Abstract
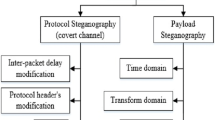
Steganography based on bits-modification of speech frames is a kind of commonly used method, which targets at RTP payloads and offers covert communications over voice-over-IP (VoIP). However, direct modification on frames is often independent of the inherent speech features, which may lead to great degradation of speech quality. A novel frame-bitrate-change based steganography is proposed in this work, which discovers a novel covert channel for VoIP and introduces less distortion. This method exploits the feature of multi-rate speech codecs that the practical bitrate of speech frame is identified only by speech decoder at receiving end. Based on this characteristic, two steganography strategies called bitrate downgrading (BD) and bitrate switching (BS) are provided. The first strategy substitutes high bit-rate speech frames with lower ones to embed secret message, which introduces very low distortion in practice, and much less than other bits-modification based methods with the same embedding capacity. The second one encodes secret message bits into different types of speech frames, which is an alternative choice for supplement. The two strategies are implemented and tested on our covert communication system StegVoIP. The experiment results show that our proposed method is effective and fulfills the real-time requirement of VoIP communication.
Similar content being viewed by others
References
KEROMYTIS A. Voice-over-IP security: Research and practice [J]. IEEE Security Privacy, 2010, 8(2): 76–78.
TIAN Hui, ZHOU Ke, FENG Dan. Dynamic matrix encoding strategy for voice-over-IP steganography [J]. Journal of Central South University of Technology, 2010, 17(6): 1285–1292.
YING Li-zhi, HUANG Yong-feng, YUAN Jian, LINDA B. A novel covert timing channel based on RTP/RTCP [J]. Chinese Journal of Electronics, 2012, 21(4): 711–714.
ZHOU Ke, LIU Jin, TIAN Hui, LI Chun-hua. State-based steganography in low bit rate speech [C]// Proceedings of the 20th ACM International Conference on Multimedia. Nara: ACM, 2012:1109–1112.
HUANG Y, TANG S, BAO C. Steganalysis of compressed speech to detect covert voice over Internet protocol channels [J]. IET Information Security, 2011, 5(1): 26–32.
ZANDER S, ARMITAGE G, BRANCH P. Covert channels and countermeasures in computer network protocols [J]. IEEE Communications Magazine, 2007, 45(12): 136–142.
TIAN Hui, JIANG Hong, ZHOU Ke, DAN Feng. Transparency-orientated encoding strategies for voice-over-IP steganography [J]. The Computer Journal, 2012, 55(6): 702–716.
TIAN Hui, ZHOU Ke, LU Jing. A VoIP-based covert communication scheme using compounded pseudorandom m sequence [J]. International Journal of Advancements in Computing Technology, 2012, 4(1): 223–230.
LIU Jin, ZHOU Ke, TIAN Hui, LI Chun-hua. Efficient least-significant-bits steganography for VoIP [J]. International Journal of Advancements in Computing Technology, 2012, 4(10): 297–305.
HUANG Y, TANG S, YUAN J. Steganography in inactive frames of VoIP streams encoded by source codec [J]. IEEE Transactions on Information Forensics and Security, 2011, 6(2): 296–306.
MAZURCZYK W, SZAGA P, SZCZYPIORSKI K. Using transcoding for hidden communication in IP telephony [J]. Multimedia Tools and Applications, 2011: 1–27.
Telecommunication standardization sector of ITU. ITU-T G.723.1-Dual rate speech coder for multimedia communications transmitting at 5.3 and 6.3 kbit/s [R]. Geneva, Switzerland: International Telecommunication Union, 2006.
SIMMONS G. The prisoner’s problem and the subliminal channel [C]// Proceedings of Crypto: Plenum 1984: 51–67.
SCHULZRINNE H, CASNER S. RTP profile for audio and video conferences with minimal control [R]. IETF Network Working Group, 2003.
XIAO Bo, HUANG Yong-feng. Modeling and optimizing of the information hiding communication system over streaming media [J]. Journal of Xidian University, 2008, 35(3): 554–558. (in Chinese)
WANG Chungyi, WU Quincy. Information hiding in real-time VoIP streams [C]// Proceedings of the 9th IEEE International Symposium on Multimedia. Taiwan: IEEE, 2007: 255–262.
NORVIG P. English letter frequency counts: Mayzner revisited [EB/OL]. [2012-12-20]. http://norvig.com/mayzner.html.
Telecommunication standardization sector of ITU. ITU-T P.862-Perceptual evaluation of speech quality (PESQ): An objective method for end-to-end speech quality assessment of narrow-band telephone networks and speech codecs [R]. Geneva, Switzerland: International Telecommunication Union, 2001.
Telecommunication standardization sector of ITU. ITU-T G.114-One-way transmission time [R]. Geneva, Switzerland: International Telecommunication Union, 2003.
LU Ji-cang, HUANG Yong-feng, LIU Fen-lin, LUO Xiang-yang. Pulse position checking-based steganalysis of G.723.1 compressed speech in VoIP [J]. International Journal Multimedia Intelligence and Security. 2011, 2(3/4): 225–237.
LI Song-bin, TAO Huai-zhou, HUANG Yong-feng. Detection of QIM steganography in G.723.1 bit stream based on quantization index sequence analysis [J]. Journal of Zhejiang University Science C. 2012, 13(8): 624–634.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Project(2011CB302305) supported by National Basic Research Program (973 Program) of China; Projects(61232004, 61302094) supported by National Natural Science Foundation of China; Project(ZQN-PY115) supported by Promotion Program for Young and Middle-aged Teacher in Science and Technology Research of Huaqiao University, China; Project(JA13012) supported by Education Science Research Program for Young and Middle-aged Teacher of Fujian Province of China; Project(2014J01238) supported by Natural Science Foundation of Fujian Province of China
Rights and permissions
About this article
Cite this article
Liu, J., Tian, H. & Zhou, K. Frame-bitrate-change based steganography for voice-over-IP. J. Cent. South Univ. 21, 4544–4552 (2014). https://doi.org/10.1007/s11771-014-2459-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11771-014-2459-5