Abstract
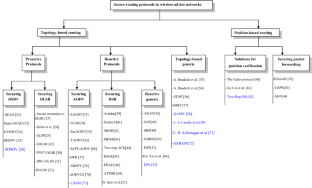
The diverse network technologies and low-end wireless technologies have enabled the deployment of self-organized wireless ad hoc networks. Nodes forming such networks have the ability to autonomously organize and cooperate among them to form an infrastructure that allows data communication in the network. Routing protocols constitute the core of this cooperation. Many routing protocols have been developed to achieve data communication in wireless ad hoc networks and a large number of high quality research papers have appeared and addressed the issue of routing at length. Although they have proved their effectiveness, these routing protocols have been designed for trustworthy environments without any security requirements. However, the presence of an adversary in the network can degrade the routing functionalities and may breaking down the entire network. Therefore, securing routing protocols in such networks becomes an issue. In this paper, we survey the-state-of-the-art of secure routing protocols proposed in the literature that address routing security issue, classifying secure routing protocols in categories according to the secured protocol, and finally discussing the proposed solutions.


Similar content being viewed by others
References
Fleury, M., Kanellopoulos, D., & Qadri, N. N. (2019). Video streaming over MANETs: An overview of techniques. Multimedia Tools and Applications, 78, 23749–23782.
Anjum, S. S., Md Noor, R., & Anisi, M. H. (2017). Review on MANET based communication for search and rescue operations. Wireless Personal Communications, 94, 31–52.
Boukerche, A., et al. (2011). Routing protocols in ad hoc networks: A survey. Computer Networks, 55(13), 3032–3080.
Moussaoui, A., & Boukeream, A. (2015). A survey of routing protocols based on link-stability in mobile ad hoc networks. Journal of Network and Computer Applications, 47, 1–10.
Robinson, Y. H., & Julie, E. G. (2019). MTPKM: Multipart trust based public key management technique to reduce security vulnerability in mobile ad-hoc networks. Wireless Personal Communications, 109, 739–760.
Mohandas, R., & Krishnamoorthi, K. (2017). MANET security betterment by enhanced multiple key management scheme. Wireless Personal Communications, 94, 2173–2188.
Ramesh, V., Subbaiah, D. P., Rao, N. K., & Raju, M. J. (2010). Performance comparison and analysis of DSDV and AODV for MANET. International Journal on Computer Science and Engineering, 2(02), 183–188.
Ade, S. A., & Tijare, P. A. (2010). Performance comparison of AODV, DSDV, OLSR and DSR routing protocols in mobile ad hoc networks. International Journal of Information Technology and Knowledge Management, 2(2), 545–548.
Mulert, J., Welch, I., & Seah, W. K. G. (2012). Security threats and solutions in MANETS: A case study using AODV and SAODV. Journal of Network and Computer Applications, 35(4), 1249–1259.
Stojmenovic, I. (2002). Position-based routing in ad hoc networks. IEEE Communications Magazine, 40(7), 128–134.
Mauve, M., Widmer, J., Hartenstein, H., & Europs, N. (2001). A survey on position based routing in mobile ad hoc networks. IEEE Network, 15(6), 30–39.
Tao, S., Ananda, A. L., & Chan, M. C. (2010). Greedy face routing with face identification support in wireless networks. Computer Networks, 54, 3431–3448.
Chen, D., & Varshney, P. K. (2007). A survey of void handling techniques for geographic routing in wireless networks. IEEE Communications Surveys and Tutorials, 9(1), 50–67.
Karp, B., & Kung, H. T. (2000). GPSR: Greedy perimeter stateless routing for wireless networks. In Proceedings of the 6th annual international conference on mobile computing and networking (pp. 243–254), CM Press.
Frey, H., & Stojmenovic, I. (2006). On delivery guarantees of face and combined greedy face routing in ad hoc and sensor networks. In Proceedings of the 12th international conference on mobile computing and networking (pp. 390–401).
Di Pietro, R., Guarino, S., Verde, N. V., & Domingo-Ferrer, J. (2014). Security in wireless ad-hoc networks—A survey. Computer Communications Journal, 51, 1–20.
Cai, R. J., Tan, W. C., & Chong, P. H. J. (2017). An overview of trust-based routing design under adversarial mobile ad hoc network environment. Wireless Personal Communications, 96, 3923–3946.
Vasudeva, A., & Sood, M. (2018). Survey on sybil attack defense mechanisms in wireless ad hoc networks. Journal of Network and Computer Applications, 120, 78–118.
Rehman, A., Rehman, S. U., & Raheem, H. (2019). Sinkhole attacks in wireless sensor networks: A survey. Wireless Personal Communications, 106, 2291–2313.
Kaur, P., Kaur, D., & Mahajan, R. (2017). Simulation based comparative study of routing protocols under wormhole attack in Manet. Wireless Personal Communications, 96, 47–63.
Qazi, S., Raad, R., Mu, Y., & Susilo, W. (2013). Securing DSR against wormhole attacks in multirate ad hoc networks. Journal of Network and Computer Applications, 36(2), 582–592.
Kaur, P., Kaur, D., & Mahajan, R. (2017). Wormhole attack detection technique in mobile ad hoc networks. Wireless Personal Communications, 97, 2939–2950.
Hu, Y. C., Johnson, D. B., & Perrig, A. (2003). SEAD: Secure efficient distance vector routing for mobile wireless ad hoc networks. Ad HOC Networks, 1(1), 175–192.
Wan, T., Kranakis, E., &Van oorschot, P. (2004). Securing the destination sequenced distance vector routing protocol (s-dsdv). In Proceedings of 6th international conference on information and communications security (pp. 358–374).
Wang, J., Chen, H., & Lin, Y. (2010). A secure destination-sequenced distance-vector routing protocol for ad hoc networks. Journal of Networks, 5(8), 942–948.
Ye, Y., Feng, S., Liu, M., Sun, X., Xu, T., & Tong, X. (2018). A safe proactive routing protocol sdsdv for ad hoc network. International Journal of Wireless Information Networks, 25, 348–357.
Halfslund, A., Tonnesen, A., Rotvik, R. B., Andersson, J., & Kure, O. (2004). Secure extension to the OLSR protocol. In Proceedings of the OLSR interop and workshop, San Diego.
Raffo, D., Clausen, T., Adjih, C., & Muhlethaler, P. (2004). An advanced signature system for OLSR. In Proceedings of the 2nd ACM workshop on security of ad hoc and sensor networks, SASN 04 (pp. 10–16).
Papadimitratos, P. & Haas, Z. J. (2003). Secure link state routing for mobile ad hoc networks. In Proceedings of the IEEE workshop on security and assurance in ad hoc networks, Orlando, FL (pp. 379–383).
Tan, S., Li, X., & Dong, Q. (2015). Trust based routing mechanism for securing OSLR-based MANET. Ad Hoc Networks, 30, 84–98.
Robert, J.-M., Otrok, H., & Chriqi, A. (2012). RBC-OLSR: Reputation-based clustering OLSR protocol for wireless ad hoc networks. Computer Communications, 35, 487–499.
Marimuthu, M., & Krishnamurthi, I. (2013). Enhanced OLSR for defense against DOS attack in ad hoc networks. Journal of Communications and Networks, 15(1), 31–37.
Zapata, M. G. & Asokan, N. (2002). Securing ad hoc routing protocols. In Proceedings of the 2002 ACM workshop on wireless security (WiSe2002) (pp. 1–10) Atlanta Georgia, USA.
Li, Q., Hu, C. Y., Zhao, M., Perrig, A., Walker, J. & Trappe, W. (2008). SEAR: A secure efficient ad hoc on demand routing protocol for wireless networks. In Proceedings of the 2008 ACM symposium on information computer and communications security, ASIACCS'08. New York, NY, USA (pp. 201–204).
Patwardhan, A., Parker, J., Iorga, M., Joshi, A., Karygiannis, T., & Yesha, Y. (2008). Threshold-based intrusion detection in ad hoc networks and secure AODV. Ad Hoc Networks, 6, 578–599.
Li, X., Lyu, M. R., & Liu, J. (2004). A trust model based routing protocol for secure ad hoc networks. In Proceedings of aerospace conference (AC'04) (pp. 1286–1295).
Rajeshwar, J., & Narsimha, G. (2017). Secure way routing protocol for mobile ad hoc network. Wireless Networks, 23(2), 345–354.
Li, T., Ma, J i a n Feng, & Sun, C. (2019). SRDPV: Secure route discovery and privacy-preserving verification in MANETs. Wireless Networks, 25(4), 1731–1747.
Hu, Y. C., Perrig, A., & Johnson, D. (2005). ARIADNE: A secure on-demand routing protocol for ad hoc networks. Wireless Networks, 11(1), 21–38.
Perrig, A., Canetti, R., Tygar, D., & Song, D. (2002). The tesla broadcast authentication protocol. RSA Cryptobytes (RSA Laboratories), 5(2), 2–13.
Buttyan, L., Acs, G., & Vajda, I. (2006). Provably secure on-demand source routing in mobile ad hoc networks. IEEE Transactions on Mobile Computing, 11(5), 1533–1546.
Kim, J., & Tsudik, G. (2009). SRDP: Secure route discovery for dynamic source routing in manets. Ad Hoc Networks, 7, 1097–1109.
Mohanapriya, M., & Krishnamurthi, I. (2014). Modified DSR protocol for detection and removal of selective black hole attack in manet. Computers and Electrical Engineering, 40, 530–538.
Djenouri, D., & Badache, N. (2009). On eliminating packet droppers in MANET: A modular solution. Ad Hoc Networks, 7, 1243–1258.
Avramopoulos, I., Kobayashi, H., Wang, R., & Krishnamurthy, A. (2004). Highly secure and efficient routing. In INFOCOM 2004 twenty-third annual joint conference of the IEEE computer and communications societies.
Cong, Pu, Lim, S., Chae, J., & Jung, B. (2019). Active detection in mitigating routing misbehavior for MANETs. Wireless Networks, 25(4), 1669–1683.
Sanzgiri, K., Dahill, B., Levine, B. N., Shields, C., & Belding-Royer, E. M. (2002). A secure routing protocol for ad hoc networks. In Proceedings of 10th IEEE international conference on network protocols (ICNP) (pp. 78–87).
Kravets, R., Yi, S., & Naldurg, P. (2001). A security-aware routing protocol for wireless ad hoc networks. In Proceedings of the 2nd ACM international symposium on mobile ad hoc networking computing (pp. 299–302).
Papadimitratos, P., & Haas, Z. J. (2002). Secure routing for mobile ad hoc networks. In Proceedings of the SCS communication networks and distributed systems modeling and simulation conference (CNDS 2002) (pp. 193–204).
Awerbuch, B., Curtmola, R., Holmer, D., Nita-Rotaru, C., & Rubens, H. ()2008. ODSBR: An on-demand secure byzantine resilient routing protocol for wireless ad hoc networks. In ACM transactions on information and system security (TISSEC) (vol. 10, No. 4).
Khan, F. A., Imran, M., Abbas, H., & Durad, M. H. (2017). A detection and prevention system against collaborative attacks in mobile ad hoc networks. Future Generation Computer Systems, 86, 416–427.
Khan, F. A., Imran, M., Abbas, H., & Durad, M. (2017). A detection and prevention system against collaborative attacks in mobile ad hoc networks. Future Generation Computer Systems, 68, 416–427.
Baadache, A., & Belmehdi, A. (2012). Fighting against packet dropping misbehavior in multi-hop wireless ad hoc networks. Journal of Network and Computer Applications, 35, 1130–1139.
Baadache, A., & Belmehdi, A. (2014). Struggling against simple and cooperative black hole attacks in multi-hop wireless ad hoc networks. Computer Networks, 73, 173–184.
Buchmann, J., Dahmen, E., & Schneider, M. (2008). Merkle tree traversal revisited. In Proceedings of the 2nd international workshop on post-quantum cryptography (PQCrypto'08) (pp. 63–78).
Stephen Dabideen, J. J. (2012). Garcia-Luna-Aceves, "Secure routing in MANETs using local times". Wireless Networks, 18(7), 811–826.
Pani, N. K., &Mishra, S. (2014). Secure hybrid routing for manet resilient to internal and external attacks. In Proceedings of the 48th annual convention of computer society of India (pp. 449–458).
Usman, M., Jan, M. A., He, X., & Nanda, P. (2018). QASEC: A secured data communication scheme for mobile ad-hoc networks. Future Generation Computer Systems. https://doi.org/10.1016/j.future.2018.05.007.
Casado, L. S., Fernández, G. M., Teodoro, P. G., & Carrión, R. M. (2015). A model of data forwarding in MANETs for lightweight detection of malicious packet dropping. Computer Networks, 87, 44–58.
Sastry, N., Shankar, U., & Wagner, D. (2003). Secure verification of location claims. In Proceedings of the 2003 ACM workshop on wireless security (WiSeâ03), New York, NY, USA (pp. 1–10).
Liu, K., Abu-Ghazaleh, N., & Kang, K. (2007). location verification and trust management for resilient geographic routing. Journal of Parallel and Distributed Computing, 67, 215–228.
Pagnin, E., Hancke, G., & Mitrokotsa, A. (2015). Using distance-bounding protocols to securely verify the proximity of two-hop neighbours. IEEE Communication Letters, 19(7), 1173–1176.
Pathak, V., Yao, D., & Iftode, L. (2008). Securing geographical routing in mobile ad-hoc networks.In Department of Computer Science, Rutgers University. Technical Report (p. 638).
Song, J., Wong, V. W. S., & Leung, V. C. M. (2007). Secure position-based routing protocol for mobile ad hoc networks. Ad Hoc Networks, 5, 76–86.
Boulaiche, M., & Bouallouche-Medjkoune, L. (2017). HSecGR: Highly secure geographic routing. Journal of Network and Computer Applications, 80, 189–199.
Xia, H., Yu, J., Pan, Z., et al. (2016). Applying trust enhancements to reactive routing protocols in mobile ad hoc networks. Wireless Networks, 22(7), 2239–2257.
Singh, T., Singh, J., & Sharma, S. (2017). Energy efficient secured routing protocol for MANETs. Wireless Networks, 23(4), 1001–1009.
Priya, S., & K annan, N. (2017). Refined trust energy-ad hoc on demand distance vector (ReTE-AODV) routing algorithm for secured routing in MANET. Wireless Networks, 23(7), 2227–2237.
Abdel-Halim, I. T., Fahmy, H. M. A., & Bahaa-Eldin, A. M. (2015). Agent-based trusted on-demand routing protocol for mobile ad-hoc networks. Wireless Networks, 21(2), 467–483.
Kout, A., Labed, S., Chikhi, S., & Bourennane, E. B. (2018). AODVCS, a new bio-inspired routing protocol based on cuckoo search algorithm for mobile ad hoc networks. Wireless Networks, 24(7), 2509–2519.
Kshirsagar, V. H., Kanthe, A. M., & Simunic, D. (2018). Trust based detection and elimination of packet drop attack in the mobile ad-hoc networks. Wireless Personal Communications, 100, 311–320.
Yun, J. H., & Park, M. H. (2013). Single-adversary relaying attack defense mechanism in wireless ad hoc networks. Wireless Personal Communications, 72, 2519–2532.
Poongodi, T., & Karthikeyan, M. (2016). Localized secure routing architecture against cooperative black hole attack in mobile ad hoc networks. Wireless Personal Communications, 90, 1039–1050.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Boulaiche, M. Survey of Secure Routing Protocols for Wireless Ad Hoc Networks. Wireless Pers Commun 114, 483–517 (2020). https://doi.org/10.1007/s11277-020-07376-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07376-1




