Abstract
The Internet of Things (IoT) is a concept that has attracted significant attention since the emergence of wireless technology. The knowledge diffusion of IoT takes place when an individual disseminates his knowledge of IoT to the persons to whom he is directly connected, and knowledge creation arises when the persons receive new knowledge of IoT, which is combined with their existing knowledge. In the current literature, several efforts have been devoted to summarising previous studies on IoT. However, the rapid development of IoT research necessitates examining the knowledge diffusion routes in the IoT domain by applying the main path analysis (MPA). It is crucial to update prior IoT studies and revisit the knowledge evolution and future research directions in this domain. Therefore, this paper adopts the keyword co-occurrence network and MPA to identify the research hotspots and study the historical development of the IoT domain based on 27,425 papers collected from the Web of Science from 1970 to 2020. The results show that IoT research is focused on IoT applications for smart cities, wireless networks, blockchain technology, computing technologies, and AI technologies. The findings from the MPA address the need to explore the knowledge evolution in the IoT domain. They also provide a valuable guide to disseminate the knowledge of IoT among researchers and practitioners, assisting them to understand the history, present and future trends of IoT development and implementation.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The concept of the Internet of Things (IoT) has been gaining momentum since the emergence of wireless technology [1,2,3,4,5,6]. The fundamental premise of IoT is to connect multiple devices through tools like Radio Frequency Identification (RFID), sensors, actuators, smartphones, by which these devices can communicate with each other [7]. As a dynamic global network infrastructure, IoT relies on smart devices with several capabilities, including sensing, networking, processing, and actuation, thereby facilitating the ability of people and objects to collaborate in heterogeneous and complex environments [8,9,10]. According to the seminal survey of [11], concepts and technologies surrounding IoT can be categorised into three main parts. The first part concerns the internet-oriented vision, which corresponds to the development of IP protocol for allowing smart things to communicate over the internet [12]. The second part is related to the things-oriented vision, which considers IoT a network of identifiable things [13]. This vision is achieved by integrating sensors and pervasive technologies to track objects. The third part concerns the semantic-oriented vision, which focuses on how vast networks of heterogeneous devices and the data they are generating can be controlled, monitored, and managed from a technical perspective [14]. As such, raw data generated from sensor-based systems will be processed and churned out to obtain a better understanding and representations. These visions can be realised through the interconnection and interoperability of sensing and actuating technologies, providing the ability to exchange information across different platforms through a unified framework and enable innovative applications [15].
Recently, IoT has drawn significant attention due to its potential to provide efficiency, convenience, and competitive advantages to the corporate world [8, 16]. The real-time data sensing and actuating capabilities of the technology can benefit sectors as diverse as supply chain and logistics, manufacturing, healthcare, automotive, agriculture, etc. For example, the deployment of IoT in supply chain management has been proven beneficial as organisations can use the technology to capture data concerning the flow of products and stock-keeping units (e.g., pallets), reduce information asymmetries between supply chain partners, and optimise operational performance [17]. Focal firms and their business partners have started to invest in IoT to improve supply chain processes. For instance, United Parcel Service (UPS), CocaCola, and Disney have leveraged IoT to reduce idle time and maintenance costs, maximise efficiency and safety, and improve customer satisfaction [18]. Incorporating IoT into digital supply chains brings better visibility, additional insights, strong collaboration, and quicker response times. In the healthcare sector, IoT is expected to improve the effectiveness of healthcare and hospital services, ensure constant monitoring of patients, and even early detect deadly diseases [19]. During health crises, such as the COVID-19 pandemic, medical IoT could save human lives by quickly notifying the issues related to health and creating intelligent information systems according to individual COVID-19 patient needs and requirements [20]. Beyond healthcare, IoT is used in the automotive industry to help identify and track manufactured parts and people without human input [21], thereby improving traceability and monitoring within firms’ manufacturing and assembly plants across the supply chain [22]. IoT can be implemented in the agriculture sector to optimise production, establish a micro-precision model of agricultural production, and provide optimal growing conditions for both animals and crops [23]. Therefore, the advancement of IoT applications spans several economic sectors and moves beyond the traditional information and communication technologies by capturing a large volume of data flowing among people, equipment, processes and changing the ways these entities access, exchange data, and interact with the environment.
Given the dramatic growth of IoT research, there is a need to examine this knowledge domain systematically. In the extant literature, several efforts have been devoted to summarising previous studies on IoT. For example, Asghari et al. [24] conduct a systematic review of IoT applications using sources published from 2011 to 2018. Nord et al. [25] review the IoT-related literature and develop a theoretical framework and conceptual model. Ng and Wakenshaw [26] review and define IoT, presenting its implication and influence on future marketing. Although these studies provide valuable insights into IoT research, only one paper has explored the knowledge diffusion routes of the IoT domain by applying the main path analysis (MPA) and using a dataset of 8913 documents [27]. Considering the exponential increase in IoT studies, it is crucial to update prior IoT studies and revisit the knowledge evolution and future research directions in this domain.
This study aims to provide more insights for scholars using the keyword co-occurrence clustering and MPA. These approaches help to comprehensively examine the entire field of IoT, identify the research hotspots, and uncover the contributions that shape the historical development of IoT. The use of MPA enables us to handle thousands of papers efficiently, identify the interrelationships among them, and depict the knowledge diffusion paths within the IoT domain. In the current study, four main paths are used to reveal the structural backbone of the formation of IoT research, including the local (forward, backward), global, and key-route main paths. As a result, the rich information obtained from these main paths can illuminate scholars and deepen their understanding of the history of the IoT domain, grasp its current status, and identify future research trends. The next section presents the data and methodology used. Section 3 presents the analysis of descriptive statistics. Section 4 provides the keyword co-occurrence network analysis, followed by MPA in Sect. 5. Section 6 presents the discussion of the findings, and lastly, a brief conclusion is drawn from the study.
2 Data Collection and Methodology
2.1 Data Collection
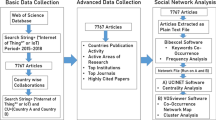
Papers are collected from the Web of Science (WoS), one of the leading and outstanding databases, to ensure the quality of the data and results [28, 29]. In addition, WoS is widely recognised as the most inclusive database for academic work since it indexes thousands of journals [30]. Furthermore, according to several studies [28, 31, 32], WoS is the premier source of materials used in bibliometrics and MPA-based studies. Therefore, WoS is consulted in this study to retrieve relevant data for the analysis. The detailed structure of the paper is depicted in Fig. 1.
The search string used in this paper is as follows: Topic Search (TS) = (“internet of things” OR “IoT”). We collected papers from different databases in WoS, including Science Citation Index Expanded (SCI-EXPANDED) and Social Sciences Citation Index (SSCI). The time span was set from 1970 to 2020, and the data was collected in May 2021. We only included English-language speaking journal articles and reviews. As a result, a total number of 27,425 papers were collected for the final analysis.
2.2 Methodology
The citation-based analysis constitutes a powerful tool to discover the interrelationship between related studies in a topic, identify the paradigms and schools of thought in a research field, and uncover the trajectory and direction of knowledge and current and future trends [33, 34]. In this study, we adopted the keyword co-occurrence network analysis and MPA [35], where the first is valuable in examining the evolution of research topics and research hotspots in a specific research field [6], and the second can detect the knowledge path due to direct references [32].
MPA is an outstanding method introduced by [35] to discover and trace the knowledge diffusion or flow. For example, when an author cites a work, a link is shaped, and certain knowledge is traversed from the cited work to the new publications. Investigating these paths would provide researchers with insights and an in-depth understanding of a research field. MPA studies in the literature are two types: those that develop and extend the method and those that apply the method [36].
MPA has been proven valuable to investigate knowledge paths in technology-related domains. For instance, many researchers have adopted MPA for such research fields. Among others, Yu and Sheng [32] trace the knowledge diffusion of the blockchain technology domain. Also, Tseng et al. [33] use MPA to determine the blockchain major sub-fields. Earlier, Fontana et al. [37] investigate the technological change in Ethernet using MPA. Fu et al. [27] study the development of IoT and identified four related paths.
Traversal weight is a crucial concept to determine the research paths. Instead of valuing all links equally, Hummon and Dereian [35] propose three different methods to assign each link a value “traversal weight”: search path link count (SPLC), search path node pair (SPNP), and node pair projection count (NPPC). Later, Batagelj [38] suggests search path count (SPC), which we applied. We present a simple citation network to explain how SPC is calculated and how different main paths (forward and backward local main paths, global main path, and key-route main path(s)) are extracted. As illustrated in Fig. 2, each node represents a paper in a citation network, for example, A, B, C, among others. Each link represents a citation from the cited to citing work, such as A–B, B–C, and E–B. The sources are the nodes that are only cited by other papers (A and H); the sinks are those that only cite other nodes (D, G, and J). The SPC value of a link can be calculated by counting the times that the link is traversed from all sources to all sinks; for example, the SPC of C-D is 3 because these are 3 paths from sources to sinks that passes C-D, namely: A–B–C–D, A–E–B–C–D, and H–E–B–C–D.
In this weighted network, now we can determine the main paths by different search algorithms. Each contributes in different ways and complements each other [32]. Local paths are suitable for finding important links; the backward local main path could reveal the papers that attract the most followers. The forward local main path focuses on papers that have taken ideas from previous ones. Neither forward nor backward local paths are the path(s) with total maximum SPC. Hence, the global main path complements them. Although all these paths could bring significant insights, they may fail to consider all links with the largest traversal weight. Therefore, the key-route main path analysis can be applied to overcome the shortcomings of local and global main paths [39].
The forward local main path starts from the sources and goes forward to sinks. In the first step, the link(s) with the highest SPC value emanating from the sources is selected, then the starting point would be the end of the link. In the next step, the links from the current starting point are compared, and the highest SPC is chosen. This process will continue till reaching a sink. In Fig. 3, the forward local main paths are drawn by solid arrows.
The backward local main paths are extracted, moving backward from sinks to sources. Solid arrows in Fig. 4 show these paths.
The global main path is designed to extract the path with the highest SPC. In our sample, the highest SPC for a path is 24. The paths are drawn by solid arrows in Fig. 5.
None of these paths alone includes all the links with the largest SPCs. In this illustrative example, we selected the two largest SPCs, 9 and 6. Liu and Lu [39] introduced a key-route search algorithm. The key route represents the link with the largest traversal weight. The more the key-routes are selected, the more details are revealed. Once the key-routes are selected, we start from the end of the key-route and move forward till reaching a sink and move backward from the start point of the key-route till reaching a source. The resulted path would be the key-route main path. Solid arrows in Fig. 6 illustrate the key-route main paths.
3 Descriptive Statistics
We referred to the h-index, the g-index, and the growth curve to analyse the publications and enrich our investigation. The h-index and the g-index suggested by Hirsch [40] and Egghe [41] indicate the relative importance of journals and authors in a specific field. These indexes are fairly simple and effectively capture researchers’ impact in different scientific fields [42,43,44]. Moreover, the analysis of the curve growth seeks to depict the growing pattern of IoT papers. We argue that the h-index and g-index are complementary to one another, and hence we used both to evaluate the impact of scholars and journals in the IoT field.
Table 1 presents the top 10 authors who made significant contributions to the IoT field. It also covers scholars from 1970 to 2020 according to the h-index and g-index. Rodrigues Joel J. P. C. leads the list in terms of publications; meanwhile, Kumar Neeraj has the highest h-index, and Guizani Mohsen has the highest g-index. These authors did substantial research on IoT.
We also used the h-index and the g-index of the top 10 journals, as shown in Table 2. According to the table, IEEE Internet of Things Journal has the highest h-index and g-index, publishing 1912 articles. We also found that IEEE Access is the most productive journal publishing 2365 papers. The h-index and g-index of the journal are 62 and 111, which means that 62 papers are cited over 62 times, and the most citation among these 2365 papers is 111. The journal impact factor is measured from the data compiled in WoS, indicating the scientific quality of academic journals. In terms of impact factor, IEEE Transactions on Industrial Informatics and IEEE Internet of Things Journal are highly influential in IoT research.
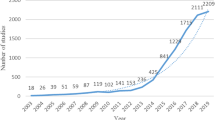
Figure 7 depicts the evolution of IoT research. From 1979 to 1990, the number of documents published did not exceed 2. From 1991 to 2010, the number of publications increased slowly, reaching 43. However, in the last decade, IoT research entered the substantial growth stage, reflecting the increasing interest in the technology and the gradual maturity of IoT knowledge structure.
4 Keyword Co-occurrence Network Analysis
Keyword co-occurrences represent a relational bibliometric measure that corresponds to scholarly knowledge. The analysis of keyword co-occurrence networks helps identify clusters that provide a broader view of different research foci in a specific field. We began by extracting all keywords from the selected articles to generate the network. Then we pretreated and refined the keywords to maintain consistency and accuracy. For example, full-length keywords (e.g., internet of things, artificial intelligence, radio frequency identification, wireless sensor networks, etc.) were abbreviated. Two keywords tend to be close if they co-occur in the same literature, thus expressing a similar research topic or direction.
To create the network, the data were imported into the visual tool VOSviewer, and the density-based spatial clustering using the full counting method was used [45]. In addition, the threshold of keyword occurrences was set at 20. As a result, five clusters with different colours were generated, as shown in Fig. 8. A node corresponds to a keyword, and the node size is proportional to the co-occurrence frequency of the keyword. The distance between two nodes in the visualisation is determined by density, and the higher this density, the closer the distance between two nodes. The detailed information regarding each cluster is presented in Table 3.
From Fig. 8, it is clear that the largest cluster is the red one. It revolves around IoT applications for smart cities, and thus it is labelled as IoT for smart cities. The role of IoT in the development of smart cities is very critical as the technology can be implemented to develop intelligent systems such as smart homes, smart grids, smart factories, smart energy, smart healthcare, and smart transportation. IoT generates massive data, which raises the need to process, manage, analyse, and understand these data through big data analytics. Additionally, IoT can be a part of cyber-physical systems (CPS), which improve information sharing, ensure flexible and seamless operations, and accelerate the transition toward Industry 4.0. The second cluster is about the potential of wireless networks to support IoT-based systems such as unmanned aerial vehicles (UAVs). In this cluster, studies focus on the benefits of recent generations of telecommunication networks (e.g., 5G) and the advent of wireless sensor networks (WSN) to ensure seamless integration and management of heterogeneous IoT devices and overcome several issues related to energy efficiency and communications reliability. The third cluster indicates that the fusion of IoT and blockchain can ensure data security and privacy and increase access control through authentication and encryption mechanisms. While IoT is adopted to achieve real-time data capture and collection and automate processes, blockchain provides open and decentralised data storage and exchange, thereby overcoming cybersecurity attacks. The fourth cluster is labelled as computing technologies, which denotes that scholars attribute importance to several computing paradigms due to the advent of modern high-speed networks and their ability to offer fast access to remote data, improve latency and location awareness, and ensure interoperability among a large number of IoT nodes. Finally, the last cluster indicates that AI techniques such as machine learning (ML), deep learning (DL), artificial neural networks (ANN) are the main target research.
5 Main Path Analysis (MPA)
This section presents the analysis of the citation network of the selected sample, followed by the discussion of the outcomes of the four main paths, namely, the local (forward and backward) local main path, the global main path, and the key-route main path (see Figs. 9, 10, 11, 12). In these figures, each node reflects a paper and is accompanied by the information of the lead author and the publication year. The arc reflects the direction of knowledge flow, and the thicker the arc, the more critical it is.
5.1 The Citation Network
The entire citation network of the selected sample is shown in Fig. 13, consisting of 27,425 nodes and 117,795 edges. In this figure, three types of nodes exist. The first type concerns the nodes in the largest subnetwork. In this subnetwork, 22,717 nodes are closely linked, which constitute the core of the whole network. The four main paths discussed in the upcoming sections are derived from the subnetwork since it maintains the most citation relationships between the articles to the greatest extent. The second type corresponds to the nodes with few citations. These nodes are linked with several papers in the citation network and are dispersed at the network’s periphery. The isolated nodes represent the third type. These nodes are disconnected from all the other nodes in the citation network.
5.2 The Analysis of the Local Main Paths
Figures 9 and 10 show the local main paths, containing 38 and 33 papers, respectively. Overall, both paths share 15 common papers, which are represented by nodes coloured in yellow.
From the close inspection of the forward local main path, it is obvious that [46] is the first paper, which is of vital importance to the initial development of IoT research. In this study, the authors proposed various prototypes to explore new ways for human–computer interaction that IoT and related technologies enable. The potential of IoT is further examined by [47], who tries to analyse the current state of the art in information management for supply chain management, highlighting the role of IoT to enhance the performance of supply chain quality management and increase automation. In [48], the authors employ transaction cost economics and contract economics to analyse the contracts derived from the existing internet architecture and conclude that IoT can give a competitive advantage to firms by supporting market data collection, analysis, and decision making processes. Later, Li et al. [49] investigate the ability of compressing sensing to offer new insights into data sampling and collection in wireless sensor networks and IoT. The sensing layer in IoT can take advantage of compressing sensing to decrease the energy consumption of IoT networks and extend the lifetime of sensors. The next paper on the path is of [50], where a novel multilayered vehicular data cloud platform is developed using the combination of cloud computing and IoT.
Unlike the forward local main path, the backward local main path uncovers several papers at the beginning of the path. For instance, earlier efforts have been made by [51], who anticipated that the development of IoT would go beyond the laboratory borders and usher in a new information technology age in both academia and industry. Later, Welbourne et al. [52] developed a suite of web-based, user-level tools and applications to increase users’ understanding and ability to manage and control personal RFID data and privacy settings. RFID represents one of the vital technologies for developing IoT applications due to its identification capabilities and potential to streamline data acquisition and integrate with different sensing technologies. These two papers merge at the paper of [11], which presents a seminal overview of IoT as a promising paradigm that complements several technologies and communication solutions and reshapes several knowledge fields as diverse as informatics, communications, electronics, and social science. Another comprehensive review of IoT is also found in the next paper on the path [53].
The capability of IoT to provide real-time information has a promise for supporting sustainability, particularly its environmental dimension. The environmental benefits gained from IoT applications have been evaluated in the next three papers on the path. For example, Su et al. [54] contend that the advent of IoT offers new opportunities to enhance urban environment monitoring and management and achieve more sustainable cities. Wang et al. [55] propose a framework for an environmental IoT (EIoT) and discuss key technologies such as wireless sensor networks (WSN), network techniques, and Geographic Information System (GIS), etc., and their role in enabling real-time monitoring of the urban environment and controlling several environmental variables like water, soil, and wind. In [56], an online water quality management system based on EIoT is proposed to manage an urban scenic river in China and ensure effective water quality management. The next paper, Xu et al. [57], builds on the previous papers and presents a survey of the industrial applications of IoT, identifying different research trends and challenges.
After the previous research, the two local main paths begin to be similar, sharing three papers. First, in [58], IoT applications in the context of cloud manufacturing are investigated, highlighting the need for the technology to realise intelligent perception and access to different manufacturing resources, including computational and intellectual resources. Moving further in this direction, Tao et al. [59] examine how IoT applications and cloud manufacturing can ensure full sharing, efficient circulation, on-demand use, and appropriate allocation of manufacturing resources and capabilities by establishing a system based on these technologies. Furthermore, Li et al. [60] summarise these previous papers on the path, studying the definitions, architecture, key technologies, and applications of IoT. Next, Butun et al. [61] propose a service approach based on cloud-centric and multi-level authentication to overcome scalability and time constraints in IoT networks and warrant their secure public safety. However, the backward local main path reveals another paper, Voegler et al. [62], which presents an infrastructure toolset that offers increased scalability and efficient network traffic between cloud and edge devices in large-scale IoT systems.
The two local main paths begin to uncover the same literature. Two papers, Fraga-Lamas et al. [63, 64], review IoT applications for defence and public safety and use this background to design a smart pipe system in the shipyard environment. In [65], a hardware and software platform named VineSens, is developed using IoT sensors to aid vine growers in collecting weather data from various vineyard spots, thereby supporting decision-making processes and preventing the degradation of product quality. To tackle the challenges of energy crises and carbon emissions, IoT constitutes a novel power generation paradigm that provides a robust and scalable infrastructure to operate, manage, and maintain smart energy systems. In this regard, Blanco-Novoa et al. [66] analyse IoT’s role in the energy sector by proposing a smart socket system that captures the information related to energy price and employs sensors and actuators to achieve optimal home energy consumption as per user preferences. Besides the energy sector, Fraga-Lamas et al. [67] review industrial IoT-connected railways and find that the latest trend relates to predictive maintenance, advanced monitoring of assets, video surveillance, safety assurance, and energy efficiency. The next paper in the forward local main is [68], whereas a different paper appears in the backward local main path [69]. In the former, the authors review industrial augmented reality (AR) systems for shipyards and conclude the critical importance of IoT in developing smart connected products that support AR applications. In the latter paper, Hernandez-Rojas et al. [69], the authors introduce a set of protocols called Lightweight Protocol for Sensors that ensure quick responses and allow plug-and-play mechanisms for IoT telemetry systems.
The next two papers, Fernandez-Carames and Fraga-Lamas[70] and Fernandez-Carames et al. [71], analyse the combination of IoT with other technologies such as blockchain and fog computing. These technologies help encrypt real-time sensor-generated data, address security and transparency issues related to IoT devices, and provide a highly virtualised platform for mobility, low latency, geo-distribution, and local awareness. While the paper of [72] appears on the forward local main path, the paper of [73] appears on the backward local main path. In the first, the authors propose a cost-effective IoT radon gas remote monitoring system, which can maintain accurate concentration measurements and prevent dangerous situations such as explosions. In the second, the authors propose an IoT-based system to make use of novel lightweight protocols that enable low latency, efficient power consumption, and required quality of service.
After these studies, similar papers are identified on both local main paths. For instance, the next two papers, Froiz-Míguez et al. [74] and Suárez-Albela et al. [75], focus on integrating IoT and fog computing in smart homes and energy management. The next paper [76], is a review of IoT applications in smart clothing, while the next two papers [77, 78], are reviews of blockchain’s potential for advanced cybersecurity in smart factories and the automotive industry.
After these papers and at the end of the local main paths, research outputs differ. It is evident that several new papers appear at the end of the forward local main path. For instance, Alladi et al. [79] conduct a review of blockchain applications for Industry 4.0 and industrial IoT. It is found that the incorporation of blockchain can benefit IoT-based industries thanks to its tamper-proof and resilient mechanisms for record-keeping. In [80], a framework for secure and reliable energy trading among unmanned aerial vehicles (UAVs) and charging stations is suggested. The proposed model leverages the capabilities of blockchain to respond to the need of UAVs and IoT devices for optimal energy consumption. Afterwards, Chamola et al. [81] investigate the possibilities of IoT alongside other technologies such as UAVs, blockchain, 5G, and AI to fight against the COVID-19 pandemic. This paper contributes to enlightening and inspiring IoT research, which becomes more diversified.
Most of the paper at the periphery focus on the prospects of new technologies for mitigating the impact of the COVID-19 pandemic. In a general sense, Javaid et al. [82] discuss how smart digital information and manufacturing technologies can provide personalised care and treatment processes to the COVID-19 patients, create a smart healthcare setting, and ensure real-time sharing of healthcare information. During disaster situations, the medical sector represents a compelling context for deploying advanced technologies since several vulnerabilities among healthcare departments and entities may arise. For this reason, Hedayatipour and Mcfarlane [83] scrutinise the potentials and challenges of wearable sensors and conclude that these devices can help detect most of the symptoms associated with coronavirus, monitor patients’ health, and facilitate access to medical data. However, the barriers to integrating smart wearables into healthcare during the COVID-19 pandemic relate to security concerns and technical limitations such as sensors’ power, size, and accuracy.
In addition, Ndiaye et al. [84] and Kumar et al. [85] examine the value of IoT for fighting against COVID-19 through virus tracing, tracking, and spread prevention. In [86], the authors propose a more accurate prediction model for intelligent healthcare services using a machine learning approach. When combined with machine learning, IoT can assist in collecting real-time data, which is necessary for analysing the current COVID-19 situation more accurately and predicting future hazards.
As healthcare is becoming more digitized and relying on real-time interaction and coordination among multiple IoT devices and sensors, there is mounting concern about cybersecurity. Because the current COVID-19 pandemic requires various healthcare operating systems, medical data may be vulnerable to cyberattacks. These issues are highlighted in the studies of [87, 88], who argue that IoT applications are still fraught with unauthorised access and privacy issues, particularly when healthcare data are shared via apps. As a result, to reduce the likelihood of cyberattacks and security risks in healthcare, Zhang and Wu [89] present a blockchain-enabled system to guarantee the secure management of home quarantine and strengthen IoT systems’ security, privacy, and efficiency. Likewise, Hasan et al. [90] propose a solution based on blockchain to lower the response time of the healthcare facilities, overcome the spread of false information by taking advantage of blockchain’s immutability, and stop the transmission of the virus through digital medical passports. Two papers, Gupta et al. [91] and Nie et al. [92], study the fusion of blockchain and artificial intelligence for drones, aiming to ensure secure and private communication, enhanced network performance, and lower transaction storage costs. Closing the path, Shubina et al. [93] survey the literature related to existing privacy-preserving solutions for wearables and mobile IoT devices, highlighting the benefits and drawbacks of these technologies in user location-tracking, proximity detection, and online contact tracing.
At the end of the backward main path, seven different papers appear. Fernandez-Carames et al. [94] design and implement a system that improves commercial Continuous Glucose Monitor (CGM) by leveraging IoT capabilities, thereby monitoring patients remotely and mitigating detrimental situations. In [95], a review of the recent developments on deep learning-based UAVs is conducted, and several deep learning techniques, solutions, and challenges are identified. Further, Haseeb et al. [96] present a robust, trusted scheme for IoT-based mobile mesh networks to maintain reliable routing, data privacy, and integrity. The proposed system involves mobile mesh clients for enhanced network exposure and improves data delivery. In the next paper, Ali et al. [97] develop an IoT-based disaster management system to overcome delays and energy consumption-related issues in disastrous situations. IoT can be used during disasters to enhance responsiveness and efficiency both in the short term and long term due to the technology’s ability to track basic resources in humanitarian supply chains such as medicines, food, humans, and equipment, thereby reducing response time and optimising relief operations. The previous research finally converges to the paper of [98], who propose a holistic and automated approach architecture for proactive forensics in IoT using a new security and privacy-aware logging scheme in fog-based clouds for digital forensics. From this paper, two papers, Hsu et al. [99] and Bano et al. [100], emerge and have different focuses. The first paper suggests an autonomous log storage management protocol based on the blockchain system and access control for IoT. The incorporation of blockchain helps increase the security of IoT logs and establish strong identity verification, immutability, data integrity, and legality. The second paper introduces a smart bin mechanism based on IoT to manage solid waste and ensure real-time monitoring of trash bins. The benefits of such a system include lower labour costs, proper hygiene in cities, and increased environmental sustainability.
5.3 The Analysis of the Global Main Path
While the two previous paths aim to find local influential connections in the citation network, the global main path helps determine the most influential path. Figure 11 depicts the global main path, which consists of 33 significant articles. The SPC values of all links are presented in Table 4. It is obvious that the arc from [63] to [64] has the highest SPC value, followed by the arc from [60] to [61] and the arc from [101] to [63]. Additionally, the arc emanating from [77] to [78] has larger SCP values among the arcs at the top of the path. Considering the potentials of blockchain, both review the role of the technology in fostering cybersecurity in several industries, including the automotive and manufacturing sectors.
The arcs at the middle of the path, particularly from 2014, are much thicker than the arcs at the beginning and the end of the path. This implies that these papers receive significant attention from other scholars. Moreover, the appearance of papers at the end of the global main path reflects the importance of these successors in the citation network. The position of the papers at the extremity of the path still needs to be evaluated with the passage of time and the publication of new articles on IoT.
5.4 The Analysis of the Key-Route Main Path
The analysis of the key-route main path enables to reveal more details about the formation of the IoT domain. This study chooses the number of key-routes with a step size 5 (i.e., 5, 10, 15, 20) and eventually selects 20 for the best outcome. The global method is used simultaneously. Figure 12 shows the key-route main path, depicting the repeating cycles of converging and diverging in the structure of the IoT knowledge diffusion. Articles on this path are similar to articles appearing on the local main paths, apart from two papers, Fernandez-Carames et al. [102] and Suarez-Albela et al. [103]. In the first paper, the authors review the most recent and common vulnerabilities as well as hardware and software security tools of RFID-based IoT applications. In the second paper, Suarez-Albela et al. [103] compare two of the most common transport layer security (TLS) authentication algorithms when executed on a resource-constrained IoT node and stress the importance of testing and empirically evaluating the performance of certain algorithms backed by hardware platforms in order to develop proper IoT configurations in terms of security, energy consumption, and throughput.
A close visual inspection of Fig. 12 reveals that at the beginning, papers converge to [57], in which the authors review the previous studies on IoT. In general, the first part of the path reveals several findings. First, at the early phase of the formation of IoT research, papers tend to focus mainly on the conceptualisations, definitions, terminologies, and architectures of IoT. Second, RFID has been investigated, with most studies featuring it as an operational and strategic tool that creates a microcosm for IoT. The proliferation of RFID makes IoT a reality as the technology can be used in several economic sectors but also poses numerous challenges, including security, privacy, and lack of standards. Third, papers revolve around examining IoT from some perspectives like supply chain management, computer science, and environmental science.
After the year 2014, three divergence-convergence patterns appear on the path. The first divergence-convergence pattern diverges at [60] and merges at [63]. At this part, the focus of research has been moved toward developing more secure and scalable IoT networks in new fields such as defence and public safety. The purpose of applying IoT in these sectors is to facilitate access to positioning, the ambient status of the environment, and healthcare data. The second divergence-convergence pattern diverges at [63] and finally gathers at [65]. At this part, the focus has moved to the role of IoT in different systems, including smart pipes and viticulture, where much work may still be required. For instance, there is a need to propose cost-effective pipeline monitoring systems that can carry out instant damage detection, location, and provide the visualisation of the pressure pulses on computers or smartphones. In this regard, IoT experimentations are important to evaluate the performance of wireless communication devices compared to data loggers and their ability to ensure real-time monitoring and detection of potential damages on pipes. In complex and dynamic systems as of viticulture, IoT can be used for real-time data collection and monitoring to eliminate waste, increase output, and achieve high precision in agriculture.
The last divergence-convergence pattern diverges at [104] and eventually merges at [77]. Taking a closer look at this part, some important findings can be obtained. First, research has been focalised on evaluating different algorithms, schemes, and technologies for the development of secure and energy-efficient IoT systems. Second, the promises of IoT and blockchain technology have been examined in the textile and automotive industries; nonetheless, the shortcoming in this part is that several equally important economic sectors have been ignored. Research after [77] start to address this knowledge gap. For instance, the examination of blockchain applications for the cybersecurity of Industry 4.0 smart factories has been undertaken. Later, the fusion of this technology and IoT has been widely investigated in the context of the current COVID-19 pandemic, especially in healthcare.
6 Discussion
This paper analyses the main topics in the IoT domain based on the keyword co-occurrence network analysis and first displays the citation network of 27,425 papers in the IoT domain. Based on the review of previous studies on IoT, the analysis of the local main path reveals several findings, especially on the historical development of IoT. Accordingly, the global main path is applied to find the overall most influential path, and the divergence-convergence structure can be shown by the key-route main path, thus systematically enlightening the development structure of this domain.
6.1 Major Findings
In sum, the main findings of this study based on the analysis of keyword co-occurrence network cluster analysis and MPA can be summarised as follows:
-
1.
The results of the keyword co-occurrence network indicate that the research mainly revolves around several aspects; the most frequent that occupies a high percentage is IoT for smart cities, followed by wireless networks, blockchain technology, computing technologies, and AI technologies. Studies on these technologies are overwhelming as they are the building blocks of the fourth industrial revolution.
-
2.
Notably, the results reveal that most of the papers tend to focus mainly on the conceptualisations, definitions, terminologies, and architectures of IoT at the early phase of the formation of IoT research. This is followed by RFID, which represents the key enabler for IoT and valuable support in the effective integration of business processes. In addition, the prevalent use of RFID makes IoT a reality as the technology can be leveraged in several economic sectors but raises numerous issues, including security, privacy, collision, investment cost, and lack of standards. Lastly, papers focus on examining IoT from some perspectives like supply chain management, computer science, and environmental science.
-
3.
Recently, a few studies have focused on the role of IoT in different systems, including smart pipes and viticulture. Thus, it is recommended that future studies propose cost-effective IoT monitoring systems that can carry out instant damage detection, location, and visualisation in pipelines, tanks and flowlines. Additionally, IoT is found to ensure real-time data collection and monitoring, reduce waste, maximise output, and achieve high precision in agriculture.
-
4.
Most of the research has focused on evaluating different algorithms, schemes, and technologies to develop secure and energy-efficient IoT systems. Moreover, the potentials of IoT have been expanded in the textile and automotive industries and healthcare, especially in the context of the current COVID-19 pandemic.
6.2 Future Research Directions
This study investigates the knowledge diffusion of IoT research as it has attracted extensive interest from many researchers since the emergence of wireless technologies. The vast interest in IoT research makes it necessary to investigate this domain systematically. Lots of recent studies have been conducted to summarise previous studies on IoT. For example, Yuly and Pradana [105] conduct a systematic literature review to identify industries that have been developed related to IoT in the Southeast Asian region and find four dominance areas that focus on IoT, including environment, agribusiness, health, and industry, [106], on the other hand, analyse this domain comprehensively using seventy-three (73) papers and examine the integration of IoT in halal food supply chains. In addition, Rejeb et al. [6] analyse 807 journal articles, and according to the keyword co-occurrence clustering, they reveal that the IoT literature in supply chain management and logistics is focalised on RFID technology, Industry 4.0 technologies, reverse logistics, and additionally covers various industries, such as the food, retailing, construction, and the pharmaceutical sectors. Although these studies provide us with valuable information concerning IoT, few papers have yet investigated the knowledge diffusion of IoT by adopting the method of MPA, which has been widely used in various fields [27, 28, 32, 107]. To fill this gap, the knowledge evolution of the IoT domain is detected in this study through MPA. Reflecting on the significant findings of this study, several future research directions for IoT can be proposed as follows:
-
1.
A framework on IoT implementation by looking at the antecedents and outcomes of IoT can be developed. Although there is global acceptance of the importance of IoT, less than one-third of organisations are currently using IoT, indicating that IoT is still in the early phase of adoption. The opportunity for the industry to leverage IoT becomes more evident with the great outcomes in providing opportunities for value creation to improve businesses and overall competitiveness. In the future, scholars can focus on more complicated frameworks to enrich IoT.
-
2.
Future research can empirically focus on the industry case study. Existing studies prefer to use numerical examples to illustrate the solution procedure. Considering the operations of companies, the corresponding solution procedures can be proposed based on their real data. Therefore, it is necessary to combine the theoretical models with the business data in the future.
-
3.
IoT ecosystem can be further studied because IoT potentially touches everything within an enterprise. Therefore, the connectedness and control across the ecosystem to adopt IoT need to be prepared in the case of disruptions to benefit from IoT capabilities. Despite the growing interest in IoT, minimal research has been carried out for its applications in supply chain resilience.
-
4.
Recently, scholars have begun to investigate the relationship between IoT and sustainability. Industry and institutions consider IoT an opportunity for the present and future to digitise many operations and bring tremendous benefits. Moreover, it also can help combat climate change and protect the environment. Additional research is required to understand how IoT can impact the sustainability of the planet in different areas, such as water use and energy efficiency.
-
5.
IoT applications are prevalent in the healthcare sector and result in a significant impact on the world. IoT allows integrating physical devices capable of connecting to the internet and providing real-time health status to doctors. Chronic diseases such as diabetes, heart, blood pressure are remarkable and can be well-suited for the integration of IoT. Thus, future research can develop IoT platforms that allow public health agencies to access the data for monitoring the COVID-19 pandemic. In this regard, Kumar et al. [108] review the literature available on Covid-19, monitoring techniques, and suggest an IoT-based architecture, which can minimise the spread of Covid-19. Similar studies in this direction are welcome.
6.3 Future Potential Areas
IoT has become an interesting topic for most scholars from various fields. To find which areas are receiving significant attention in the IoT domain, this study selected a total of 27,425 articles to be analysed. Table 5 lists the top 20 subjects according to the number of papers. It can be seen that papers in Engineering, Electrical & Electronic occupy a high percentage of 19.94 percent. This is followed by Computer Science, Information Systems (17.05 percent) and Telecommunications (16.99 percent), respectively. The rest of the subjects areas are less than 5 percent, although they are IT-related subjects, they are most likely not involved in the technicality of IoT. Unexpectedly, the field of economic, business, and management is not listed among the top 20 subjects areas of IoT, which calls for more increased research on IoT from the business and management perspective.
7 Conclusions
This paper conducts a retrospective analysis of five decades of research on IoT, where the main objective was to shed light on IoT and determine the pattern of knowledge diffusion, the key roots over the previous decade, and highlight the current research areas and potential opportunities for further academic investigations. In light of this, we used a multi-step approach to the bibliometric examination of IoT research, employing two complementary analytical methods, the keyword co-occurrence network and MPA, and utilizing the software tools VOSviewer and Pajek in the analysis of publications extracted from the Web of Science (WoS). These two methods aim to systematically investigate the entire domain of IoT based on 27,425 papers retrieved from WoS from 1970 to 2020. The idea of blending both methods provides in-depth insights for researchers to enhance their understanding of IoT development over the past fifty years. To our knowledge, this is the first study that uses four different main paths to investigate the knowledge diffusion trajectories in the IoT domain. The results show that there are five main clusters and the most significant clusters are around IoT applications for smart cities, and thus it is labelled as IoT for smart cities, followed by wireless networks, blockchain technology, computing technologies, and AI technologies. This numerical method helps researchers identify important activities in the IoT domain and unearth the routes of knowledge diffusion on IoT systematically. Accordingly, several insights and recommendations are suggested for the scholars and practitioners to understand the history, present and future trends of IoT development in a new review approach, which is more comprehensive than traditional review methods and bibliometric analysis.
With respect to knowledge diffusion, MPA shows that research on IoT progressed out of necessity, with four various perspectives of the basic foundation of IoT research. The forward local main path comprised 38 articles in which early efforts focused on the role of IoT in supply chain management and its combination with wireless sensor networks and cloud computing. Later, the path revealed the need for IoT to support cloud manufacturing, defence applications, energy management, and blockchain systems. The backward local main path is composed of 33 articles that initially focused on RFID applications and recently on IoT applications in healthcare, disaster management, and environmental sustainability. The global main path contained 33 articles that all appeared in the local main paths and emphasized the utility of blockchain to ensure cybersecurity in the automotive and manufacturing sectors. Finally, the key-route main path revealed the IoT knowledge diffusion cycles of convergence and divergence.
The contributions of this paper, therefore, can be summarised as follows. First, the combination of the cluster analysis of keywords and MPA is applied to systematically investigate the IoT domain, which has been ignored in previous studies. Second, valuable guidelines to disseminate the knowledge diffusion on IoT among researchers and practitioners are provided in this paper from different perspectives, including the local, global and key-route main paths. Third, based on this, the evolutionary process and the convergence-divergence structure of IoT development are clearly shown.
This paper nevertheless has several limitations. For instance, when collecting articles to be analysed, a keyword search was performed on the article titles. Therefore, articles implicitly related to IoT may be omitted from this study. Furthermore, this paper’s database to collect research papers is the WoS, which does not include all IoT-related papers. However, according to our knowledge of the subject, we are confident that the studies extracted from the WoS database offered us a comprehensive set of the most relevant research that scholars have contributed to advance IoT applications.
Data Availability
Data available on request from the authors.
Code availability
No code available.
References
Gao, H. (2021). Big data development of tourism resources based on 5G network and Internet of Things system. Microprocessors and Microsystems, 80, 103567. https://doi.org/10.1016/j.micpro.2020.103567
Khan, F. A., Noor, R. M., Mat Kiah, M. L., Noor, N. M., Altowaijri, S. M., & Rahman, A. U. (2019). QoS enabled layered based clustering for reactive flooding in the Internet of Things. Symmetry, 11(5), 634. https://doi.org/10.3390/sym11050634
Knieps, G. (2017). Internet of Things, future networks, and the economics of virtual networks. Competition and Regulation in Network Industries, 18(3–4), 240–255. https://doi.org/10.1177/1783591718784398
Liu, X., Zhang, T., Hu, N., Zhang, P., & Zhang, Y. (2020). The method of Internet of Things access and network communication based on MQTT. Computer Communications, 153, 169–176. https://doi.org/10.1016/j.comcom.2020.01.044
Mieronkoski, R., Azimi, I., Rahmani, A. M., Aantaa, R., Terävä, V., Liljeberg, P., & Salanterä, S. (2017). The Internet of Things for basic nursing care—A scoping review. International Journal of Nursing Studies, 69, 78–90. https://doi.org/10.1016/j.ijnurstu.2017.01.009
Rejeb, A., Simske, S., Rejeb, K., Treiblmaier, H., & Zailani, S. (2020). Internet of Things Research in supply chain management and logistics: A bibliometric analysis. Internet of Things, 12(2020), 100318. https://doi.org/10.1016/j.iot.2020.100318
Giusto, D., Iera, A., Morabito, G., & Atzori, L. (2010). The Internet of Things: 20th Tyrrhenian workshop on digital communications. Springer.
Borgia, E. (2014). The Internet of Things vision: Key features, applications and open issues. Computer Communications, 54, 1–31. https://doi.org/10.1016/j.comcom.2014.09.008
de Vass, T., Shee, H., & Miah, S. J. (2018). The effect of “Internet of Things” on supply chain integration and performance: An organisational capability perspective. Australasian Journal of Information Systems. https://doi.org/10.3127/ajis.v22i0.1734
Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics and trends. Information systems frontiers, 17(2), 261–274.
Atzori, L., Iera, A., & Morabito, G. (2010). The Internet of Things: A survey. Computer Networks. https://doi.org/10.1016/j.comnet.2010.05.010
Aggarwal, C. C., Ashish, N., & Sheth, A. (2013). The Internet of Things: A survey from the data-centric perspective. In C. C. Aggarwal (Ed.), Managing and mining sensor data (pp. 383–428). https://doi.org/10.1007/978-1-4614-6309-2_12
Riggins, F. J., & Wamba, S. F. (2015). Research directions on the adoption, usage, and impact of the Internet of Things through the use of big data analytics. In 2015 48th Hawaii international conference on system sciences (pp. 1531–1540). https://doi.org/10.1109/HICSS.2015.186
Williams, S., Hardy, C., & Nitschke, P. (2019). Configuring the Internet of Things (IoT): A review and implications for big data analytics. https://doi.org/10.24251/HICSS.2019.706
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A vision, architectural elements, and future directions. Future Generation Computer Systems, 29(7), 1645–1660. https://doi.org/10.1016/j.future.2013.01.010
Parry, G. C., Brax, S. A., Maull, R. S., & Ng, I. C. L. (2016). Operationalising IoT for reverse supply: The development of use-visibility measures. Supply Chain Management: An International Journal, 21(2), 228–244. https://doi.org/10.1108/SCM-10-2015-0386
Rejeb, A., Keogh, J. G., & Treiblmaier, H. (2019). Leveraging the Internet of Things and blockchain technology in supply chain management. Future Internet, 11(7), 161. https://doi.org/10.3390/fi11070161
Aryal, A., Liao, Y., Nattuthurai, P., & Li, B. (2018). The emerging big data analytics and IoT in supply chain management: A systematic review. Supply Chain Management: An International Journal, 25(2), 141–156. https://doi.org/10.1108/SCM-03-2018-0149
Saheb, T., & Izadi, L. (2019). Paradigm of IoT big data analytics in the healthcare industry: A review of scientific literature and mapping of research trends. Telematics and Informatics, 41, 70–85. https://doi.org/10.1016/j.tele.2019.03.005
Javaid, M., Haleem, A., Singh, R. P., Haq, M. I. U., Raina, A., & Suman, R. (2020). Industry 5.0: Potential applications in covid-19. Journal of Industrial Integration and Management. https://doi.org/10.1142/S2424862220500220
Haddud, A., DeSouza, A., Khare, A., & Lee, H. (2017). Examining potential benefits and challenges associated with the Internet of Things integration in supply chains. Journal of Manufacturing Technology Management, 28(8), 1055–1085. https://doi.org/10.1108/JMTM-05-2017-0094
Segura Velandia, D. M., Kaur, N., Whittow, W. G., Conway, P. P., & West, A. A. (2016). Towards industrial internet of things: Crankshaft monitoring, traceability and tracking using RFID. Robotics and Computer-Integrated Manufacturing, 41, 66–77. https://doi.org/10.1016/j.rcim.2016.02.004
Tzounis, A., Katsoulas, N., Bartzanas, T., & Kittas, C. (2017). Internet of Things in agriculture, recent advances and future challenges. Biosystems Engineering, 164, 31–48.
Asghari, P., Rahmani, A. M., & Javadi, H. H. S. (2019). Internet of Things applications: A systematic review. Computer Networks, 148, 241–261. https://doi.org/10.1016/j.comnet.2018.12.008
Nord, J. H., Koohang, A., & Paliszkiewicz, J. (2019). The Internet of Things: Review and theoretical framework. Expert Systems with Applications, 133, 97–108. https://doi.org/10.1016/j.eswa.2019.05.014
Ng, I. C. L., & Wakenshaw, S. Y. L. (2017). The Internet-of-Things: Review and research directions. International Journal of Research in Marketing, 34(1), 3–21. https://doi.org/10.1016/j.ijresmar.2016.11.003
Fu, H., Wang, M., Li, P., Jiang, S., Hu, W., Guo, X., & Cao, M. (2019). Tracing knowledge development trajectories of the Internet of Things domain: A main path aAnalysis. IEEE Transactions on Industrial Informatics, 15(12), 6531–6540. https://doi.org/10.1109/TII.2019.2929414
Xiao, Y., Lu, L. Y. Y., Liu, J. S., & Zhou, Z. (2014). Knowledge diffusion path analysis of data quality literature: A main path analysis. Journal of Informetrics, 8(3), 594–605. https://doi.org/10.1016/j.joi.2014.05.001
Zhu, J., & Liu, W. (2020). A tale of two databases: The use of Web of Science and Scopus in academic papers. Scientometrics, 123(1), 321–335.
Chen, K., Zhang, Y., & Fu, X. (2019). International research collaboration: An emerging domain of innovation studies? Research Policy, 48(1), 149–168. https://doi.org/10.1016/j.respol.2018.08.005
Mostafa, M. M. (2020). A knowledge domain visualization review of thirty years of halal food research: Themes, trends and knowledge structure. Trends in Food Science & Technology, 99, 660–677. https://doi.org/10.1016/j.tifs.2020.03.022
Yu, D., & Sheng, L. (2020). Knowledge diffusion paths of blockchain domain: The main path analysis. Scientometrics, 125(1), 471–497. https://doi.org/10.1007/s11192-020-03650-y
Tseng, F.-M., Palma Gil, E. I. N., & Lu, L. Y. Y. (2021). Developmental trajectories of blockchain research and its major subfields. Technology in Society, 66, 101606. https://doi.org/10.1016/j.techsoc.2021.101606
Xu, S., Hao, L., An, X., Pang, H., & Li, T. (2020). Review on emerging research topics with key-route main path analysis. Scientometrics, 122(1), 607–624. https://doi.org/10.1007/s11192-019-03288-5
Hummon, N. P., & Dereian, P. (1989). Connectivity in a citation network: The development of DNA theory. Social Networks, 11(1), 39–63. https://doi.org/10.1016/0378-8733(89)90017-8
Liu, J. S., Lu, L. Y. Y., & Ho, M.H.-C. (2019). A few notes on main path analysis. Scientometrics, 119(1), 379–391. https://doi.org/10.1007/s11192-019-03034-x
Fontana, R., Nuvolari, A., & Verspagen, B. (2009). Mapping technological trajectories as patent citation networks. An application to data communication standards. Economics of Innovation and New Technology, 18(4), 311–336. https://doi.org/10.1080/10438590801969073
Batagelj, V. (2003). Efficient algorithms for citation network analysis. Retrieved from arXiv:cs/0309023
Liu, J. S., & Lu, L. Y. Y. (2012). An integrated approach for main path analysis: Development of the Hirsch index as an example. Journal of the American Society for Information Science and Technology, 63(3), 528–542. https://doi.org/10.1002/asi.21692
Hirsch, J. E. (2005). An index to quantify an individual’s scientific research output. Proceedings of the National Academy of Sciences, 102(46), 16569–16572. https://doi.org/10.1073/pnas.0507655102
Egghe, L. (2006). Theory and practise of the g-index. Scientometrics, 69(1), 131–152.
Bornmann, L., & Daniel, H.-D. (2005). Does the h-index for ranking of scientists really work? Scientometrics, 65(3), 391–392.
Mingers, J. (2009). Measuring the research contribution of management academics using the Hirsch-index. Journal of the Operational Research Society, 60(9), 1143–1153. https://doi.org/10.1057/jors.2008.94
Saad, G. (2009). Applying the h-index in exploring bibliometric properties of elite marketing scholars. Scientometrics, 83(2), 423–433. https://doi.org/10.1007/s11192-009-0069-z
van Eck, N. J., & Waltman, L. (2011). Text mining and visualization using VOSviewer. arXiv:1109.2058
Kranz, M., Holleis, P., & Schmidt, A. (2010). Embedded interaction: Interacting with the Internet of Things. IEEE Internet Computing, 14(2), 46–53. https://doi.org/10.1109/MIC.2009.141
Xu, L. D. (2011). Information architecture for supply chain quality management. International Journal of Production Research, 49(1), 183–198. https://doi.org/10.1080/00207543.2010.508944
Fu, C., Zhang, G., Yang, J., & Liu, X. (2011). Study on the contract characteristics of Internet architecture. Enterprise Information Systems, 5(4), 495–513. https://doi.org/10.1080/17517575.2011.570457
Li, S., Xu, L. D., & Wang, X. (2013). Compressed sensing signal and data acquisition in Wireless Sensor Networks and Internet of Things. IEEE Transactions on Industrial Informatics, 9(4), 2177–2186. https://doi.org/10.1109/TII.2012.2189222
He, W., Yan, G., & Xu, L. D. (2014). Developing vehicular data cloud services in the IoT environment. IEEE Transactions on Industrial Informatics, 10(2), 1587–1595. https://doi.org/10.1109/TII.2014.2299233
Gershenfeld, N., Krikorian, R., & Cohen, D. (2004). The Internet of Things. Scientific American, 291(4), 76–81. https://doi.org/10.1038/scientificamerican1004-76
Welbourne, E., Battle, L., Cole, G., Gould, K., Rector, K., Raymer, S., Balazinska, M., & Borriello, G. (2009). Building the Internet of Things using RFID the RFID ecosystem experience. IEEE Internet Computing, 13(3), 48–55. https://doi.org/10.1109/MIC.2009.52
Miorandi, D., Sicari, S., De Pellegrini, F., & Chlamtac, I. (2012). Internet of things: Vision, applications and research challenges. Ad Hoc Networks, 10(7), 1497–1516. https://doi.org/10.1016/j.adhoc.2012.02.016
Su, X., Shao, G., Vause, J., & Tang, L. (2013). An integrated system for urban environmental monitoring and management based on the Environmental Internet of Things. International Journal of Sustainable Development and World Ecology, 20(3), 205–209. https://doi.org/10.1080/13504509.2013.782580
Wang, H., Zhang, T., Quan, Y., & Dong, R. (2013). Research on the framework of the Environmental Internet of Things. International Journal of Sustainable Development and World Ecology, 20(3), 199–204. https://doi.org/10.1080/13504509.2013.783517
Wang, S., Zhang, Z., Ye, Z., Wang, X., Lin, X., & Chen, S. (2013). Application of Environmental Internet of Things on water quality management of urban scenic river. International Journal of Sustainable Development and World Ecology, 20(3), 216–222. https://doi.org/10.1080/13504509.2013.785040
Xu, L. D., He, W., & Li, S. (2014). Internet of Things in industries: A survey. IEEE Ttransactions on Industrial Informatics, 10(4), 2233–2243. https://doi.org/10.1109/TII.2014.2300753
Tao, F., Zuo, Y., Xu, L. D., & Zhang, L. (2014). IoT-Based intelligent perception and access of manufacturing resource toward cloud manufacturing. IEEE Ttransactions on Industrial Informatics, 10(2), 1547–1557. https://doi.org/10.1109/TII.2014.2306397
Tao, F., Cheng, Y., Xu, L. D., Zhang, L., & Li, B. H. (2014). CCIoT-CMfg: Cloud computing and Internet of Things-based cloud manufacturing service system. I IEEE Ttransactions on Industrial Informatics, 10(2), 1435–1442. https://doi.org/10.1109/TII.2014.2306383
Li, S., Xu, L. D., & Zhao, S. (2015). The internet of things: A survey. Information Systems Frontiers, 17(2), 243–259. https://doi.org/10.1007/s10796-014-9492-7
Butun, I., Erol-Kantarci, M., Kantarci, B., & Song, H. (2016). Cloud-centric multi-level authentication as a service for secure public safety device networks. IEEE Communications Magazine, 54(4), 47–53. https://doi.org/10.1109/MCOM.2016.7452265
Voegler, M., Schleicher, J. M., Inzinger, C., & Dustdar, S. (2016). A scalable framework for provisioning large-scale IoT deployments. ACM Transactions on Internet Technology. https://doi.org/10.1145/2850416
Fraga-Lamas, P., Fernandez-Carames, T. M., Suarez-Albela, M., Castedo, L., & Gonzalez-Lopez, M. (2016). A review on Internet of Things for defense and public safety. Sensors. https://doi.org/10.3390/s16101644
Fraga-Lamas, P., Noceda-Davila, D., Fernandez-Carames, T. M., Diaz-Bouza, M. A., & Vilar-Montesinos, M. (2016). Smart pipe system for a shipyard 4.0. Sensors. https://doi.org/10.3390/s16122186
Perez-Exposito, J. P., Fernandez-Carames, T. M., Fraga-Lamas, P., & Castedo, L. (2017). VineSens: An eco-smart decision-support viticulture system. Sensors. https://doi.org/10.3390/s17030465
Blanco-Novoa, O., Fernandez-Carames, T. M., Fraga-Lamas, P., & Castedo, L. (2017). An electricity price-aware open-source smart socket for the Internet of Energy. Sensors. https://doi.org/10.3390/s17030643
Fraga-Lamas, P., Fernandez-Carames, T. M., & Castedo, L. (2017). Towards the Internet of Smart trains: A review on industrial IoT-connected railways. Sensors. https://doi.org/10.3390/s17061457
Fraga-Lamas, P., Fernandez-Carames, T. M., Blanco-Novoa, O., & Vilar-Montesinos, M. A. (2018). A review on industrial Augmented Reality systems for the industry 4.0 shipyard. IEEE Access, 6, 13358–13375. https://doi.org/10.1109/ACCESS.2018.2808326
Hernandez-Rojas, D. L., Fernandez-Carames, T. M., Fraga-Lamas, P., & Escudero, C. J. (2018). Design and practical evaluation of a family of lightweight protocols for heterogeneous sensing through BLE beacons in IoT telemetry applications. Sensors. https://doi.org/10.3390/s18010057
Fernandez-Carames, T. M., & Fraga-Lamas, P. (2018). A review on the use of blockchain for the Internet of Things. IEEE Access, 6, 32979–33001. https://doi.org/10.1109/ACCESS.2018.2842685
Fernandez-Carames, T. M., Fraga-Lamas, P., Suarez-Albela, M., & Diaz-Bouza, M. A. (2018). A fog computing based cyber-physical system for the automation of pipe-related tasks in the industry 4.0 shipyard. Sensors, 1, 1. https://doi.org/10.3390/s18061961
Blanco-Novoa, O., Fernandez-Carames, T. M., Fraga-Lamas, P., & Castedo, L. (2018). A cost-effective IoT system for monitoring indoor radon gas concentration. Sensors. https://doi.org/10.3390/s18072198
Hernandez-Rojas, D. L., Fernandez-Carames, T. M., Fraga-Lamas, P., & Escudero, C. J. (2018). A plug-and-play human-centered virtual TEDS architecture for the Web of Things. Sensors. https://doi.org/10.3390/s18072052
Froiz-Míguez, I., Fernández-Caramés, T. M., Fraga-Lamas, P., & Castedo, L. (2018). Design, implementation and practical evaluation of an IoT home automation system for fog computing applications based on MQTT and ZigBee-WiFi sensor nodes. Sensors, 18(8), 2660. https://doi.org/10.3390/s18082660
Suárez-Albela, M., Fraga-Lamas, P., Castedo, L., & Fernández-Caramés, T. M. (2019). Clock frequency impact on the performance of high-security cryptographic cipher suites for energy-efficient resource-constrained IoT devices. Sensors, 19(1), 15. https://doi.org/10.3390/s19010015
Fernandez-Carames, T. M., & Fraga-Lamas, P. (2018). Towards the Internet of Smart clothing: A review on IoT wearables and garments for creating intelligent connected e-textiles. Electronics. https://doi.org/10.3390/electronics7120405
Fraga-Lamas, P., & Fernandez-Carames, T. M. (2019). A review on blockchain technologies for an advanced and cyber-resilient automotive industry. IEEE Access, 7, 17578–17598. https://doi.org/10.1109/ACCESS.2019.2895302
Fernandez-Carames, T. M., & Fraga-Lamas, P. (2019). A review on the application of blockchain to the next generation of cybersecure industry 4.0 smart factories. IEEE Access., 7, 45201–45218. https://doi.org/10.1109/ACCESS.2019.2908780
Alladi, T., Chamola, V., Parizi, R. M., & Choo, K.-K.R. (2019). Blockchain applications for industry 4.0 and industrial IoT: A review. IEEE Access, 7, 176935–176951. https://doi.org/10.1109/ACCESS.2019.2956748
Hassija, V., Chamola, V., Krishna, D. N. G., & Guizani, M. (2020). A distributed framework for energy trading between UAVs and charging stations for critical applications. IEEE Transactions on Vehicular Technology, 69(5), 5391–5402. https://doi.org/10.1109/TVT.2020.2977036
Chamola, V., Hassija, V., Gupta, V., & Guizani, M. (2020). A comprehensive review of the COVID-19 pandemic and the role of IoT, drones, AI, blockchain, and 5G in managing its impact. IEEE Access, 8, 90225–90265. https://doi.org/10.1109/ACCESS.2020.2992341
Javaid, M., Haleem, A., Singh, R. P., Haq, M. I. U., Raina, A., & Suman, R. (2020). Industry 5.0: Potential applications in COVID-19. Journal of Industrial Integration and Management-Innovation and Entrepreneurship, 5(4), 507–530. https://doi.org/10.1142/S2424862220500220
Hedayatipour, A., & Mcfarlane, N. (2020). Wearables for the next pandemic. IEEE Access, 8, 184457–184474. https://doi.org/10.1109/ACCESS.2020.3029130
Ndiaye, M., Oyewobi, S. S., Abu-Mahfouz, A. M., Hancke, G. P., Kurien, A. M., & Djouani, K. (2020). IoT in the wake of COVID-19: A survey on contributions, challenges and evolution. IEEE Access, 8, 186821–186839. https://doi.org/10.1109/ACCESS.2020.3030090
Kumar, R. N. V., Arun, M., Baraneetharan, E., Prakash, S. J. J., Kanchana, A., & Prabu, S. (2020). Detection and monitoring of the asymptotic COVID-19 patients using IoT devices and sensors. International Journal of Pervasive Computing and Communications. https://doi.org/10.1108/IJPCC-08-2020-0107
Alanazi, S. A., Kamruzzaman, M. M., Alruwaili, M., Alshammari, N., Alqahtani, S. A., & Karime, A. (2020). Measuring and preventing COVID-19 using the SIR model and machine learning in smart health care. Journal of Healthcare Engineering. https://doi.org/10.1155/2020/8857346
Pranggono, B., & Arabo, A. (2021). COVID-19 pandemic cybersecurity issues. Internet Technology Letters. https://doi.org/10.1002/itl2.247
Hakak, S., Khan, W. Z., Imran, M., Choo, K.-K.R., & Shoaib, M. (2020). Have you been a victim of COVID-19-related cyber incidents? Survey, taxonomy, and mitigation strategies. IEEE Access, 8, 124134–124144. https://doi.org/10.1109/ACCESS.2020.3006172
Zhang, J., & Wu, M. (2020). Blockchain use in IoT for privacy-preserving anti-pandemic home quarantine. Electronics. https://doi.org/10.3390/electronics9101746
Hasan, H. R., Salah, K., Jayaraman, R., Arshad, J., Yaqoob, I., Omar, M., & Ellahham, S. (2020). Blockchain-based solution for COVID-19 digital medical passports and immunity certificates. IEEE Access, 8, 222093–222108. https://doi.org/10.1109/ACCESS.2020.3043350
Gupta, R., Kumari, A., & Tanwar, S. (2021). Fusion of blockchain and artificial intelligence for secure drone networking underlying 5G communications. Transactions on Emerging Telecommunications Technologies. https://doi.org/10.1002/ett.4176
Nie, Y., Zhao, J., Liu, J., Jiang, J., & Ding, R. (2020). Energy-efficient UAV trajectory design for backscatter communication: A deep reinforcement learning approach. China Communications, 17(10), 129–141.
Shubina, V., Holcer, S., Gould, M., & Lohan, E. S. (2020). Survey of decentralized solutions with mobile devices for user location tracking, proximity detection, and contact tracing in the COVID-19 era. Data. https://doi.org/10.3390/data5040087
Fernandez-Carames, T. M., Froiz-Miguez, I., Blanco-Novoa, O., & Fraga-Lamas, P. (2019). Enabling the internet of mobile crowdsourcing health things: A mobile fog computing, blockchain and IoT based continuous glucose monitoring system for diabetes mellitus research and care. Sensors. https://doi.org/10.3390/s19153319
Fraga-Lamas, P., Ramos, L., Mondejar-Guerra, V., & Fernandez-Carames, T. M. (2019). A review on IoT deep learning UAV systems for autonomous obstacle detection and collision avoidance. Remote Sensing. https://doi.org/10.3390/rs11182144
Haseeb, K., Ud Din, I., Almogren, A., Islam, N., & Altameem, A. (2020). RTS: A robust and trusted scheme for IoT-based mobile wireless mesh networks. IEEE Access, 8, 68379–68390. https://doi.org/10.1109/ACCESS.2020.2985851
Ali, Z., Shah, M. A., Almogren, A., Din, I. U., Maple, C., & Khattak, H. A. (2020). Named data networking for efficient IoT-based disaster management in a smart campus. Sustainability. https://doi.org/10.3390/su12083088
Janjua, K., Shah, M. A., Almogren, A., Khattak, H. A., Maple, C., & Din, I. U. (2020). Proactive forensics in IoT: Privacy-aware log-preservation architecture in fog-enabled-cloud Using holochain and containerization technologies. Electronics. https://doi.org/10.3390/electronics9071172
Hsu, C.-L., Chen, W.-X., & Le, T.-V. (2020). An autonomous log storage management protocol with blockchain mechanism and access control for the Internet of Things. Sensors. https://doi.org/10.3390/s20226471
Bano, A., Ud Din, I., & Al-Huqail, A. A. (2020). AIoT-based smart bin for real-time monitoring and management of solid waste. Scientific Programming. https://doi.org/10.1155/2020/6613263
Butun, I., Erol-Kantarci, M., Kantarci, B., & Song, H. (2016). Cloud-centric multi-level authentication as a service for secure public safety device networks. IEEE Communications Magazine, 54(4), 47–53. Presented at the IEEE Communications Magazine. https://doi.org/10.1109/MCOM.2016.7452265
Fernandez-Carames, T. M., Fraga-Lamas, P., Suarez-Albela, M., & Castedo, L. (2017). Reverse engineering and security evaluation of commercial tags for RFID-based IoT applications. Sensors. https://doi.org/10.3390/s17010028
Suarez-Albela, M., Fraga-Lamas, P., Castedo, L., & Fernandez-Carames, T. M. (2019). Clock frequency impact on the performance of high-security cryptographic cipher suites for energy-efficient resource-constrained IoT devices. Sensors. https://doi.org/10.3390/s19010015
Suarez-Albela, M., Fraga-Lamas, P., & Fernandez-Carames, T. M. (2018). A practical evaluation on RSA and ECC-based cipher suites for IoT high-security energy-efficient fog and mist computing devices. Sensors. https://doi.org/10.3390/s18113868
Yuly, A. R., & Pradana, H. (2020). Systematic Literature Review (SLR) Development of the IoT Industry in the Southeast Asian Region. In 2020 3rd international conference on computer and informatics engineering (IC2IE) (pp. 460–466). https://doi.org/10.1109/IC2IE50715.2020.9274619
Rejeb, A., Rejeb, K., Zailani, S., Treiblmaier, H., & Hand, K. J. (2021). Integrating the Internet of Things in the halal food supply chain: A systematic literature review and research agenda. Internet of Things, 13, 100361. https://doi.org/10.1016/j.iot.2021.100361
Liang, H., Wang, J.-J., Xue, Y., & Cui, X. (2016). IT outsourcing research from 1992 to 2013: A literature review based on main path analysis. Information & Management, 53(2), 227–251. https://doi.org/10.1016/j.im.2015.10.001
Kumar, K., Kumar, N., & Shah, R. (2020). Role of IoT to avoid spreading of COVID-19. International Journal of Intelligent Networks, 1, 32–35. https://doi.org/10.1016/j.ijin.2020.05.002
Funding
The authors have no funding to report.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no conflict of interest to declare.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rejeb, A., Rejeb, K., Zailani, S. et al. Knowledge Diffusion of the Internet of Things (IoT): A Main Path Analysis. Wireless Pers Commun 126, 1177–1207 (2022). https://doi.org/10.1007/s11277-022-09787-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-022-09787-8