Abstract
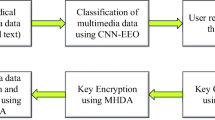
Cloud computing (CC) is a rapidly growing technology that is deployed by various organizations due to the high level of scalability, elasticity, and virtualization it offers. However, security-related challenges arise due to insecure access control points. Security models in the cloud such as authentication, data recovery, confidentiality, accessibility, and data integrity. This includes the deployment model, barriers in cloud computing, cloud services, and security issues. Data security can be improved via the usage of encryption and decryption keys during transmission. However, the existing techniques often suffered from improved time consumption and complexity in handling more users. This paper mainly focuses on the data security issue with the outsourced sensitive data in the cloud server by designing a novel Modified Multi-scale Convolutional Neural Network-based Zebra Optimization (MMCNN-ZO) approach to improve the cloud data sharing system. The proposed MMCNN-ZO approach safeguards the crucial data effectively and outputs in the form of cipher text/image. Here, the weight functions of the MMCNN are tuned mechanically using the ZO algorithm for the enhanced encryption process. The decryption process is performed to obtain the data in user understandable format. These procedures make the proposed system effectively secure the data content by protecting against intrusions. The efficacy of the proposed MMCNN-ZO method is investigated using diverse evaluation indicators namely throughput, decryption, and encryption time. The proposed MMCNN-ZO algorithm achieved improvements in terms of throughput, encryption time, and decryption time of 7450 bits/sec, 4.82 ms, and 4.86 ms respectively compared to other existing methods of SVM, ANN, BPPSVC, and GBCRP. The experimental results inherit the better performances of the suggested MMCNN-ZO approach over other methods in terms of all metrics.


















Similar content being viewed by others
Availability of data and material
The data that support the findings of this study are available from the corresponding author upon reasonable request.
Code availability
Not applicable.
References
Rehman MU, Shafique A, Khan KH, Hazzazi MM (2023) Efficient and secure image encryption using key substitution process with discrete wavelet transform. J King Saud Univ-Comput Inform Sci 101613
Hazzazi MM, Attuluri S, Bassfar Z, Joshi K (2023) A novel cipher-based data encryption with galois field theory. Sensors 23(6):3287
Nadeem M, Arshad A, Riaz S, Zahra SW, Dutta AK, Al Moteri M, Almotairi S (2023) An efficient technique to prevent data misuse with matrix cipher encryption algorithms. Comput Mater Contin 74(2)
Sutradhar S, Karforma S, Bose R, Roy S (2023) A dynamic step-wise tiny encryption algorithm with fruit fly optimization for quality of service improvement in healthcare. Healthc Anal 3:100177
Sodhro AH, Pirbhulal S, Muzammal M, Zongwei L (2020) Towards blockchain-enabled security technique for industrial internet of things based decentralized applications. J Grid Comput 18(4):615–628
Kumar P, Gupta GP, Tripathi R (2021) TP2SF: A Trustworthy Privacy-Preserving Secured Framework for sustainable smart cities by leveraging blockchain and machine learning. J Syst Architect 115:101954
Nguyen DC, Pathirana PN, Ding M, Seneviratne A (2020) Integration of blockchain and cloud of things: Architecture, applications and challenges. IEEE Commun Surv Tutor 22(4):2521–2549
Ahmad S, Mehfuz S (2023) Efficient time-oriented latency-based secure data encryption for cloud storage. Cyber Secur Appl 100027
Oktian YE, Witanto EN, Lee SG (2021) A conceptual architecture in decentralizing computing, storage, and networking aspect of IoT infrastructure. IoT 2(2):205–221
Kadry H, Farouk A, Zanaty EA, Reyad O (2023) Intrusion detection model using optimized quantum neural network and elliptical curve cryptography for data security. Alex Eng J 71:491–500
Samanta D, Alahmadi AH, Karthikeyan MP, Khan MZ, Banerjee A, Dalapati GK, Ramakrishna S (2021) Cipher block chaining support vector machine for secured decentralized cloud enabled intelligent IoT architecture. IEEE Access 9:98013–98025
Mrabet H, Alhomoud A, Jemai A, Trentesaux D (2022) A secured industrial Internet-of-Things architecture based on blockchain technology and machine learning for sensor access control systems in smart manufacturing. Appl Sci 12(9):4641
Singh AK, Saxena D (2022) A cryptography and machine learning based authentication for secure data-sharing in federated cloud services environment. J Appl Secur Res 17(3):385–412
Sana MU, Li Z, Javaid F, Liaqat HB, Ali MU (2021) Enhanced security in cloud computing using neural network and encryption. IEEE Access 9:145785–145799
Meena U, Sharma P (2023) An improved blockchain based encryption scheme for secure routing in wireless sensor network using machine learning technique. Trans Emerg Telecommun Technol 34(3):e4713
Gupta R, Saxena D, Gupta I, Singh AK (2022) Differential and triphase adaptive learning-based privacy-preserving model for medical data in cloud environment. IEEE Netw Lett 4(4):217–221
Saxena D, Singh AK (2022) A high availability management model based on VM significance ranking and resource estimation for cloud applications. IEEE Trans Serv Comput
Smahi A, Xia Q, Xia H, Sulemana N, Fateh AA, Gao J, Du X, Guizani M (2020) A blockchainized privacy-preserving support vector machine classification on mobile crowd sensed data. Pervasive Mob Comput 66:101195
Shen M, Tang X, Zhu L, Du X, Guizani M (2019) Privacy-preserving support vector machine training over blockchain-based encrypted IoT data in smart cities. IEEE Internet Things J 6(5):7702–7712
Singh SK, Rathore S, Park JH (2020) Blockiotintelligence: A blockchain-enabled intelligent IoT architecture with artificial intelligence. Futur Gener Comput Syst 110:721–743
Ghazal TM, Hasan MK, Abdullah SNHS, Bakar KAA, Al Hamadi H (2020) Private blockchain-based encryption framework using computational intelligence approach. Egypt Inform J
Rahman MA, Hossain MS, Islam MS, Alrajeh NA, Muhammad G (2020) Secure and provenance enhanced internet of health things framework: A blockchain managed federated learning approach. IEEE Access 8:205071–205087. https://doi.org/10.1109/ACCESS.2020.3037474
Chen X, Zhang H, Song J, Guan J, Li J, He Z (2022) Micro-motion classification of flying bird and rotor drones via data augmentation and modified multi-scale CNN. Remote Sens 14(5):1107
Trojovská E, Dehghani M, Trojovský P (2022) Zebra optimization algorithm: A new bio-inspired optimization algorithm for solving optimization algorithm. IEEE Access 10:49445–49473
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
AM, JJJ, MISL agreed on the content of the study. AM, JJJ, MISL collected all the data for analysis. AM, JJJ, MISL agreed on the methodology. AM, JJJ, MISL completed the analysis based on agreed steps. Results and conclusions are discussed and written together. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Human and animal rights
This article does not contain any studies with human or animal subjects performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Track on Networking and Applications
Guest Editor: Vojislav B. Misic
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
M, A., J, J.J. & L, M.I.S. MMCNN-ZO: Modified multi-scale convolutional neural network-based zebra optimization for enhancing data encryption system. Peer-to-Peer Netw. Appl. 17, 924–943 (2024). https://doi.org/10.1007/s12083-023-01592-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-023-01592-9