inf 16(8):5309–5316. https://doi.org/10.1109/tii.2019.2961340
Cheng B et al (2016) Situation-aware IOT service coordination using the event-driven SOA paradigm. IEEE Trans Netw Serv Manage 13(2):349–361. https://doi.org/10.1109/tnsm.2016.2541171
Lyu T et al (2023) Source selection and resource allocation in wireless powered relay networks: an adaptive dynamic programming based approach. IEEE Internet Things J:1–1. https://doi.org/10.1109/jiot.2023.3321673
Palanisamy S, Sankar S, Somula R (2021) Communication trust and energy-aware routing protocol for WSN using DS theory. Int J Grid High Perform Comput (IJGHPC -IGI) 13(4):24–36. https://doi.org/10.4018/IJGHPC.2021100102. (Publisher IGI Global)
Manuel AJ et al (2020) Optimization of routing-based clustering approaches in wireless sensor network: review and open research issues. Electronics 9(10):1630. https://doi.org/10.3390/electronics9101630
Selvaraj A et al (2019) Optimal virtual machine selection for anomaly detection using a swarm intelligence approach. Appl Soft Comput 84:105686. https://doi.org/10.1016/j.asoc.2019.105686
Nagarajan SM et al (2022) Integration of IOT based routing process for food supply chain management in sustainable smart cities. Sustain Cities Soc 76:103448. https://doi.org/10.1016/j.scs.2021.103448
Krishnasamy L et al (2020) A heuristic angular clustering framework for secured statistical data aggregation in sensor networks. Sensors 20(17):4937. https://doi.org/10.3390/s20174937
Gopal DG, Saravanan R (2016) Selfish node detection based on evidence by trust authority and selfish replica allocation in DANET. Int J Inf CommunTechnol 9(4):473–491
Karuppiah M, Ramana TV, Mohanty R, Devarajan GG, Nagarajan SM (2023) UIoTN-PMSE: Ubiquitous IoT network-based predictive modeling in smart environment. Inte J Commun Syst e5661
Sivakumar NR, Nagarajan SM, Devarajan GG, Pullagura L, Mahapatra RP (2023) Enhancing network lifespan in wireless sensor networks using deep learning-based graph neural network. Phys Commun:102076. https://doi.org/10.1016/j.phycom.2023.102076
Marimuthu K, Sashi Kanth K, Setty S, Tainwala K Scalable and secure data sharing for dynamic groups in the cloud, 2014/5/8, pp 1697–1701, 2014 IEEE International Conference on Advanced Communication Control and Computing Technologies (ICACCCT)
Malik G, Boominathan P, Marimuthu K (2014) A secured cloud system and log records based on 2LE. Int J Appl Eng Res (IJAER) 9(20):7435–7451
Marimuthu K, Ganesh Gopal D, Aditya S, Mittal V (2014) Cryptanalysis of oPass. 2014 IEEE international conference on advanced communications, control and computing technologies. https://doi.org/10.1109/icaccct.2014.7019457
Funding
No funding.
Author information
Authors and Affiliations
Contributions
All the authors have contributed in a equal manner.
Corresponding author
Ethics declarations
Ethics approval
Authors provide the Ethics Approval for the given manuscript.
Consent to publish
All the authors gave permission to Consent to publish.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Shanmugapriya, R., SVN, S.K. An energy efficient Swan Intelligent based Clustering Technique (SICT) with fuzzy based secure routing protocol in IoT. Peer-to-Peer Netw. Appl. (2024). https://doi.org/10.1007/s12083-024-01670-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12083-024-01670-6