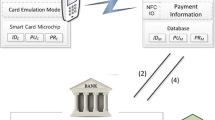
Abstract
Near field communication (NFC) is one of the utmost pullulating technology in the lea of pervasive computing. In the domain of mobile commerce, mobile payments have advantages akin user convenience (anytime and anywhere) enhanced throughout. Several mutual authentication protocols by this time have been schemed to provide security in NFC applications. To guarantee secure communication a conditional privacy preserving security protocol, pseudonym-based NFC protocol and secure and efficient authentication protocol were schemed which could not forfend impersonation attack. In the direction of guaranteeing safe communication a security protocol for NFC-based mobile payments have been proposed. The proposed NFC-based authentication protocol (NAP) describes a simplified authentication process and pawn secure information in mobile commerce transaction. A major concern when using NFC-enabled mobile payment system is user anonymity therefore, users in the mobile payment system are guaranteed their anonymity with the help of pseudonym. The payment transactions are susceptible to variant attacks like replay attack, impersonation attack, man in the middle attack/relay attack and double spending attack thereupon, NAP is the first concern to defend an unauthorized user from retrieving the sensitive payment transaction information.






Similar content being viewed by others
References
Odelu, V., Das, A. K., & Goswami, A. (2016). SEAP: Secure and efficient authentication protocol for NFC applications using pseudonyms. IEEE Transactions on Consumer Electronics, 62(1), 30–38. https://doi.org/10.1109/TCE.2016.7448560
Coskun, V., Ozdenizci, B., & Ok, K. (2013). A survey on near field communication (NFC) technology. Wireless Personal Communications, 71(3), 2259–2294.
Yang, J. H., & Chang, C. C. (2012). A low computational-cost electronic payment scheme for mobile commerce with large-scale mobile users. Wireless Personal Communications, 63, 83. https://doi.org/10.1007/s11277-010-0109-2
Available: https://www.insidesecure.com/Company/More/whitepapers/Securing-Mobile-Payments, 9, May 2019.
Vishwakarma, P. P., Tripathy, A. K., & Vemuru, S. (2020). Designing a cryptosystem for data at rest encryption in mobile payments. International Journal of Applied Science and Engineering, 17, 373–382. https://doi.org/10.6703/IJASE.202012_17(4).373
Vishwakarma, P., Tripathy, A. K., & Vemuru, S. (2016). A hybrid security framework for near field communication driven mobile payment model. International Journal of Computer Science and Information Security, 14(12), 337–348.
Gorantla, M. C., Boyd, C., Nieto, J. M. G., & Manulis, M. (2011). Modeling key compromise impersonation attacks on group key exchange protocols. ACM Transactions on Information and System Security (TISSEC), 14(4), Article No. 28. https://doi.org/10.1145/2043628.2043629
Wu, L., Zhang, Y., Xie, Y., et al. (2017). An efficient and secure identity-based authentication and key agreement protocol with user anonymity for mobile devices. Wireless Personal Communications, 94, 3371. https://doi.org/10.1007/s11277-016-3781-z
Goga, O., Venkatadri, G., and Gummadi, K.P. (2015). The doppelgänger bot attack: Exploring identity impersonation in online social networks. In Proceedings of the 2015 internet measurement conference (IMC '15). ACM, Tokyo, Japan (pp. 141–153). https://doi.org/10.1145/2815675.2815699
Gummeson, J.J., Priyantha, B., Ganesan, D., Thrasher, D., and Zhang, P. (2013). EnGarde: Protecting the mobile phone from malicious NFC interactions. In Proceeding of the 11th Annual International Conference on Mobile systems, applications, and services (MobiSys '13). ACM, Taipei, Taiwan (pp. 445–458). https://doi.org/10.1145/2462456.2464455.
Thiranant, N., Lee, Y.S., and Lee, H. (2015). Performance comparison between RSA and elliptic curve cryptography-based QR code authentication In 2015 IEEE 29th international conference on advanced information networking and applications workshops, Gwangiu, South Korea (pp. 278–282).
Gurulian, I., Akram, R.N., Markantonakis, K., and Mayes, K. (2017). Preventing relay attacks in mobile transactions using infrared light. In Proceedings of the Symposium on Applied Computing (SAC '17). ACM, Marrakech, Morocco (pp. 1724–1731). https://doi.org/10.1145/3019612.3019794.
Akinyokun, N., and Teague, V. (2017). Security and privacy implications of NFC-enabled contactless payment systems. In Proceedings of the 12th International conference on availability, reliability and security (ARES '17). ACM, Reggio Calabria, Italy Article 47, 10 pages. https://doi.org/10.1145/3098954.3103161.
Eun, H., Lee, H., & Oh, H. (2013). Conditional privacy preserving security protocol for NFC applications. IEEE Transactions on Consumer Electronics, 59(1), 153–160. https://doi.org/10.1109/TCE.2013.6490254
He, D., Kumar, N., & Lee, J. H. (2015). Secure pseudonym-based near field communication protocol for the consumer internet of things. IEEE Transactions on Consumer Electronics, 61(1), 56–62. https://doi.org/10.1109/TCE.2015.7064111
Xu, J., Xue, K., Yang, Q., & Hong, P. (2018). PSAP: Pseudonym-based secure authentication protocol for NFC applications. IEEE Transactions on Consumer Electronics, 64(1), 83–91. https://doi.org/10.1109/TCE.2018.2811260
Yang, S. S., Jang, Y. H., Park, M. H., et al. (2021). Design and implementation of active access control system by using NFC-based EAP-AKA protocol. Wireless Personal Communications. https://doi.org/10.1007/s11277-021-08139-2
Madhoun, N.E., Guenane, F., and Pujolle, G. (2015). A cloud-based secure authentication protocol for contactless-NFC payment. In 2015 IEEE 4th international conference on cloud networking (CloudNet), Niagara Falls, ON (pp. 328–330). https://doi.org/10.1109/CloudNet.2015.733533.
Boureanu, I., Chen, L., and Ivey, S. (2020). Provable-security model for strong proximity-based attacks: With application to contactless payments. In Proceedings of the 15th ACM asia conference on computer and communications security (ASIA CCS '20). Association for Computing Machinery, New York, NY, USA (pp. 87–100). https://doi.org/10.1145/3320269.3384748.
Al-Haj, A., and Al-Tameemi, M.A. (2018). Providing security for NFC-based payment systems using a management authentication server. In 2018 4th International conference on information management (ICIM) (pp. 184–187). https://doi.org/10.1109/INFOMAN.2018.8392832.
Li, P., Fang, H., Liu, X., and Yang, B. (2017)) A countermeasure against relay attack in NFC payment. In Proceedings of the second international conference on internet of things, data and cloud computing (ICC '17). ACM, Cambridge, United Kingdom, Article 96 (5 pages). https://doi.org/10.1145/3018896.3025144.
Cavdar, D., and Tomur, E. (2015). A practical NFC relay attack on mobile devices using card emulation mode. In 2015 38th International convention on information and communication technology, electronics and microelectronics (MIPRO), Opatija (pp. 1308–1312). https://doi.org/10.1109/MIPRO.2015.7160477
Francis, L., Hancke, G., Mayes, K., & Markantonakis, K. (2010). Practical NFC peer-to-peer relay attack using mobile phones. In S. B. Ors Yalcin (Ed.), Radio frequency identification: security and privacy issues. RFIDSec 2010. Lecture notes in computer science. (Vol. 6370). Springer.
Luo, J. N., Yang, M. H., & Huang, S.-Y. (2016). An unlinkable anonymous payment scheme based on near field communication. Computers & Electrical Engineering, 49, 198–206. https://doi.org/10.1016/j.compeleceng.2015.08.007
Ceipidor, U.B., Medaglia, C.M., Marino, A., Sposato, S., and Moroni, A. (2012). KerNeeS: A protocol for mutual authentication between NFC phones and POS terminals for secure payment transactions. In 2012 9th international ISC conference on information security and cryptology, Tabriz (pp. 115–120). https://doi.org/10.1109/ISCISC.2012.6408203
Fan, K., Li, H., Jiang, W., Xiao, C., and Yang, Y. (2017). U2F based secure mutual authentication protocol for mobile payment. In Proceedings of the ACM turing 50th celebration conference - China (ACM TUR-C '17), Article 27, Shanghai, China. (6 pages). https://doi.org/10.1145/3063955.3063982.
Alabrah, A., and Bassiouni, M. (2017). Preventing single sign-on impersonation attacks with a keyless signature scheme. In 2017 10th IFIP wireless and mobile networking conference (WMNC), Valencia (pp. 1–7). https://doi.org/10.1109/WMNC.2017.8248852
Badra, M., Badra, R.B. (2016). A lightweight security protocol for NFC-based mobile payments. Procedia Computer Science, vol. 83 (pp. 705–711) ISSN 1877-0509. https://doi.org/10.1016/j.procs.2016.04.156.
Li, D., Wong, W.E., Chau, M., Pan, S., and Koh, L.S. (2020). A survey of NFC mobile payment: Challenges and solutions using Blockchain and Cryptocurrencies. In 2020 7th International conference on dependable systems and their applications (DSA) (pp. 69–77) https://doi.org/10.1109/DSA51864.2020.00018.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Vishwakarma, P.P., Tripathy, A.K. & Vemuru, S. Cryptanalysis of Near Field Communication Based Authentication Protocol for Mobile Payment System. Wireless Pers Commun 121, 963–983 (2021). https://doi.org/10.1007/s11277-021-08667-x
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08667-x