Abstract
Additive Manufacturing (AM) offers revolutionary design capabilities but introduces cybersecurity vulnerabilities due to its digital integration. While existing research focuses on cyber threats, a significant gap exists in addressing physical and cyber risks. The current research focuses on cyber threats, but more attention needs to be paid to addressing physical and cyber risks. This paper proposes a new risk assessment framework that considers both physical and cyber threats quantitatively and qualitatively and helps safeguard the AM supply chain. The framework identifies, analyses, and prioritises potential threats based on their characteristics. It also considers the trustworthiness of data and the frequency of reported threats to estimate the likelihood of each threat. The risks are then prioritised based on a combined impact-likelihood score. The framework has been validated on the standard benchmark MITRE CVEs dataset and has proven effective in identifying critical vulnerabilities. This approach empowers manufacturers to proactively deal with security concerns and navigate the complexities of the rapidly evolving AM landscape.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Additive Manufacturing (AM), also known as 3D printing, is a rapidly advancing technology that is revolutionizing the way we create complex objects. Layering materials offers many benefits, such as the ability to produce custom-designed components, reduce lead time and inventory costs through on-demand production, Utilize a wider range of materials compared to traditional manufacturing, and Create intricate shapes with complex geometries [1]. These advantages, coupled with its alignment with the Industry 4.0 principles of automation and connectivity, position AM as a game-changer in modern manufacturing [2, 3].
However, this increased reliance on digital technologies introduces new cybersecurity challenges. As AM integrates with cyber-physical systems (CPS) and the Internet of Things (IoT), it becomes vulnerable to cyberattacks [4]. AM is a prime target for cyber-attacks due to several factors. First, the increasing digitization of businesses means that attackers can exploit more digital touchpoints. Second, as systems become more interconnected, the risk of attackers infiltrating the entire supply chain increases. Finally, cyber attackers are constantly developing new methods to exploit vulnerabilities, making it crucial for businesses to stay vigilant and take appropriate measures to protect themselves [5].
Cyberattacks in the additive manufacturing (AM) industry can have severe consequences, such as intellectual property theft, disrupted production, counterfeit products, and safety hazards. Attackers can steal sensitive design data, malware can manipulate printing processes, stolen designs can be used to create fake parts, and tampered designs can lead to product failures. According to the IBM X-Force report,Footnote 1 the manufacturing industry, including AM, is a prime target for cyberattacks due to its growing digital footprint and the potential for significant economic disruption [6].
1.1 Existing Works
Additive Manufacturing (AM) provides numerous opportunities for innovation, but it also brings new cybersecurity challenges across its supply chain [7]. Research on possible attack vectors within AM systems is still in progress. Although current frameworks for conventional manufacturing with digital connections can be customised for AM, the main challenge is to develop countermeasures that do not impede the system’s operating speed. Several frameworks have been proposed to address Additive Manufacturing (AM) cybersecurity threats.
Cabezali et al. [8] focus on the risks involved in managing Additive Manufacturing (AM) Research and Development (R &D) projects. Significant risks that impact project objectives are identified through a literature review and expert survey. A model based on fuzzy logic is developed using MATLAB Fuzzy Logic Toolbox, which assesses the relevance of each risk based on its likelihood and impact. Organizations and researchers can use the model to prioritize risks and develop effective strategies to achieve project success in AM R &D. Combita et al. [9] used game theory to reason out the difference between the attacker and the security system with a conflict of goals, with the attacker intending to maximise damage to the system and the security working to minimise the damage.
Desmit et al. [10] considered that the area to evaluate and predict cyber-physical attacks is at the intersection of the manufacturing process of cyber, physical, cyber-physical and human entities. They proposed intersection mapping to identify points of vulnerability and propose impact analysis of intersection with decision trees that provide a scale to classify the vulnerabilities into low, medium and high levels. Once the intersections are mapped, an impact analysis is carried out at these junctions using metric characterising intersections, which include Loss of information, Inconsistency, Relative frequency, Lack of maturity, and Time until detection. Each of these is ranked low, medium, and high, indicating their vulnerability Impact. Decision trees are then made for these easily repeatable metrics for different situations.
Padmanabhan et al. [11] reviewed the significant cybersecurity risks associated with the additive manufacturing (AM) industry. They also proposed a new framework to identify potential threats and evaluate vulnerabilities in the AM process. In addition, they suggested a new technique of encrypting 3D model information using 2D images, which may improve cybersecurity in the AM process. Gupta et al. [12] discuss the possible attacks (printer, raw material and design level) and risks (reverse engineering, counterfeiting and theft) and provide an enhanced risk classification scheme. It contends that traditional cybersecurity methods must evolve to address the new class of attack vectors that threaten the AM supply chain. It also discusses the nature of existing solutions that help address risks and attack threats. In providing a holistic view of the AM supply chain, the interdependencies of the processes in the AM supply chain are presented, and the effects of local attack vectors on the entire supply chain are elucidated.
1.2 Research Challenge and Motivation
Existing works focus on cyber security threats within the Additive Manufacturing (AM) supply chain, but there needs to be a significant gap in addressing physical risks. The research mainly concentrates on cyber threats, neglecting potential physical security vulnerabilities. These vulnerabilities include unauthorised access to AM systems, manipulation of physical components such as raw materials, and safety hazards during printing. With a comprehensive approach that considers both physical and cyber risks, a complete understanding of potential vulnerabilities in AM is easier to achieve. This hinders the development of effective mitigation strategies.
To address this gap, a new, comprehensive framework is crucial. Such a framework must integrate physical and cyber aspects into a unified risk assessment methodology for AM. Doing so would enhance security by allowing for the implementation of more robust measures across the AM supply chain, leading to a significant reduction in the risk of successful attacks. Additionally, it would empower stakeholders to prioritise resources and mitigation efforts more effectively. This promotes innovation in AM security solutions and supports this transformative technology’s continued growth and adoption.
1.3 Contribution
This paper introduces a proactive threat-centric risk assessment framework for enhancing the security of the Additive Manufacturing (AM) supply chain. The methodology diverges from traditional reactive approaches, enabling AM organisations to identify and mitigate potential threats and vulnerabilities pro-actively. The process unfolds through the following systematic steps:
-
Literature Review: We conduct a comprehensive literature review to identify categories of threats in AM and identify twenty-two potential cyber-physical and cybersecurity threats in the AM supply chain.
-
Threat Analysis: We perform meticulous threat analysis, including identification and categorization. The framework defines five crucial threat characteristics for assessing impact: target precision, area of impact, collateral damage, stealth, and attack repeatability. Threat severity is estimated qualitatively and quantitatively based on these characteristics.
-
Likelihood Estimation: We estimate threat likelihood based on factors such as the source’s severity level and frequency of occurrence.
-
Risk Analysis and Threat Prioritization: Utilizing threat severity and likelihood metrics for comprehensive risk analysis and prioritization. This step ensures strategic prioritization of threats based on their assessed severity and likelihood, facilitating effective resource allocation.
-
Testing and Validation: The framework is tested and validated on standard benchmark dataset of Common Vulnerabilities and Exposures (CVEs) managed by MITRE.
1.4 Organisation
The remainder of the paper is organized as follows. Section 2 provides a conceptual background on threats in the manufacturing industry, cyber-attacks in the AM sector, and cyber threat intelligence. Section 3 offers an overview of the proposed risk assessment method. Sections 4 and 5 detail threat analysis and likelihood estimation. Section 6 covers risk estimation, while Section 7 demonstrates the experimental result. Section 8 discusses the challenges and Future scope of this work. The conclusion is discussed in Section 9.
2 Conceptual Background
2.1 AM Life Cycle
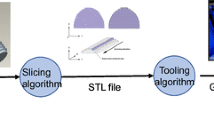
AM life cycle includes the following phases: product designing, computer-aided design (CAD) modelling, and the use of STereoLithography or Standard Tessellation Language (STL) format files [13]. The design phase can be time-consuming and may need many iterations. Finite Element Analysis (FEA) and other computational technologies are utilised to evaluate CAD models (shown in Fig 1). When the design is finished, the CAD file is converted to a generic STL format and cut into two-dimensional slices for printing. The tool path file contains printer settings like temperature and laser power and is utilised by the 3D printer to build the component. Post-processing operations, such as support material removal, surface finishing, and heat treatment, may be required after printing. The process chain steps can all be carried out or delegated to various parties participating in the supply chain. The Manufacturer may be involved in the design phase or delegated to third-party design firms. Printing and post-processing can be done in-house or outsourced to third-party manufacturers or service bureaus. Furthermore, the testing of the parts might be done in-house or outsourced to third-party testing companies. Intellectual property protection and AM process security are critical problems in the AM supply chain, and dangers like AM sabotage and intellectual property theft must be handled. Thus, the AM process is a complex network of parties and processes, with excellent coordination and collaboration vital to its success.
2.2 Cyberattacks in AM Industry
These attacks can significantly impact the AM supply chain’s cyber-physical systems, leading to serious consequences.
One notable example is the FLAW3D attack mentioned earlier [14]. This attack involves a firmware Trojan which can control a 3D printer remotely, leading to the production of faulty parts or even data theft. The traditional antivirus software struggles to detect this Trojan and can self-update, making it difficult to remove. This attack emphasizes the need for users and manufacturers in the AM industry to be vigilant and take necessary precautions to prevent such threats.
The research by Belikovetsky et al. [15] demonstrated how the propeller design of a 3D-printed drone could be hacked to cause the drone to crash before takeoff. They used a technique called “digital twinning” to create a virtual model of the drone and simulate the effects of different propeller designs on the drone’s flight performance. This example shows that even the design and manufacturing process of 3D-printed components can be vulnerable to cyber-attacks.
Gupta et al. [12] delves into the unique characteristics of the Additive Manufacturing (AM) supply chain, proposing three distinct models tailored to the industry’s specific nature. The models underscore the importance of a comprehensive view of the AM supply chain, encompassing raw materials, printer hardware, and the virtual supply chain. Throughout the lifecycle of additively manufactured products, intertwining the virtual supply chain (or digital thread) with the physical supply chain fundamentally transforms the AM process into a Cyber-Physical System (CPS). This transformation brings with it the advantages of a CPS but also introduces a new class of attack vectors. Potential attacks at the printer, raw material, design levels and associated risks are discussed. These risks include reverse engineering, counterfeiting, and theft, all of which pose significant threats to the integrity and security of the AM supply chain. Understanding these potential vulnerabilities is crucial for developing robust security measures and safeguarding the AM supply chain from these threats.
2.3 Attack Classification in Additive Manufacturing
This section categorizes the attacks that have impacted the Additive Manufacturing (AM) industry. The classification encompasses side-channel attacks, sabotage incidents, reverse engineering activities, and instances of product counterfeiting.
-
1.
Side-channel attacks: In AM, side-channel attacks are a significant risk. These attacks take advantage of unintended information leakage caused by the AM process, such as electromagnetic radiation and power consumption patterns. Attackers can utilise this information to deduce sensitive details on the AM process, such as the design of the 3D object, the qualities of the material used, and the exact AM parameters. An attacker, for example, could utilise acoustic emanations to determine the geometry of a 3D object being printed by studying the sounds made by the printer’s motors and extruder [16]. Similarly, an attacker may use patterns in power consumption to discover the printing parameters used to create a particular object. These attacks are especially problematic because they can be carried out remotely.
-
2.
Sabotage Attack: Sabotage attacks attempt to compromise the integrity of a product by tampering with its design or manufacturing process. Attackers, for example, may change the 3D model or the printing process parameters to create a weakened or damaged product. This can result in a product that performs differently than intended or offers a safety concern to end users [14]. Using AM technologies in critical infrastructure industries such as aerospace, medical, and automotive enhances the potential impact of sabotage strikes. These attacks could have disastrous implications, such as the failure of an aeroplane or a medical implant. Furthermore, because AM can generate complicated geometries with internal structures, it may be difficult to detect flaws or modifications, making mitigation challenging.
-
3.
Reverse Engineer attack: Reverse engineering is a security issue in AM that requires illegal access to product information such as 3D object design, physical qualities of an object, and AM process limits to infringe on the original product. Attackers may reverse engineer an object using numerous approaches such as 3D scanning, photogrammetry, or manual measurements. They can utilise the digital replica of the object to replicate the original product or modify it for the wrong reasons once they have obtained a digital replica [17]. Attacks on reverse engineering can have severe consequences in industries such as aerospace, defence, and healthcare, where safety-critical components are made utilising AM technology. Attackers may reverse engineer such components to manufacture counterfeit parts or change them to cause problems or failures that can be disastrous. Furthermore, reverse engineering assaults can result in intellectual property theft, in which attackers acquire design information and use it to produce unlicensed reproductions of the original product, incurring financial damages to the manufacturers.
-
4.
Product counterfeiting: Counterfeiters can disrupt the AM supply chain by introducing fake parts or components into production. For example, they may replace genuine materials with defective ones, compromising the end product’s safety and quality. Product counterfeiting is a significant security risk in the AM industry [18]. Attackers can employ AM technology to create counterfeit products that look and work like the real thing, posing substantial financial and safety hazards. For example, counterfeit parts may not fulfil the same safety or performance criteria as genuine ones, resulting in product failure, accidents, and even death.
3 Proposed Framework
Exiting state-of-the-art risk assessment schemes [5, 10, 11] in Additive manufacturing focus on cyber threats and ignore physical risks such as unauthorized access and safety hazards. It is necessary to have a comprehensive framework that integrates both physical and cyber aspects for a better understanding of these vulnerabilities and effective mitigation. Such a framework would enhance security, enable resource prioritization, and foster innovation in AM security solutions, thereby supporting the growth and adoption of AM. To address this gap, a unified risk assessment methodology is proposed to facilitate the implementation of robust measures and reduce the risk of successful attacks. This holistic approach ensures AM’s secure and efficient integration in various industries.
The proposed risk assessment framework (in Figure 2) compromises four phases. The workflow starts with gathering data from various sources. The model’s pre-processing, analysis, and threat assessment in the following phases depend on the data source’s specific features. The first step is to identify and classify AM threats requiring protection. This identification process is critical in determining which components of the AM system need high-security protection due to their value. To do this, a thorough examination of the physical attributes of 3D objects is necessary. This examination includes scrutinising any unintentional changes to the STL files, CAD phases, and any contaminants present. The second step is identifying and analysing potential risks identified in the previous step. This analysis is essential as it helps determine the risk level that each category is exposed to. In this phase, all identified risks are carefully evaluated to determine the potential impact of each threat. A risk assessment phase is carried out to ensure that the threat analysis process is comprehensive. This phase evaluates all the identified risks to determine the likelihood of each threat occurring and the severity of the potential impact on the identified risks. By conducting a risk assessment, it is possible to develop effective strategies to mitigate the risks identified. Ultimately, a thorough threat analysis process is essential to ensure that all risks are protected from potential threats that could compromise the integrity of the AM system.
During the risk assessment phase, we carefully evaluate the probability and severity of each potential threat. We consider several critical criteria, including the source’s trustworthiness, the threat’s severity, and the likelihood of its occurrence. We carefully consider various factors to fully understand the extent of the threat’s potential impact on the organisation. These include the targeting precision of the attack, the area of impact in which it could occur, the potential for collateral damage, the level of stealth involved, and whether or not the attack could be repeated in the future. By carefully analysing these parameters, we can develop a comprehensive understanding of our organisation’s potential risks and take proactive steps to mitigate them.
We developed a comprehensive risk matrix to assess the threat level and its potential impact on our AM system. This matrix enables us to calculate the risks associated with each threat and prioritise them accordingly. By assigning a rating based on the calculated risk score, we can determine which threats pose the most significant risk to our system. As a result, any threat deemed to pose a high level of risk is classified as significant and given immediate attention.
4 Threat Analysis
This section discusses threat categorisations in AM and classifies threats.
4.1 Threats Identification and Categorisation
Additive manufacturing (AM) presents a transformative technology, but its rapid growth creates a complex threat landscape demanding a comprehensive understanding. While existing classifications often focus on specific aspects like cyber-physical vulnerabilities, a broader perspective is crucial to managing risks effectively. This section proposes a novel categorization framework inspired by Yampolskiy et al.’s study [19] on compromised elements and manipulations with crucial enhancements from Cabezali et al.’s categorization of cybersecurity attacks [8]. Figure 3 visually captures this expanded threat landscape, encompassing seven essential categories that span beyond the purely cyber-physical:
-
1.
Manufactured Object: The very essence of AM, the printed object itself, can be compromised. Attackers may introduce intentional flaws during printing or manipulate the object afterwards, significantly impacting its performance. This includes material substitution, surface alterations to hide defects, and biological contamination. Securing the digital realm and the physical object is paramount for AM safety [19].
-
2.
Manufacturing Equipment: AM equipment, including 3D printers and software, are prime targets for malicious actors. Cyber manipulation of control parameters, as seen in past incidents like Stuxnet and the Aurora Experiment, can cause catastrophic damage. Equipment ageing and inadequate maintenance further exacerbate risks, leading to unreliable output, increased breakdowns, and potential safety hazards [19].
-
3.
Environment: The manufacturing environment encompassing the physical area, temperature controls, and materials introduces another layer of vulnerabilities. Contamination and manipulation of temperature/humidity can disrupt the entire AM process. Explosion/implosion, fires, and NBC (Nuclear, Biological, and Chemical) contamination pose environmental, health, and safety risks requiring robust control measures and waste management procedures [19].
-
4.
Intellectual Property (IP): The digital nature of AM operations generates valuable data, making IP a key target. Breaches of CAD files can expose confidential design and material details, while manipulation of STL files or unauthorized access to machines can lead to data theft, sabotage, and financial losses. Intellectual property protection necessitates secure digital infrastructure and physical access control protocols [13, 15, 20, 21].
-
5.
Body Injuries and Diseases: AM may introduce health risks for end-users and operators. Poor design can compromise product integrity, increasing risks of injuries and malfunctions. Neglected equipment maintenance can further endanger product quality and safety. Additionally, exposure to ultrafine particles during printing poses potential respiratory health hazards for AM operators [22,23,24].
-
6.
Human Capital: The success of AM heavily relies on skilled professionals. Threats to human capital, such as ineffective training, insufficient management support, and poor communication, can significantly impact project outcomes, hinder enterprise growth, and reduce overall productivity. Investing in talent development and fostering strong team dynamics are crucial for mitigating these risks [25,26,27].
-
7.
Financial Risk: Financial challenges occur throughout the AM development cycle. Inflation, foreign exchange fluctuations, and insufficient financing can impact project budgets, cash flow, and product viability. Organizations need sound financial planning and risk management strategies to navigate these challenges [28].
This framework offers a comprehensive understanding of the landscape of AM threats, empowering AM stakeholders to develop strategies to mitigate risks and ensure the safe growth of this transformative technology.
4.2 Threat Characteristics
Before analysing the threat qualitatively, we have conducted a threat analysis based on the characteristics highlighted by Yampolskey et al. [19]. These characteristics include targeting precision, area of impact, collateral damage, stealth, and attack repeatability (shown in Fig 4). They are crucial in determining the potential impact of a threat on the Additive Manufacturing (AM) process and supply chain.
-
1.
Targeting Precision: Determines the likelihood of achieving the intended goal, categorized from unknown to critical.
-
2.
Area of Impact: Assesses the potential extent of an attack’s influence, ranging from unknown to critical.
-
3.
Collateral Damage: Examines the unexpected harm to the supply chain or individuals, graded from unknown to critical.
-
4.
Stealth: Measures the ability of an attack to avoid detection, categorized from unknown to critical.
-
5.
Attack Repeatability: Measures the attacker’s capability to repeat an attack, ranging from unknown to critical.
Understanding these characteristics is crucial for a qualitative threat analysis, providing insights into threat severity and potential impact. The assessment will thoroughly analyze threats within the context of these characteristics. Table 1 provides parameter values for assessing the impact level of threats. Each characteristic has corresponding values (0, 1, 10, 50) assigned to the severity levels (Unknown, Low, Medium, High, Critical). These values help quantify the impact level of a threat, facilitating a systematic assessment of potential risks within the defined parameters.
4.3 Qualitative Analysis
This section analyses the identified threats qualitatively and evaluates them for each threat characteristic. Table 2 provides a qualitative analysis and estimation of threats concerning various characteristics. It outlines the perceived levels of targeting precision, area of impact, collateral damage, stealth, and attack repeatability for each threat. Table 3 assigns interpretation values (Unknown, Low, Medium, High, Critical) to the threat levels, providing a comprehensive understanding of their potential impact.
-
1.
Altering Physical properties to Object: The altering physical properties of 3D objects can have a high severity level regarding targeting precision, impact, and attack repeatability. Attackers can specifically target critical areas, causing significant damage to the 3D object, with the potential for precise and extensive harm. The impact is critical, as it can compromise structural integrity and functionality, leading to catastrophic consequences. Collateral damage is expected to be critical, affecting surrounding components and structures. The threat exhibits medium stealth, making detection challenging, but physical evidence of tampering might be detectable. Attack repeatability is critical, posing a continuous and pervasive risk of damage to other objects.
-
2.
NBC contamination to object: The threat of NBC contamination to an object exhibits low targeting precision, suggesting a lower chance of precise damage to the 3D object. However, it poses a high level of impact, leading to severe damage. Collateral damage is also high, affecting nearby components and systems. The threat has low stealth, making it relatively detectable. The high attack repeatability indicates that it can be repeated with moderate effort.
-
3.
Alteration in Electronic circuit: Any modification in the Electronic circuit of 3D equipment or machine can have high targeting precision, leading to specific damage to critical areas. It also has a high level of impact, causing significant harm to the 3D object. Collateral damage is low, limiting its impact on nearby components. The threat has high stealth, making detection challenging, and attack repeatability is also high.
-
4.
Ageing or Outdated 3D Equipment: The targeting precision for this threat is medium, leading to damage that may not be highly precise. It exhibits a low level of impact, causing limited harm to the 3D equipment’s overall lifespan. Collateral damage is also low, affecting only specific areas. The threat’s stealth and attack repeatability is medium, making it moderately detectable and repeatable.
-
5.
Irreparable damage threat to 3D equipment: This threat demonstrates medium targeting precision, leading to specific damage to critical components. It also has a low level of impact, causing limited harm but potentially rendering the equipment irreparable. Collateral damage is low, affecting only specific components. The threat’s stealth and attack repeatability are medium.
-
6.
Explosion/Implosion to 3D equipment: This threat poses medium targeting precision, leading to damage that affects electrical and mechanical components. It exhibits a medium level of impact, causing moderate harm to the 3D equipment. Collateral damage is medium, affecting both electrical and mechanical systems. The threat’s stealth is low, making detection relatively easier. Attack repeatability is also low.
-
7.
Explosion/Implosion to the environment: The targeting precision for this threat is low, leading to random or imprecise damage. It poses a medium level of impact, causing moderate environmental harm. Collateral damage is also medium, affecting surrounding systems. The threat exhibits low stealth, making detection relatively easier. Attack repeatability is low.
-
8.
Fire threat to the environment: This threat has low targeting precision, leading to random or imprecise damage. It exhibits a medium level of impact, causing moderate environmental harm. Collateral damage is medium, affecting surrounding structures. The threat’s stealth is low, making it relatively detectable, and attack repeatability is medium.
-
9.
NBC’s contamination to the environment: The targeting precision for this threat is low, leading to random or imprecise damage. It poses a medium level of impact, causing moderate environmental harm. Collateral damage is also medium, affecting nearby structures. The threat exhibits medium stealth, making detection moderately challenging. Attack repeatability is medium.
-
10.
Unauthorised access to CAD model phase: This threat poses high targeting precision, leading to specific vulnerabilities in the CAD model during its design phase. It also exhibits a high level of impact, as any issues or vulnerabilities at this stage can significantly impact the final product. Collateral damage is high, potentially affecting other parts of the design or project. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is also medium.
-
11.
Unauthorised access to STL file: The targeting precision for this threat is high, leading to specific vulnerabilities in the STL file format used for 3D printing. However, it exhibits a low level of impact, causing limited harm to the final product. Collateral damage is low, affecting only specific aspects of the STL file. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is low.
-
12.
Unauthorised access to in Toolpath: This threat demonstrates high targeting precision, leading to specific vulnerabilities in the toolpath used for 3D printing. It has a medium impact, causing moderate harm to the final product. Collateral damage is low, affecting only specific sections of the toolpath. The threat’s stealth is low, making detection relatively easier. Attack repeatability is low.
-
13.
Unauthorised access to physical machine: This threat poses high targeting precision, leading to specific vulnerabilities in the physical 3D printing machine. It exhibits a low level of impact, causing limited harm to the machine. Collateral damage is medium, potentially affecting other parts of the machine. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is low.
-
14.
Defective design: This threat demonstrates medium targeting precision, leading to specific issues and vulnerabilities due to defective design. It has a critical impact, causing severe harm to the final product’s functionality and integrity. Collateral damage is high, potentially affecting other parts of the design or project. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is high.
-
15.
Defects during the manufacturing process: This risk poses high targeting precision, leading to specific defects introduced during the 3D printing process. It exhibits a critical level of impact, causing severe harm to the final product’s quality and functionality. Collateral damage is critical, potentially affecting multiple aspects of the manufacturing process. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is high.
-
16.
Exposure to ultrafine particles: The targeting precision for this threat is high, leading to specific vulnerabilities due to exposure to ultrafine particles during the 3D printing process. It has a high impact, causing significant harm to the final product’s structural integrity. Collateral damage is low, affecting only specific aspects of the printing process. The threat’s stealth is low, making detection relatively easier. Attack repeatability is low.
-
17.
Ineffective training plan: This threat demonstrates high targeting precision, leading to specific vulnerabilities caused by an ineffective training plan for personnel involved in the 3D printing process. It exhibits a medium level of impact, causing moderate harm to overall productivity and efficiency. Collateral damage is low, affecting only specific areas of the training plan. The threat’s stealth is low, making detection relatively easier. Attack repeatability is low.
-
18.
Insufficient management support: This threat poses high targeting precision, leading to specific vulnerabilities resulting from insufficient management support for the 3D printing project. It exhibits a low level of impact, causing limited harm to the overall project. Collateral damage is medium, potentially affecting other aspects of the project. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is low.
-
19.
Poor communication: This threat demonstrates medium targeting precision, leading to specific issues and vulnerabilities caused by poor communication among team members in the 3D printing project. It has a critical level of impact, causing severe harm to project coordination and efficiency. Collateral damage is high, affecting other aspects of the project. The threat’s stealth is high, making detection challenging. Attack repeatability is low.
-
20.
Inflation threat: The targeting precision for this threat is medium, leading to random or imprecise impacts caused by inflation or changes in the cost of materials or resources. It exhibits a high level of impact, causing significant economic harm to the project. Collateral damage is low, affecting only specific aspects of the project. The threat’s stealth is low, making it relatively detectable. Attack repeatability is low.
-
21.
Foreign exchange rate fluctuation: This threat poses high targeting precision, leading to specific impacts caused by fluctuations in foreign exchange rates. It exhibits a low level of impact, causing limited economic harm to the project. Collateral damage is medium, potentially affecting other aspects of the project. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is low.
-
22.
Insufficient financing: This threat demonstrates high targeting precision, leading to specific issues caused by insufficient financing for the 3D printing project. It exhibits a high level of impact, causing significant economic harm and potential project delays. Collateral damage is critical, potentially affecting other aspects of the project. The threat’s stealth is medium, making detection moderately challenging. Attack repeatability is low.
4.4 Threat Impact Decay
Iklody et al. [29] highlight the phenomenon wherein the impact of indicators of compromise (IOCs) diminishes over time, suggesting that their effectiveness in detecting and addressing security threats weakens as time elapses. This concept is quantified through a decay function outlined in Equation (1).
Here, \(f(x, \delta , \tau )\) represents the decay function, characterized by parameters \(\tau\) and \(\delta\), where \(\tau\) signifies the active time. As time progresses (x), the value of f(x) decreases, ultimately reaching 0, with \(\delta\) determining the decay rate for an IOC.
In the context of Additive Manufacturing (AM), the lifespan of a threat, referred to as the IOC’s active time, is a critical factor influencing threat severity. Unobserved or unmonitored IOCs diminish in severity over time. The IOC’s lifetime is estimated based on its severity and decay rate. A dynamic approach to IOC lifetime is considered, as presented in Table 4, illustrating a lifespan scale for various IOCs. The impact of an IOC rapidly decreases for lower values of \(\delta\), while higher \(\delta\) values result in a more gradual decrease. Critical IOCs, identifying severe threats, are assumed to be active for up to 21 days, significantly affecting the AM supply chain. Specific values of \(\delta\) are set accordingly: \(\delta = 0.25\) for critical and high IOCs, \(\delta = 0.5\) for medium IOCs, and \(\delta = 1\) for all other IOCs. For instance, a significant IOC maintains its value for approximately five days. Beyond that, decay initiates, reaching zero after 21 days (Fig. 5).
4.5 Impact Agrregation
After successfully estimating the impact parameters, the aggregated impact is assessed using the following linear equation:
The equation (2) denotes the aggregate impact score \(Imp_{aggr_i}\) for \(i^{th}\) Indicator of Compromise (IOC), where \(X_{tp_i}\), \(X_{ai_i}\), \(X_{cd_i}\), \(X_{s_i}\), and \(X_{ar_i}\) represent severity scores for targeting precision, area of impact, collateral damage, stealth, and attack repeatability, respectively. Each severity score is weighted by \(w_{tp_i}\), \(w_{ai_i}\), \(w_{cd_i}\), \(w_{s_i}\), and \(w_{ar_i}\) to reflect their relative importance in determining the overall impact of the IOC. The equation offers a comprehensive assessment of the potential impact of the IOC, considering multiple dimensions of threat severity. The weight can be adjusted according to specific needs. Considering that the parameters area of impact and collateral damage may lead to more severe consequences, we set weights as \(w_{ai} = w_{cd} = 10\) and \(w_{tp} = w_s = w_{ar} = 1\).
We calculate the overall impact of the threat using Equation (3).
Here, the impact (\(\text {Impact}_i\)) of the \(i^{th}\) IOC is determined by aggregating severity scores for targeting precision (\(X_{tp_i}\)), area of impact (\(X_{ai_i}\)), collateral damage (\(X_{cd_i}\)), stealth (\(X_s\)), and attack repeatability (\(X_{ar_i}\)), each scaled by a factor of 10. The resulting sum is then multiplied by the decay rate (\(d_i\)), which depends on parameters \(\tau\) and \(\delta\) from Equation (2). This decay rate reflects the diminishing impact of the IOC over time. Finally, the aggregated impact level estimates the overall threat impact level, as detailed in Table 5.
5 Threat Likelihood
This section explores the likelihood of threats causing disruptions in the AM process. Estimating likelihood involves evaluating threat parameters: data source reliability (\(Rel_i\)), frequency of IOC provided (\(Occur_i\)), and severity assigned by the data source (\(Sev_i\)). Equation (4) calculates the aggregated likelihood:
Here, \(w_i\) represents parameter weights, which are adjustable based on specific needs. Assuming equal importance (\(w_R=w_S=w_O=1\)), the equation simplifies to:
5.1 Reliability
Trusting a data source becomes challenging due to false positive IOCs [30]. Our framework assesses source reliability by quantifying intelligence feed quality through extensiveness (how much context a source provides IOCs), timeliness (how fast a source provides a threat), and completeness (how much data the source contributes to the total set of IOCs),
Let \(Rel_k\) represent the relevance score of the \(k^{th}\) data source. This score is calculated based on the weighted average of three parameters: \(p_{ex_k}\), \(p_{t_k}\), and \(p_{c_k}\), each representing the relevance of the risk in terms of extensiveness, timeliness, and completeness, respectively. The weights assigned to these parameters are denoted by \(w_{ex_k}\), \(w_{t_k}\), and \(w_{c_k}\), reflecting their relative importance in determining the overall relevance score. The relevance score \(Rel_k\) is evaluated in Equation (6).
where n is the number of IOCs, i represents each IOC, and \(w_i\) and \(p_{i_k}\) denote the weight and relevance score of the \(i^{th}\) IOC for the \(k^{th}\) data source, respectively. The weights and relevance scores are chosen such that \(w_i \in \{w_{ex}, w_{t}, w_{c}\}\) and \(p_{i_k} \in \{p_{ex_k}, p_{t_k}, p_{c_k}\}\), indicating their belongingness to extensiveness, timeliness and completeness, respectively. The weights (0.8, 1.0, 0.8) for extensiveness (\(w_{ex_k}\)), timeliness (\(w_{t_k}\)), and completeness (\(w_{c_k}\)) consider their impact on physical, security, and financial aspects, reflecting severity. Trust levels are quantified as in Table 6.
The parameters of data sources, namely Extensiveness, Timeliness, and Completeness, are evaluated using the following criteria:
-
Extensiveness: It describes how much context an intelligence feed provides to assist the IOC in describing specific characteristics of the information. The context can be how many optional and required properties are filled by the data source as defined by the CTI sharing standards. The estimation of the extensiveness parameter is computed as \(\sum _{i=0}^z{\frac{o_i}{max(y_i)}}\), where \(o_i\) denotes the number of filled-in optional properties in a specific IOC, and \(max(y_i)\) represents the maximum number of contextual properties.
-
Timeliness: It is the time between the occurrence of an attack vector and the indicators associated with it in the feed [31]. Some authors termed it latency or speed [32]. The value of a feed used in active defence equipment, such as an intrusion detection mechanism, can be determined by its timeliness. Timeliness depends on how fast a data source shares its IOCs compared to other data sources. If a specific data source is slow in sharing and provides the same IOCs later than another, they could be obsolete, and we assign less source reliability to it. The timeliness is evaluated as \(p_T=\frac{1}{z} \sum _{i=0}^{z} \frac{min(t_i)}{ts_i}\), where \(min(t_i)\) is the timestamp at which the fastest data source sighted IOC, \(ts_i\) is the time that data source s has sighted IOC and is the number of IOCs shared by the data source.
-
Completeness: It states how much a data source contributes to the total set of IOCs, including all distinct IOCs provided by the data source [33]. A big part of the IOC set provided by a single data source indicates that the source is precious for the final score evaluation. Instead of focusing on data source quality, this parameter focuses more on the quantity of a data source. The completeness parameter is evaluated \(p_C=\frac{z_s}{z_{total}}\), where \(z_s\) is the total number of IOCs shared by data source s and \(z_{total}\) is the total number of distinct IOCs of all data sources.
5.2 Threat severity
The framework assesses a threat’s severity based on the score assigned by the specific data source, denoted as \(Sev_{score_k}\) for the \(i^{th}\) IOC. We quantify the score \(Sev_{score_k}\) from low to critical, reflecting the seriousness of the threat as shown in Table 7. This score provides valuable insight into the potential impact of each threat.
We consider data feeds from multiple data sources, each potentially assigning a severity score (\(Sev_{score_i}^k\)) to the \(i^{th}\) IOC type. Equation (7) defines a method for calculating the average severity score for a specific type of Indicator of Compromise (IOC), denoted by "i".
5.3 Occurrence
The third factor influencing likelihood is the recorded prevalence of IOCs reported by the data source’s threat feed. We analyze the \(i^{th}\) IOC occurrence across all data sources and consider the average number of times it has been observed. This average occurrence, calculated in equation (8), provides insight into how frequently this type of IOC has been encountered historically.
Equation (8) represents the average frequency of a specific Indicator of Compromise (IOC) type denoted by "i" across all the data sources considered in our analysis. We calculate this frequency by averaging the individual occurrences (\(Occur_i^k\)) of the \(i^{th}\) IOC type within each data source (k). In other words, this equation shows how frequently the \(i^{th}\) IOC type has been historically observed on average across all the data sources included in our analysis. We quantify the \(\text {Occur}_i\) score scale from 0-100 (shown in Tables 8, 9).
6 Risk Estimation
To maintain a secure and safe additive manufacturing supply chain, it is crucial to understand the risks associated with each operation. Our proposed framework considers two important factors determining this risk level: the likelihood of a threat occurring \(likelihood_i\) and the potential impact \(Impact_i\) that threat would have. The risk assessment calculation is based on a specific equation, referred to as equation (9). This equation plays a key role in determining the level of protection measures that need to be implemented throughout the additive manufacturing supply chain.
Table 10 summarizes the metrics utilized to assess the impact of threats and the corresponding threat levels employed in determining the overall risk level. This proposal classifies risk into unknown, low, moderate, high, and critical risk levels based on threat severity. Consequently, the risk with an unknown risk level would not necessitate specific security requirements. The remaining four risk levels (low, moderate, high, and critical) would mandate the implementation of a substantial degree of security measures.
7 Experimental Result and Validation
This section presents the experiments’ outcomes to evaluate the proposed framework. The framework was rigorously tested using MITRE CVE lists as the basis for assessment. The following subsections detail the experimental setup, methodology, and the key findings obtained during the evaluation.
7.1 Experiments results
The proposed risk assessment system categorizes risks into seven distinct classes and identifies a total of twenty-two AM-related risks. An in-depth analysis of the impact of each risk on threat characteristics, including precision targeting, area of effect, collateral damage, stealth, and attack repetition, has been conducted quantitatively. The impact of each threat has been thoroughly measured and quantified, leading to the calculation of final threat values. Table 11 provides a comprehensive summary of the threat impact and likelihood scores, along with their corresponding values. This suggested approach gives a more accurate and thorough understanding of the potential risks by considering various threat characteristics. Quantitative analysis enables a more precise assessment of the risks, providing valuable insights into their possible consequences and probabilities. This approach facilitates a thorough evaluation of the risk landscape in AM and enhances the overall risk management process. Considering the diverse threat characteristics, the proposed system contributes to a more robust and comprehensive risk assessment, offering key advantages in effectively identifying and mitigating potential risks.
Threat Impact: Table 11 shows that many threats associated with AM represent a significant risk to the manufacturing of 3D objects. The physical property of the 3D object has been identified as the most serious concern, with the possibility of manipulation during or after manufacturing. This finding emphasises the significance of adequately monitoring the manufacturing process to avoid illegally manipulating the 3D object. Contamination of the 3D object during or after manufacturing is another serious concern highlighted. The exposure of this risk varies according to the source material and AM technique employed. The researchers underline the need to manage and store raw materials properly to avoid contamination and ensure consistent quality of the 3D object. Threats to digital files and CAD models utilised in the AM process, including theft, encryption, and partial geometric data loss, are also identified in the study. These risks emphasise the importance of data security and the necessity of putting robust data protection procedures in place to protect intellectual property and avoid data breaches.
Furthermore, the paper stresses the need for appropriate communication and coordination among team members, the organisation, and consumers to prevent mistakes and minimise risks. Inadequate communication may result in design flaws, faulty production, and legal action against the product designer. Overall, the findings of this study give helpful information on the possible risks and vulnerabilities linked with AM. The suggested methodology provides a complete approach to analysing and managing assets in the context of AM. The findings help enterprises prioritise security efforts and adopt comprehensive methods to reduce risks and ensure secure and efficient 3D object development.
Table 11 discusses the threat’s likelihood as well. Some of the risks that have been found pose significant risks in AM systems. These risks include physical property damage to 3D objects, nuclear, biological, and chemical (NBC) attacks on 3D objects, the risks associated with CAD model phase cybersecurity and intellectual property (CS &IP), and the threat of BI &D due to defective design.
Risk: Table 12 summarises each threat’s risk value, level, and rank. The numerical value and severity (severe, high, moderate, low, unknown) of the risk value and risk level are based on the impact value and risk value, as given in Table 10. The risk level determines the priority of risk, with more priority given to threats with a higher risk level. The threat impact score determines the priority when two threats have the same risk level. The most significant risks discovered to be “Physical property danger to 3D object,” “BI &D threat owing to poor design,” “CS &IP risk in CAD model phase,” and “NBC threat to 3D object,” rated first, second, third, and fourth, respectively. As a result, measures must be taken to limit and prevent these risks from realising. Fire threat to the environment, E/I threat to the environment, E/I threat to 3D equipment, Reduced lifespan threat to 3D equipment, and Irreparable damage threat to 3D equipment, on the other hand, were all low-risk level threats. While these risks may not constitute an immediate threat to the 3D printing process, they should not be overlooked since they have the possibility of causing long-term harm and disrupting production. Overall, the findings of this research show the need to employ comprehensive risk management measures in 3D printing procedures. Organisations may proactively try to prevent risks, preserve their equipment and assets, and maintain the smooth functioning of their 3D printing operations by detecting possible threats and analysing their effect.
The risk assessment system guarantees that the analysis is systematic and consistent, allowing participants to make intelligent decisions based on objective and reliable facts. The proposed method gives AM organisations helpful information regarding the related vulnerabilities and risks associated with assets, allowing them to focus their security efforts and reduce possible losses.
7.2 Testing Setup
The proposed risk assessment approach is validated using a dataset of MITRE Corporation’s Common Vulnerabilities and Exposures (CVE) repository, which has been maintained and managed for the past 26 years (1999-2023). The CVE database lists publicly known cybersecurity vulnerabilities and exposures linked with computer security. The information is gathered in the open standard file format and data interchange format (JSON), a popular format for storing and transmitting data. The collection is 1084MB in size and contains a total of 249,816 CVEs from 1999 to 21 March 2023. Each CVE in the dataset is represented by its intrinsic characteristics, which may contain a description of the vulnerability, its severity level, the impacted software or hardware systems, and other pertinent information. The National Vulnerability Database associates each CVE in the collection with a Common Vulnerability Scoring System (CVSS) base score (NVD). The CVSS is a standardised scoring system that offers a quantifiable evaluation of a vulnerability’s severity. Table 13 summarises the dataset.
We evaluated the efficacy of our proposed threat-centric risk assessment framework using the MITRE CVE dataset. The MITRE CVE dataset includes Common Vulnerabilities and Exposures (CVEs) and impact metrics, such as Common Vulnerability Scoring System (CVSS) scores and relevant metadata. The CVSS scores provided by the dataset range from "None" to "Critical," with numerical values varying from 0 to 10, where higher scores indicate more severe vulnerabilities.
To perform our analysis, we leveraged the CVSS scores and metadata from the MITRE CVE dataset and applied our proposed framework to analyze the aggregated CVEs qualitatively. This framework incorporates diverse threat characteristics, including precision targeting, area of impact, collateral damage, stealth, and attack repeatability, to comprehensively evaluate the threat impact linked to each vulnerability. To estimate the likelihood value for each risk, we considered a trustworthiness score of 0.8 for the data sources. Additionally, the frequency was calculated using the available metadata, and the Indicator of Compromise (IOC) severity was determined based on the CVSS score associated with each vulnerability. By employing these metrics, we were able to assess the potential threat level and impact of each vulnerability in the context of additive manufacturing. For the experiments, we utilized a Windows 10 platform with an Intel(R) Core(TM) i7-10610U CPU operating at 1.80 GHz, 2.30 GHz, and 32 GB of RAM. The Python 3.7 software platform was employed to code and implement our proposed framework.
By applying our threat-centric risk assessment framework to the MITRE CVE dataset, we aimed to gain valuable insights into the potential risks posed by various vulnerabilities in the context of additive manufacturing. This analysis allows us to identify critical areas of concern and prioritize mitigation efforts to enhance the security and resilience of AM supply chains against potential cyber threats.
Table 14 summarises the CVEs list with the following details: CVE score, Threat impact level, likelihood value and risk level. CVE score is the NVD assigned score ranging from 0-10, where 0 means low and 10 means critical. Threat impact level and likelihood values are estimated using the proposed risk assessment system, and risk level is determined by the risk matrix defined in Table 10. Severe Common Vulnerabilities and Exposures (CVEs) are summarised in Table 14, along with the following data: CVE score, threat impact level, likelihood value, and risk level associated with each CVE. The National Vulnerability Database (NVD) assigns the CVE score on a scale of 0-10, with 0 denoting a low severity rating and 10 denoting a critical severity rating. The proposed risk assessment technique was utilised to estimate the threat impact level and likelihood values. The risk level was obtained by reviewing the matrix in Table 10.
7.3 Findings
From Table 14, it has been evident that code injection poses a significant threat to the AM supply chain. This attack involves malicious code, such as viruses or malware, injected into legitimate software or hardware components crucial in the AM supply chain. As these compromised components are distributed throughout the supply chain, the malicious code can spread to other systems, leading to widespread damage and potential disruptions in the manufacturing process. Several CVEs, including CVE-2021-21480, CVE-2009-4046, CVE-2009-4037, CVE-2018-20187, and CVE-2018-19436, have been identified as critical or high-risk threats related to code injection in the AM supply chain. These vulnerabilities underscore the critical need to address and mitigate code injection risks to safeguard the integrity and security of the entire supply chain.
The second prominent risk observed in the AM supply chain is unauthorised network access and improper authentication. This risk involves an attacker gaining unauthorized access to the AM supply chain’s network or exploiting weaknesses in the authentication process. As a result, sensitive information can be stolen, and the network can be compromised, leading to potential damage and security breaches. Several CVEs, including CVE-2021-2238, CVE-2018-13804, CVE-2017-9630, CVE-2022-20817, and CVE-2019-13945, have highlighted the risk of unauthorised network access in the AM supply chain. These vulnerabilities have been rated as high or medium risk, signifying the potential impact of such security breaches on the overall security and stability of the AM supply chain.
Proactive measures must be taken to address these identified risks and strengthen the security of the AM supply chain. Robust cybersecurity protocols, such as regular security audits, network monitoring, and intrusion detection systems, can help detect and prevent code injection attempts and unauthorized network access. Implementing robust authentication mechanisms, access controls, and encryption techniques can fortify the network against potential threats. Regular staff training and awareness programs can also help educate employees about cybersecurity best practices, reducing the risk of human-related vulnerabilities.
By proactively addressing these risks, stakeholders in the AM supply chain can foster a more resilient and secure environment for AM processes. Mitigating these vulnerabilities will protect sensitive data and intellectual property and contribute to the overall efficiency and reputation of the AM supply chain.
7.4 Comparisons
The primary advantage of our proposed risk assessment framework lies in its comprehensive coverage of potential risks associated with additive manufacturing. Unlike existing methods by Yampolkiy et al. [19] and Moreno-Cabezali [8], which focus on specific aspects of the risk landscape, our framework encompasses both cyber-physical and cyber attacks on additive manufacturing processes. By considering both cyber-physical attacks (where digital systems manipulate physical processes) and cyber attacks (targeting digital aspects of additive manufacturing), our risk assessment framework provides a holistic approach to identifying, analyzing, and evaluating vulnerabilities and threats in 3D printing technologies.
The second notable advantage of our proposed risk assessment framework is its incorporation of MITRE CVEs for testing, enhancing the credibility of the assessment process. By evaluating the framework against known vulnerabilities in the MITRE CVE database, we can validate its effectiveness in identifying and mitigating risks associated with additive manufacturing. Using MITRE CVEs as a reference provides real-world examples of cybersecurity vulnerabilities and exposures. This approach ensures that our risk assessment is grounded in practical experiences and aligns with the challenges faced by industries in additive manufacturing.
8 Limitations and Future Scope
Although the proposed threat-centric risk assessment framework makes a valuable contribution to the security of the AM supply chain, certain limitations must be considered.
-
Scope Limitation: The framework identifies and evaluates potential threats based on a predetermined set of criteria, potentially overlooking emerging threats or those not covered within the defined scope. This could lead to gaps in threat coverage, leaving specific vulnerabilities to be addressed.
-
Data Source Dependency: The estimation of threat likelihood relies on data source analysis, which may introduce bias or inaccuracies depending on the quality and availability of the data sources. Over-reliance on specific data sources could skew the assessment results and impact the overall effectiveness of the framework.
-
Validation Methodology: While experimental validation with the MITRE CVEs dataset demonstrates the framework’s effectiveness in detecting severe vulnerabilities, it may not capture the full spectrum of threats encountered in real-world AM settings. The validation approach may need further refinement to ensure comprehensive coverage of potential threats.
-
Dependency on Third-Party Providers: Adopting cloud-based solutions often involves relying on third-party providers for infrastructure, platform, or software services. This dependency introduces additional risks related to service disruptions, vendor lock-in, and compliance with regulatory requirements [34, 35]. Organizations must carefully evaluate the security posture of cloud service providers and establish clear contractual agreements to mitigate these risks effectively. However, maintaining oversight and accountability over third-party providers can be challenging, especially in multi-tenant cloud environments.
-
Post-Processing Complexity: Post-processing in additive manufacturing (AM) involves various techniques such as cleaning, finishing, and surface treatment, each introducing its own set of risks. The complexity of these activities can make it challenging to identify and mitigate specific risks effectively [36]. The lack of standardized protocols and guidelines for post-processing further exacerbates this issue, making it challenging to address risks comprehensively. Therefore, it is essential to develop comprehensive risk mitigation strategies that account for the complexity of post-processing in AM.
Addressing these limitations is an essential step towards enhancing the risk assessment framework’s robustness and applicability in real-world AM environments. However, it is important to note that this is an ongoing process. Further research and refinement are needed to overcome these challenges and optimize the framework’s effectiveness in enhancing the security of the AM supply chain.
9 Conclusions
This paper introduced a threat-centric risk assessment framework to strengthen the security of the AM supply chain. The framework systematically identifies and evaluates potential threats, categorizing them into twenty-two distinct risks that could pose significant challenges to AM operations. Qualitative assessment, incorporating threat characteristics, aids in measuring the potential impact of each threat. The framework generates an overall risk profile by estimating the likelihood of threats through data source analysis. Experimental validation with the MITRE Common Vulnerabilities and Exposures (CVEs) dataset demonstrates the framework’s effectiveness in detecting severe CVEs that could lead to substantial damage in AM settings. This comprehensive and systematic approach empowers the AM industry to implement targeted security measures, enhancing the resilience and security of the AM supply chain.
Data availability
The data that support the findings of this study are available from the corresponding author upon request.
References
Haleem A, Javaid M (2019) Additive manufacturing applications in industry 4.0: a review. Journal of Industrial Integration and Management 4(04):1930001
Pozzi R, Rossi T, Secchi R (2023) Industry 4.0 technologies: Critical success factors for implementation and improvements in manufacturing companies. Production Planning & Control 34(2):139–158
Kumar M, Epiphaniou G, Maple C (2023) “Leveraging semantic relationships to prioritise indicators of compromise in additive manufacturing systems”. In: International Conference on Applied Cryptography and Network Security, Springer, pp. 321–335
Dietz M, Pernul G (2020) Unleashing the digital twin’s potential for ics security. IEEE Security & Privacy 18(4):20–27
Campbell TA, Ivanova OS (2013) Additive manufacturing as a disruptive technology: Implications of three-dimensional printing. Technology & Innovation 15(1):67–79
Kumar M, Chand S (2021) A provable secure and lightweight smart healthcare cyber-physical system with public verifiability. IEEE Systems Journal 16(4):5501–5508
Kumar M, Epiphaniou G, Maple C (2023) “A novel intelligence and information acquisition system for managing indicators of compromise in distributed responsive manufacturing systems”. CADE 2023
Moreno-Cabezali BM, Fernandez-Crehuet JM (2020) Application of a fuzzy-logic based model for risk assessment in additive manufacturing r &d projects. Computers & Industrial Engineering 145:106529
Cómbita LF, Giraldo J, Cárdenas AA, Quijano N (2015) “Response and reconfiguration of cyber-physical control systems: A survey”. In: 2015 IEEE 2nd Colombian Conference on Automatic Control (CCAC), IEEE, pp. 1–6
DeSmit Z, Elhabashy AE, Wells LJ, Camelio JA (2016) Cyber-physical vulnerability assessment in manufacturing systems. Procedia manufacturing 5:1060–1074
Padmanabhan A, Zhang J (2018) Cybersecurity risks and mitigation strategies in additive manufacturing. Progress in Additive Manufacturing 3:87–93
Gupta N, Tiwari A, Bukkapatnam ST, Karri R (2020) Additive manufacturing cyber-physical system: Supply chain cybersecurity and risks. IEEE Access 8:47322–47333
Sturm LD, Williams CB, Camelio JA, White J, Parker R (2017) Cyber-physical vulnerabilities in additive manufacturing systems: A case study attack on the. stl file with human subjects. Journal of Manufacturing Systems 44:154–164
Pearce H, Yanamandra K, Gupta N, Karri R (2022) Flaw3d: A trojan-based cyber attack on the physical outcomes of additive manufacturing. IEEE/ASME Transactions on Mechatronics 27(6):5361–5370
Belikovetsky S, Yampolskiy M, Toh J, Gatlin J, Elovici Y (2017) “dr0wned-cyber-physical attack with additive manufacturing.”. In: WOOT
Pearce H, Surabhi VR, Krishnamurthy P, Trujillo J, Karri R, Khorrami F (2022) Detecting hardware trojans in pcbs using side channel loopbacks. IEEE Transactions on Very Large Scale Integration (VLSI) Systems 30(7):926–937
Moore S, Armstrong P, McDonald T, Yampolskiy M (2016) “Vulnerability analysis of desktop 3d printer software”. In: 2016 Resilience Week (RWS), IEEE, pp. 46–51
Song C, Lin F, Ba Z, Ren K, Zhou C, Xu W (2016) “My smartphone knows what you print: Exploring smartphone-based side-channel attacks against 3d printers”. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp. 895–907
Yampolskiy M, Skjellum A, Kretzschmar M, Overfelt RA, Sloan KR, Yasinsac A (2016) Using 3d printers as weapons. International Journal of Critical Infrastructure Protection 14:58–71
Sturm LD, Williams CB, Camelio JA, White J, Parker R (2014) “Cyber-physical vulnerabilities in additive manufacturing systems”. In: 2014 International Solid Freeform Fabrication Symposium, University of Texas at Austin
Wu D, Ren A, Zhang W, Fan F, Liu P, Fu X, Terpenny J (2018) Cybersecurity for digital manufacturing. Journal of manufacturing systems 48:3–12
Zhang Q, Sharma G, Wong JP, Davis AY, Black MS, Biswas P, Weber RJ (2018) Investigating particle emissions and aerosol dynamics from a consumer fused deposition modeling 3d printer with a lognormal moment aerosol model. Aerosol Science and Technology 52(10):1099–1111
Harris A (2015) “The effects of in-home 3d printing on product liability law”. Journal of Science Policy & Governance
du Preez S, de Beer DJ, du Plessis JL (2018) Titanium powders used in powder bed fusion: Their relevance to respiratory health. South African Journal of Industrial Engineering 29(4):94–102
Biswas DD (2018) How companies maintain their workforce to gain a sustainable competitive advantage. International Journal of Management 9(1)
Abudi G (2013) “Managing communications effectively and efficiently”. Project Management Institute
Loonam J, McDonagh J, Kumar V, O’Regan N (2014) Top managers & information systems:‘crossing the rubicon’! Strategic Change 23(3–4):205–224
Boudt K, Neely CJ, Sercu P, Wauters M (2019) The response of multinationals’ foreign exchange rate exposure to macroeconomic news. Journal of International Money and Finance 94:32–47
Iklody A, Wagener G, Dulaunoy A, Mokaddem S, Wagner C (2018) “Decaying indicators of compromise”. arXiv preprint arXiv:1803.11052
Schaberreiter T, Kupfersberger V, Rantos K, Spyros A, Papanikolaou A, Ilioudis C, Quirchmayr G (2019) “A quantitative evaluation of trust in the quality of cyber threat intelligence sources”. In: Proceedings of the 14th International Conference on Availability, Reliability and Security, pp. 1–10
Bouwman X, Griffioen H, Egbers J, Doerr C, Klievink B, Van Eeten M (2020) “A different cup of ti? the added value of commercial threat intelligence”. In: Proceedings of the 29th USENIX Conference on Security Symposium, pp. 433–450
Li VG, Dunn M, Pearce P, McCoy D, Voelker GM, Savage S (2019) “Reading the tea leaves: A comparative analysis of threat intelligence”. In: 28th USENIX security symposium (USENIX Security 19), pp. 851–867
Sillaber C, Sauerwein C, Mussmann A, Breu R (2016) “Data quality challenges and future research directions in threat intelligence sharing practice”. In: Proceedings of the 2016 ACM on Workshop on Information Sharing and Collaborative Security, pp. 65–70
Kumar M, Chand S (2020) A lightweight cloud-assisted identity-based anonymous authentication and key agreement protocol for secure wireless body area network. IEEE Systems Journal 15(2):2779–2786
Kumar M, Chand S (2020) A secure and efficient cloud-centric internet-of-medical-things-enabled smart healthcare system with public verifiability. IEEE Internet of Things Journal 7(10):10650–10659
Piedra-Cascón W, Krishnamurthy VR, Att W, Revilla-León M (2021) 3d printing parameters, supporting structures, slicing, and post-processing procedures of vat-polymerization additive manufacturing technologies: A narrative review. Journal of Dentistry 109:103630
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Kumar, M., Epiphaniou, G. & Maple, C. Comprehensive Threat Analysis in Additive Manufacturing Supply Chain: A Hybrid Qualitative and Quantitative Risk Assessment Framework. Prod. Eng. Res. Devel. (2024). https://doi.org/10.1007/s11740-024-01283-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11740-024-01283-1