Abstract
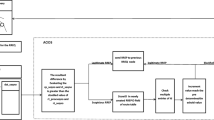
The decentralized administration and the lack of an appropriate infrastructure causes the MANET prone to attacks. The attackers play on the vulnerable characteristics of the MANET and its underlying routing protocols such as AODV, DSR etc. to bring about a disruption in the data forwarding operation. Hence, the routing protocols need mechanisms to confront and tackle the attacks by the intruders. This research introduces the novel host-based intrusion detection system (HIDS) known as analytical termination of malicious nodes (ATOM) that systematically detects one of the most significant black hole attacks that affects the performance of AODV routing protocol. ATOM IDS performs detection by computing the RREP count (Route Reply) and the packet drop value for each individual node. This system has been simulated over the AODV routing protocol merged with the black hole nodes and the resultant simulation scenario in NS2 has been generated. The trace obtained shows a colossal increase in the packet delivery ratio (PDR) and throughput. The results prove the efficacy of the proposed system.





Similar content being viewed by others
References
IETF Mobile Ad-Hoc Networks Working Group (MANET). IETF. https://www.ietf.org/dyn/wg/charter/manet-charter.html
Zhou, L., & Haas, Z. (1999). Securing ad hoc networks. IEEE, 13(6), 24–30.
Nadeem, A., & Howarth, M. P. (2013). A survey of manet intrusion detection & prevention approaches for network layer attacks. Communications Surveys & Tutorials IEEE, 15(4), 2027–2045.
Kumar, S., & Dutta, K. (2016). Intrusion detection in mobile ad hoc networks: Techniques, systems, and future challenges. Security and Communication Networks, 9(14), 2484–2556.
Ad hoc On-Demand Distance Vector (AODV)—Routing protocol. https://tools.ietf.org/html/rfc3561
Sivanesh, S., & Dhulipala, V. S. (2019). Comparitive analysis of blackhole and rushing attack in MANET. In 2019 TEQIP III sponsored international conference on microwave integrated circuits, photonics and wireless networks (IMICPW) (pp. 495–499). IEEE.
Marti, S., Giuli, T. J., Lai, K., & Baker, M. (2000). Mitigating routing misbehavior in mobile ad hoc networks. ACM, 255–265.
Buchegger, S., & Le Boudec, J. Y. (2002). Performance analysis of the CONFIDANT protocol. In Proceedings of the 3rd ACM international symposium on mobile ad hoc networking & computing (pp. 226–236). ACM.
Hassan, H. M., Mahmoud, M., & El-Kassas, S. (2006). Securing the AODV protocol using specification-based intrusion detection. In Proceedings of the 2nd ACM international workshop on Quality of service & security for wireless and mobile networks (pp. 33–36). ACM.
Shakshuki, E. M., Kang, N., & Sheltami, T. R. (2012). EAACK—a secure intrusion-detection system for MANETs. IEEE Transactions on Industrial Electronics, 60(3), 1089–1098.
Su, M. Y. (2011). Prevention of selective black hole attacks on mobile ad hoc networks through intrusion detection systems. Computer Communications, 34(1), 107–117.
Raj, P. N., & Swadas, P.B. (2009). Dpraodv: A dyanamic learning system against blackhole attack in aodv based manet. arxiv preprint arXiv:0909.2371.
Rajeswari, A. R., Kulothungan, K., & Kannan, A. (2016). GNBAODV: Guard node based–aodv to mitigate black hole attack in MANET. International Journal of Scientific Research in Science, Engineering and Technology, 2(6), 671–677.
Sivanesh, S., & Dhulipala, V. S. (2020). Accurate and cognitive intrusion detection system (ACIDS): A novel black hole detection mechanism in mobile ad hoc networks. Mobile Networks and Applications, 1–9.
The Network Simulator NS-2 version 2.35. http://www.isi.edu/nsnam/ns/index.html.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest exists between the authors or financial or personal relationship with a third party whose interests could be positively or negatively influenced by the article’s content.
Ethical Approval
This article does not contain any studies with human participants performed by any of the authors (Or). This article does not contain any studies with animals performed by any of the authors (Or). This article does not contain any studies with human participants or animals performed by any of the authors.
Informed consent
This article does not contain any human participants in the study.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sivanesh, S., Sarma Dhulipala, V.R. Analytical Termination of Malicious Nodes (ATOM): An Intrusion Detection System for Detecting Black Hole attack in Mobile Ad Hoc Networks. Wireless Pers Commun 124, 1511–1524 (2022). https://doi.org/10.1007/s11277-021-09418-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-09418-8