Abstract
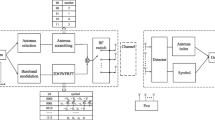
This paper proposes a novel modulated symbols-based one-time pad (SOTP) secure transmission scheme using physical layer keys. Unlike classical physical layer key generation and exclusive OR (XOR) encryption in the discrete binary space, we design a framework for modulated symbols-based one-time pad (OTP) encryption, where the cryptographic primitive and mathematical model of SOTP is given to build a practical cryptographic protocol. Compared with existing physical layer encryption (PLE) schemes, we provide rigorous proof that the framework can meet perfect secrecy and correctness requirements. In addition, we provide a specific scheme of physical layer OTP secure transmission for quadrature amplitude modulation (QAM) and phase-shift keying (PSK) symbols based on physical layer keys. This scheme realizes the unification of bit encryption and symbol encryption, which can adaptively select the quantization level according to the signal-to-noise ratio (SNR) to minimize the symbol error rate (SER). Further, we analyze the performance quantitatively and derive the closed-form expressions of SER, which indicates that the proposed scheme has a lower SER. Finally, simulation results verify that the proposed symbol-wise OTP secure transmission scheme can achieve perfect secrecy and high reliability.
Similar content being viewed by others
References
Lv L, Li Z, Ding H Y, et al. Secure coordinated direct and untrusted relay transmissions via interference engineering. Sci China Inf Sci, 2022, 65: 182304
Vernam G S. Secret signaling system. U.S. Patent 1310719, 1919
Shannon C E. Communication theory of secrecy systems. Bell Syst Technical J, 1949, 28: 656–715
Sun L, Du Q. Physical layer security with its applications in 5G networks: a review. China Commun, 2017, 14: 1–14
Jin L, Hu X, Lou Y, et al. Introduction to wireless endogenous security and safety: problems, attributes, structures and functions. China Commun, 2021, 18: 88–99
Gong S X, Tao X F, Li N, et al. Secret key generation over a Nakagami-m fading channel with correlated eavesdropping channel. Sci China Inf Sci, 2022, 65: 192304
Wan Z, Huang K, Lou Y, et al. Channel covariance matrix based secret key generation for low-power terminals in frequency division duplex systems. Electron Lett, 2021, 57: 324–327
Zhang J, Duong T Q, Marshall A, et al. Key generation from wireless channels: a review. IEEE Access, 2016, 4: 614–626
Li G, Zhang Z, Yu Y, et al. A hybrid information reconciliation method for physical layer key generation. Entropy, 2019, 21: 688
Peng L, Li G, Zhang J, et al. Securing M2M transmissions using nonreconciled secret keys generated from wireless channels. In: Proceedings of IEEE Globecom Workshops (GC Wkshps), 2018. 1–6
Wan Z, Huang K. Non-reconciliation secret keys based secure transmission scheme using polar codes. In: Proceedings of IEEE 5th International Conference on Computer and Communications (ICCC), 2019. 1499–1504
Li G, Zhang Z, Zhang J, et al. Encrypting wireless communications on the fly using one-time pad and key generation. IEEE Internet Things J, 2021, 8: 357–369
Hu X, Jin L, Huang K, et al. A secure communication scheme based on equivalent interference channel assisted by physical layer secret keys. Secure Commun Networks, 2020. doi: https://doi.org/10.1155/2020/8840645
Wang M, Huang K, Wan Z, et al. Non-reconciled physical-layer keys-assisted secure communication scheme based on channel correlation. Entropy, 2022, 24: 1167
Bang I, Kim T. Secure modulation based on constellation mapping obfuscation in OFDM based TDD systems. IEEE Access, 2020, 8: 197644–197653
Chen B, Zhu C, Li W, et al. Original symbol phase rotated secure transmission against powerful massive MIMO eavesdropper. IEEE Access, 2016, 4: 3016–3025
Althunibat S, Sucasas V, Rodriguez J. A physical-layer security scheme by phase-based adaptive modulation. IEEE Trans Veh Technol, 2017, 66: 9931–9942
Loganathan L D, Rengaraj R, Konganathan G, et al. Physical layer security using an adaptive modulation scheme for improved confidentiality. IET Commun, 2019, 13: 3383–3390
Bi S, Yuan X, Zhang Y J A. DFT-based physical layer encryption for achieving perfect secrecy. In: Proceedings of IEEE International Conference on Communications (ICC), 2013. 2211–2216
Mao T, Wang Q, Wen M, et al. Secure single-input-multiple-output media-based modulation. IEEE Trans Veh Technol, 2020, 69: 4105–4117
Husain M I, Mahant S, Sridhar R. CD-PHY: physical layer security in wireless networks through constellation diversity. In: Proceedings of IEEE Military Communications Conference, 2012. 1–9
Chorti A. Masked-OFDM: a physical layer encryption for future OFDM applications. In: Proceedings of IEEE Globecom Workshops, 2010. 1254–1258
Xi C, Gao Y, Nan S, et al. Constellation symbol obfuscation design approach for physical layer security. In: Proceedings of the 10th International Conference on Communication Software and Networks (ICCSN), 2018. 264–269
Ma R, Dai L, Wang Z, et al. Secure communication in TDS-OFDM system using constellation rotation and noise insertion. IEEE Trans Consumer Electron, 2010, 56: 1328–1332
Xiong T, Lou W, Zhang J, et al. MIO: enhancing wireless communications security through physical layer multiple intersymbol obfuscation. IEEE Trans Inform Forensic Secur, 2015, 10: 1678–1691
Katz J, Lindell Y. Introduction to Modern Cryptography. 2nd ed. Boca Raton: Chapman and Hall/CRC, 2014
Szabo Z. Information theoretical estimators toolbox. J Mach Learn Res, 2014, 15: 283–287
Acknowledgements
This work was supported by National Natural Science Foundation of China (Grant No. U22A2001, 62301608) and National Key Research and Development Program of China (Grant Nos. 2022YFB2902202, 2022YFB2902205).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hu, X., Wan, Z., Huang, K. et al. Modulated symbol-based one-time pad secure transmission scheme using physical layer keys. Sci. China Inf. Sci. 67, 112303 (2024). https://doi.org/10.1007/s11432-022-3768-8
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-022-3768-8