Abstract
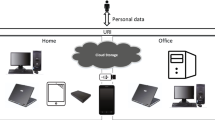
Small and medium sized businesses have lacked of good and automate backup system. Data storages are unreliable and tend to fail without any warning. Whereas, personal computers are already equipped with terabytes of hard drives. This is enormous space for personal or business use. Under normal working conditions, more than half of total storage space is not being used. It is scattered in all connected devices. This paper proposes pooling unused storage resources to create a personal private cloud. The process will be transparent to the users by having a reliable drive with an auto backup built in. The proposed system solution uses a replica-based model in which three sets of the same information would distribute and keep in three different nodes. All the participated nodes are peer-to-peer (P2P) and are decentralized. Therefore, private cloud system can support small or medium businesses as backup system or business sharing drives without adding any cost.














Similar content being viewed by others
References
Upra, R. (2016). Survey Local Small and Medium Business 8–12 October 2016. Resource document. Retrieved July 2020, from https://tinyurl.com/y8z6zhue.
Eddy, N. (2013). Small Businesses Unprepared for Data Loss, Lack Backup Policies, eWeek, November 14. Resource document. Eweek. http://www.eweek.com/security/small-businesses-unprepared-for-data-loss-lack-backup-policies Accessed July 2020.
Yaibuates, M., & Chaisricharoen, R. (2019). Starvation delayed DHCP service for enabling pool recovery. Malaysian Journal of Computer Science. https://doi.org/10.22452/mjcs.sp2019no2.2
Yaibuates, M., & Chaisricharoen, R. (2020). A combination of ICMP and ARP for DHCP. In Proceeding of the 5th international conference on digital arts, media and technology and 3rd ECTI Northern section conference on electrical, electronics, computer and telecommunications engineering. https://doi.org/10.1109/ECTIDAMTNCON48261.2020.9090760
Ponemon Institute. (2015). Cost of Data Breach Study: Global Analysis. Retrieved July 2020, from https://nhlearningsolutions.com/Portals/0/Documents/2015-Cost-of-Data-Breach-Study.PDF.
Womack, B. (2015). Dell Says 'Large' Number of Companies Return From Public Cloud. Resource document. Bloomberg. Retrieved July 2020, from https://www.bloomberg.com/news/articles/2017-05-09/dell-says-large-number-of-companies-return-after-pricey-public-cloud.
Upra, R., & Chaisricharoen, R. (2014). Workgroup Distribution File System (WDFS) for personal cloud system. https://doi.org/10.1109/JICTEE.2014.6804091
Upra, R., Yaibuates, M., & Chaisricharoen, R. (2016). Data recovery for workgroup distribution file system (WDFS). In Proceedings of the 6th global wireless summit, 2016, GWS 2016 (pp. 68–71).
Stoica, I., Morris, R., Liben-Nowell, D., Kanger, D. R., Kasshoek, M. F., Dabek, F., & Balakrishnan, H. (2003). Chord: a scalable Peer-to-peer lookup protocol for Internet applications. IEEE/ACM Transactions on Networking. https://doi.org/10.1109/TNET.2002.808407.
Rowstron, A. & Druschel, P. (2001). Pastry: Scalable, decentralized object location, and routing for large-scale peer-to-peer systems. In Proceedings of the IFIP/ACM international conference on distributed systems platforms Heidelberg, 2001 (pp. 329–350).
Matei, R., Lamnitchi, A., & Foster, P. (2002). Mapping the gnutella network. IEEE Internet Computing. https://doi.org/10.1109/4236.978369.
Parameswaran, M., Susarla, A., & Whinston, A. B. (2001). P2P networking: an information sharing alternative. IEEE Computer Society. https://doi.org/10.1109/2.933501.
Guo, L., Chen, S., & Xiao, Z. (2007). A performance study of BitTorrent-like peer-to-peer systems. IEEE Journal on Selected Areas in Communications. https://doi.org/10.1109/JSAC.2007.070116.
Katz, R. H. (1992). Network-attached storage systems. In Proceedings of scalable high performance computing conference, 1992. SHPCC-92. https://doi.org/10.1109/SHPCC.1992.232686
Qiu, S., Zhou, J. & Yang, T. (2013). Versioned file backup and synchronization for storage clouds. In Proceedings of the 13th IEEE/ACM international symposium on cluster, cloud, and grid computing. https://doi.org/10.1109/CCGrid.2013.60
Katal, A., Gupta, N., Sharma, S. (2012). Information storage on the cloud: A survey of effective storage management system. In Proceeding of the 2012 students conference on engineering and systems. https://doi.org/10.1109/SCES.2012.6199040
Pinho, A. & Neves, A. (2006). Lossy-to-lossless compression of images based on binary tree decomposition. In Proceeding of the 2006 international conference on image processing. https://doi.org/10.1109/ICIP.2006.312812
Rufai, M.A., Anbarjafari, G., & Demirel, H. (2013). Lossy medical image compression using Huffman coding and singular value decomposition. In Proceeding of the 21st signal processing and communications applications conference (SIU), 2013. https://doi.org/10.1109/SIU.2013.6531592
Robert, L., & Nadarajan, R. (2009). Simple lossless preprocessing algorithms for text compression. IET Software. https://doi.org/10.1049/iet-sen:20070106.
Fanfara, P., Danková, E. & Dufala, M. (2012). Usage of asymmetric encryption algorithms to enhance the security of sensitive data in secure communication. In Proceeding of the IEEE 10th international symposium on applied machine intelligence and informatics, 2012. https://doi.org/10.1109/SAMI.2012.6208959
Bharadwaj, Y. & Chakraverty, S. (2013). A design pattern for symmetric encryption. In Proceeding of 2013 international conference on control computing communication & materials. https://doi.org/10.1109/ICCCCM.2013.6648912
Guo, G., Qian, Q. & Zhang, R. (2015). Different implementations of AES cryptographic algorithm. In Proceeding of 2015 IEEE 17th international conference on high performance computing and communications, 2015 IEEE 7th international symposium on cyberspace safety and security, and 2015 IEEE 12th international conference on embedded software and systems. https://doi.org/10.1109/HPCC-CSS-ICESS.2015.215
Lu, C., & Tseng, S. (2002). Integrated design of AES (Advanced Encryption Standard) encrypter and decrypter. Proceedings of IEEE International Conference on Application- Specific Systems, Architectures, and Processors. https://doi.org/10.1109/ASAP.2002.1030726.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Upra, R., Chaisricharoen, R. & Yaibuates, M. Personal Cloud P2P. Wireless Pers Commun 119, 2837–2857 (2021). https://doi.org/10.1007/s11277-021-08372-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-021-08372-9